CHANGING PILLARS OF online AUTHENTICATION

who am i?


NoT EveryONE perceives the same about us
IDENTITY = set of attributes related to an entity
(ISO 29115)


He is a singer
He has a deep warm voice
He plays the ukulele, guitar
He is the front man of Pearl Jam
He is a father
He loves baseball
He supports the Chicago Cubs





What does our digital identity say about us?
WHO IS READING THIS INFORMATION?
WHO IS STORING THIS INFORMATION?
WHAT ARE THEY DOING WITH IT?
WHAT IMPACT WILL it HAVE oN MY FUTURE?
Privacy: Getting back the control of sharing your data


Protecting Access: Authenticate in a secure way

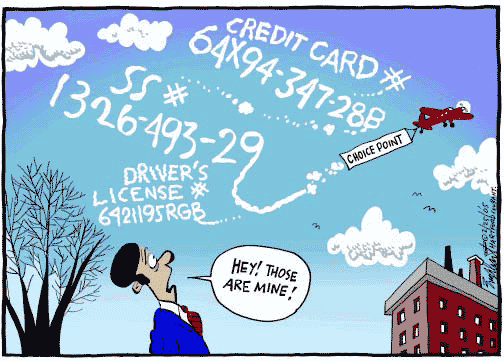
HOW DO WE COME TO HERE?
Too many passwords to remember,
difficult to type and not secure

REUSED
PHISHED
KEYLOGGED
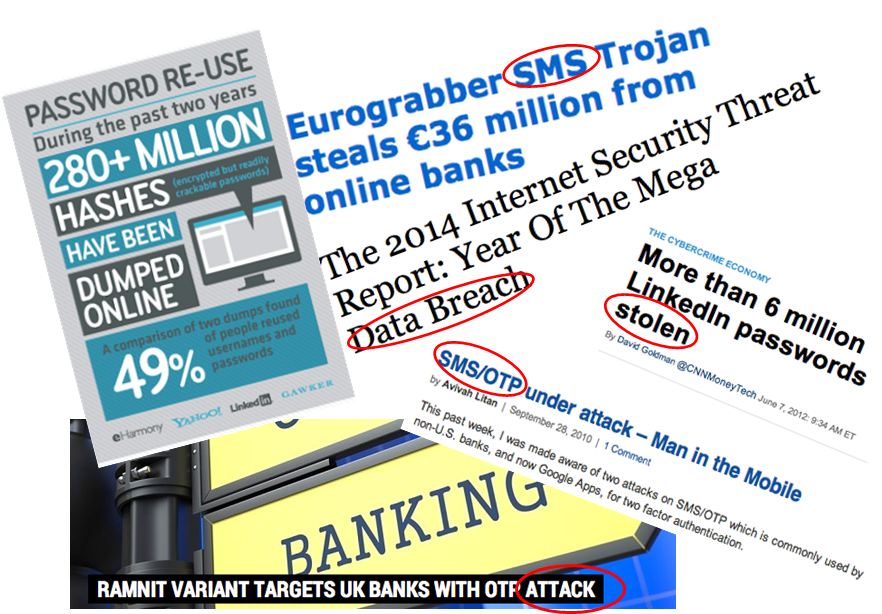
Passwords are a PROBLEM FOR USERS
Security BREACHES: A SERVICE PROVIDERS PROBLEM
REGULATORY CHANGES
-
ECB draft Recommendation on the security of mobile payments
- Ensure the security of mobile payments
- Recommendations impose proportionate authentication only on licensed financial service providers
-
eIDAS regulation
-
Mutual recognition across EU Member States
-
Replacing the existing e-Signature Directive 1993/99 covering authentication, identification and e-signature
-


¡ATTRIBUTE SHARING!
- We could provide a verified identity
- Banks need mechanism to improve the onboarding process
- Need to check the physical identity of the user
- This slows down the time to have the new product available
- A lot of times the user drops out the process in the meantime
authenticators
CURRENT AVAILABLE AUTHENTICATORS HAVE DRAWBACKS
-
User/password
-
SMS OTPs
-
Code cards
-
PKI based solutions
-
. . .
What OTHERS DO


FIDO ALLIANCE BOARD
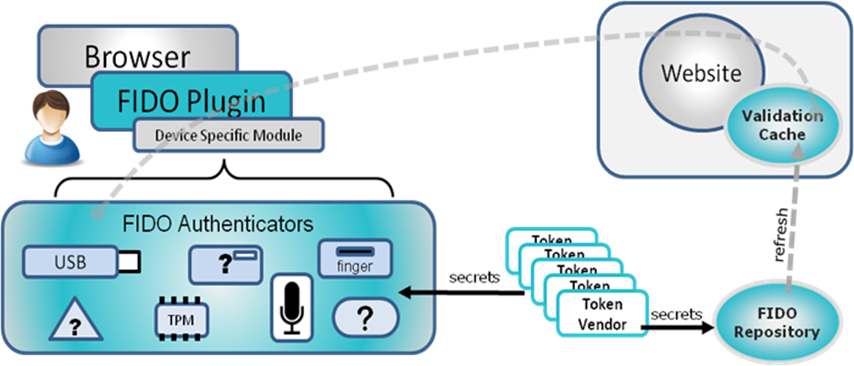
FIDO ALLIANCE BASIC ARCHITECTURE
PROPRIETARY SOLUTIONS

WHAT WE TRY TO DO
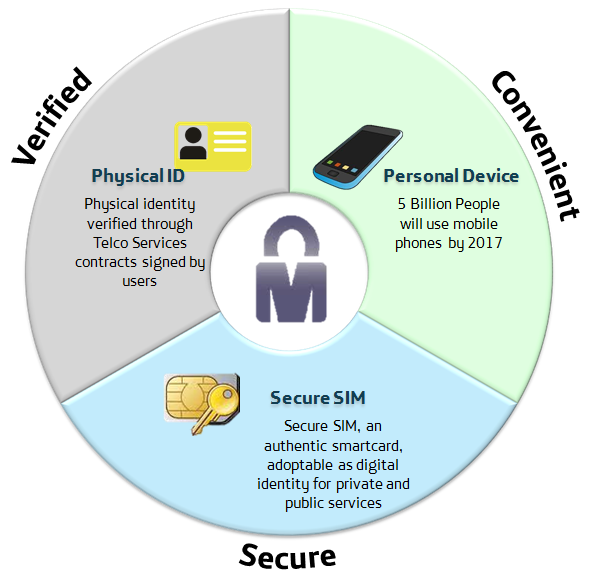
GSMA MOBILE CONNECT

IDENTITY SERVICES BASED ON MNO ASSETS
mobile connect
ARcHITECTURE GUIDELINES
-
Plugable authenticators
-
Standard definition of LoA (Level of Assurance)
-
OpenID Connect, as the interface with the service providers
-
Authenticator selected based on the LoA requested
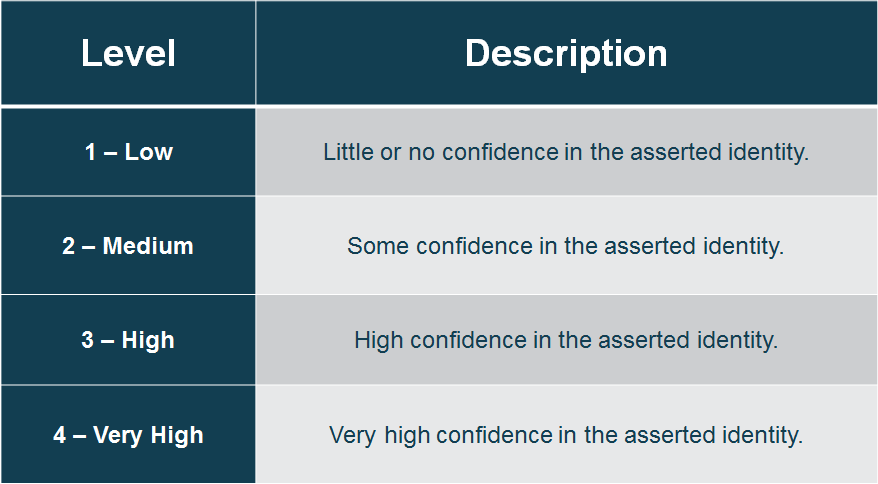
Level OF ASSURANCE (ISO/IEC 29115)
What the mobile connect is about?
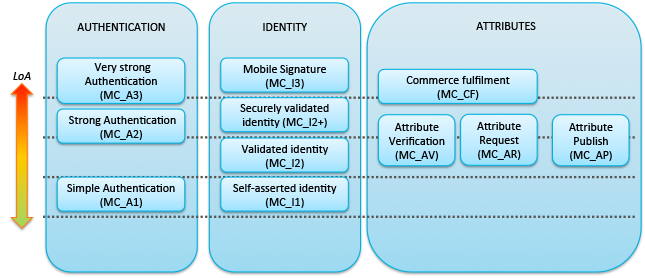
mobile connect
ARCHITECTURE
logical components
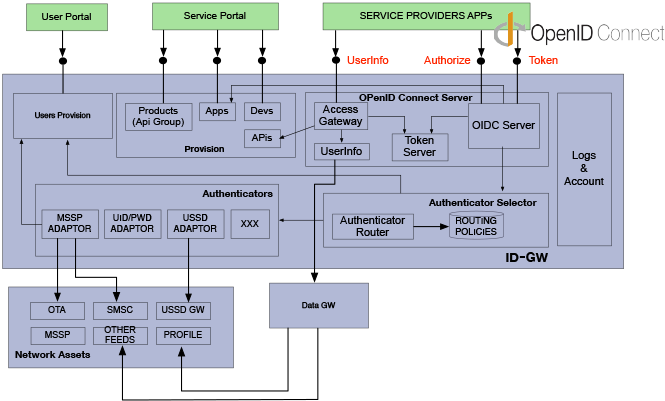

Identity Layer on Top of OAuth 2.0

INTEROPERABLE
- Standard scopes: openid, profile, email, address, phone
- Standard UserInfo endpoint and Indiviual Claims (granularity)
- Id_token: info about the authenticated user

SIMPLE
- JSON based & REST Friendly

SECURE
- Scale thanks to LoA (ISO/IEC 29115 Entity Authentication Assurance)
- Encryption
THE IDENTITY LAYER
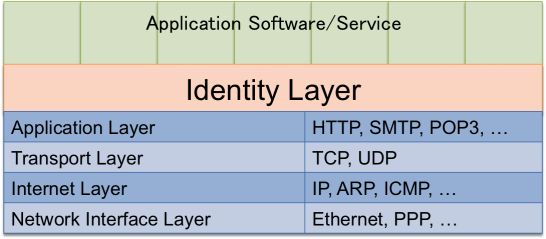
http://nat.sakimura.org/2014/02/26/openid-connect-is-here/
Helps Mobile Connect to be Interoperable
Boost the Separation of Concerns

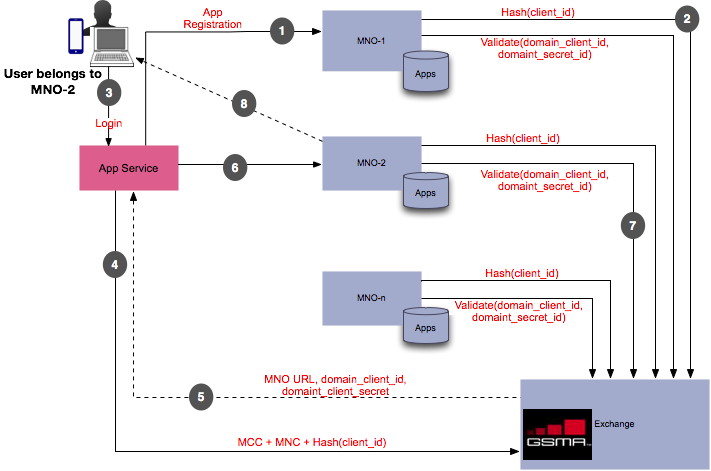
CURRENT DISCOVERY process
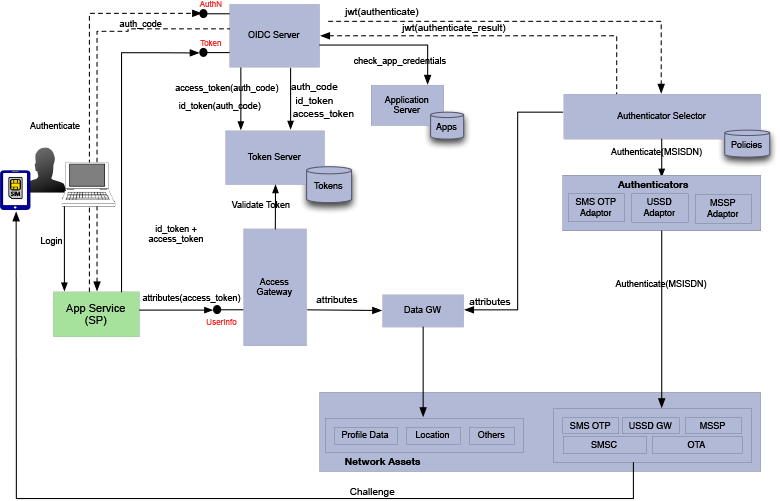
logical components: interaction
HTTP/1.1 302 Found
Location: https://server.example.com/authorize?
response_type=code
&client_id=s6BhdRkqt3
&redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb
&scope=openid%20profile
&state=af0ifjsldkjGET /authorize?
response_type=code
&client_id=s6BhdRkqt3
&redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb
&scope=openid%20profile
&state=af0ifjsldkj HTTP/1.1
Host: server.example.comHTTP/1.1 302 Found
Location: https://client.example.org/cb?
code=SplxlOBeZQQYbYS6WxSbIA
&state=af0ifjsldkjHTTP 302 redirect response sent by the Client to the UA
Authentication Request sent by the UA to the Authorization Endpoint
End-user Authentication: a challenge is sent to the user's SIM applet

After obtaining the user consent a response with the auth_code is sent back to the user
AUTHENTICATION request
POST /token HTTP/1.1
Host: server.example.com
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW
Content-Type: application/x-www-form-urlencoded
grant_type=authorization_code&code=SplxlOBeZQQYbYS6WxSbIA
&redirect_uri=https%3A%2F%2Fclient%2Eexample%2Ecom%2Fcb HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"access_token": "SlAV32hkKG",
"token_type": "Bearer",
"refresh_token": "8xLOxBtZp8",
"expires_in": 3600,
"id_token": "eyJhbGciOiJSUzI1NiIsImtpZCI6IjFlOWdkazcifQ.ewogImlzc
yI6ICJodHRwOi8vc2VydmVyLmV4YW1wbGUuY29tIiwKICJzdWIiOiAiMjQ4Mjg5
NzYxMDAxIiwKICJhdWQiOiAiczZCaGRSa3F0MyIsCiAibm9uY2UiOiAibi0wUzZ
fV3pBMk1qIiwKICJleHAiOiAxMzExMjgxOTcwLAogImlhdCI6IDEzMTEyODA5Nz
AKfQ.ggW8hZ1EuVLuxNuuIJKX_V8a_OMXzR0EHR9R6jgdqrOOF4daGU96Sr_P6q
Jp6IcmD3HP99Obi1PRs-cwh3LO-p146waJ8IhehcwL7F09JdijmBqkvPeB2T9CJ
NqeGpe-gccMg4vfKjkM8FcGvnzZUN4_KSP0aAp1tOJ1zZwgjxqGByKHiOtX7Tpd
QyHE5lcMiKPXfEIQILVq0pc_E2DzL7emopWoaoZTF_m0_N0YzFC6g6EJbOEoRoS
K5hoDalrcvRYLSrQAZZKflyuVCyixEoV9GfNQC3_osjzw2PAithfubEEBLuVVk4
XUVrWOLrLl0nx7RkKU8NXNHq-rvKMzqg"
}Client makes a Token Request by presenting its Authorization Grant
If code is validated successfully then Client receives Tokens
HTTP/1.1 400 Bad Request
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"error": "invalid_request"
}Error Response
TOKENS





Attribute Verification
Attribute Request
AntiFraud
Contextual-setup Authentication
Commerce Fullfilment
the attributes enhance digital transactions
Objective: Provide a selection of attributes and attribute verification services
{
"iss": "http://mobileconnect.tid.es",
"sub": "as7654098289126",
"aud": "z3GdrS2Qbs",
"nonce": "n-0S6_WzA2Mj",
"exp": 1311281970,
"iat": 1311280970,
"acr": "urn:mace:incommon:iap:gold",
"amr": ["password", "SIM-PIN-Applet"],
"name": "Gonzalo Fernández",
"given_name": "Gonzalo",
"family_name": "Fernández",
"gender": "male",
"birthdate": "1971-09-28",
"email": "gfr@tid.es",
"picture": "http://mobileconnect.tid.es/gfr/me.jpg"
}HTTP/1.1 302 Found
Location: https://mobileconnect.tid.es/authorize?
response_type=code
&client_id=z3GdrS2Qbs
&redirect_uri=https%3A%2F%2Fcollosus.bank.tid.es%2Fcb
&scope=openid%20profile
&acr_values=urn:mace:incommon:iap:gold urn:mace:incommon:iap:silver
&state=gd0ai2mqzptInitial Authentication Request
Id_Token: control claims + acr value + personal data
id_token
UserInfo endpoint
GET /userinfo HTTP/1.1
Host: server.example.com
Authorization: Bearer SlAV32hkKGHTTP/1.1 200 OK
Content-Type: application/json
{
"sub": "248289761001",
"name": "Jane Doe",
"given_name": "Jane",
"family_name": "Doe",
"preferred_username": "j.doe",
"email": "janedoe@example.com",
"picture": "http://example.com/janedoe/me.jpg"
}INDIVIDUAL CLAIMS
{
"userinfo":
{
"given_name": {"essential": true},
"nickname": null,
"email": {"essential": true},
"email_verified": {"essential": true},
"picture": null,
"http://example.info/claims/groups": null
},
"id_token":
{
"auth_time": {"essential": true},
"acr": {"values": ["urn:mace:incommon:iap:silver"] }
}
}MOBILE CONNECT
SIM BASED AUTHENTICATOR
SIM BASED AUTHENTICATOR
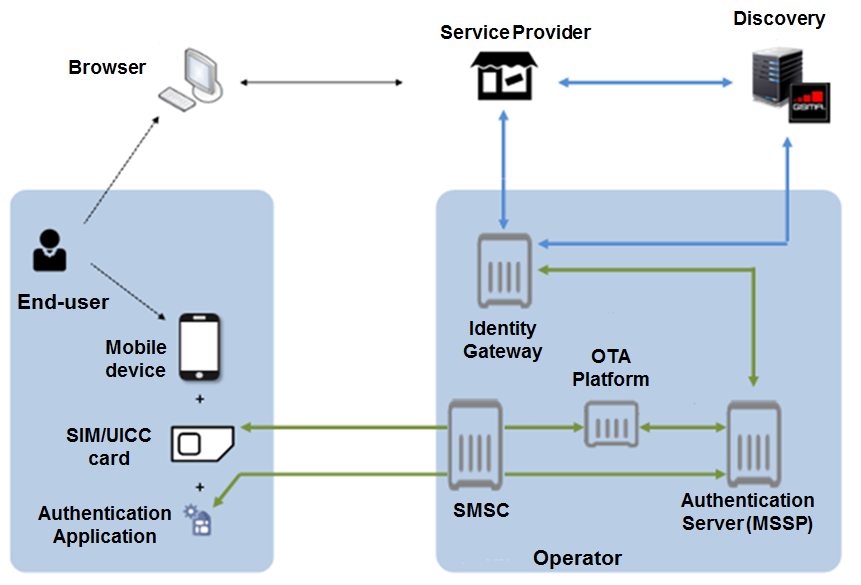
MSSP: Mobile Signature Service Provider
-
Authentication server based on ETSI TS 102 204
-
Northbound Interface is based on web services, allows to the ID Gateway to send auth request independtly of the underlying authenticators
-
Southbound interface connect with the authenticators, isn't specified
-
-
Mobile Connect defines the southbound interface to talk with the SIM authentication application
THE SIM IS A SEcURE ELEMENT
- Tamper-resistant platform
- you need the keys to access the system.
-
Connected directly to baseband (OTA secure channel)
-
Includes a framework to run applications (JavaCard)
-
Very limited subset of Java
-
Remotely deployable applications, called applets
-
SimToolKit
-
allows to create text based user interfaces
-
compatible with almost any existing mobile phone
-
-

Mobile CoNNECT APPLET
-
Two user journeys:
-
Click OK -> LoA 2
-
Insert Personal Code -> LoA3
-
-
Several authenticator handlers
-
3DES
-
AES
-
OATH OCRA
-
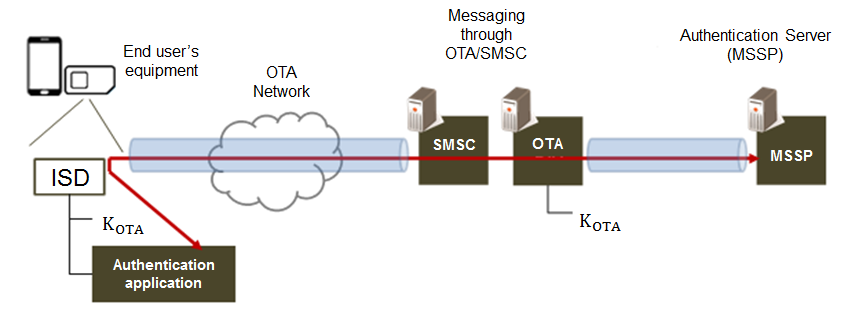
COMMUNICATIONS ThROUGH OTA
COMUNICATIONS WITHOUT OTA
