Ephemeral Onions
Decentralized transitory Uses of the
network
hiro@torproject.org
https://mastodon.social/@nopressure
https://twitter.com/nopressure

Hi! 👋

Hi, I am silvia..
- Some known me as Hiro.
- I work at the Tor Project.
- I am also part of the Information Security Group in the Department of Telematics Engineering at UPC-Barcelona where I got my Ph.D.

Let's talk about anonymity .
I am going to tell you a short story ...

What is and
what it can do for you

Tor is a privacy tool
- Tor is free software.
- Tor is a community made up of a diverse group of developers, researchers, relay operators, volunteers.
- Tor is an open network.
- Tor is a non-profit.

What does Tor do?
- Tor provides privacy.
- Tor provides anonymity.
- Tor provides communication security.
- Tor provides a traffic analysis resistant communication network.
- Tor provides reachability against censorship.

How does provide Privacy and Anonymity?

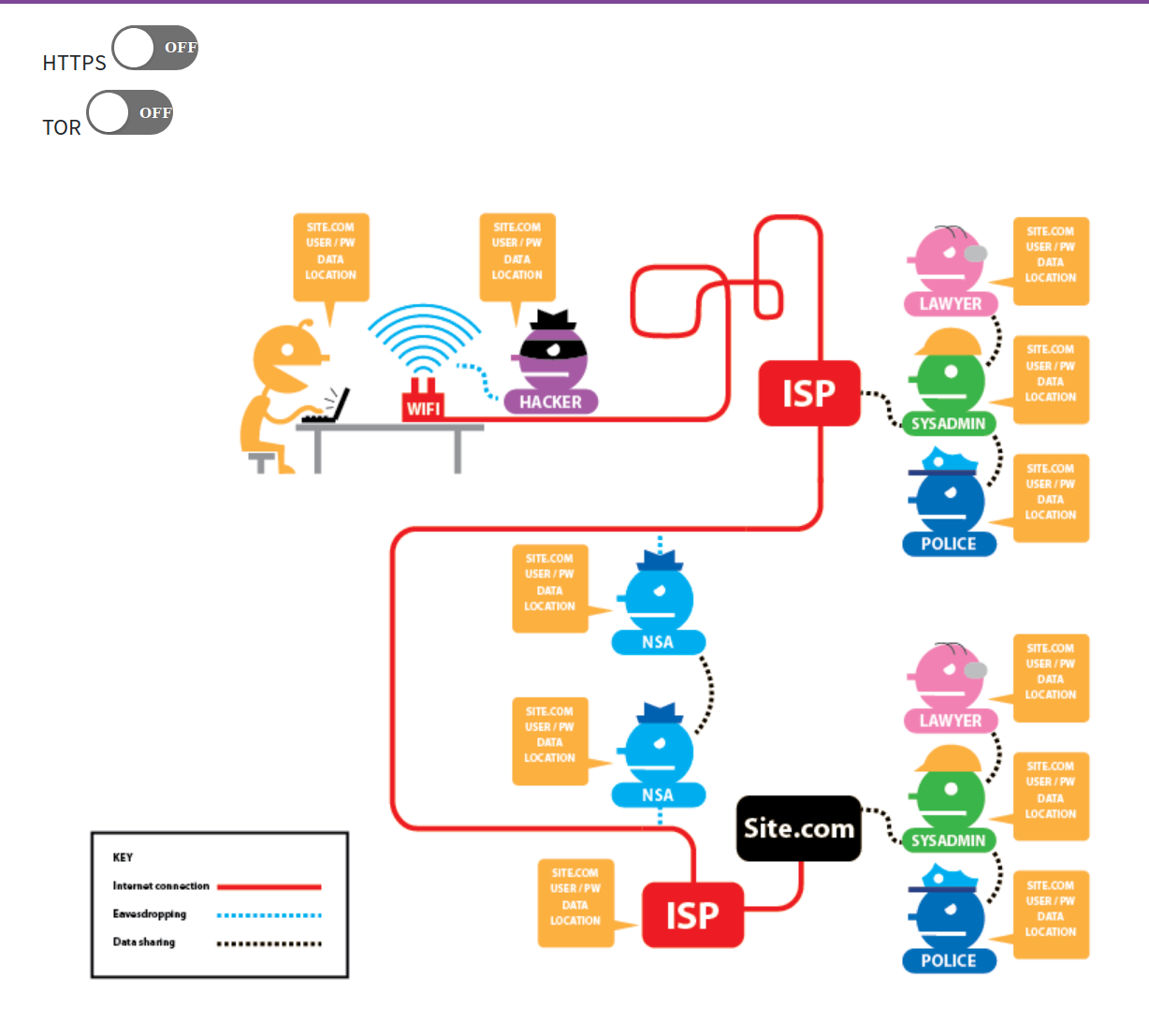
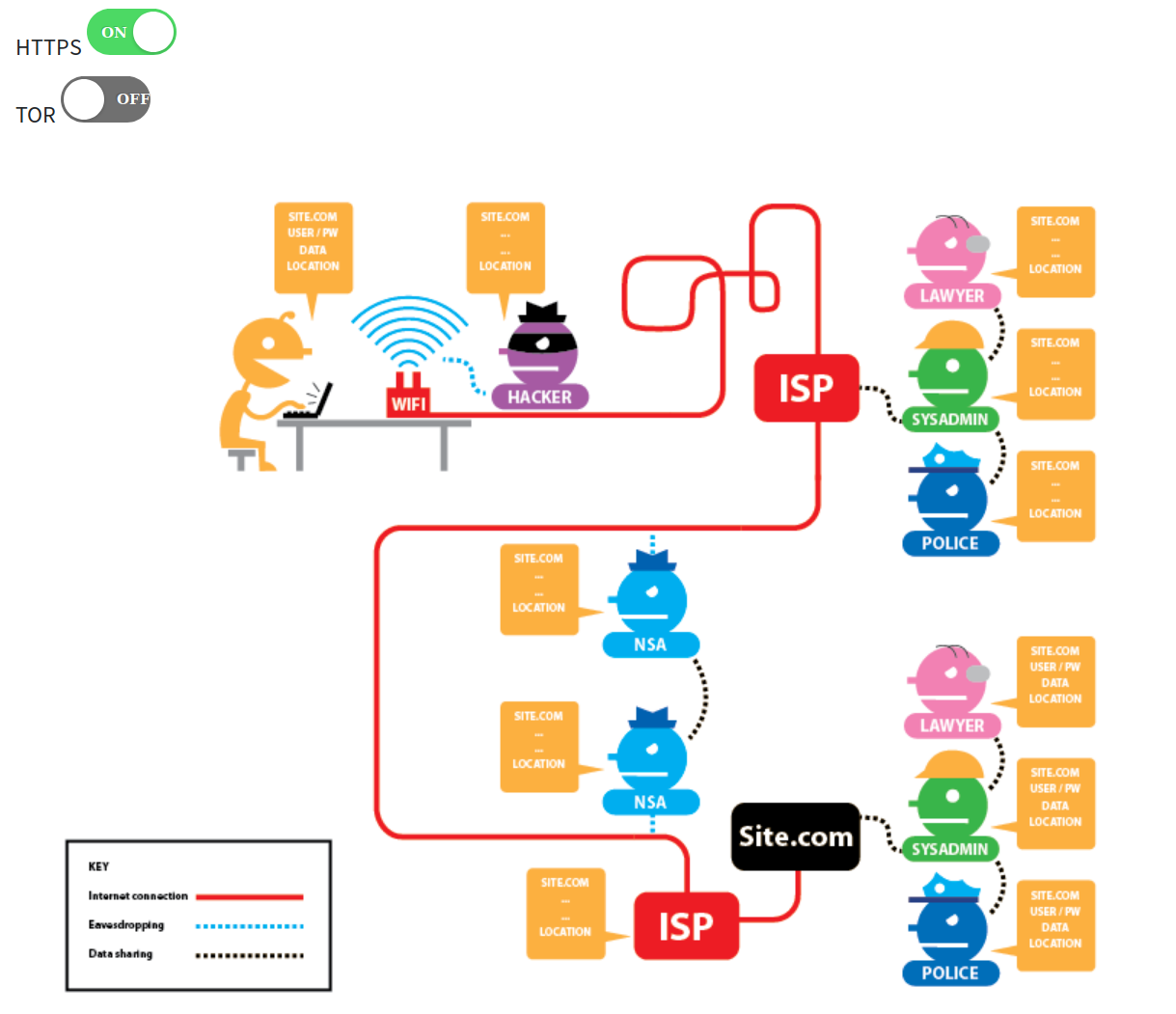
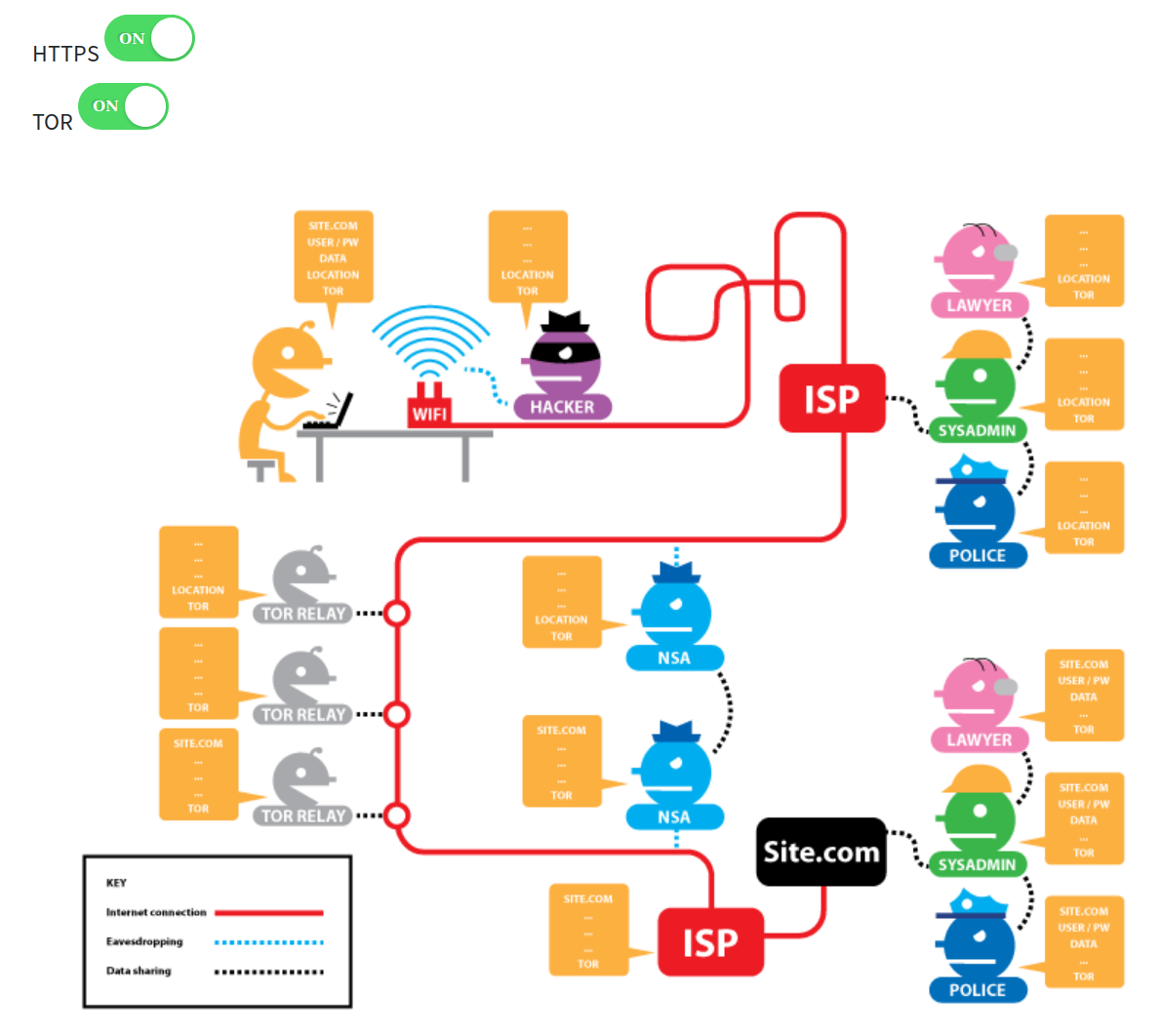
Privacy by design
Tor provides privacy by distributing TRUST


Privacy by design
When you use a VPN you are trusting a single node

🖥️
💻
Alice
bob.com
Privacy by design
When you use a VPN you are trusting a single node

💻
Alice
bob.com
👾
👾
👾
🖥️
How Tor works
Alice wants to talk to some Bob. Alice also wants to stay safe.
💻
Alice's Tor client obtains a list of Tor nodes from a directory server and picks a random path to destination server.
Alice
bob.com
DS
🖥️
🖥️
🖥️
🖥️
How Tor works
How does it work in practice?
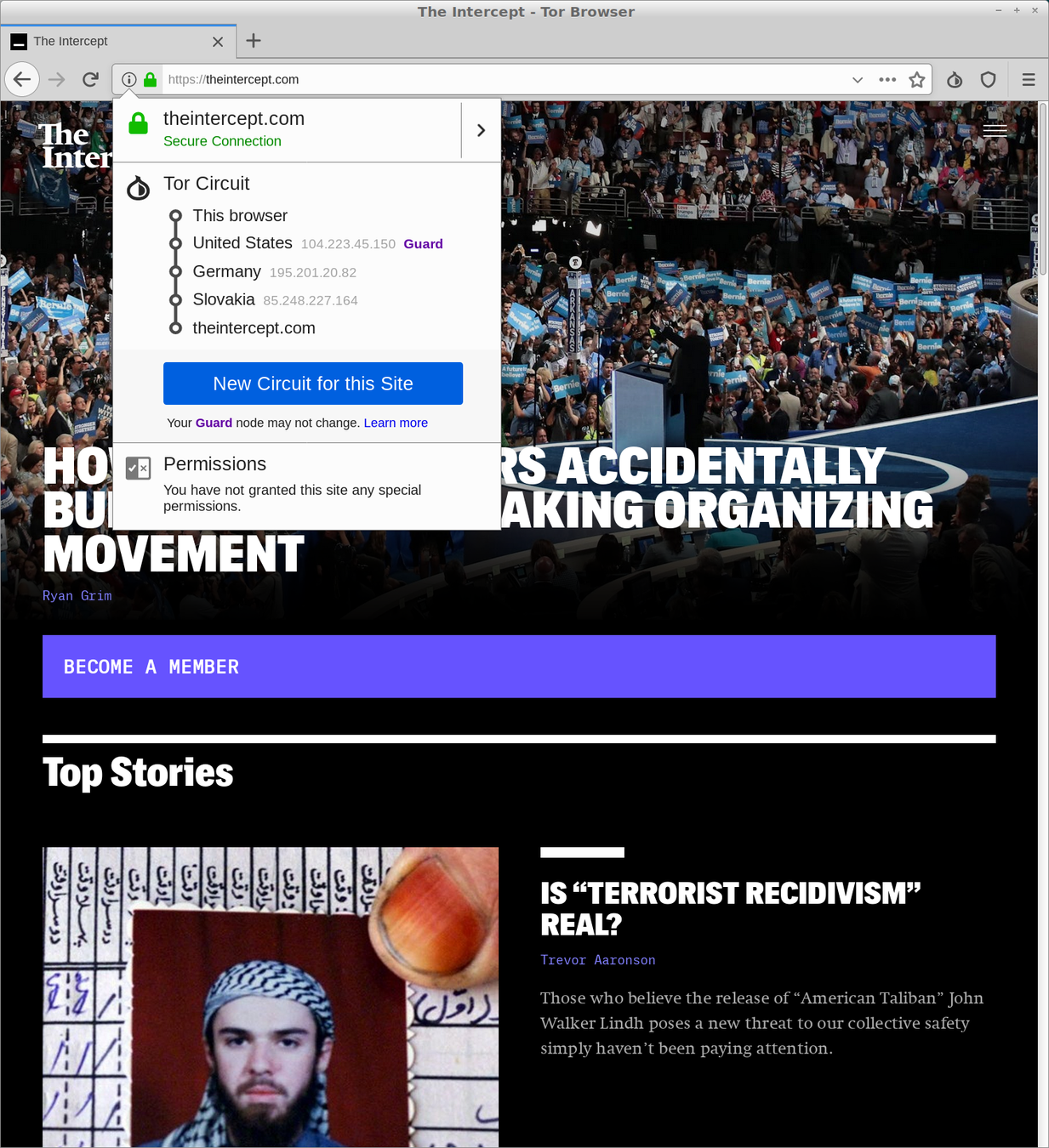
How Tor works
How does it work in practice?
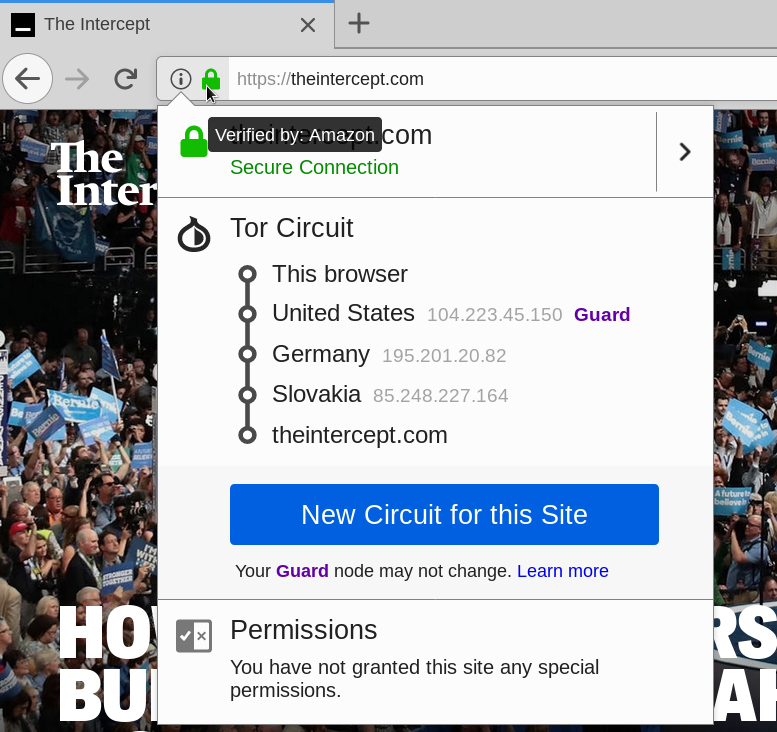
Anonymity > Encryption
Anonymity > Encryption
- Encryption doesn't hide conversations metadata
- how long you talk, how often ...
- Encryption doesn't hide your social graph
- the people you talk to ...
- Encryption doesn't hide network metadata
- network addresses, traffic patterns ...
- Encryption doesn't hide your location
- location services, geo-coding ...
Using at the app layer:
Tor Browser

What is Tor Browser
Tor Browser is a modified Firefox ESR.
Tor Browser Packages:
-
Tor, Torbutton,
-
TorLauncher,
-
NoScript,
-
and HTTPS-Everywhere.
Why Tor makes a browser
Tor browser is designed to:
- Ensure the safe use of Tor.
- Reduce linkability of user activities on different websites.

Onion Services
Providing bidirectional anonymity
Onion Services
-
Onion services can be started from your computer
-
Onion services are p2p
-
Onion services are decentralised
-
Onion services have a smaller attack surface
-
Onion services provide by-directional anonymity
-
Onion services addresses are 54 chars public keys [ed|curve25519 - Keccak(SHA3)]

Bob is an onion service and Alice a Tor Browser user.
Bob picks 3 introduction points and builds a circuit.
💻
Alice
bob.onion
Bob picks some introduction points and builds a circuit to them...
🖥️
🖥️
🖥️
How Onion Services work
Bob builds a descriptor and uploads it to the directory
Bob picks some introduction points and builds a circuit to them, then advertises its service at the database...
DS
💻
Alice
bob.onion
🖥️
🖥️
🖥️
🖥️
How Onion Services work
Alice fetches the descriptor from the directory and learns how to reach Bob.
Alice hears that bob.onion exists and they request more info from the database. They also setup a rendezvous point.
DS
💻
Alice
bob.onion
🖥️
🖥️
🖥️
🖥️
How Onion Services work
Alice tells Bob to meet her at the rendezvous point.
Alice writes a message to Bob listing the rendezvous point and a one time secret, and asks an introduction point to deliver it to Bob.
💻
Alice
bob.onion
🖥️
🖥️
🖥️
How Onion Services work
Bob connects to Alice's rendezvous point and provides their one-time secret.
💻
Alice
bob.onion
🖥️
🖥️
🖥️
How Onion Services work
Both Alice and Bob connect with a 3 hops circuit to the RP.
Bob and Alice use their circuit normally.


💻
Alice
bob.onion
🖥️
🖥️
🖥️
Using Tor within other applications through onion services.
Tor ecosystem


SSH onion-services
ssh:
container_name: onion_ssh
hostname: onion_ssh
build: ${PWD}/config/ssh
command: /home/root/init.sh
volumes:
- ./config/ssh/tor/torrc:/etc/tor/torrc
- ./config/ssh/keys/:/home/root/.ssh/keys
- ./config/ssh/init.sh:/home/root/init.sh
- ./config/ssh/sshd_config:/home/root/.ssh/ssh/sshd_config
ports:
- "2222:22"FROM debian
MAINTAINER hiro <hiro@torproject.org>
RUN apt-get update
RUN apt-get install -y sudo vim openssh-server tor
USER root
RUN mkdir -p 700 /home/root/.ssh \
&& mkdir /var/run/sshd \
&& mv /etc/ssh /home/root/.ssh/ssh \
&& ln -s /home/root/.ssh/ssh /etc/ssh
WORKDIR /home/root
VOLUME /home/root
EXPOSE 22SSH onion-services
## /etc/torcc
##
############### This section is just for location-hidden services ###
## Once you have configured a hidden service, you can look at the
## contents of the file ".../hidden_service/hostname" for the address
## to tell people.
##
## HiddenServicePort x y:z says to redirect requests on port x to the
## address y:z.
HiddenServiceDir /home/tor/onion_ssh_service/
HiddenServicePort 22 127.0.0.1:22TorSOCKS
$ torsocks ssh hiro@yjuwkcxlgo7f7o6s.onion
$ torsocks curl http://yjuwkcxlgo7f7o6s.onion/
- Torsocks is a wrapper use applications through the Tor network
- In this example, we run curl through the tor network and reach the onion address for archive.torproject.org
- We have a how-to torify apps [WIP]
Using the Socks5 Proxy
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import requests
proxies = {
'http': 'socks5://127.0.0.1:9050',
'https': 'socks5://127.0.0.1:9050'
}
r = requests.get('http://yjuwkcxlgo7f7o6s.onion/', proxies=proxies)
- We can use the SOCKS5 proxy provided by tor
- In this example, we fetch archive.torproject.org via its onion address

Onions for the
decentralised weB
Onion services can also be used for p2p applications:
-
OnionShare is a file sharing app that works by starting a web server, making it accessible as a Tor Onion Service, and generating an unguessable URL to access and download the files.
- https://onionshare.org
NEXT STEP
Use Onionshare to share static websites.
Onions for the
decentralised weB
MyOnion is a proof of concept to run onion services into docker containers from your command line, via cli, or more simply via gui.
This project explore the idea of running ephemeral onion services on the Tor network.
https://github.com/hiromipaw/myonion/
NEXT STEP
Start a container from any device and share any kind of service and make this as easy as opening an app!
Onions for the
decentralised weB
api_client = docker.APIClient(base_url='unix://var/run/docker.sock')
client = docker.from_env()
build = [line for line in
api_client.build(
path=self.common.get_resource_path('containers/website'), tag='website', dockerfile='./Dockerfile'
)
]
container = client.containers.run('website:latest', detach=True)
Onions for the
decentralised weB
FROM debian
RUN \
apt-get update && \
apt-get install -y nginx tor && \
rm -rf /var/lib/apt/lists/* && \
echo "\ndaemon off;" >> /etc/nginx/nginx.conf && \
chown -R www-data:www-data /var/lib/nginx
COPY tor/torrc /etc/tor
COPY default /etc/nginx/sites-available/
...
Onions for the
decentralised weB
Because .onion services live on the Tor network, you do not need hosting or a public ip address to offer some service via .onion address.
This means .onion services are a gateway to a decentralised, peer-to-peer internet, where you regain control on the content you create and who you are sharing it with.
Onions for the
decentralised weB
The .onion is hosted on your computer for the time you desire, allowing the people visiting your site to remain anonymous, and also you.
We believe anonymity to be very important since it can free people, allowing them to decide how to expose themselves or to make themselves visible on their own terms.
When our privacy is stolen, so is our right to control our own narrative...
The End of Trust - McSweeney's 54
Learn more...
- www.torproject.org
- Tor Browser design doc
- Mozilla Firefox Extended Support Release
- Tor Projects
- Tor Rendezvous Specification - Version 3
- Secure Messaging with Onion Services, a How-To