Securing Docker
environment
Information security monitoring analyst:
Igor Tarpan

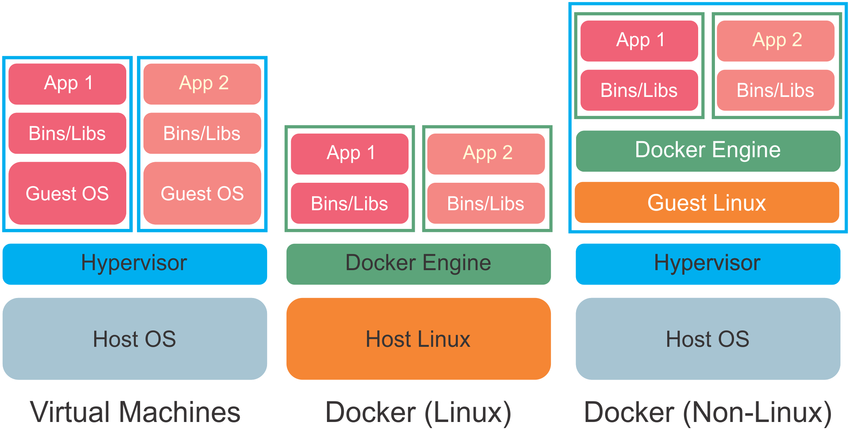
Docker vs VM's
Security aproach
Security aproach
Agenda
- Attack vectors
- docker build
- docker push & docker pull
- docker run
- Docker minimal security checklist
Attack vectors
docker build .
- Do not run as root * (Dockerfile add user)
- Use minimal base images for your application * (meme small cintainers)
- Use multi-stage builds for your application * (Multistage build)
- Use COPY not ADD * (diffrences)
- Use only official images but not blindly (nginx as root)
- STOP COPY . . * (demo ssh key)
- Do not copy sensitive data in your image * (demo .env and use ignore)
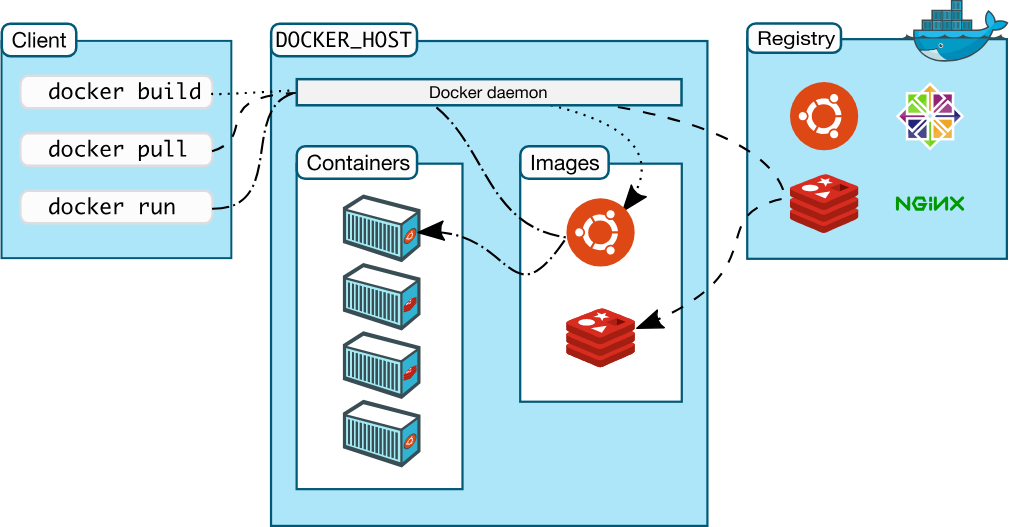
docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image
Do not use root
FROM ubuntu:latest RUN apt-get update --fix-missing && \ apt-get install -y redis-server && \ rm -rf /var/lib/apt/lists/* USER 9000 EXPOSE 6379 CMD redis-server
second method will be soon *
docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image

docker run -p 9000:80 python:3.7.2-debian
935 Mb
docker run -p 9000:80 python:3.7.2-debian-slim
196 Mb
docker run -p 9000:80 python:3.7.2-alpine
93 Mb
docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image
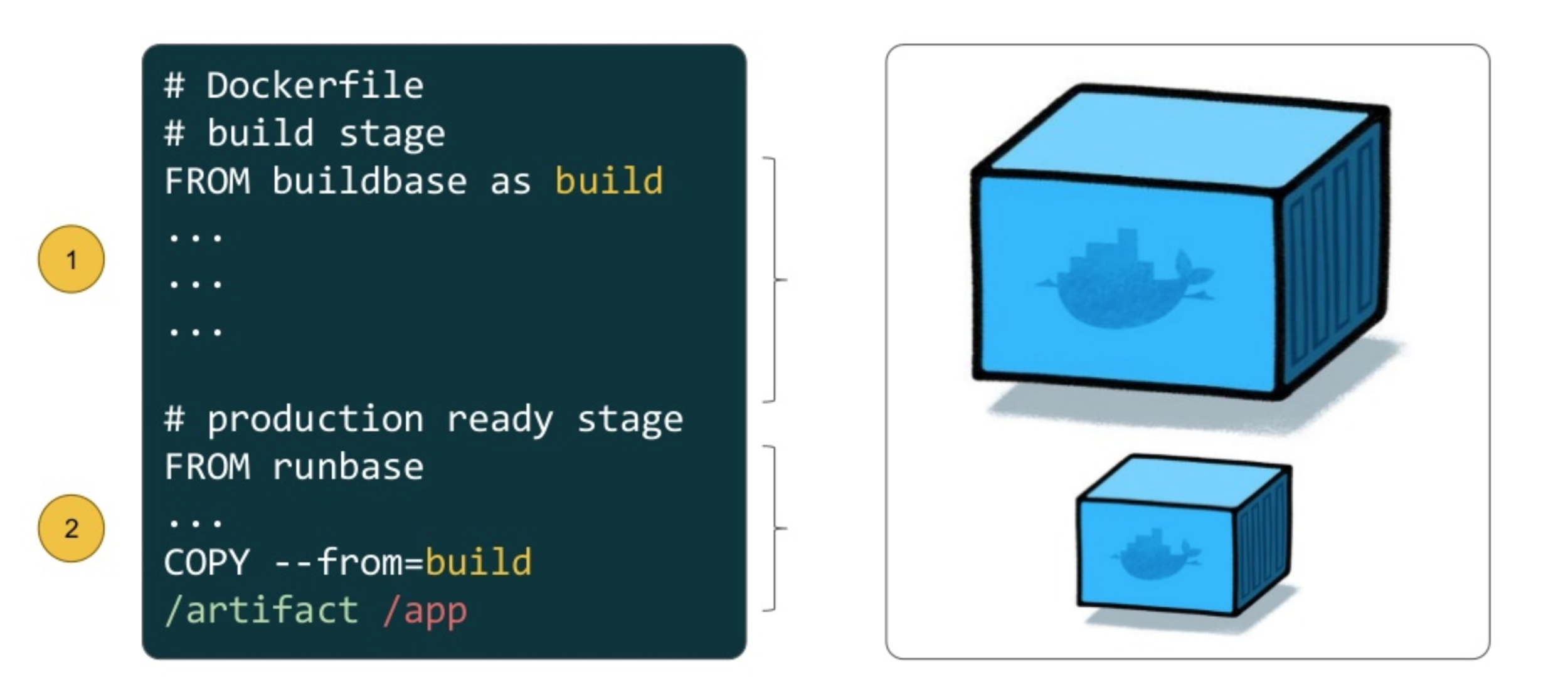
Before
After
FROM maven:3.5.2-jdk-9
COPY src /usr/src/app/src
COPY pom.xml /usr/src/app
RUN mvn -f /usr/src/app/pom.xml clean package
EXPOSE 8080
ENTRYPOINT ["java","-jar","/usr/src/app/target/
flighttracker-1.0.0-SNAPSHOT.jar"]#### Build ####
FROM maven:3.5.2-jdk-9 AS build
COPY src /usr/src/app/src
COPY pom.xml /usr/src/app
RUN mvn -f /usr/src/app/pom.xml clean package
#### Run ####
FROM openjdk:9
COPY --from=build /usr/src/app/target/flighttracker-1.0.0-SNAPSHOT.jar /usr/app/flighttracker-1.0.0-SNAPSHOT.jar
EXPOSE 8080
ENTRYPOINT ["java","-jar","/usr/app/flighttracker-1.0.0-SNAPSHOT.jar"]docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image
docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image
docker build .
- docker pull couchbase
- docker pull redis
- docker pull mongo
- docker pull postgres
- docker pull ubuntu (root)
- docker pull nginx (root)
- docker pull node
- docker pull traefik
- docker pull httpd
- docker pull golang
docker build .
- Do not run as root
- Use minimal base images for your application
- Use multi-stage builds for your application
- Use COPY not ADD
- Use only official images but not blindly
- STOP COPY . .
- Do not copy sensitive data in your image
Demo

docker push & docker pull
- Avoid using third party images (bitcoin miners)
- Use private repositories/registers and limit access to them ()
- Docker Content Trust (Demo docker content trust)
- Perform security scanning of your image at every deploy (demo Anchor)
- Security should be part of your SDLC (Security life cicle img)
- Update images to the latest version
- Do not use image:latest
docker push & docker pull
- Avoid using third party images
- Use private repositories/registers and limit access to them
- Perform security scanning of your image at every deploy
- Security should be part of your SSDLC
- Update images to the latest version
- Do not use image:latest
- Docker Content Trust (Demo docker content trust)
docker push & docker pull
- Avoid using third party images
- Use private repositories/registers and limit access to them
- Perform security scanning of your image at every deploy
- Security should be part of your SSDLC
- Update images to the latest version
- Do not use image:latest
- Docker Content Trust (Demo docker content trust)
docker push & docker pull
- Avoid using third party images
- Use private repositories/registers and limit access to them
- Perform security scanning of your image at every deploy
- Update images to the latest version
- Do not use image:latest
- Docker Content Trust
Scan Docker images
docker push & docker pull
- Avoid using third party images
- Use private repositories/registers and limit access to them
- Perform security scanning of your image at every deploy
- Update images to the latest version
- Do not use image:latest
- Docker Content Trust (Demo docker content trust)
docker run
- Update docker-engine and software component from the host
- Do not mount sensitive data in container
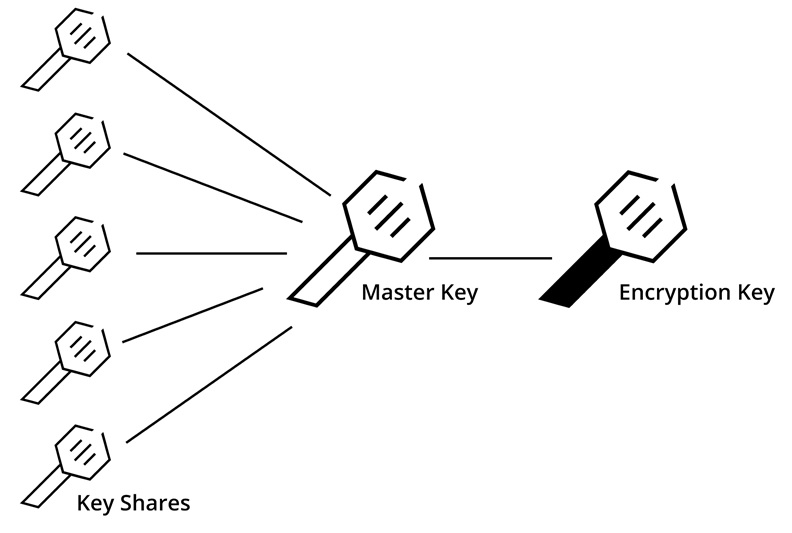
- Secrets should be stored carefully
- All persistent data should be mount outside of container
- Do not run container in elevation mode
- Do not run as user
- Use TLS everywhere (demo HTTP2)
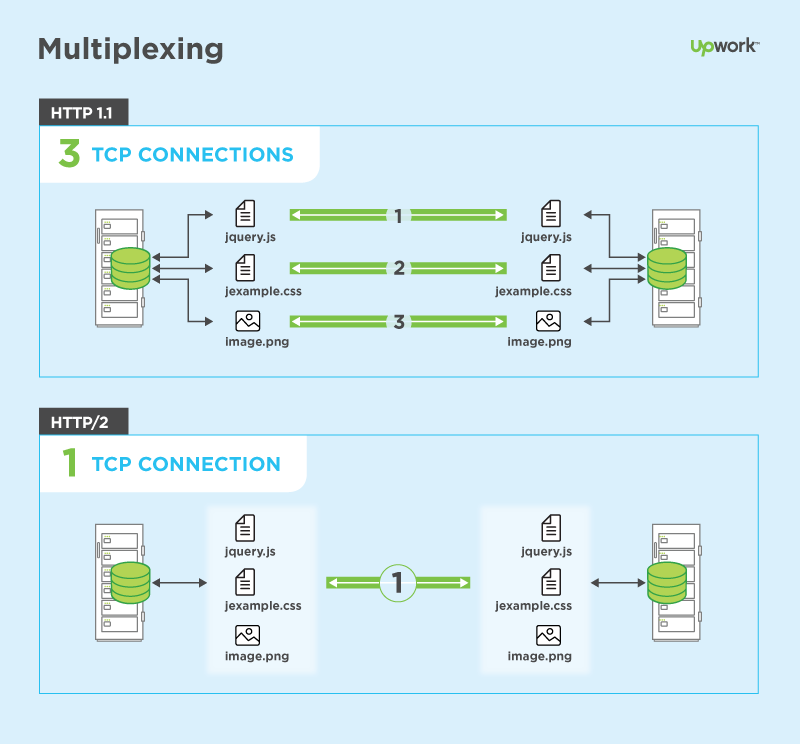
HTTP 1.1 vs HTTP/2
Vault by Hashicorp
docker run
- stop doing -p 80:80, -p 9200:9200, -p 5432:5432
- Use application gateways and firewalls in front of your application
- Limit resources for your containers
- Runtime security (apparmor)
- Monitor and Audit Container Activity
To much info ?
-
Limit
- White list is better then black list
-
Encrypt
- Longer key is better then short one
-
Safe secret management
- Store them safely
- Do not use defaults secrets
-
Scan
- Auto is better then manual
-
Monitor
- Application metrics is better then system metrics
-
Update
- Daily is better then weekly
Too Little Info?
- Docker CIS Benchmark
- https://www.cisecurity.org/benchmark/docker/
- Docker CIS Benchmark check
- https://github.com/docker/docker-bench-security