Heimdall
Author: Ivan Zlatanov, NTBHS
Mentor: Yavor Papazov, VMWare
USB mass storage devices threat evaluation using an embedded system


The problem that we explore
- The high count of cyberattacks, executed or delivered via USB mass storage devices;
- Device exploitation mechanisms, such as BadUSB, USBee, and Cottonmouth;
- The lack of adequate detection and defense methods for such devices and attacks, leading to the ban of such devices in multiple governments and private facilities.
What is Heimdall
- A stack of USB devices threat evaluation methods;
- Implemented into an open-source Python 3.x framework, called Heimdall Framework;
- All running on a modified Raspberry Pi 4 with a custom hardware port controller.
General architecture
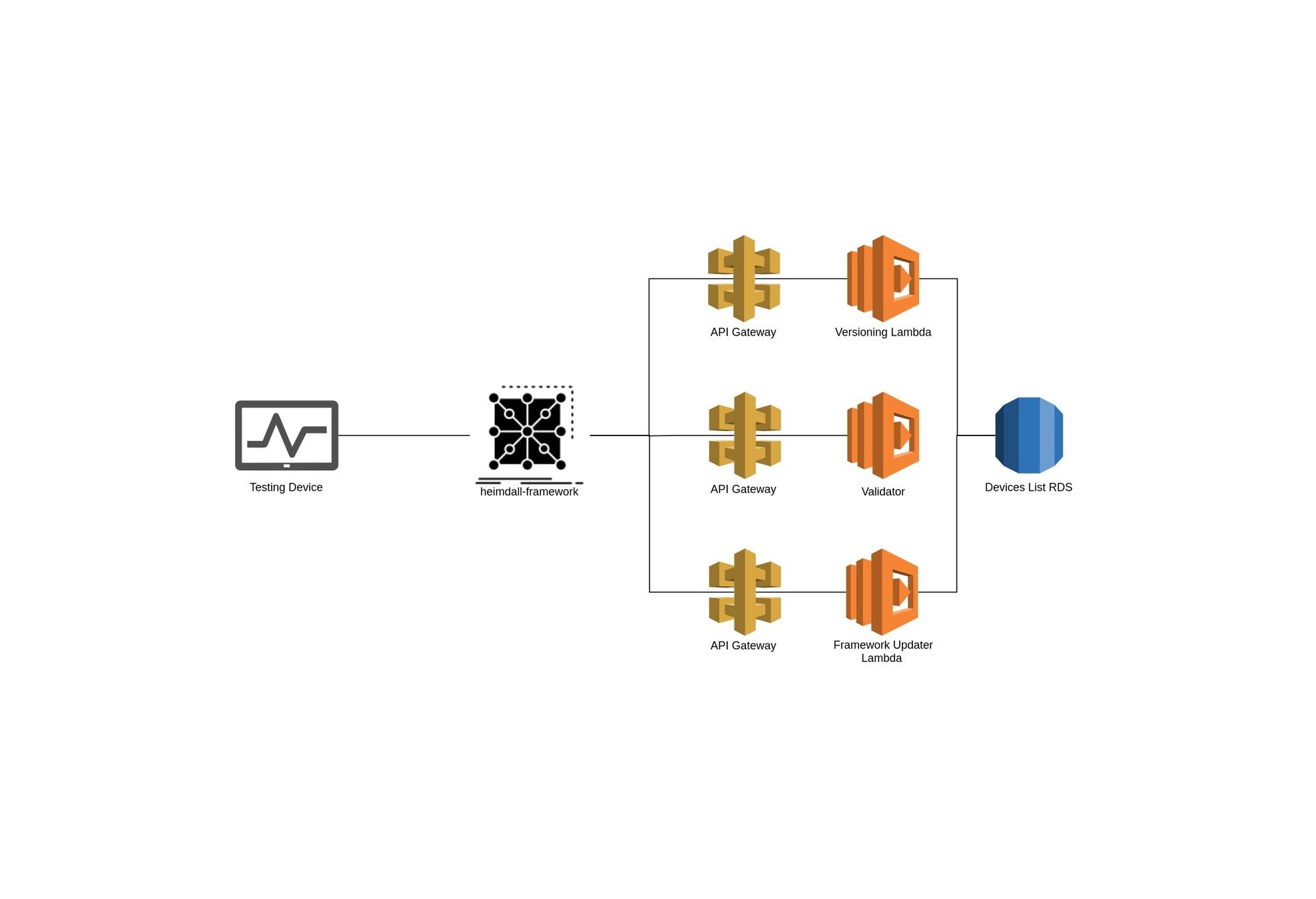
The testing device
- Raspberry Pi 4;
- External hardware power controller for the USB ports;

Heimdall Framework
- Open-source Python 3.x framework;
- Built for Raspberry Pi based devices;
- Executes multiple USB device evaluation tests:
- Unplugging simulation;
- Device type validation;
- Vendor information validation;
- Virus scan;
- Input/Output test;
- Linux-based live distributions validation.
- Supports custom security tests via a plugin management system.
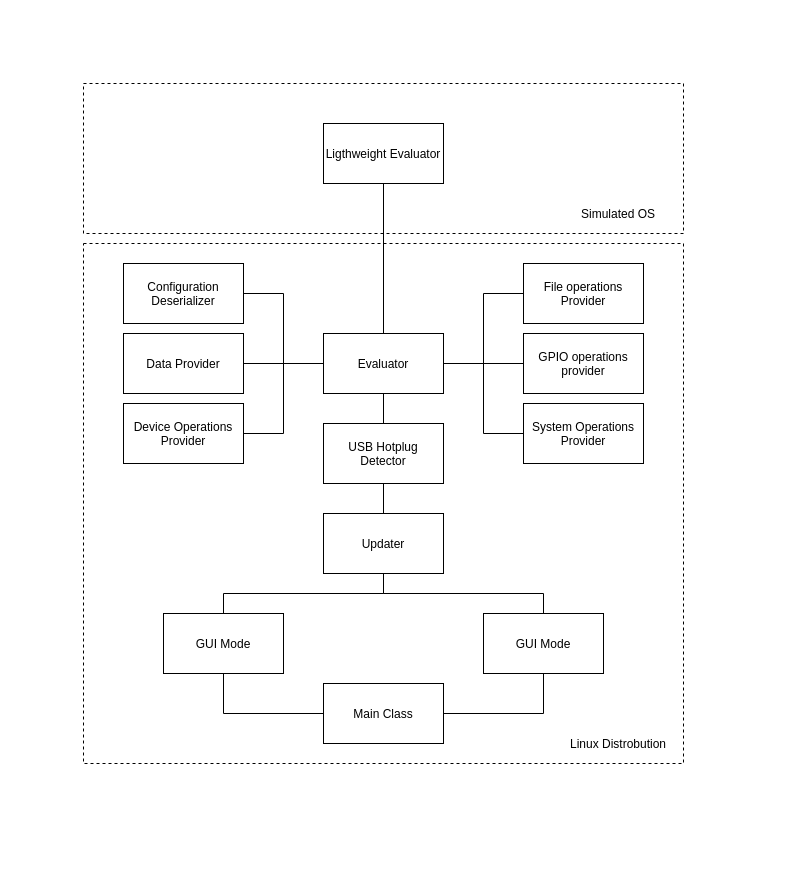
Heimdall Framework Architecture
Further Development
Expanding the scope of HID tests


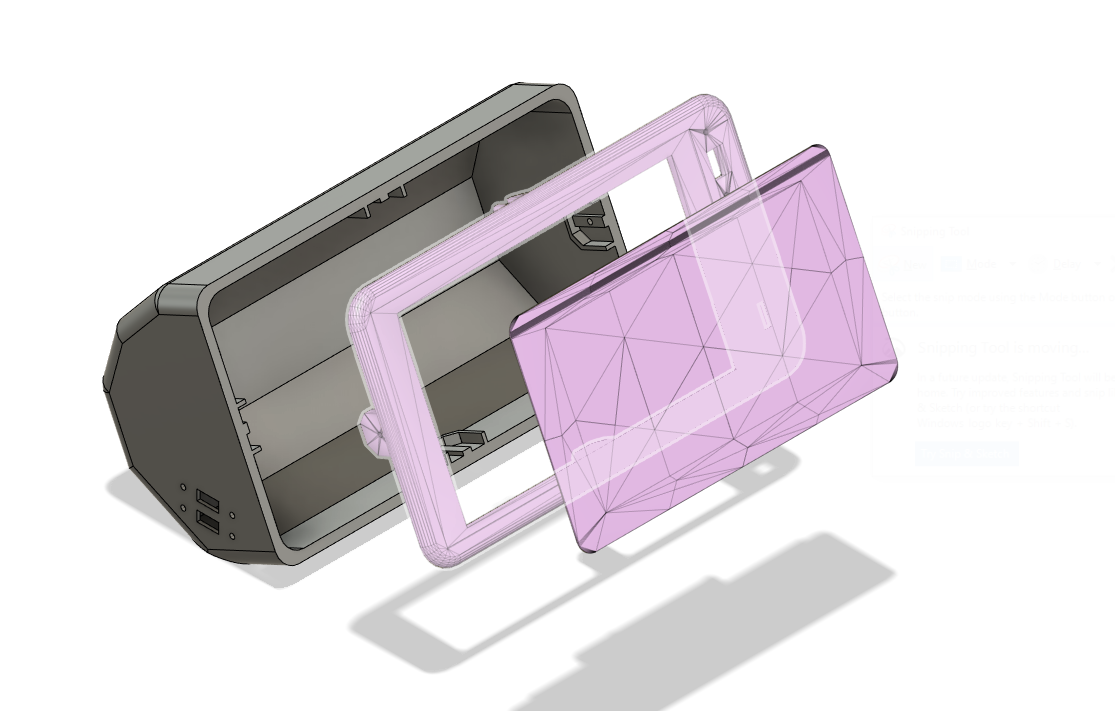
Rapid prototyping of the device's case
Researching BSD and Linux exploits and developing proper detection mechanisms


