How To Use Tor
And what Can do for you

Hi! 👋

Tor is a privacy tool
- Tor is free software.
- Tor is a community made up of a diverse group of developers, researchers, relay operators, volunteers.
- Tor is an open network.
- Tor is a non-profit.

How does provide Privacy and Anonymity?

Privacy by design
Tor provides privacy by distributing TRUST


Privacy by design
When you use a VPN you are trusting a single node

🖳
💻
Alice
Privacy by design
When you use a VPN you are trusting a single node

🖳
💻
Alice
👾
👾
👾
How Tor works
Alice wants to talk to some Bob. Alice also wants to stay safe.
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
🖳
Alice's Tor client obtains a list of Tor nodes from a directory server and picks a random path to destination server.
Alice
bob.com
DS
How Tor works
The connection between Alice and the tor network is encrypted. The connection between the last exit node and Jane is not.
That's why it is important to use HTTPS!
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice's Tor client peaks another random path to destination server.
Alice
jane.info
How Tor works
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
The first node in the circuit is called guard. It is a fast and stable relay that remains the first one in your circuit for 2-3 months in order to protect against a known anonymity-breaking attack.
Alice
jane.info
How Tor works
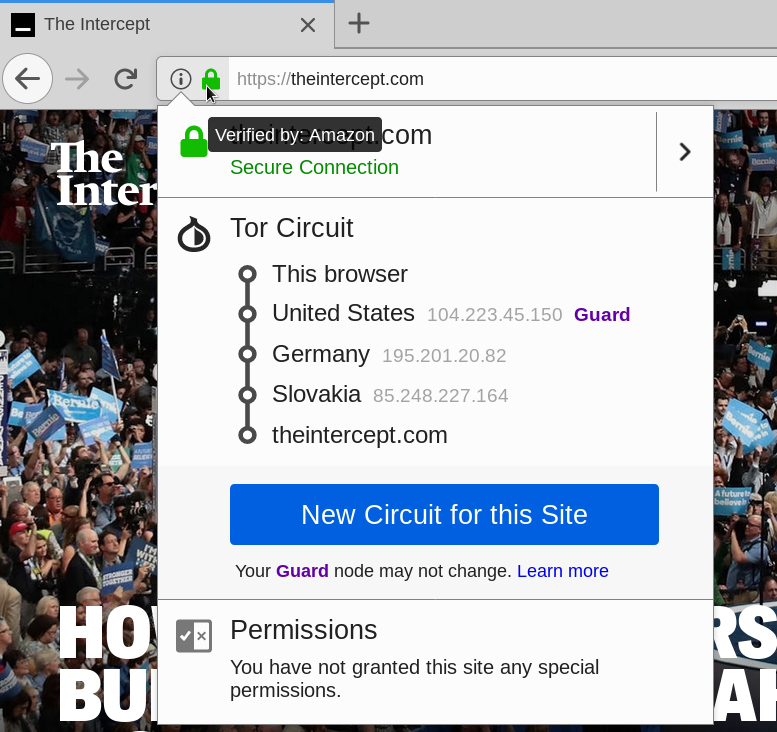
How does it work in practice?
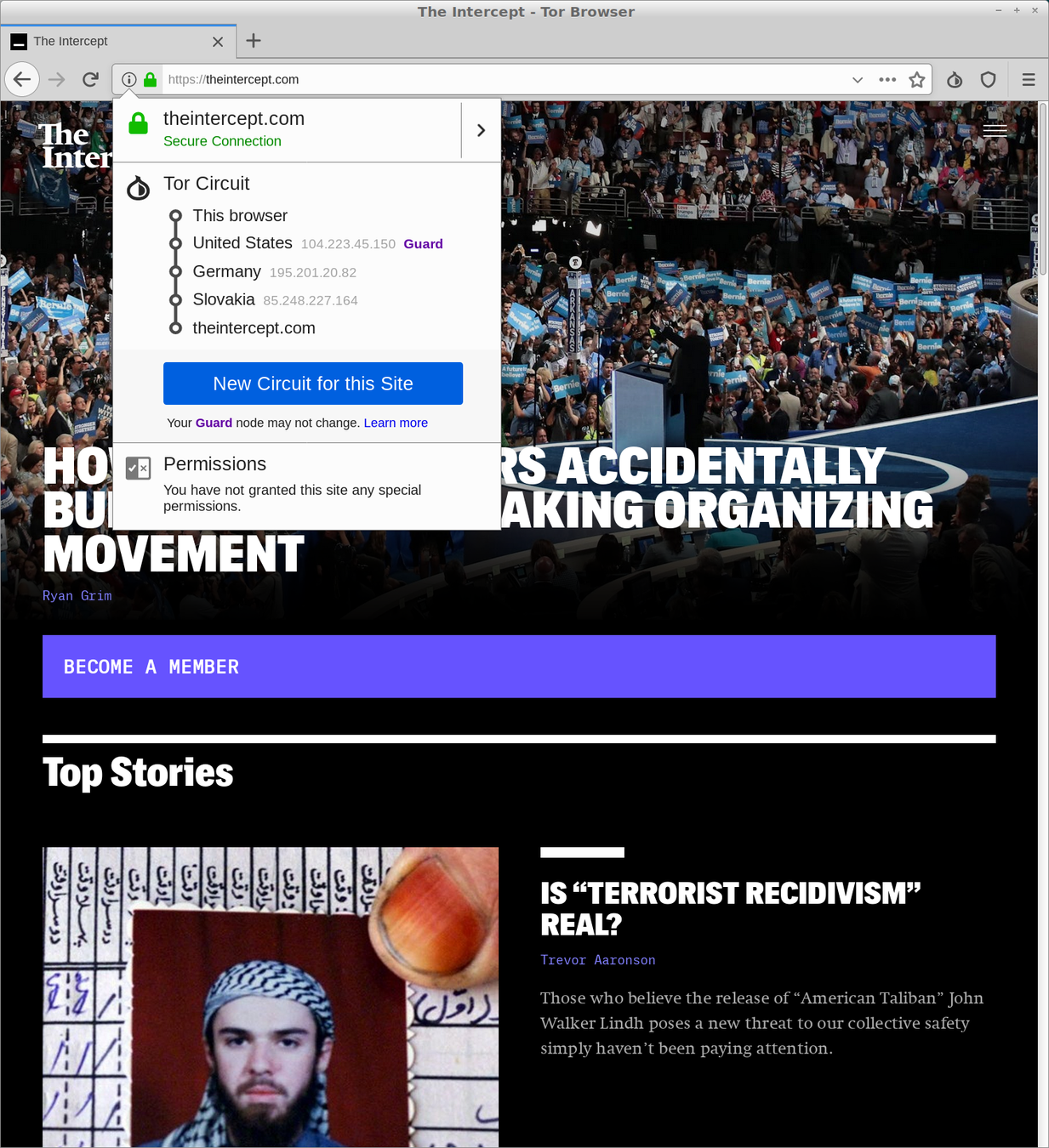
How Tor works
How does it work in practice?
Anonymity > Encryption
Anonymity > Encryption
- Encryption doesn't hide conversations metadata
- how long you talk, how often ...
- Encryption doesn't hide your social graph
- the people you talk to ...
- Encryption doesn't hide network metadata
- network addresses, traffic patterns ...
- Encryption doesn't hide your location
- location services, geo-coding ...

Anonymity loves company
Privacy is a team sport
- To truly provide anonymity Tor needs a diverse group of users using the network
- A diverse population of nodes sustaining the network
- A diverse group of people developing the protocols and software
Using at the app layer:
Tor Browser

What is Tor Browser
Tor Browser is a modified Firefox ESR.
Tor Browser Packages:
-
Tor, Torbutton,
-
TorLauncher,
-
NoScript,
-
and HTTPS-Everywhere.
Why Tor makes a browser
Tor browser is designed to:
- Ensure the safe use of Tor.
- Reduce linkability of user activities on different websites.

Downloading Browser

https://www.torproject.org/download
Onion Services
Providing bidirectional anonymity
Onion Services
-
Onion services can be started from your computer
-
Onion services are p2p
-
Onion services are decentralised
-
Onion services have a smaller attack surface
-
Onion services provide by-directional anonymity
-
Onion services addresses are 54 chars public keys [ed|curve25519 - Keccak(SHA3)]

How Onion Services work
Bob is an onion service and Alice a Tor Browser user.
Bob picks 3 introduction points and builds a circuit.
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
Bob picks some introduction points and builds a circuit to them...
How Onion Services work
Bob builds a descriptor and uploads it to the directory
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
Bob picks some introduction points and builds a circuit to them, then advertises its service at the database...
🖳
DS
How Onion Services work
Alice fetches the descriptor from the directory and learns how to reach Bob.
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
🖳
Alice hears that bob.onion exists and they request more info from the database. They also setup a rendezvous point.
DS
How Onion Services work
Alice tells Bob to meet her at the rendezvous point.
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
🖳
Alice writes a message to Bob listing the rendezvous point and a one time secret, and asks an introduction point to deliver it to Bob.
DS
How Onion Services work
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
Bob connects to Alice's rendezvous point and provides their one-time secret.
How Onion Services work
Both Alice and Bob connect with a 3 hops circuit to the RP.
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
🖳
💻
Alice
bob.onion
Bob and Alice use their circuit normally.


When our privacy is stolen, so is our right to control our own narrative...
The End of Trust - McSweeney's 54
Learn more...
- www.torproject.org
- Tor Browser design doc
- Mozilla Firefox Extended Support Release
- Tor Projects
- Tor Rendezvous Specification - Version 3
- Secure Messaging with Onion Services, a How-To