
Protest
Security
cypurr.nyc
slides.com/cypurr/protest-security/
Locking down your digital life
Outline:
- Intro
- Holistic Security & Threat Modeling
- Protest Security
- Locking down your phone
Who are we?
- We are…
- The Cypurr Collective
- In bk/nyc
- Cat enthusiasts
- Tech unenthusiasts
- Coming from a queer/feminist/anti-capitalist lens
- Members of the Electronic Frontier Alliance
- Here to learn from you as well

Ground Rules
-
Saf(er) Space
-
We DO NOT tolerate demeaning/harmful language or behavior
-
Don't pressure or question someone discussing their experience/threat model/situation
-
Consent: Ask before helping someone out!
-
-
Keep it constructive!
-
Share the space!
-
Stack! Raise your hand, we'll queue speakers
-
-
Photo/Video- Ask for approval!
-
Identify yourself if you are a...
-
reporter, researcher, or law enforcement
-


Warmup
What are some things you consider when you...
- Are out late at night?
- Leave home for a few days?
- Aren't allowed to have your phone?
- Are attending a protest?

What are our goals today?
What does the word "hacking" make you think of?
Holistic Approach


https://myshadow.org/
Holistic Approach


Balance > Purity Growing > Finishing
Threat Modeling
- What is being protected?
- Assets
- Who am I protecting it from?
- Adversaries
- How likely is this threat?
- Capabilities
- What are the consequences of failure?
- Threat
- How much trouble am I willing to go through to prevent the consequences?
- Risk

ssd.eff.org

Balance Threats

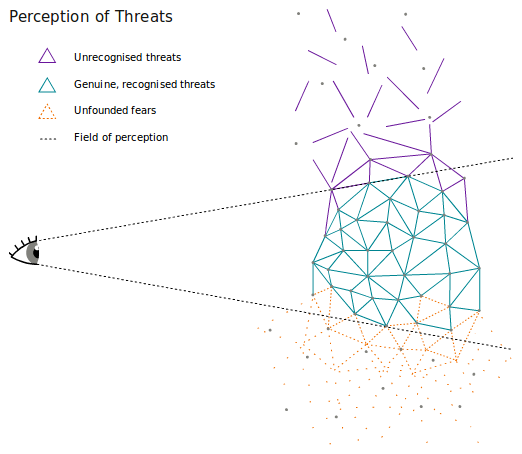

Threat Responses

- Groups
- Harder Group Boundaries
- Authoritarianism
- Fixed Patterns
- Individuals
- Freeze
- Fight
- Flight
- Comply
- Tend
- Befriend
- Posture

Before a Protest

ssd.eff.org
- Enable full-disk encryption on your device
- Remove fingerprint unlock, pixel imprint, and FaceID
- biometrics v. passwords - the 5th amendment
- Install Signal
- Back up your data
- Prepaid phone or no phone
- Face protection



At a Protest

ssd.eff.org
- Take photos and videos without unlocking
-
Consider biking or walking to the protest
-
Enable airplane mode
-
IF arrested, remember:
-
request an attorney before/during questioning
-
You can't lie, but officers can (and will)
-
If asked to open your phone say you "do not consent to a search of your device"
-
Remember the 5th amendment!
-
Defending your rights may be penalized
-

- Not designed for privacy and security
- More locked down with proprietary code, making it harder to control than regular computers.
- Many apps collect and share data
- Might not need access to your phone to get assets
- Phones and Phone #s attached to our identity, finances, etc

The Problem with Mobile Phones
Code: Instructions for your computer to complete.
"Open Source": A program that lets you read the instructions it contains (and even change them)
Proprietary: A program that keeps their instructions a secret

First, some terms to keep in mind
Phone Prep
"Smart" Components
SD card- "Secure Digital"
Similar to a flash drive
NFC- "Near Field Communication"
Can speak to devices within 4cm. e.g. used for payments.
SIM card - "Subscriber Identity Module"
Unique card idenity, user identity when activated, contacts
Your info
- What information are you making available to your phone?
- What info is available to 3rd party programs?
- What info can be picked when your phone communicates with other devices?
- How is location tracked?





- Check your settings!
- Marie Kondo app management
- Use a browser instead of apps!
- Use a computer instead of phone!
- Turn things off! (bluetooth, nfc, etc)









- Check your settings/permissions regularly
- Update update update!
- Avoid new proprietary apps
- Make regular backups of important data!
- Leave your phone at home
- Educate others!
- Advocate for policy changes! (e.g. eff.org)

Let's install Signal
- What does it cost?
- Nothing! it is a open source non-profit
- Why?
- Signal offers encrypted texts between users
- Privacy needs herd immunity
- Is it complicated?
- It's like any other app, you can also make it your default text app on android
- What are the downsides?
- It uses mobile data, it is secure but not anonymous-- still uses your phone #

Data in Motion

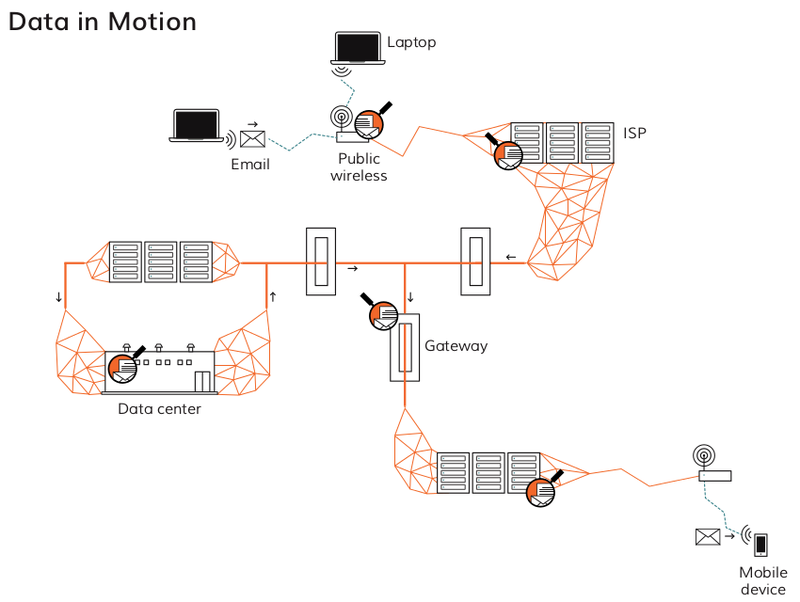



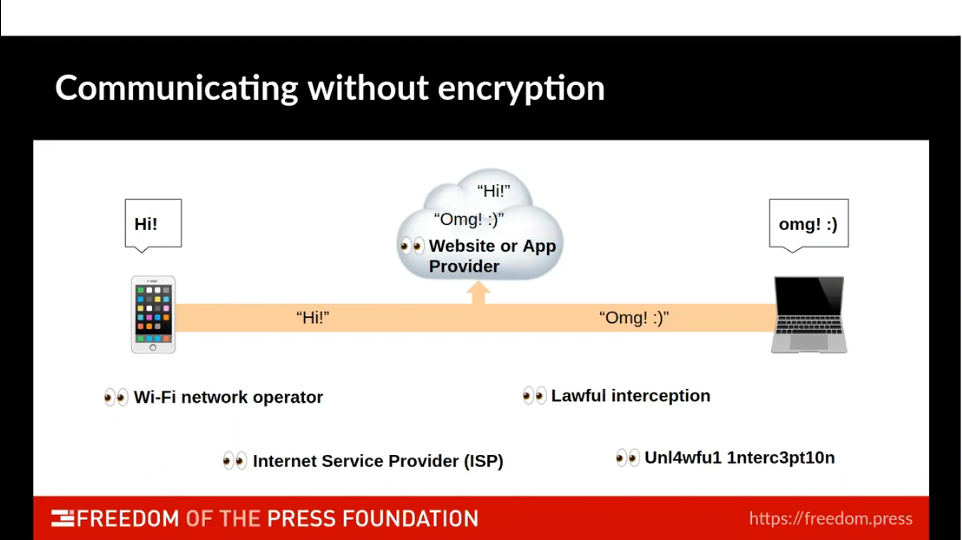

How would you make a secret code?

- iOS/Android groups
- Go to your app store
- Search for "Signal"
- Install the app
- App setup
- Safety numbers!
- What is "verification"?
- Send a message! (optional)
- Who will you help install signal?
Resources
-
NYC
-
CyPurr Collective- cypurr.nyc and cypurr@protonmail.com
-
NYC CryptoParty and Meetup.com for other events
-
Freedom of the Press Foundation (Freedom.press)
- Tech and Learning Collective
- Calyx Institute & CryptoHarlem
- Pop Gym (self defense)
-
- Online
- Tactical Tech Collective- tacticaltech.org
- EFF- Surveillance Self Defense (ssd.eff.org) Security Edu Companion (sec.eff.org)
- Tool Recommendations
- privacytools.io
- prism-break.org
Upcoming
Brooklyn Public Library every month
(Feb 2nd 2-4pm)
Monthly open meeting
(Feb 4th 6-8pm)
Movie night at Babycastles
(Feb 13th 7-10pm)
securiTEA time at Bluestockings
(Feb 16th 1-3pm)
And more! check out our social media or email list
Thanks!
