bitcoin

laurent hardy


@donhylo
WHO I AM

2009 Bio Engineer
2010 Water & Energy Nexus
2012 MSc Renewable Energy Systems Technology
2012 Complex Adaptive Systems
2016 Ethereum Madrid
2018 Cryptoeconomics.hub
Photo from VitalCheck
Banking
Prove your identity
Have enough money
Trust them to handle private information
Pay for maintenance
Wait...




ID
money
trust the bank
account + access
BITCOIN How banking works


@donhylo
BITCOIN HOW BANKING WORKs


@donhylo

alice
[0x171]


$10
0

source: Karl Floersh, cryptoeconomics.study
nonces = {
0x171: 0,
}





nonces = {
0x171: 1,
}balances = {
0X171: 50,
0x3f3: 0,
}balances = {
0X171: 40,
0x3f3: 10,
}BITCOIN HOW BANKING WORKs


@donhylo


alice
[0x171]


$10
0

source: Karl Floersh, cryptoeconomics.study
nonces = {
0x171: 0,
}





nonces = {
0x171: 1,
}balances = {
0X171: 50,
0x3f3: 0,
}balances = {
0X171: 40,
0x3f3: 10,
}

$20
1


$20
1








nonces = {
0x171: 2,
}balances = {
0X171: 20,
0x3f3: 10,
0xbad: 20,
}

Bitcoin has no barrier to entry




a private key – Available in different formats, must be kept private
an address – Used to receive payments, can be shown to anybody
example 1: 1J7mdg5rbQyUHENYdx39WVWK7fsLpEoXZy example 2: qR code

private key ≈ secret key ≈ sk
BITCOIN How Bitcoin works


@donhylo
private key
address
BITCOIN How Bitcoin works


@donhylo
BITCOIN HOW bitcoin WORKs | utxo


@donhylo

alice
[0x171]


$49
source: Karl Floersh, cryptoeconomics.study


$49
output
is_spent
$100
value: 100 owner: 0x171
0
{
{
{
inputs: [0],
outputs: [
{value: 49, owner: 0x3f3},
{value: 49, owner: 0x8t6},
{value: 2, owner: 0x171},
],
sigs: [ ]
}
value: 49 owner: 0x3f3
value: 49 owner: 0x8t6
value: 2 owner: 0x171
0
0
0
1
{
{
{
{
{
{
BITCOIN HOW bitcoin WORKs | utxo


@donhylo

jing
[0x8t6]


$35
source: Karl Floersh, cryptoeconomics.study
output
is_spent
$49
value: 100 owner: 0x171
{
{
{
inputs: [2],
outputs: [
{value: 35, owner: 0xUt2},
{value: 14, owner: 0x8t6},
],
sigs: [ ]
}
value: 49 owner: 0x3f3
value: 49 owner: 0x8t6
value: 2 owner: 0x171
0
0
0
1
{
{
{
{
{
{
1
value: 14 owner: 0x8t6
0
{
{
value: 35 owner: 0xUt2
0
{
{
BITCOIN How Bitcoin works | double spend attack


@donhylo


alice
[0x171]



node a
node b
source: Karl Floersh, cryptoeconomics.study


$10


$10


$10


$10
Bitcoin is cryptographically secure
Prove your private key is the owner of your public key
(sk,pk) := generateKeys(keysize)
private key ≈ secret key ≈ sk
public key ≈ pk
sig ≈ digital signature
BITCOIN Cryptography


@donhylo
Prove you own a public key without revealing the private key
sig := sign(message,sk)
Let everyone verify you own a public key without revealing the private key
isValid := verify(message,sig,pk)
An private key is a 256-bit randomly generated number between
The total number of 256-bit numbers is equal to \(2^{256}\)
see why \(2^{256}\) is an astronomical number
source: Mastering Bitcoin, LearMeABitcoin
"string"
Binary:
1101111101011011011000101011111001111100111011011110100110010101001001010101000001010111110011111001010101011001100001101001100001010000101010111101011001110101010010010101010101110000100110001110010010000110111000111110100010111100100111010111000000011111
Decimal:
101027229823651685479805873605520737270124184003399402029102140131823486595103
Hexadecimal:
df5b62be7cede995255057cf9559869850abd67549557098e486e3e8bc9d701f
0 and 115792089237316195423570985008687907853269984665640564039457584007913129639935
BITCOIN Private key


@donhylo
A public key is derived from the private key and is obtained through ECDSA (Elliptic Curve Digital Signature Algorithm).
- Start at G
- Draw a tangent
- Find the intersection (-2G)
- Take the inverse (2G)
This is one round of elliptic curve multiplication (i.e an elliptic curve multiplication of 2).
To find a public key, "multiply" G by the private key, i.e bounce around the ecliptic curve private key numbers of times.
source: Mastering Bitcoin, LearMeABitcoin
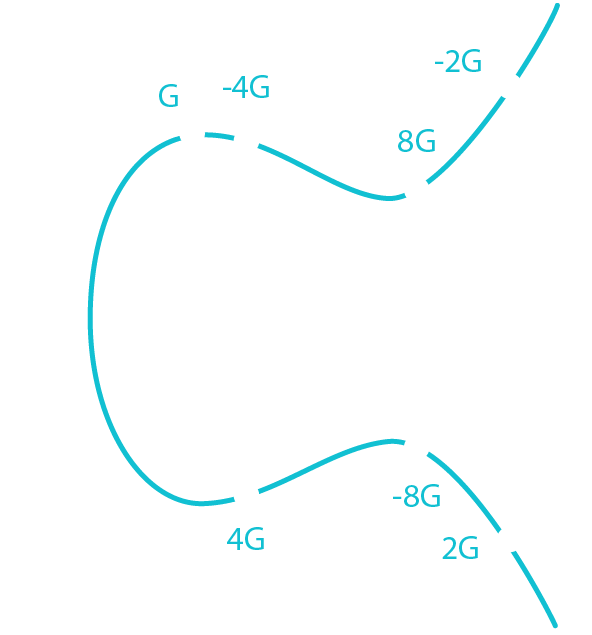
BITCOIN Public key


@donhylo
Public Key = G * Private Key
Public Key = G * df5b62be7cede995255057cf9559869850abd67549557098e486e3e8bc9d701f
Through ECDSA we get 2 new coordinates:
x = 81591541406288143274758265124625798440200740391102527151086648448953253267255
y = 64573953342291915951744135406509773051817879333910826118626860448948679381492
In hexadecimal
Public Key (x) = b4632d08485ff1df2db55b9dafd23347d1c47a457072a1e87be26896549a8737
Public Key (y) = 8ec38ff91d43e8c2092ebda601780485263da089465619e0358a5c1be7ac91f4
Keep only the (x) coordinate and discriminate the sign of the (y) coordinate
Public Key = 02b4632d08485ff1df2db55b9dafd23347d1c47a457072a1e87be26896549a8737
source: LearMeABitcoin
BITCOIN Public key


@donhylo
An address is derived from the public key through the use of one-way cryptographic hashing (SHA256 and RIPEMD160).
Addresses are almost always presented to users in an encoding to help human readability, avoid ambiguity, and protect against errors (Base58Check).
Example: 1J7mdg5rbQyUHENYdx39WVWK7fsLpEoXZy
source: Mastering Bitcoin
BITCOIN Address


@donhylo
A wallet is a software application that contain your private key, can generate pair of keys and make things convenient for the user.
Wallets contain keys, not coins! Wallets are keychains.
- Nondeterministic (Random) Wallets
- Deterministic (Seeded) Wallets
- Mnemonic Code Words
- Hierarchical Deterministic Wallets
source: Mastering Bitcoin
BITCOIN Wallet


@donhylo
Prove your private key is the owner of your public key
(sk,pk) := generateKeys(keysize)
private key ≈ secret key ≈ sk
public key ≈ pk
sig ≈ digital signature
BITCOIN Cryptography


@donhylo
Prove you own a public key without revealing the private key
sig := sign(message,sk)
Let everyone verify you own a public key without revealing the private key
isValid := verify(message,sig,pk)
Used to claim ownership of your bitcoin (UTXO).
A digital signature (Sig) is public information, accesible to everyone.
It is unique to the message, i.e the signature changes with the message being signed.
Ran = G * Random Number Sig = [Ran * Private Key] + Message / Random Number
Sig = [Ran * Private Key] + H[transaction] / Random Number
You can proof you own a public key by giving Ran and Sig to someone.
source: LearMeABitcoin
BITCOIN Digital signature


@donhylo
Prove your private key is the owner of your public key
(sk,pk) := generateKeys(keysize)
private key ≈ secret key ≈ sk
public key ≈ pk
sig ≈ digital signature
BITCOIN Cryptography


@donhylo
Prove you own a public key without revealing the private key
sig := sign(message,sk)
Let everyone verify you own a public key without revealing the private key
isValid := verify(message,sig,pk)
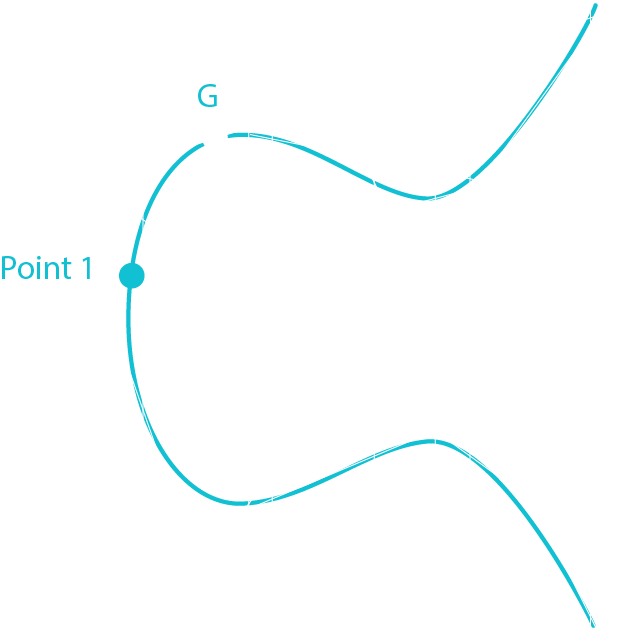
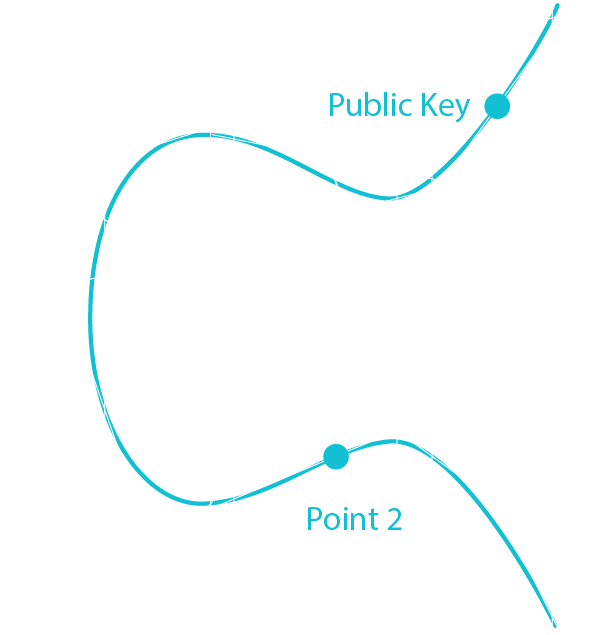
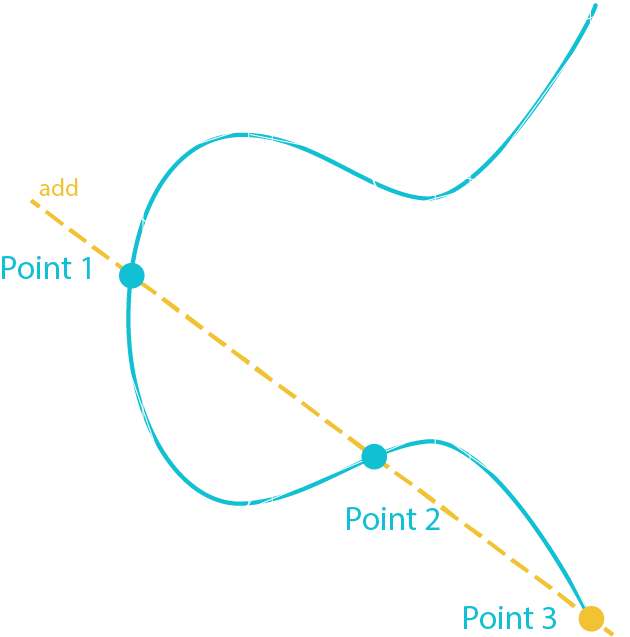
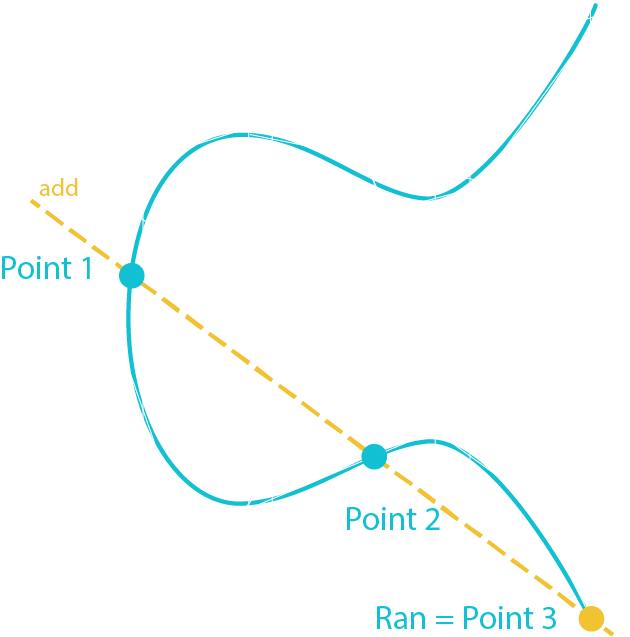
The goal is to verify that the public key and the digital signature were made using the same private key by giving them Sig, Ran, Public Key and Message.
Point 1 = G * [Sig * Message]
Point 2 = Public Key * [Sig * Ran]
Point 3 = Point 1 + Point 2
If Point 3 is equal to Ran then the signature has been proven to be valid
Ran = G * Random Number
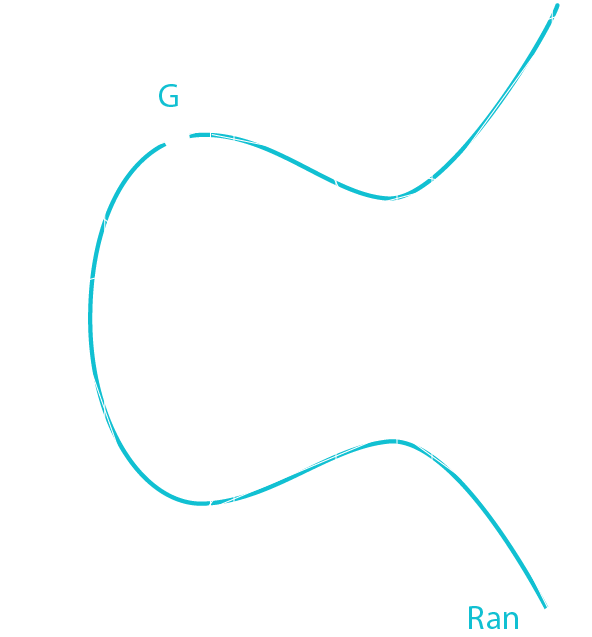
BITCOIN Signature verification


@donhylo
availability
be able spend your coin whenever you want
security
make sure nobody else can spend your coin
convenience
managing your keys in a relatively easy way
BITCOIN Storing crypto assets


@donhylo
local storage


cold storage
app wallets


paper wallets
hierarchical deterministic wallets
hardware wallets
air gapped computer
hot storage
BITCOIN Storing crypto assets


@donhylo
hot side
cold side
generate keys function
private key generation info
address generation info
generate address
generate key
\(i\) th address
\(i\) th
key
\(i\)
\(i\)
BITCOIN Hierarchical deterministic wallets


@donhylo


Ledger Nano S [LedgerWallet]
Trezor [SatoshiLabs]
BITCOIN Hardware wallets


@donhylo


@donhylo
BITCOIN Mining & consensus
the purpose of mining is to
secure the network


@donhylo
a random game
is played every 10 minutes
between anonymous players

BITCOIN Mining & consensus
Bitcoin
ASIC
Mining Farm


@donhylo
how a
work?
Bitcoins are incentives, or a mean to an end
expected value
block reward
hash power for the participant
number of tokens rewarded each block


@donhylo
BITCOIN Mining & consensus


@donhylo
mining is a colloquial term
of a distributed network
a consensus algorithm
to reach consensus
run by anonymous PARTICIPANTS
for proof-of-work
BITCOIN Mining & consensus
on the state of the blockchain
who use their computation power
in exchange for a reward in bitcoin


@donhylo
BITCOIN Mining & consensus
every 10 minutes
a new block gets created
10min


@donhylo
BITCOIN Mining & consensus
a hash of more or less difficulty to find is established as target
in mining, a valid hash must be below the difficulty target


@donhylo
BITCOIN Mining & consensus
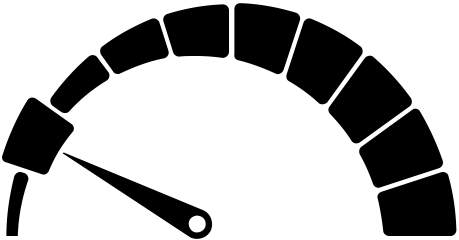
difficulty: 1 (0 bits)
difficulty: 8 (3 bits)
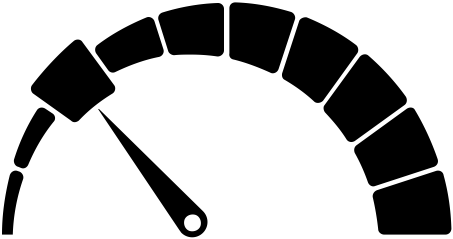
difficulty: 16 (4 bits)
2016*10 minutes
New Target
Old Target
actual time of last 2016 blocks
=
x

BITCOIN Mining & consensus
Proof-of-Work
Proof-of-Stake
Delegated-Proof-of-Stake
Proof-of-Authority
Proof-of-Weight
Byzantine Fault Tolerance
Directed Acyclic Graphs

@donhylo

BITCOIN TEMPER-EVIDENT DATABASE
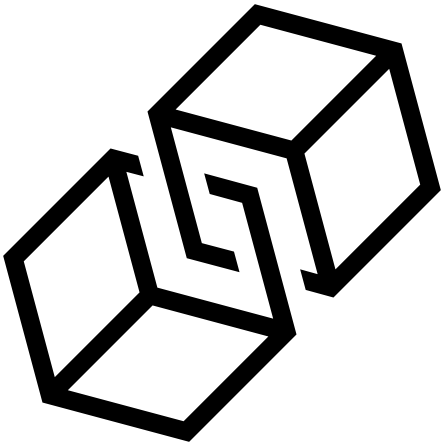
previous block hash
merkle root
difficulty target
timestamp
nonce

previous block hash
merkle root
difficulty target
timestamp
nonce
previous block hash
merkle root
difficulty target
timestamp
nonce

block11
block6
block7
block8
block9
block10


@donhylo
BITCOIN Elements | TEMPER-EVIDENT DATABASE
| 4 bytes | Version | A version number to track software/protocol upgrades |
| 32 bytes | Previous Block Hash | A reference to the hash of the previous (parent) block in the chain |
| 32 bytes | Merkle Root | A hash of the root of the merkle tree of this block’s transactions |
| 4 bytes | Timestamp | The approximate creation time of this block (seconds from Unix Epoch) |
| 4 bytes | Difficulty Target | The Proof-of-Work algorithm difficulty target for this block |
| 4 bytes | Nonce | A counter used for the Proof-of-Work algorithm |
source: Mastering Bitcoin


@donhylo
BITCOIN Elements | previous block header hash
| previous block header hash |
| timestamp |
| difficulty |
| nonce |
| merkle root |
| block height |
| header hash |
| transactions |
| previous block header hash |
| timestamp |
| difficulty |
| nonce |
| merkle root |
| block height |
| header hash |
| transactions |
| previous block header hash |
| timestamp |
| difficulty |
| nonce |
| merkle root |
| block height |
| header hash |
| transactions |
source: Mastering Bitcoin


@donhylo
BITCOIN Elements | merkle root
\(H_{ABCD}\)
Hash\((H_{AB}+H_{CD})\)
\(H_{AB}\)
Hash\((H_{A}+H_{B})\)
\(H_{CD}\)
Hash\((H_{C}+H_{D})\)
\(H_{A}\)
Hash\((T_ A)\)
\(H_{B}\)
Hash\((T_B)\)
\(H_{C}\)
Hash\((T_C)\)
\(H_{D}\)
Hash\((T_D)\)
merkle root
Hands on


@donhylo


@donhylo
BITCOIN Soft fork & Hard fork
Feedback is welcome.
Thanks.



