Federated Identity Pattern
The problems
> Disrupted user experience
> Expose security vulnerabilities
> Complicate user management
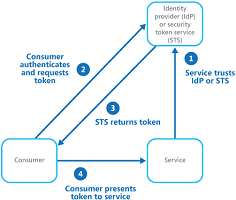
Separate authentication from aplication
> Decouple authentication from authorisation
> Use Identity Providers
> With Security Token Service
> No Identity Management
Considerations and When to use
> Deploy authentication mechanism to same data-centres as applications using them
> IPs might not provide information about user
> Role based access control RBAC
> Home Realm discovery by STS for several IPs
To use for:
> Single sign on, multi-partners access, SaaS applicatons