Intro to Mobile Security
cypurr.org
slides.com/cypurr/intro2mobile

Who are we? Who are you?
- We are the…
- The Cypurr Collective: A group of folks that organize cybersecurity workshops and socials, looking to spread knowledge and talk about privacy rights!
- ...and you are?
- Name
- Pronouns (i.e. he/him, she/her, they/them, etc)
- In a few words, what brings you here today?
- Safer space workshops
- What are we trying to protect?
- Who makes money from your phone? (and how?)
- What are some components of a mobile phone?
Code: Instructions for your computer to complete.
"Open Source": A program that lets you read the instructions it contains (and even change them)
Proprietary: A program that keeps their instructions a secret

First, some terms to keep in mind
The Problem with Mobile Phones
- Not designed for privacy and security
- More locked down with proprietary code, making it harder to control than regular computers.
- Can't change OS
- Planned obsolescence with updates
- harder to investigate malware
- harder to prevent snooping
- Phones and Phone #s attached to our identity, finances, etc

Building a smart phone
- Central Processing Unit (CPU)- Completes instructions from code
- IMEI- unique ID assigned to every phone
- Baseband Processor (bbp)- Manages all radio functioning
- The bbp acts as a second mind, running its own proprietary code
"Smart" Components
SD card- "Secure Digital"
Similar to a flash drive
NFC- "Near Field Communication"
Can speak to devices within 4cm. e.g. used for payments.
SIM card - "Subscriber Identity Module"
Unique card idenity, user identity when activated, contacts
Software
- Before this, any code was provided by the manufacturer(s), e.g. Samsung
- What are the differences between Android and iOS?
- What apps do you use?
- Any apps you can't remove?
- How many apps are proprietary v. "open"?
- Where do you get your apps?
Your info
- What information are you making available to your phone?
- What info is available to 3rd party programs?
- What info can be picked when your phone communicates with other devices?
- How is location tracked?





- Check your settings!
- secure lock screen
- disk encryption
- SIM-card lock
- Google ad/location settings!
- Marie Kondo app management
- Use a browser instead of apps!
- Use a computer instead of phone!
- Turn things off! (bluetooth, nfc, etc)









- Check your settings/permissions regularly
- Update update update!
- Avoid new proprietary apps
- Make regular backups of important data!
- Leave your phone at home
- Educate others!
- Advocate for policy changes! (e.g. eff.org)

Let's install Signal
- What does it cost?
- Nothing! it is a open source non-profit
- Why?
- Signal offers encrypted texts between users
- Privacy needs herd immunity
- Is it complicated?
- It's like any other app, you can also make it your default text app on android
- What are the downsides?
- It uses mobile data, it is secure but not anonymous-- still uses your phone #

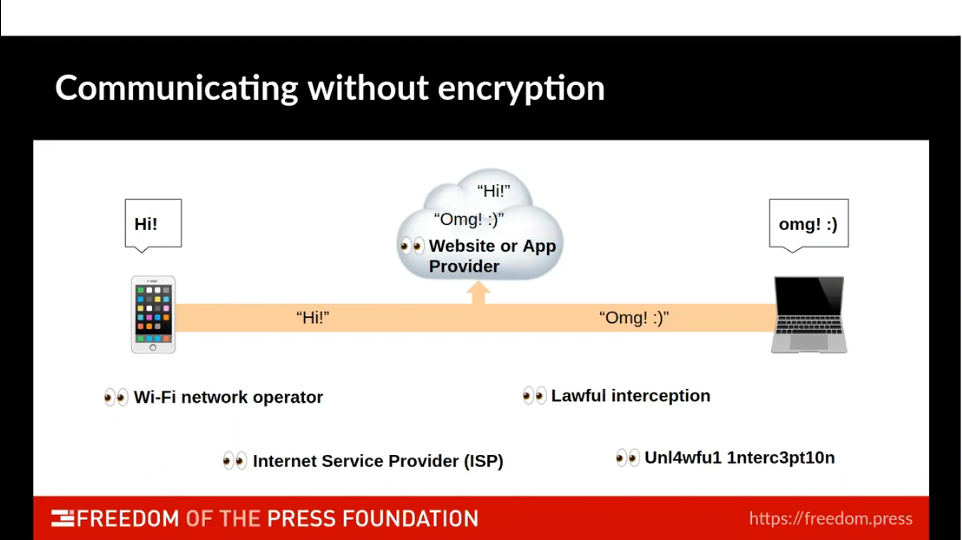

How would you make a secret code?

- iOS/Android groups
- Go to your app store
- Search for "Signal"
- Install the app
- App setup
- Safety numbers!
- What is "verification"?
- Send a message! (optional)
- Who will you help install signal?
Resources
Find us on cypurr.nyc
Ask about our email list
-
Further Resources
-
NYC CryptoParty Meetup/CryptoParty Harlem (Meetup)
-
HackBlossom (Hackblossom.org)
-
ctrlshift.space I/O
-
Tactical Tech Collective- Holistic Security, MyShadow, Data Detox
- EFF ssd.eff.org and sec.eff.org
-
Freedom of the Press Foundation (Freedom.press)
-
Upcoming
Brooklyn Public Library every month
(Nov 10th)
Monthly open meeting
(Nov 12th)
Movie night at Babycastles
(Nov 14th)
securiTEA online harassment chat at Bluestockings
(Nov 17th)
And more! check out our social media or email list

Thanks!