Webszerverek Biztonsági Beállításai
Pfeiffer Szilárd
Balasys
Grades
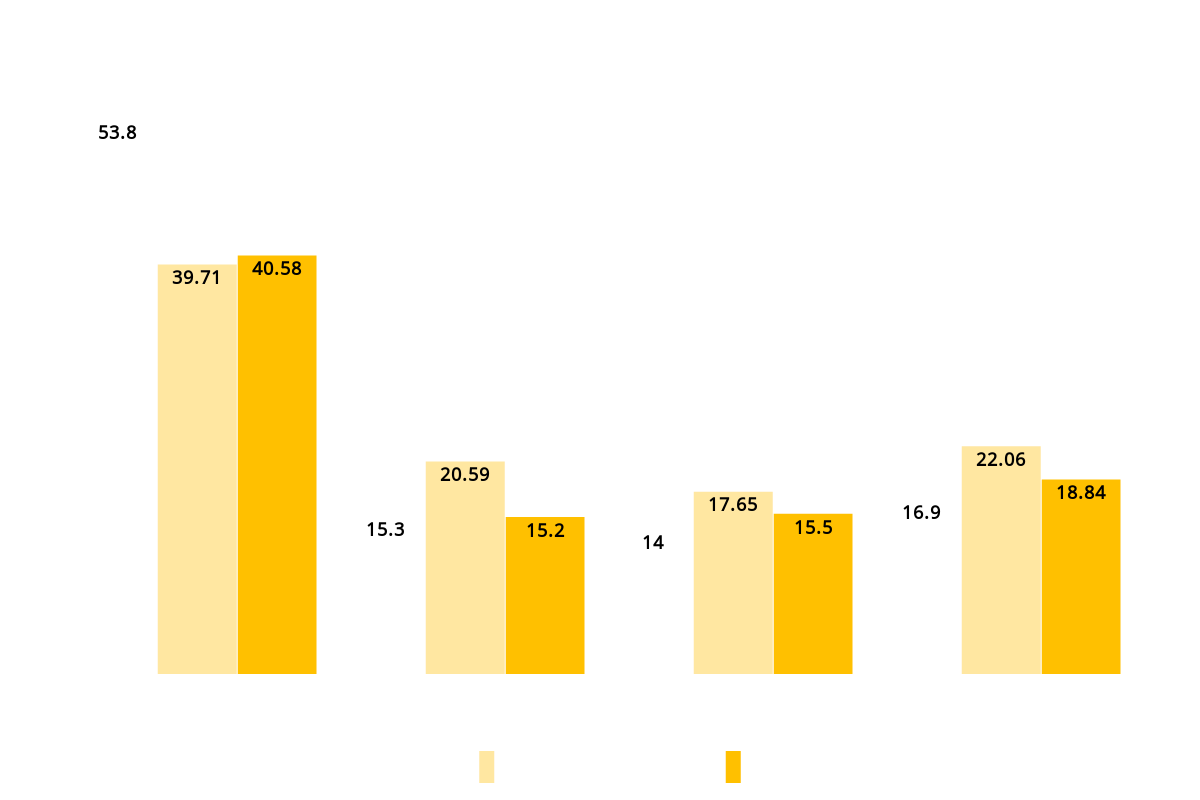
Vulnerabilities
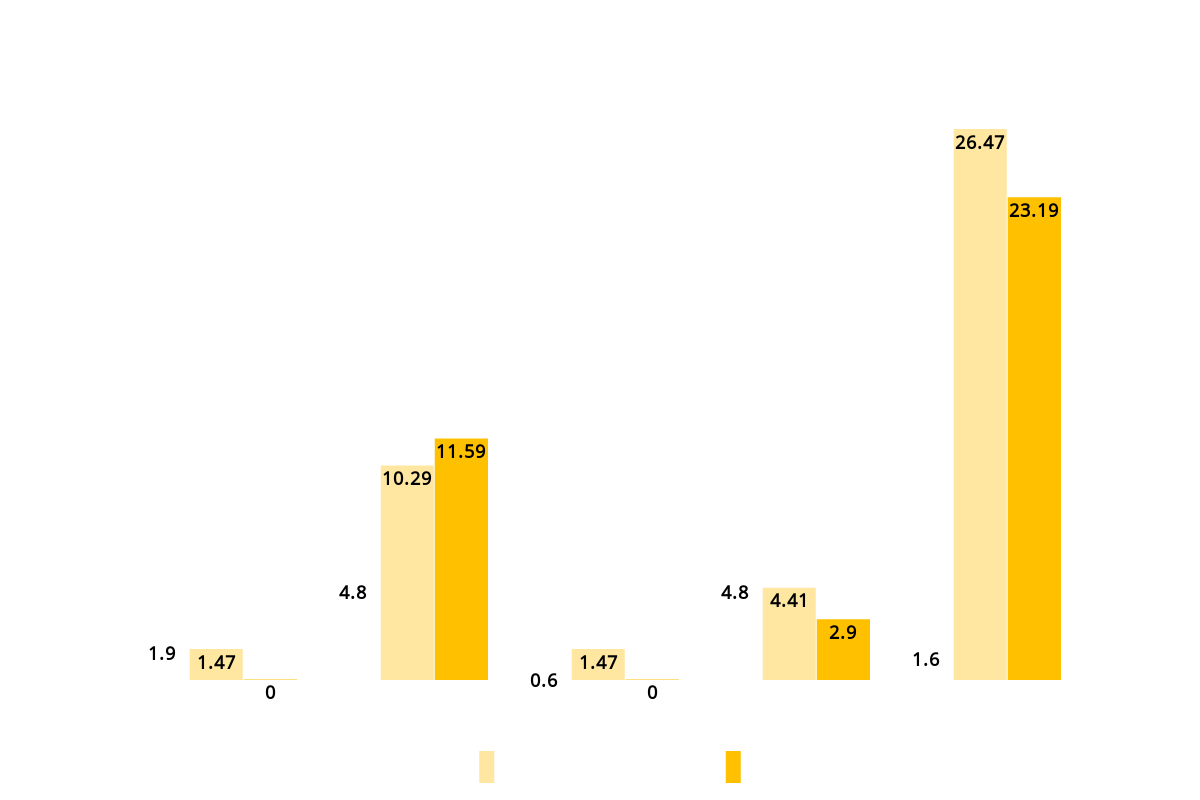
TLS Protocols
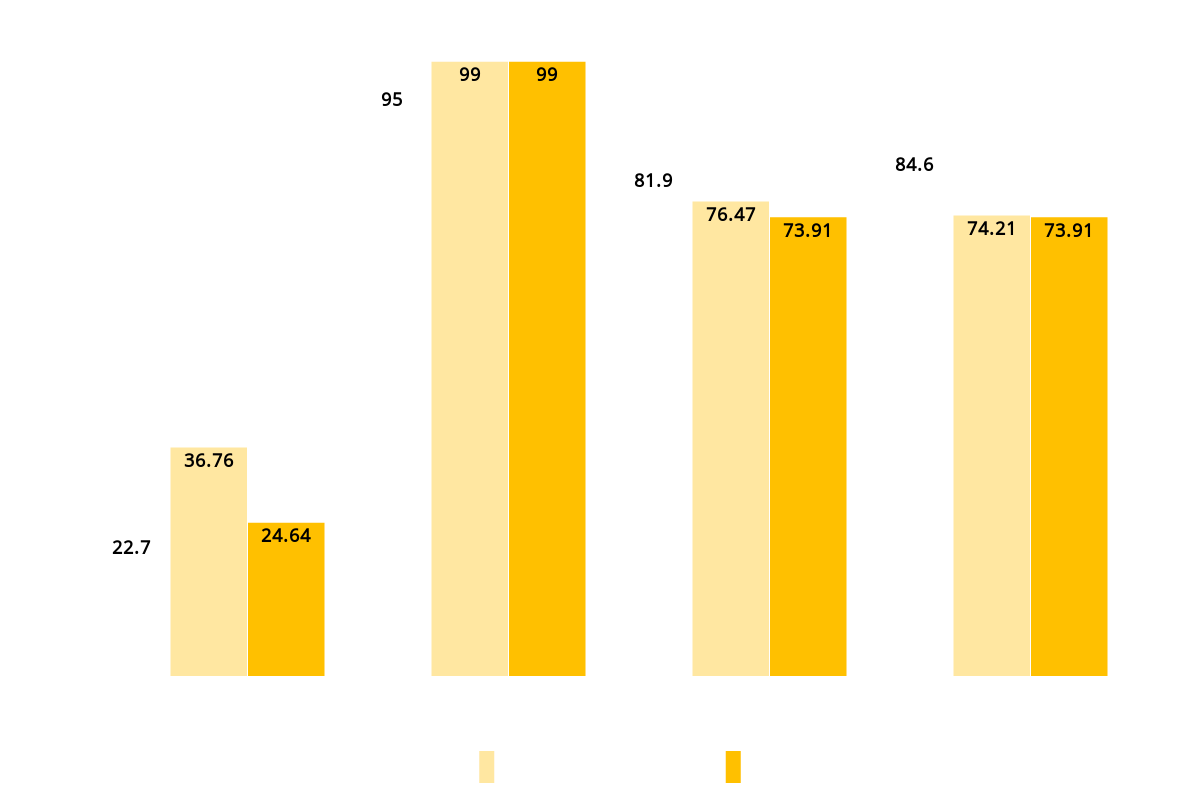
TLS Protocols
ssl.use-sslv2 = "disable" ssl.use-sslv3 = "disable"
Lighttpd
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
Nginx
SSLProtocol all -SSLv2 -SSLv3
Apache
?TLSv1 !SSLv2 !SSLv3
Cipher Suites
TLS
protocol
_ECDHE
_RSA
_AES_CBC
_SHA
key agreement
authentication
symmetric cipher
mac
hash
Key Sizes
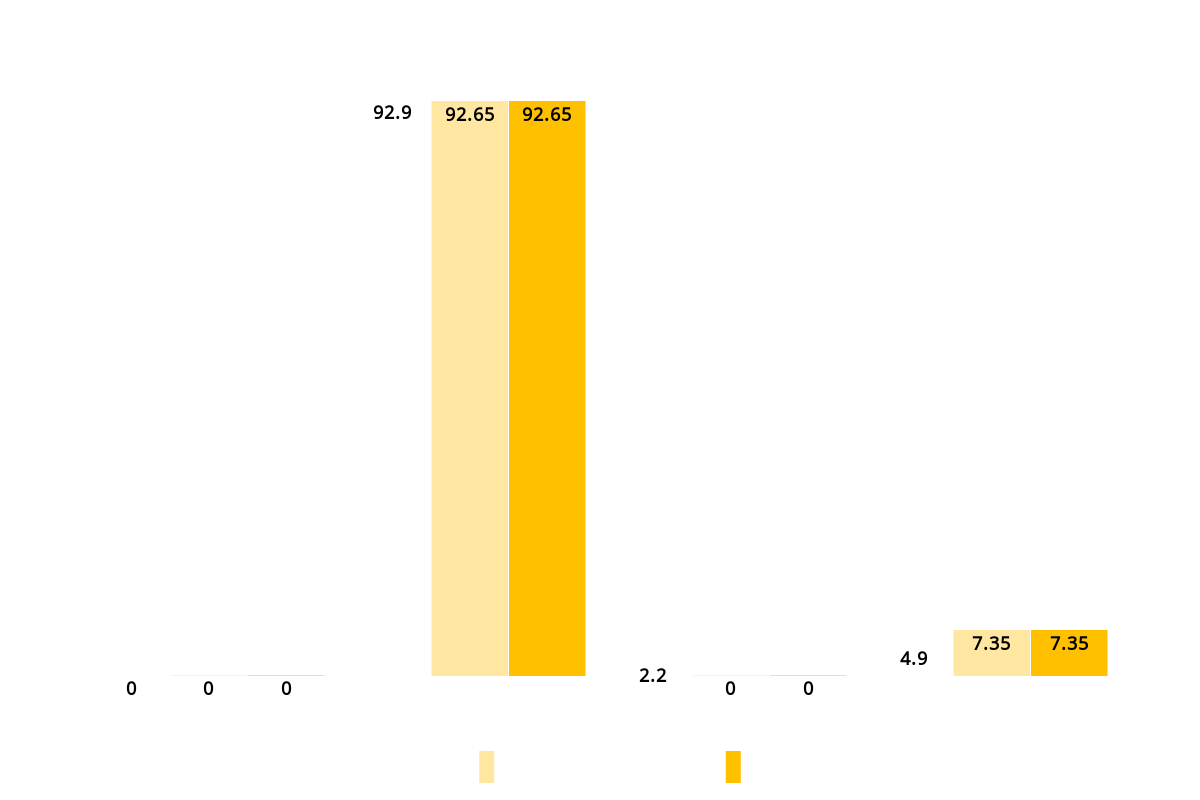
Rivest Cipher 4
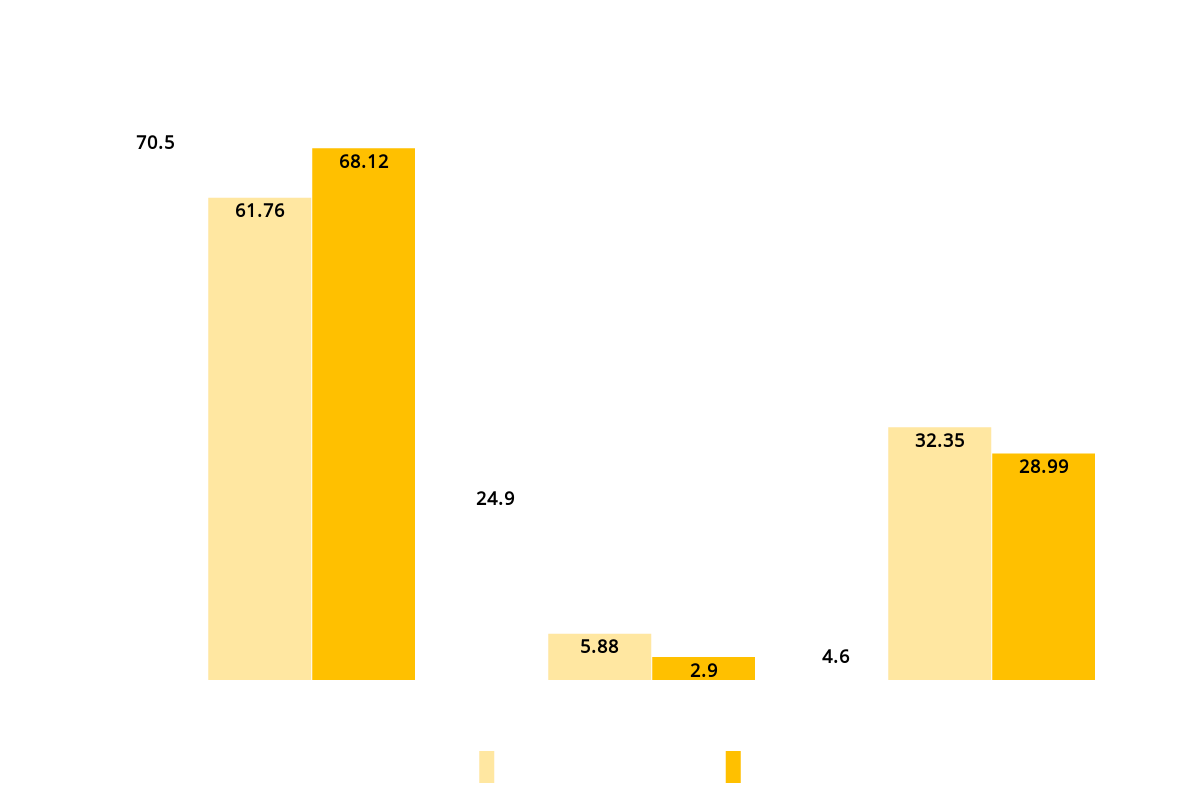
Exchange Strength
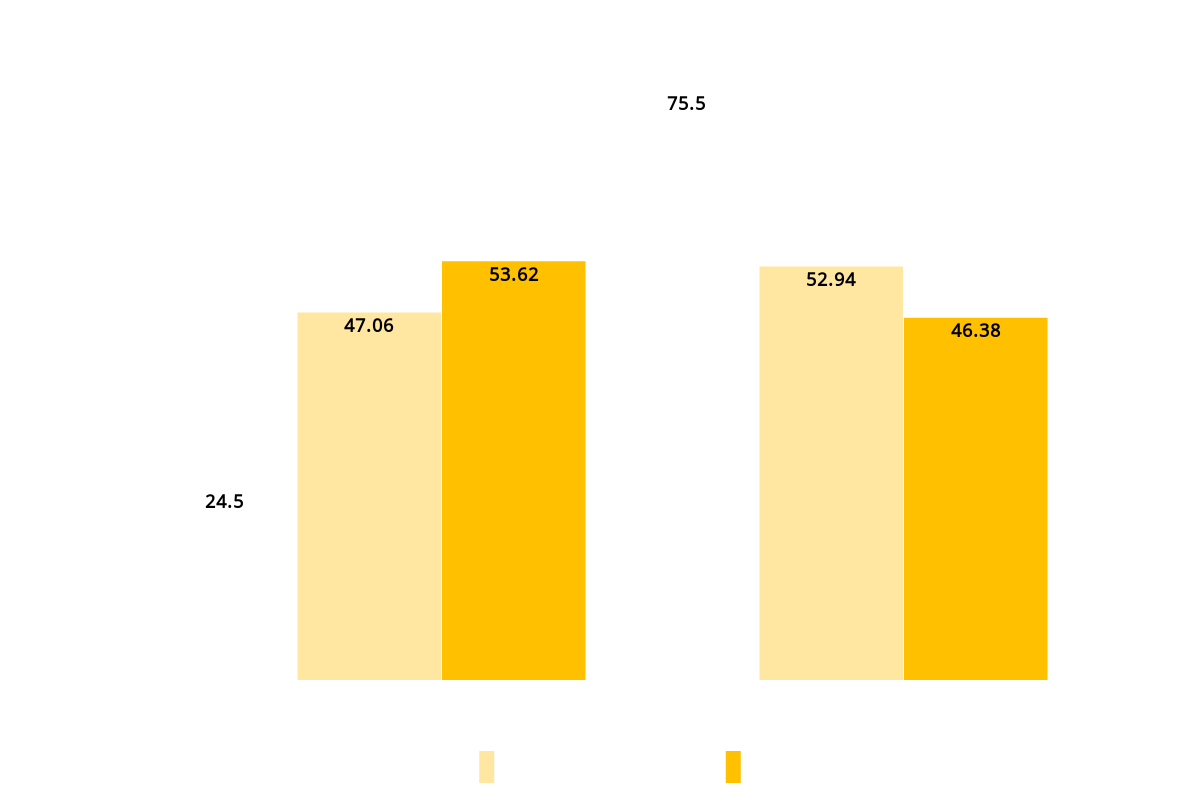
Cipher Suites
ssl.cipher-list = "CipherSuiteString"
Lighttpd
ssl_ciphers CipherSuiteString
Nginx
SSLCipherSuite CipherSuiteString
Apache
EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5;
Cipher Preference
honor-cipher-order = "enable"
Lighttpd
ssl_prefer_server_ciphers on;
Nginx
SSLHonorCipherOrder on
Apache
Always On
Revocation Check
-
Certificate Revocation List
-
Online Certificate Status Protocol
-
Responders
-
Stapling
-
OCSP Stapling
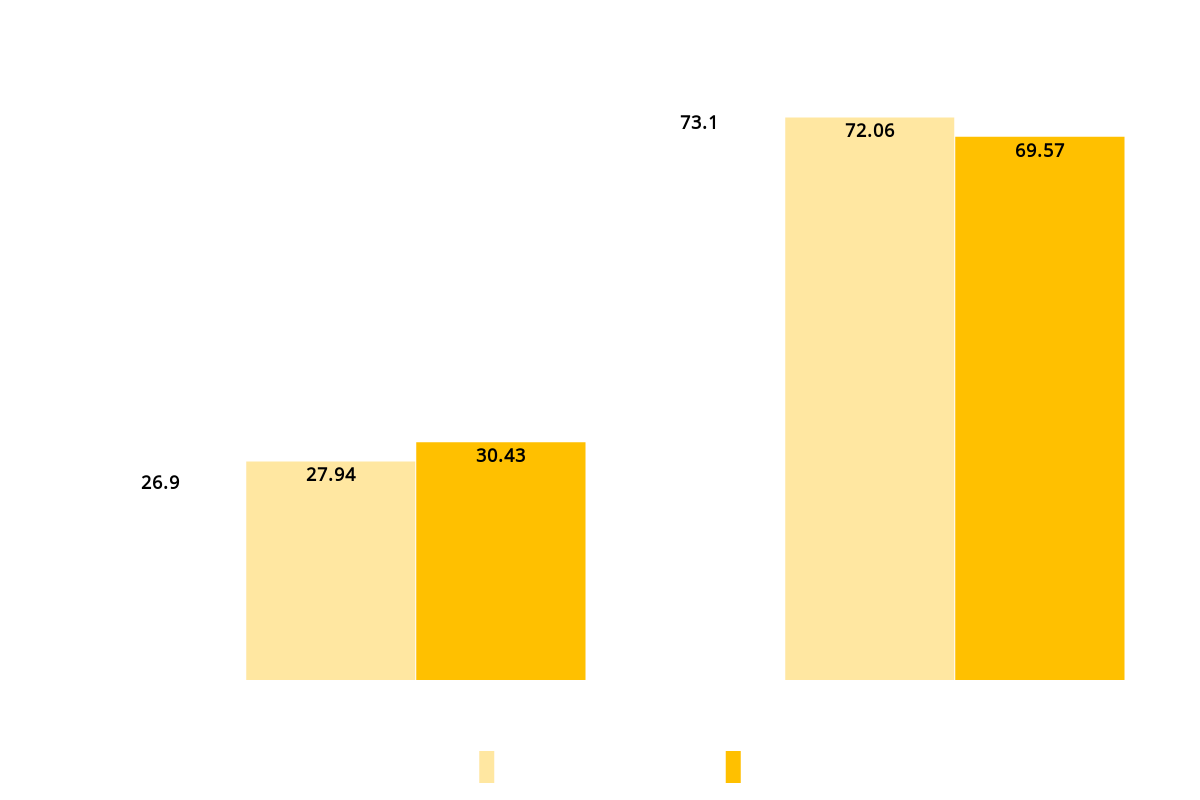
OCSP Stapling
-
Lighttpd
ssl_stapling on;
Nginx
SSLUseStapling on
Apache
Should Be On
Secure Headers
-
Automatic Redirect to HTTPS
-
Public Key Pinning
-
Defense against
-
Clickjacking
-
Content Injection Attacks
-
Cross-site scripting
-
HTTP Strict Transport Security
setenv.add-response-header=("Strict-Transport-Security"=>"Value")
Lighttpd
add_header Strict-Transport-Security "Value" always;
Nginx
Header always set Strict-Transport-Security "Value"
Apache
max-age=63072000; includeSubdomains;
HTTP Public Key Pinning
setenv.add-response-header=("Public-Key-Pins"=>"Value")
Lighttpd
add_header Public-Key-Pins "Value" always;
Nginx
Header always set Public-Key-Pins "Value"
Apache
pin-sha256="GRAH5Ex+kB4cCQi5gMU82urf..."; max-age=15768000; includeSubDomains
Clickjacking
setenv.add-response-header=("X-Frame-Options"=>"Value")
Lighttpd
add_header X-Frame-Options "Value" always;
Nginx
Header always set X-Frame-Options "Value"
Apache
SAMEORIGIN
XSS Protection
setenv.add-response-header=("X-XSS-Protection"=>"Value")
Lighttpd
add_header X-XSS-Protection "Value" always;
Nginx
Header always set X-XSS-Protection "Value"
Apache
X-XSS-Protection: 1; mode=block
Content Security Policy
setenv.add-response-header=("Content-Security-Policy"=>"Value")
Lighttpd
add_header Content-Security-Policy "Value" always;
Nginx
Header always set Content-Security-Policy "Value"
Apache
default-src https://same.domain:443
Tools
- Proxy
- MITM
- Squid
- Zorp
-
Checker
-
Online
-
HTBridge
-
Qualys
-
securityheaders.io
-
-
Offline
-
CipherScan
-
SSLyze
-
-
Questions?
