Security issues in software defined networks
Generalised view of vulnerabilities
DoS the control layer
Flooding an edge router with purposefully crafted packets it can be possible to DoS the control plane.
Possible solution:
- controller replication
- proactive rules
Attack the switch / router
A fault in the implementation of the network forwarding element software can lead to losing control of it to the attacker
Possible solution:
- software updates
- self-healing mechanisms
- diversity

Attack the control layer API
Insecure communication can lead to evesdropping control layer messages, or worst their modification and subsequent loss of control over the network
Possible solution:
- encrypted comms
- mutual authentication

Attack the controller
The headers of a packet can be specially crafted to attack the control layer that receives the headers from a network FE that does not know what to do with the packet. Loss of controller means loss of network.
Possible solution:
- software updates
- strict header formats

Attack the applications
An implementation fault in one of the applications that create the rules can result in loss of control over that application, worst it can be used to generate rules in favor of the attacker.
Possible solution:
- rule conflict analysis
- network policies
Attack the applications
If the applications are not certified and authenticated, it could be possible to inject a malicious application that should not be there.
Possible solution:
- app-controller mutual authentication
- encrypted comms
- authorisation roles

SDN: OpenFlow perspective
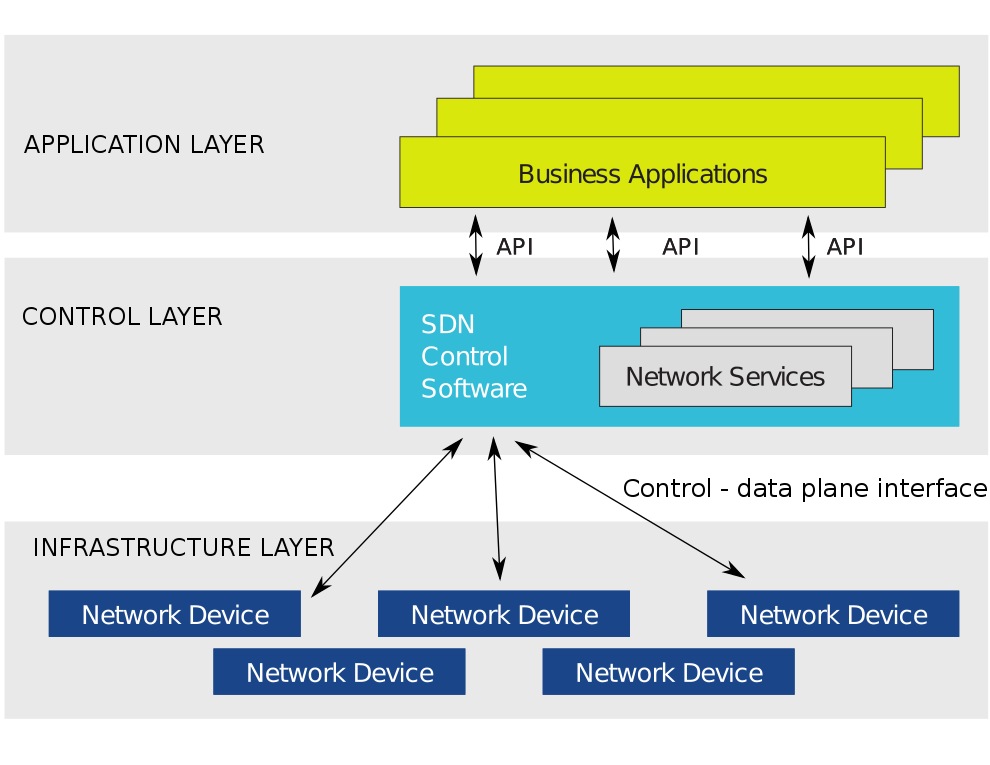
Generalised view of the network Forwarding Element
All routers and switches contain some kind of match-action based logic for packet forwarding. OpenFlow generalises the table and rules into the 'flow table'.
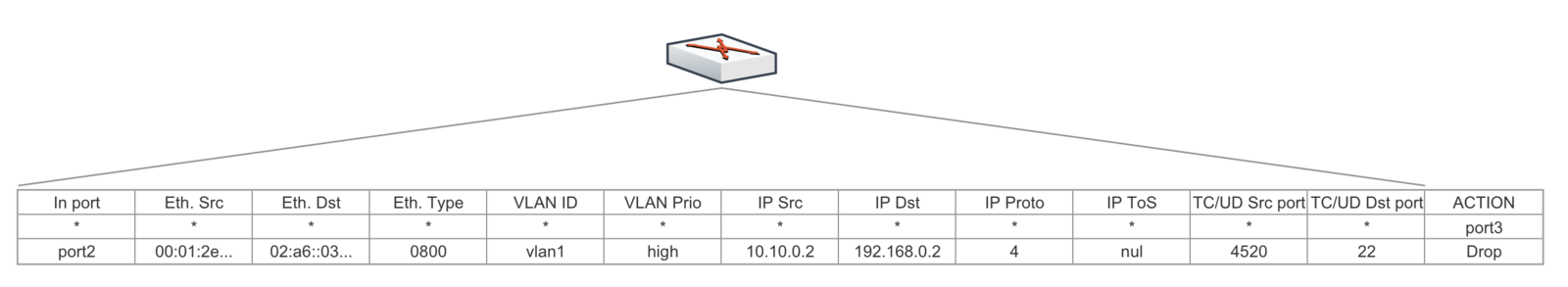
Vulnerabilities?
- DoS on the control layer
- Information disclosure
- Possibly chache poisoning
Securing the
control layer
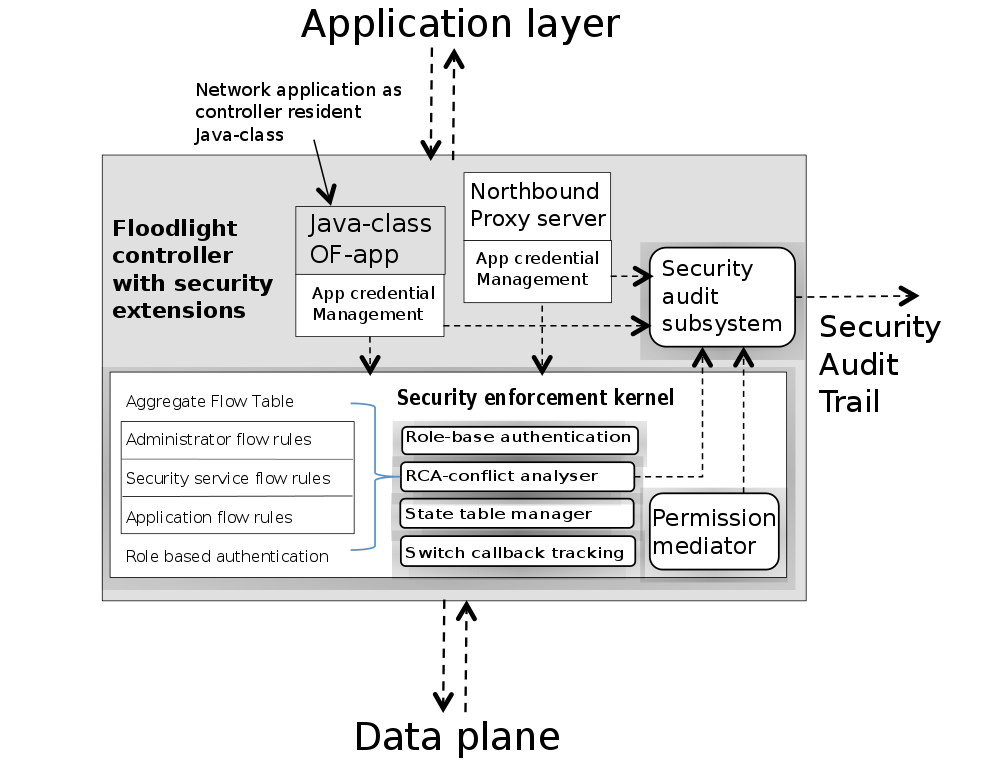
SE-Floodlight
- Security enforcement kernel (SEK)
- Authorisation roles
- Security policies
- Application authentication
- Rule Conflict Analysis
Problems:
- Single point of failure (DoS)
- Delays (Information disclosure)
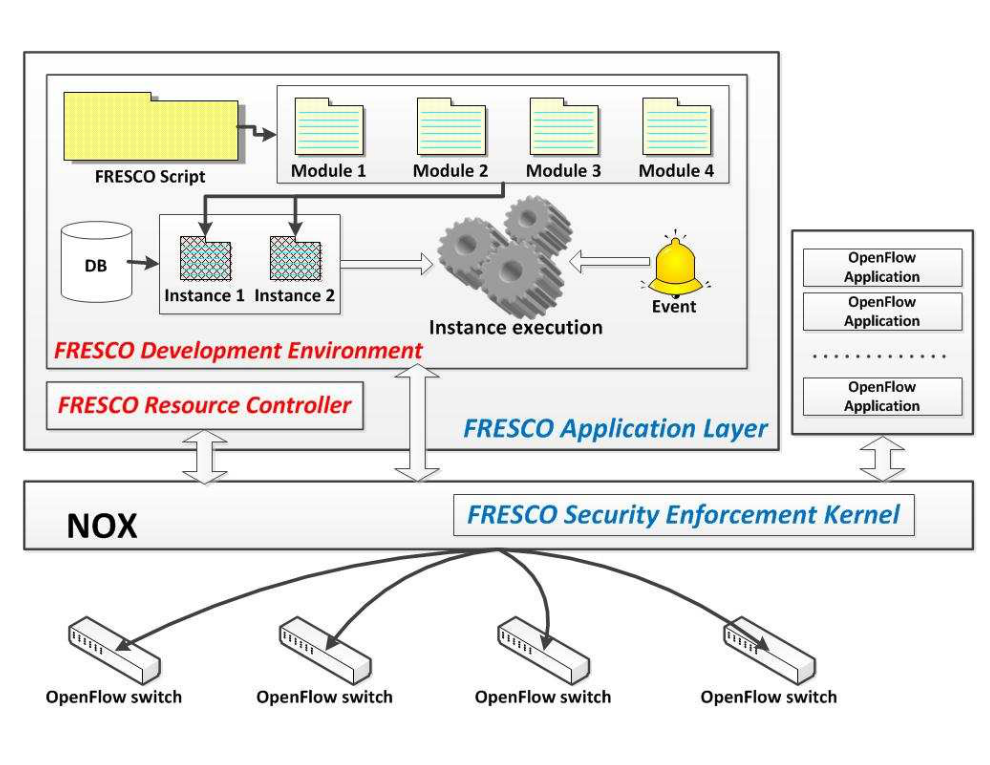
FRESCO
- Security application development framework
- SEK (FortNOX)
- Modular applications
- Application authentication
- Authorisation roles
- Security policies
- RCA
Comprehensive set of tools
Problems:
- Single point of failure (DoS)