API Insecurities
Silvia Puglisi - @nopressure
Hello World
My name is Silvia Puglisi. I am a software engineer and Ph.D. candidate at UPC Barcelona Tech.
I research in privacy and web science.
A web of data
In 2011, the amount of digital information created and replicated globally exceeded 1.8 zettabytes (1.8 trillion gigabytes).
75% of this information is created by individuals.
By the end of 2011, Facebook had 845 million monthly active users, sharing over 30 billion pieces of content.
Library Briefing - Library of the European Parliament - 01/03/2012

Applications and services today aim to build a sense of serendipitous discovery of people, places and interests.

Applications exchange user data through REST interfaces (most of the times) in the form of hypermedia representations of resources identified by URIs
Unfortunately Applications are not built with user security and privacy at heart.
API Insecurities
A number of privacy violations and threats can be easily spotted by looking at API calls made by devices through a simple proxy.
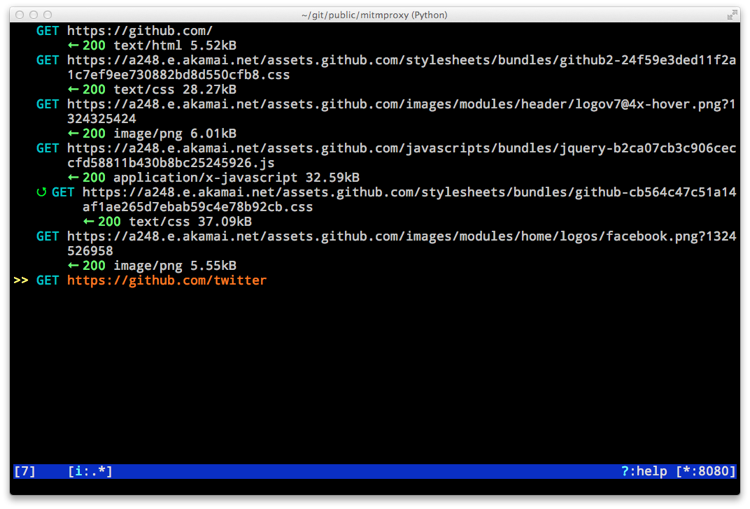
MITMProxy: An interactive console program allowing traffic flows to be intercepted, inspected, modified and replayed.
Let's see how this work in practice..
Classifying violations
- Collection
- Processing
- Dissemination
- Invasion
[1] D. J. Solove, “A taxonomy of privacy,” University of Pennsylvania law review, pp. 477–564, 2006.
Collection
Surveillance, interrogation or information probing.
Watching, reading, listening, recording of individual.
Inference of information
regarding individuals
Processing
Aggregation and identification of data.
Failure to provide data security.
Secondary use of data to which the user has not been informed.
Dissemination
Breach of confidentiality, unwanted disclosure and exposure of information.
Appropriation and distortion of data about people.
Invasion
Invasion is the threat of intrusion of an entity into someone’s private life and it includes acts that are said to disturb one’s tranquillity or solitude.

API Security
- Is a matter of technological hygiene
- Should be consider a product feature
- Neglecting it could destroy your product*
