
A Security Framework
Based on
Apache Shiro


Authentication
Authorization

Session Management
All Through A Common API
Decoupled Security

A Project With Batteries Included
First Release in Less than 1 Month

Goal of This Presentation
Initializing Yosai
from yosai.core import SecurityUtils, ...
# ... initialize a Security Manager here
security_manager = ...
yosai = SecurityUtils(security_manager)
Plug components into the SecurityManager
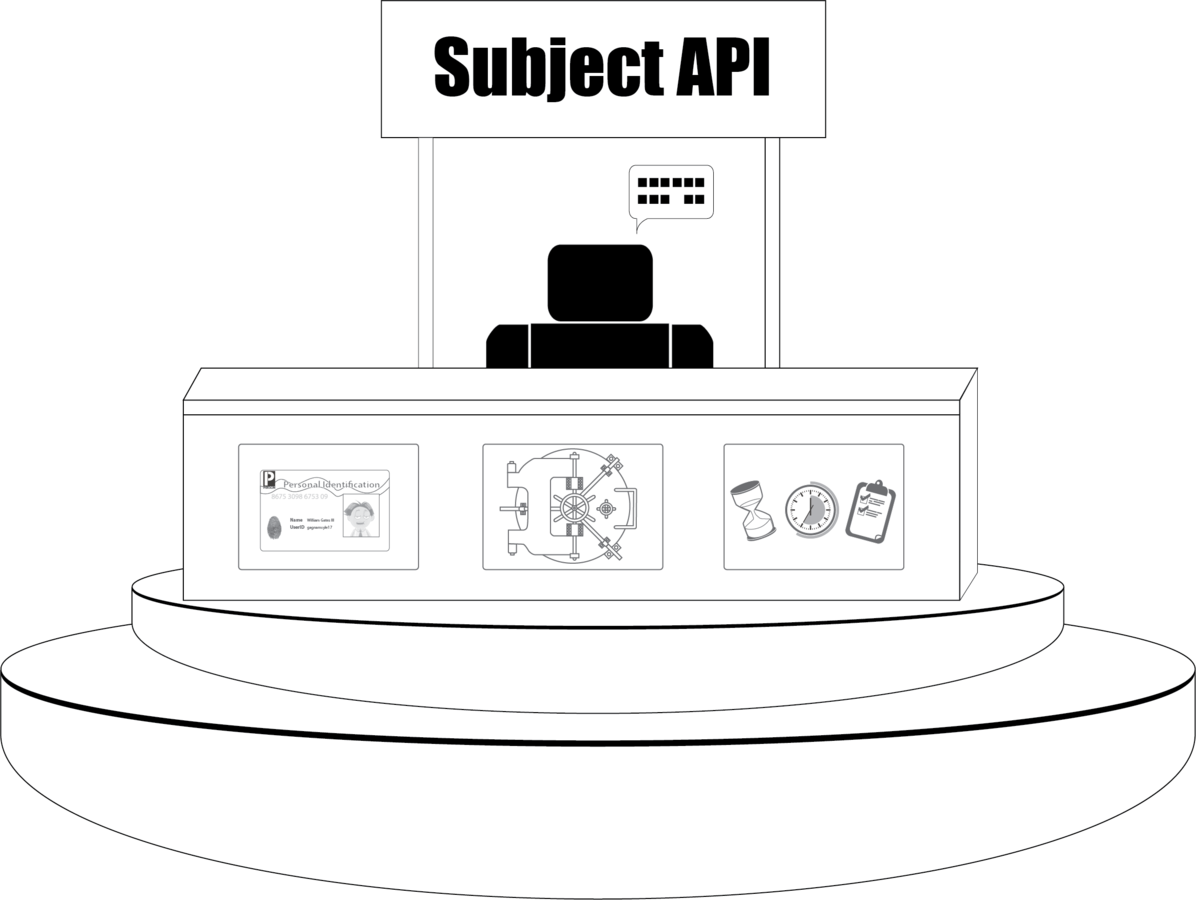
The Main API

Use to Access All
Three Services
Subject API
Interaction
subject = yosai.subject
def do_something():
print('We are doing something here!')
try:
subject.check_permission(...)
do_something()
except AuthorizationException:
print('Failed to Authorize')Option 1: Direct Interaction
Subject API
Interaction
@requires_permission(...)
def do_something():
print('We are doing something here!')
with yosai:
do_something()
Option 2: Indirect Interaction
Subject API
Main Concepts
- Secure your application using the Subject API
- Interact with the Subject API directly or indirectly
- Expect to use both methods of interaction
Authentication

proving that a subject is who it claims to be
from yosai.core import SecurityUtils, ...
# ... initialize a Security Manager here
security_manager = ...
yosai = SecurityUtils(security_manager)
realm = AccountStoreRealm('AlchemyPasswordRealm')
realm.account_store = AlchemyAccountStore()
security_manager = NativeSecurityManager(realms=(realm,),
... )
Authentication
current_user = yosai.subject
authc_token = UsernamePasswordToken(username='thedude',
credentials='letsgobowling')
try:
current_user.login(authc_token)
except AuthenticationException:
...Authentication
Authentication
Cryptographic Hashing of Passwords
Yosai uses the Passlib library
Default hashing scheme is
bcrypt_sha256
sha2-256
bcrypt
Fully configurable
Authentication
A Framework Solution
Addressing Factors of Authentication
- Something you know
- Something you have
- Something you are
Plug your authentication into
the framework
OAuth2
OpenID
OAuth1
2FA
MFA
LDAP
U2F
Kerberos
Authorization
aka Access Control

The rules and mechanisms governing how a user interacts with a system
(who can do what)
Authorization
Yosai Enables
Role Based Access Control
Many forms of access control
- Discretionary (DAC)
- Mandatory (MAC)
- Role-Based (RBAC)
- Attribute-Based (ABAC)
Hybrid forms of RBAC are common (beyond NIST specs)
RBAC Fundamentals
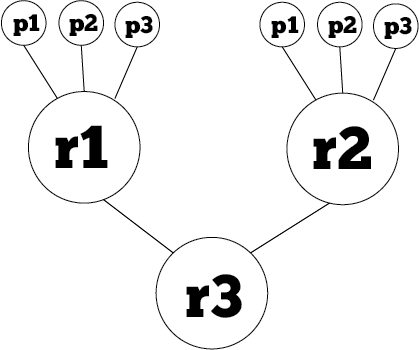
Core RBAC
Hierarchical RBAC
In Plain English
"Do This to That"
A Permission
A Role
(Group of Permissions)
Evaluates roles and permissions to answer questions:
- Is the user a member of [any, all] of these roles?
- Does the user have [any, all] of these permissions?
Authorization API
Declarative Authz
@requires_role(roleid_s=['patient'])
def request_prescription_refill(patient, prescription):
...
@requires_role(roleid_s=['cardiologist', 'nurse'], logical_operator=any)
def get_prescription_refill_requests(patient):
...
@requires_permission(['prescription:write'])
def issue_prescription(patient, prescription):
...
def fill_all_pending_prescriptions(patient):
with yosai:
for prescription in get_prescription_refill_requests(patient):
issue_prescription(patient, prescription)
Authorization API
Imperative Authz
def request_prescription_refill(patient, prescription):
...
def get_prescription_refill_requests(patient):
...
def issue_prescription(patient, prescription):
...
def fill_all_pending_prescriptions(patient):
subject = yosai.subject
subject.check_role(roleid_s=['cardiologist', 'nurse'], logical_operator=any)
subject.check_permission(['prescription:write'])
for prescription in get_prescription_refill_requests(patient):
issue_prescription(patient, prescription)
Session Management
Sessions track state
Session Management
- C.R.U.D
- Validation

Sessions and Security
- Access is limited by user identity
- Identity of authenticated user recorded in a Session
Therefore, access control is considered bound to a Session
Authc, Authz, and Sessions are Related
Advanced forms of RBAC use Sessions
Dynamic separation of duties (least privilege)
Session Facilitation
Anonymous Session created with first request
New Session created upon successful authentication
subject = yosai.subject
authc_token = UsernamePasswordToken(username='thedude',
password='letsgobowling')
subject.login(authc_token)Session API
Supports basic R.U.D. operations
Caching requires user-defined Session attributes schema
current_user = yosai.subject
session = current_user.get_session()
session.set_attribute('key', 'value')
print(session.get_attribute('key', 'value'))
session.remove_attribute('key')Session Validation
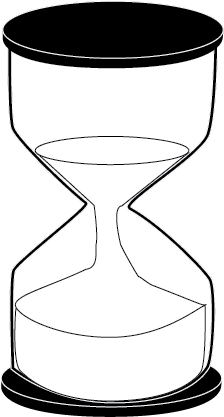

Risk of compromising a Session increases over time
Therefore, we time-out Sessions
- Idle Timeout
- Absolute Time to Live (TTL)
Session Expiration
Session validation triggers a series of cache invalidation events
- Session is cleared from cache (if caching)
- Authorization info is cleared from cache
Caching
-
Native support, throughout the framework
-
Extension available: yosai_dpcache
- Fork of dogpile projects (Bayer)
- Currently supports redis
-
Complete serialization solution
First Release: v 0.1.0
Tested.
Documented.
web site coinciding with release
Questions?
