Protect Your Work! Intro to Data Security for Graduate Students
Please go to:
https://slides.com/cypurr/cuny-data-security#/
Series
Your Perspective
http://bit.ly/ITP-images
Find/make images that depict your mental images of "Data security"
Holistic Approach


Holistic Approach

- Balance, not purity
- Improving, not finishing
Threat Modeling
- What do I want to protect?
- Who am I protecting it from?
- How likely is this threat?
- What are the consequences if I fail?
- How much trouble am I willing to go through to prevent the consequences?
- Implement change && return to (1)

Threat #1: You
Defend yourself from yourself: maintain good backup practices
Common Examples:
- Saving a file while you are working on it
- Saving copies for different versions
- realFINAL-FINALcopy(2).docx
- Saving to external HDD or Flash
- Printing a copy
- Emailing to self
- Uploading Dropbox/Gdrive/
OneDrive for Business
Backup Strategies: Crunch v. Maintenance
Designing a backup strategy
- Standardize: Find a naming/saving style that works
- eg. Title_2018-11-12.doc
- eg. Embrace the desktop clutter
- Minimum of "3 - 2 -1 Backup"
- 3 copies of a file
- 2 forms of storage
- 1 off-site location
- Automate as much as possible



$ bash
Levels of backup
-
Full disk clone
- 'dd' in commandline
- Clonezilla
- File/Folder auto-backup
- On a PC:
- Duplicati
- borg
- On a Network:
- Syncthing
- Across the web:
- Duplicati
- rClone/Cryptomator
- IFTTT
- NextCloud
- On a PC:





Threats 2+: Data security
Data at rest v Data in motion
- At rest:
- Physical access
- Web access
- Hardware/Software failures hazards
- In Motion
- "On the wire" security
- Infrastructure
- Shared security (herd immunity)





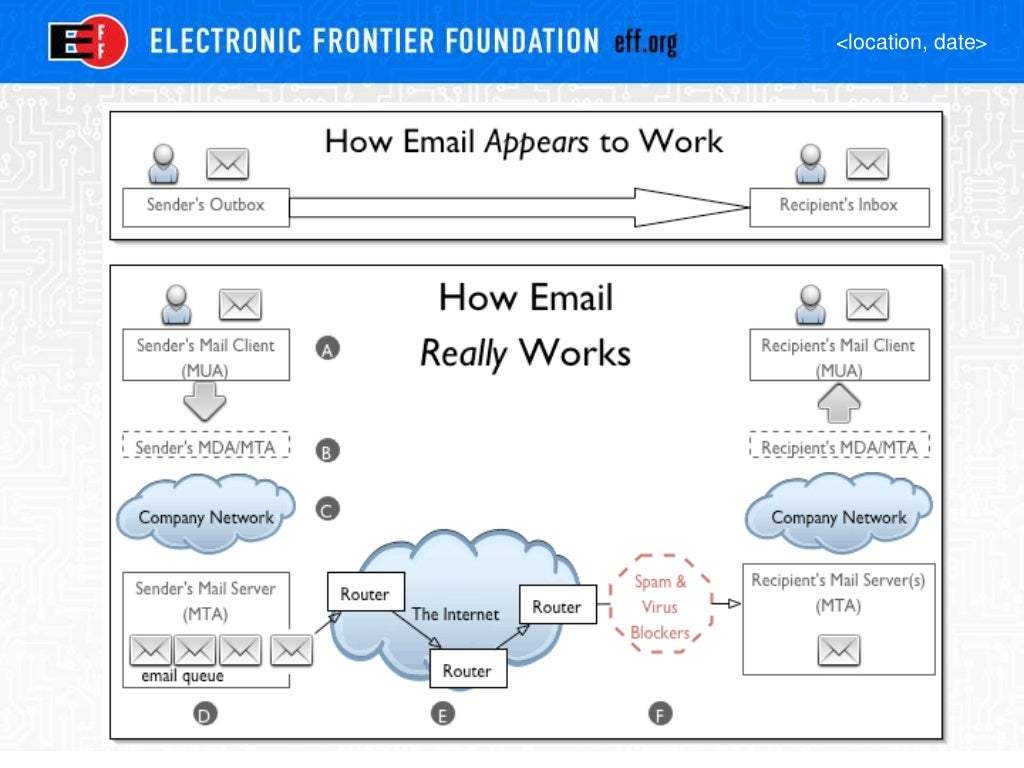
Important File Actor Map
You
Your PC
Your Phone
Your server space
Peer's server space
Peer
Peer's PC
Peer's Phone

CUNY PC


ISPs

Encryption (without the math)







You

Server

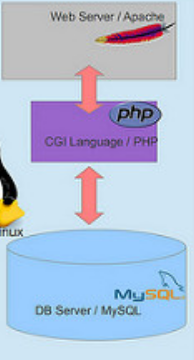

In motion



VPNs



You

Server



In motion

"client-side"

"Server-side"
Online storage
Public or Private?
Maintain authorship?
Maintain authorship?










Data at Rest
- Access
- Who controls the hardware?
- Who has access to your files?
- Air gap
- Check the settings
- Strong passwords
- Encryption
- Veracrypt
- Collaboration
- Establish an access protocal
- Establish a moving protocol

Data at Rest - Know your Rights
- Access
- Passwords are protected by 5th amendment
- biometrics (i.e. fingerprint) are NOT.
- Forced access: 0days, GrayKey, etc
- 4th amendment, but not on the border
- Border includes 100 mi from international airport
- Collaboration
- Tools like TOR now = probable cause
- Subpoena-proof Standard
- Includes Signal Messenger, Private Internet Access VPN
Scenario:
- You are doing controversial research in an authoritarian country. You are also worried that this research may stir interest from US intelligence agencies
- What do you do before your trip?
- What do you bring?
- How do you store/more data during your trip?
- Harm-reduction model