What is the dark net? Really.
Hello World
My name is Silvia Puglisi. I am a system engineer at Tor Project and Ph.D. candidate at UPC Barcelona Tech.
I research in privacy and web science.
I am here to talk you about the somewhat dark web.
But first, what is the internet?

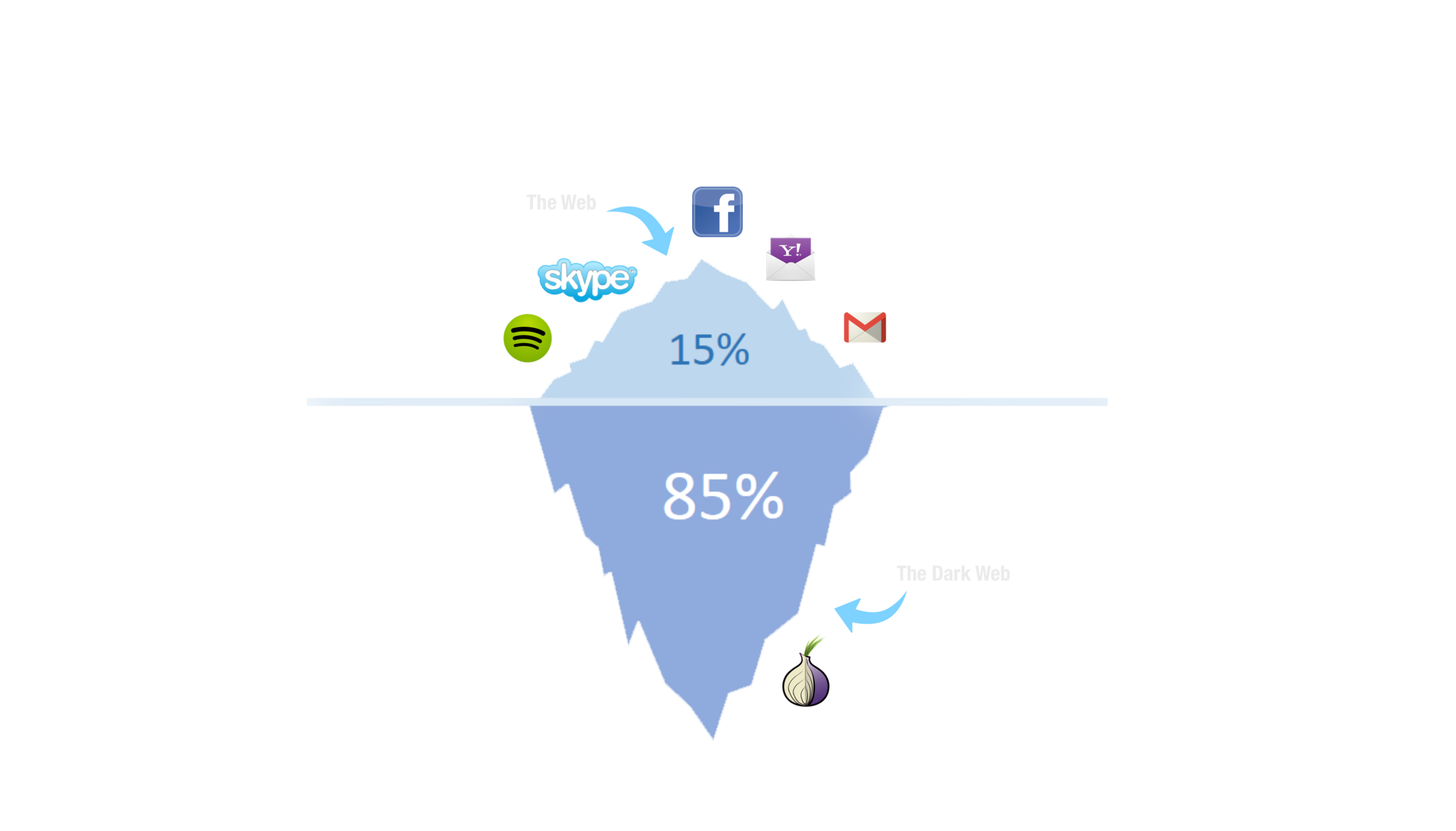
The Internet/web/interwebs is what can be crawled by search engines (or tracking networks). But it is not so "light":
- Between 25% and 50% of traffic is created by bots.
- When users surf the web networks of personalisation
services tracks their preferences generating data. - Web ads networks exhibit the same properties of malwares.
What about privacy?

It is complicated..
How to define privacy violations? *
-
Information collection:
-
surveillance, interrogation or information probing.
-
-
Information processing:
-
aggregation and identification of data.
-
-
Information dissemination:
-
unwanted disclosure and exposure of information.
-
-
Invasion:
-
intrusion of an entity into some-one’s private life.
-
* D. J. Solove, “A taxonomy of privacy,” University of Pennsylvania law review, pp. 477–564, 2006
What about the dark web?
What if we switch it around?
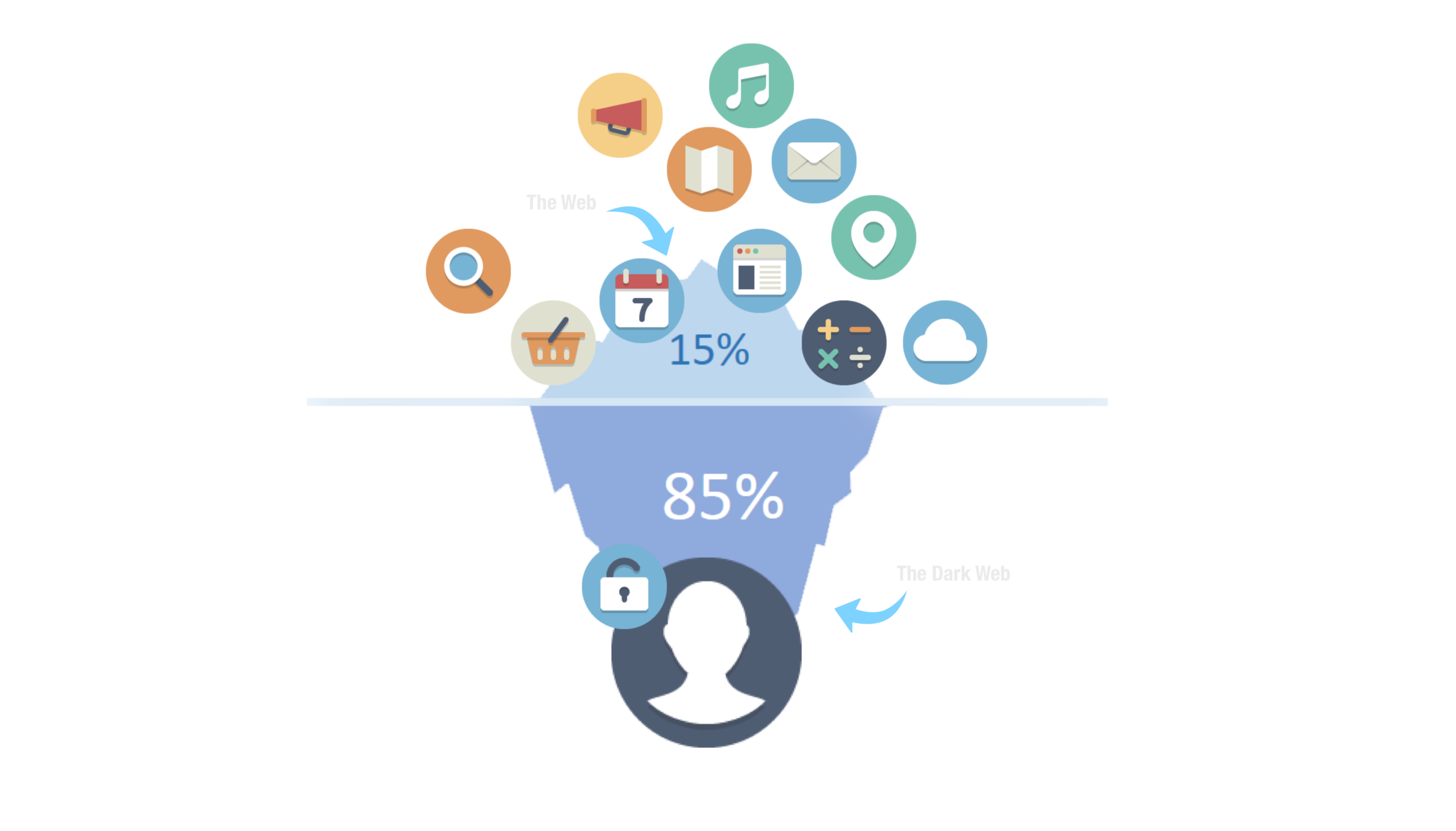
The dark web is where you can surf privately *
- Using Tor protects you against a common form of Internet surveillance known as "traffic analysis." Traffic analysis can be used to infer who is talking to whom over a public network. Knowing the source and destination of your Internet traffic allows others to track your behavior and interests.
- Tor reduce the risks of both simple and sophisticated traffic analysis by distributing your transactions over several places on the Internet.
- Check: why we need Tor
* Terms and conditions apply
I have gone dark. now what?
- You can surf the web normally. It will (mostly) work the same.
- You can access news that would normally not be accessible in your country (if you live somewhere where checking Facebook can put you in trouble).
- You can check The hidden wiki.
- You can contact C'thulhu.
Safety Tips
- Do use Tor Browser.
- Don't torrent. File-sharing applications sometimes ignore proxy settings and make direct connections even when they are told to use Tor. This deanonymise your torrent traffic and your other simultaneous Tor web traffic.
- Don't enable or install browser plugins as they can bypass Tor or make your browser easier to fingerprint (https://panopticlick.eff.org/)
- Do use HTTPS versions of websites so that the encryption of your traffic to the final destination website is also encrypted.
- Don't open documents downloaded through Tor while online.
- Do use bridges and/or find company to avoid attackers from learning that you're using Tor. Reduce this risk by configuring Tor to use a Tor bridge relay.