Frontend security
Craig Loftus
OWASP
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging & Monitoring

Server
Django
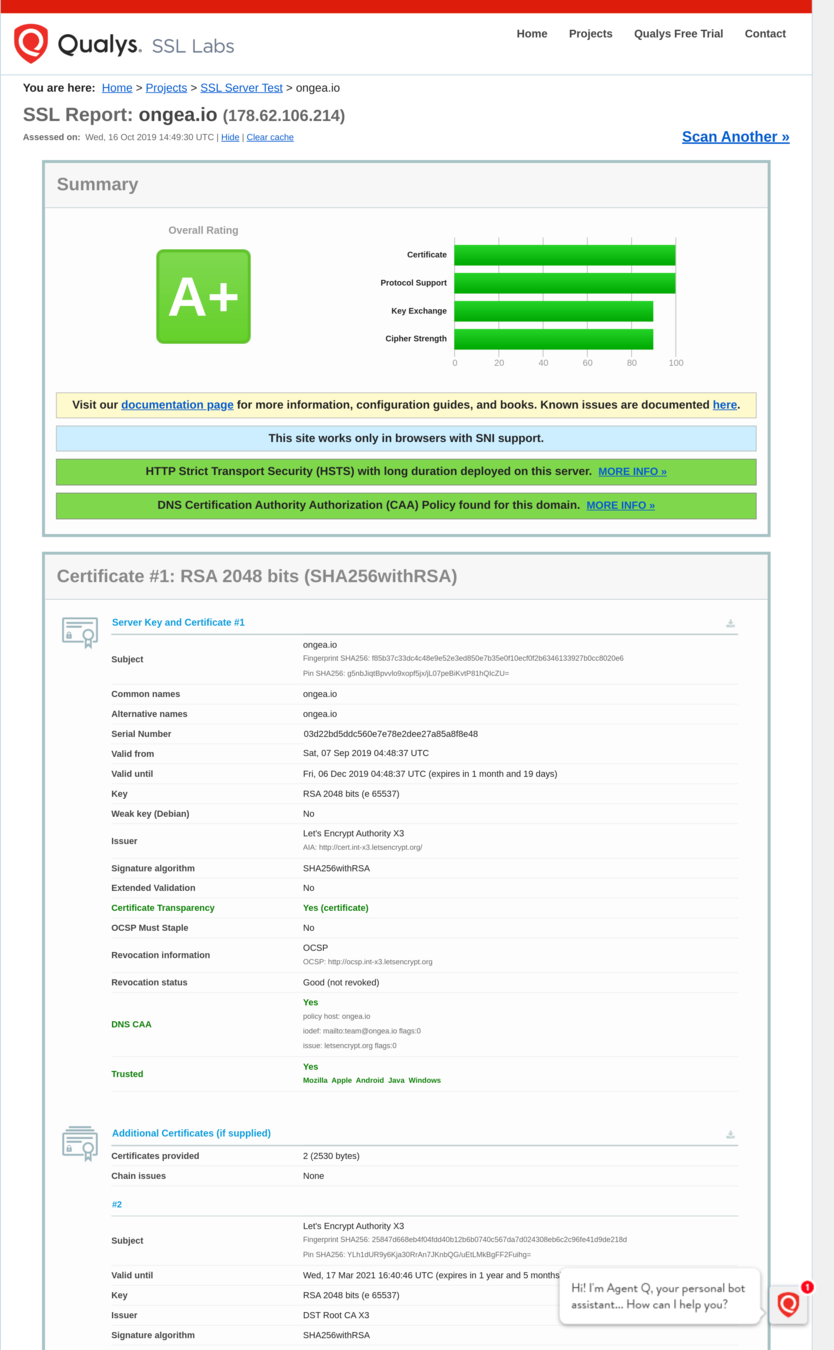
TLS
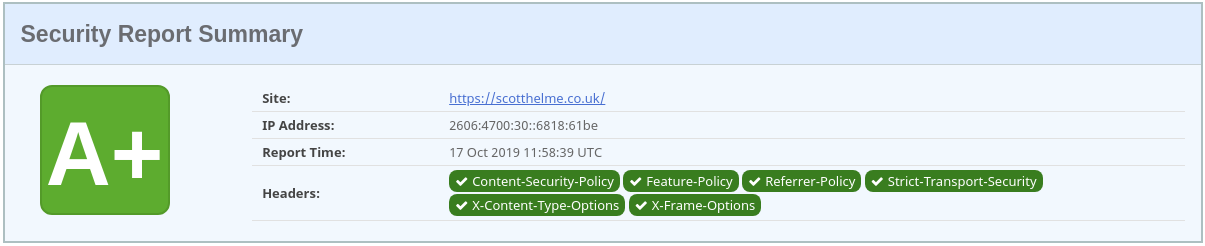
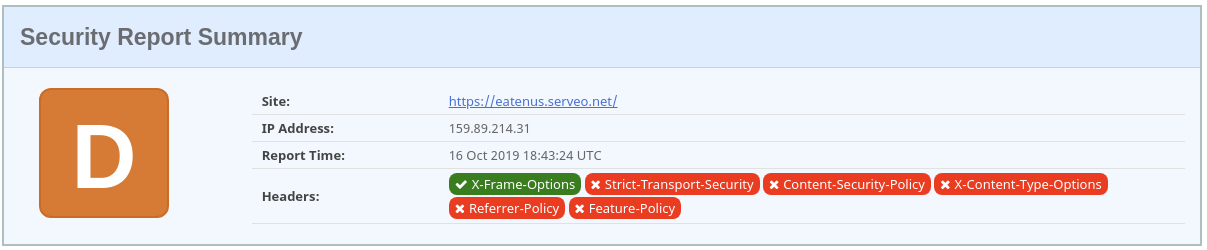
Security headers
TLS
HSTS & Preloading

CAA
Certification Authority Authorization
example.org. CAA 128 issue "letsencrypt.org"Not a hard technical control
CT
Certificate Transparency
OCSP Stapling
Tries to fix certificate revocation...
Enforce with Must-Staple
Django
By default
Batteries included
$ ./manage.py check --deployX_FRAME_OPTIONS = 'DENY'
CSRF_COOKIE_SECURE = True
SESSION_COOKIE_SECURE = True
SECURE_SSL_REDIRECT = True
SECURE_BROWSER_XSS_FILTER = True
SECURE_CONTENT_TYPE_NOSNIFF = True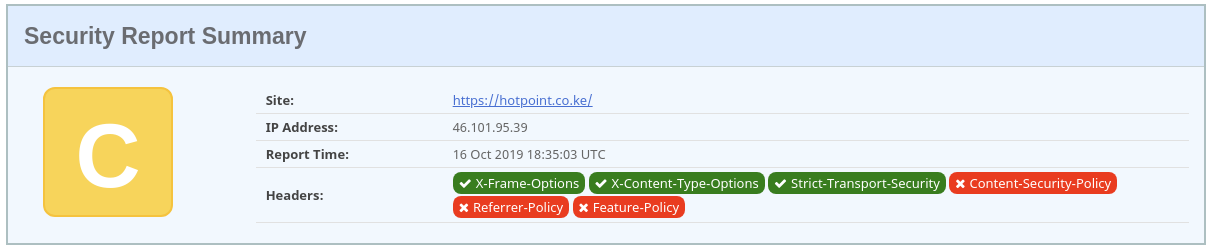
CSP_DEFAULT_SRC = ("'self'",)
CSP_SCRIPT_SRC = ("'self'", "static.example.com")
CSP_IMG_SRC = ("*",)Content-Security-Policy
$ pip install django-cspcsp.middleware.CSPMiddlewareMitigate cross site scripting attacks by blocking resources
CSP Wizard
CSP_DEFAULT_SRC = ("'none'",)
CSP_REPORT_ONLY = True
CSP_REPORT_URI = "{wizard url}"Migrating existing be daunting
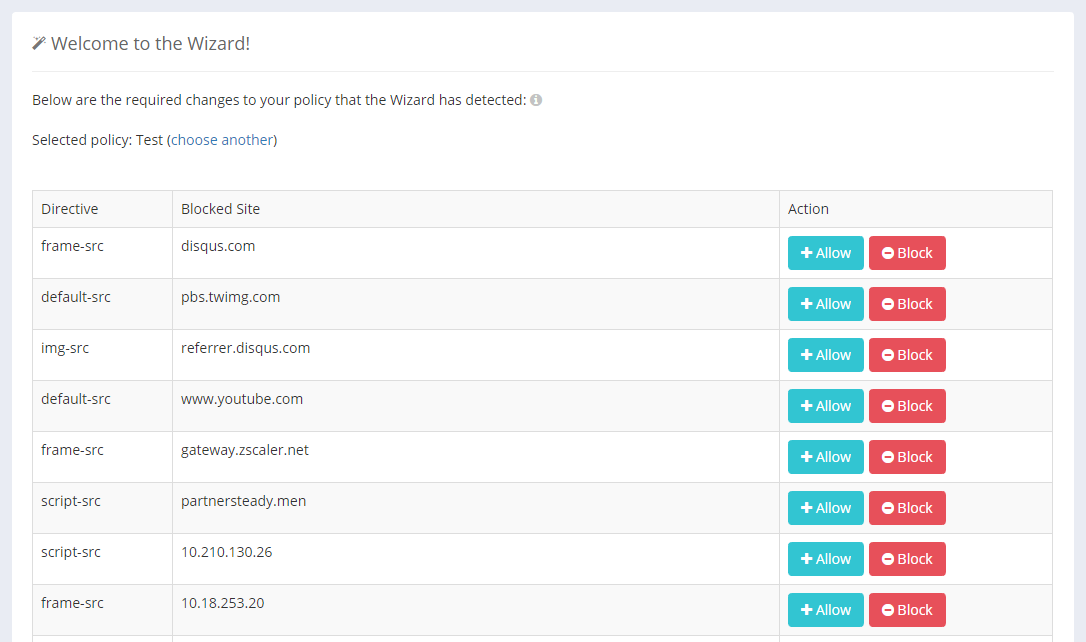
CSP extra
CSP_UPGRADE_INSECURE_REQUESTS = TrueCSP_BLOCK_ALL_MIXED_CONTENT = TrueCSP don'ts
'unsafe-inline'
'unsafe-eval'Don't be Mozilla
Referrer-Policy
REFERRER_POLICY = "same-origin"$ pip install django-referrer-policydjango_referrer_policy.middleware.ReferrerPolicyMiddlewareHow and when to send the Referer header
Feature-Policy
FEATURE_POLICY = {
'geolocation': 'none',
'usb': 'none',
}$ pip install django-feature-policydjango_feature_policy.FeaturePolicyMiddlewareLets you turn off browser features
All good now?