
Security in Web Development



LET'S BUILD TOGETHER
OWASP TOP 10
- A1 Injection
- A2 Broken Authentication and Session Management
- A3 Cross-Site Scripting (XSS)
- A4 Broken access control
- A5 Security Misconfiguration
- A6 Sensitive Data Exposure
- A7 Insufficient Attack Protection
- A8 Cross-Site Request Forgery (CSRF)
- A9 Using Components with Known Vulnerabilities
- A10 Underprotected APIs


LET'S BUILD TOGETHER
A1 Injection



LET'S BUILD TOGETHER
A2 Broken Authentication and Session Management



LET'S BUILD TOGETHER
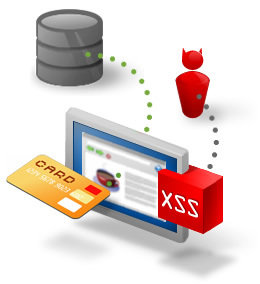
A3 Cross-Site Scripting (XSS)


LET'S BUILD TOGETHER
A4 Broken access control


LET'S BUILD TOGETHER
A5 Security Misconfiguration


LET'S BUILD TOGETHER
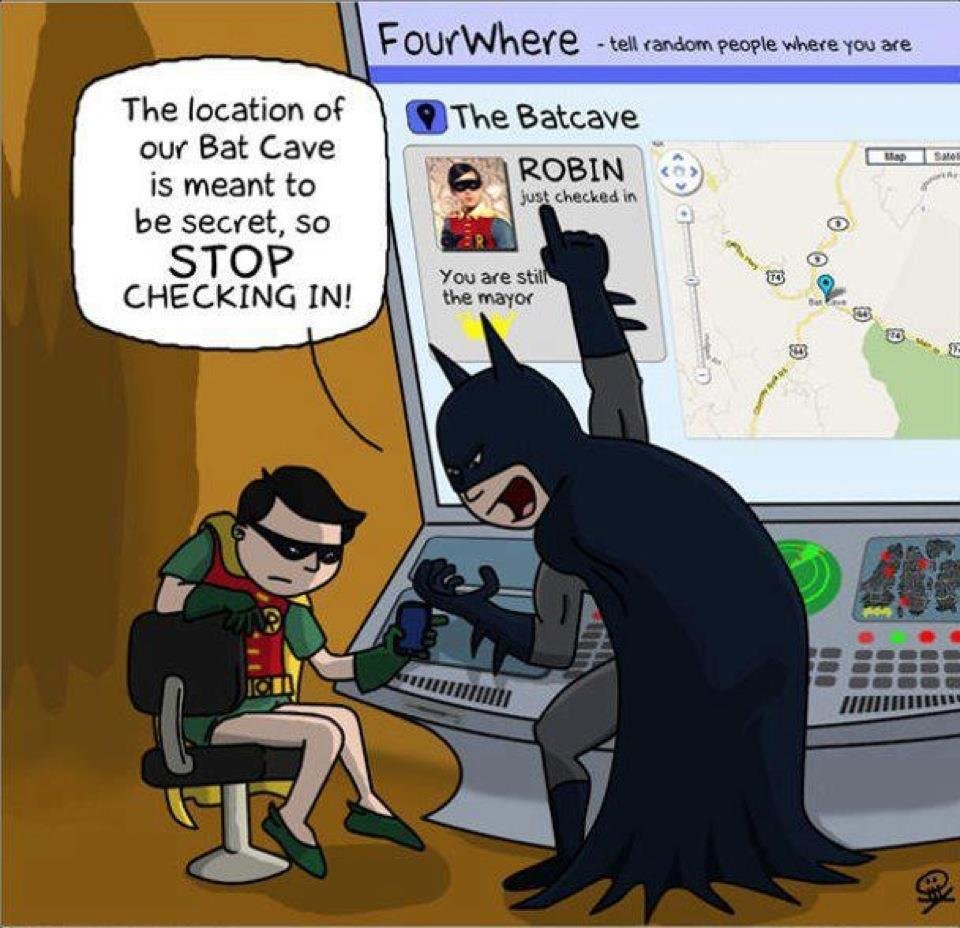
A6 Sensitive Data Exposure


LET'S BUILD TOGETHER
A7 Insufficient Attack Protection



LET'S BUILD TOGETHER
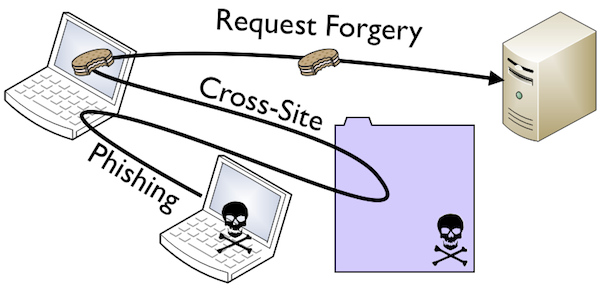
A8 Cross-Site Request Forgery (CSRF)


LET'S BUILD TOGETHER
A9 Using Components with Known Vulnerabilities
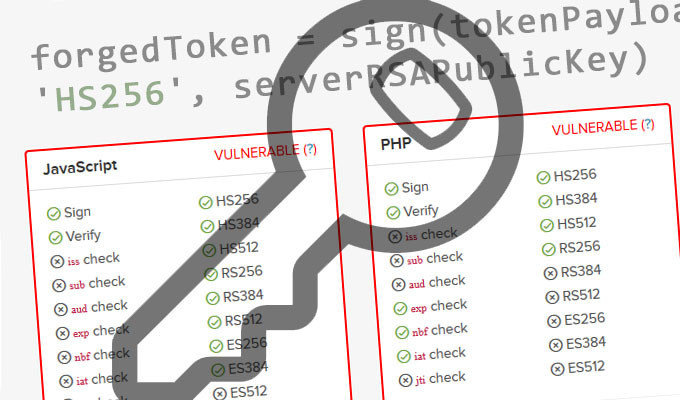


LET'S BUILD TOGETHER
A10 Unprotected APIs



LET'S BUILD TOGETHER
Tools OWASP

Zed Attack Proxy
Spidering
Fuzzing

XSS
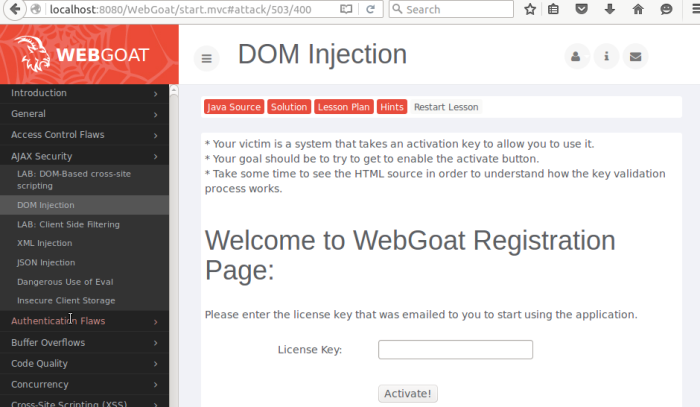
Test web security

Test all owasp points


LET'S BUILD TOGETHER

http://rockalabs.com

Juankzu
JUAN C. ZULUAGA
WEB DEVELOPER

