VPC

WTF is a VPC
A virtual network dedicated to your AWS account.
It resembles a traditional network that you’d run in our own data center, with the benefits of using the AWS infrastructure.
Bare metal VPC 👉
10.0.0.0/16 | 10.0.0.0 to 10.0.255.255
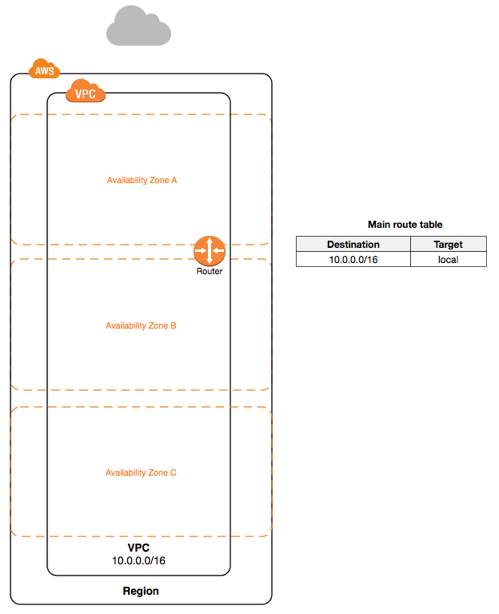
Availability Zones
Distinct locations that are engineered to be isolated from failures in other Availability Zones.
A VPC spans all of the Availability Zones in the Region. We are in US East 1 N. Virginia

Subnets
A sub network of our virtual network. Essentially a range of IP addresses in your VPC. The range will be a CIDR range that is a subset of the VPC CIDR in each availability zone.
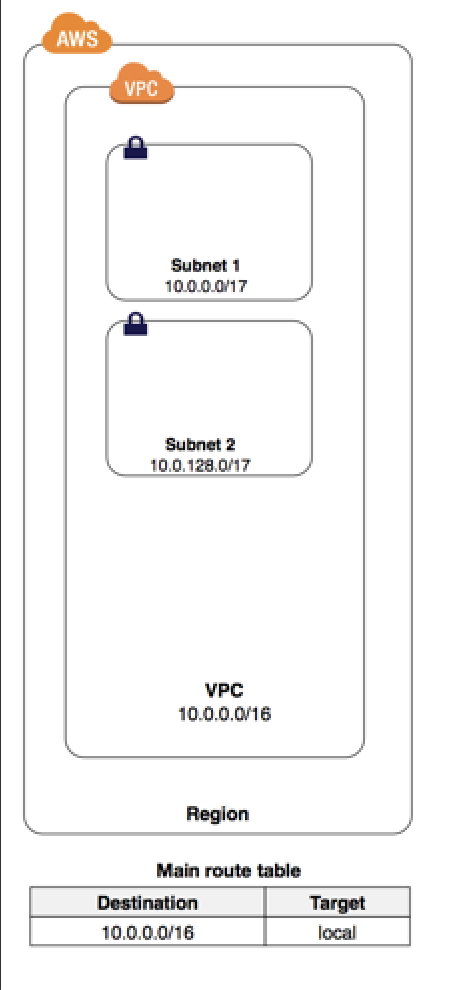
Subnets
3 Types of Subnets:

- Public - traffic is routed to an internet gateway
- Private - doesn’t have a route to the internet gateway
- VPN Only - traffic routed to a virtual private gateway for a Site-to-Site VPN connection
Route Tables
Route tables are the rules that determine where network traffic is directed, and are applied by the the implicit router that each VPC possesses.
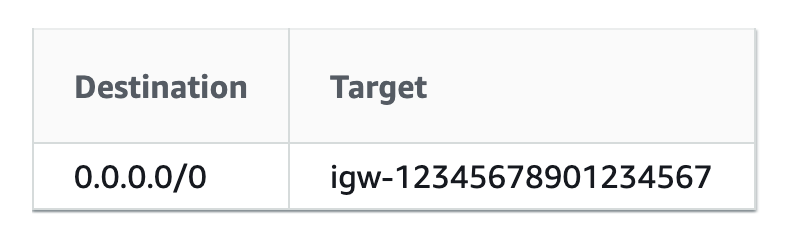
Each subnet in your VPC must be associated with a route table, which controls the routing for the subnet.
Each rule defines a destination, where the traffic is going, and a target, which is the means to get to the provided destination.
This rule sends all traffic to an internet gateway
Internet gateways
A gateway that enables internet access to and from instances in subnet of the VPC
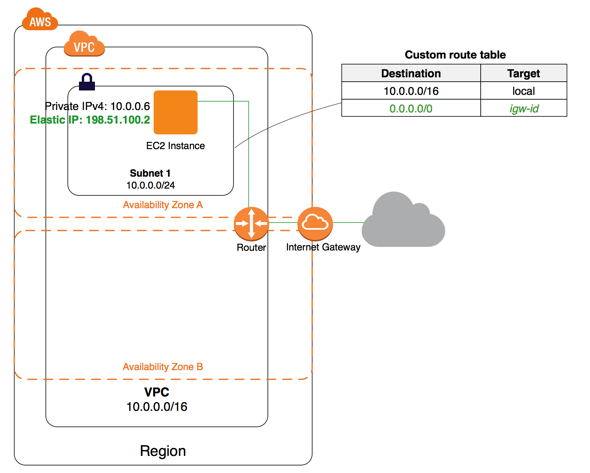
This gateway provides a target in your VPC route tables for internet-routable traffic
Additionally these gateways perform network address translation (NAT) for instances that have been assigned public IPv4 addresses.
NAt Gateway
Enables instances in a private subnet to connect to the internet or other AWS services, but prevent the internet from initiating a connection with those instances
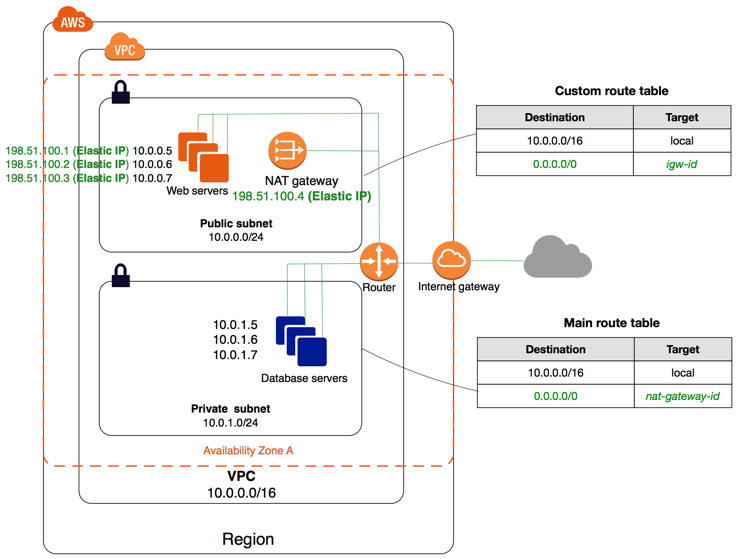
Nat Gateways must live in a public subnet
Security Groups
Are essentially firewalls
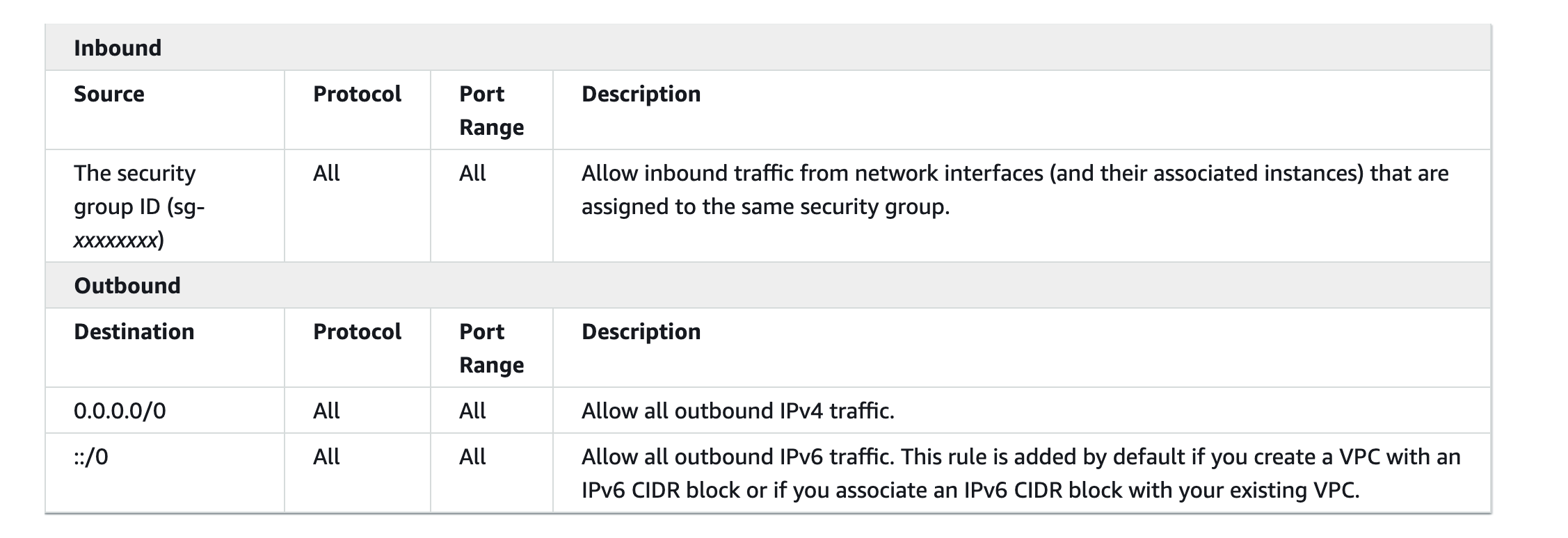
Unlike traditional firewalls they are less rigid and only allow us to specify permissive rules.
If a data packet has no particular rule that permits it to go through, it will be dropped instantly.
By default all traffic is denied.