Automation in Pentest
By: Jaimin Gohel
About Speaker
- MCA(GLSICT)
- Bug hunter
- Laravel Developer @ QlooIt Solutions
- Speaker at Mozilla Gujarat
Why do want to automate?
-
Saves time
-
Consistency
-
Accuracy
-
easier to pass on to other testers
-
Bad guys are automating too
-
eg:- malware that spreads without user interaction, botnets (send commands to several machines at a time).
- Dridex malware scans memory for credit card numbers
Ways to automate
-
Grab list of subdomains (sublister, knockpy,google dorks)
-
Ping sweap (script to check which ip addresses are up in the network)
-
Nmap + Nikto
-
Nmap + Searchsploit
-
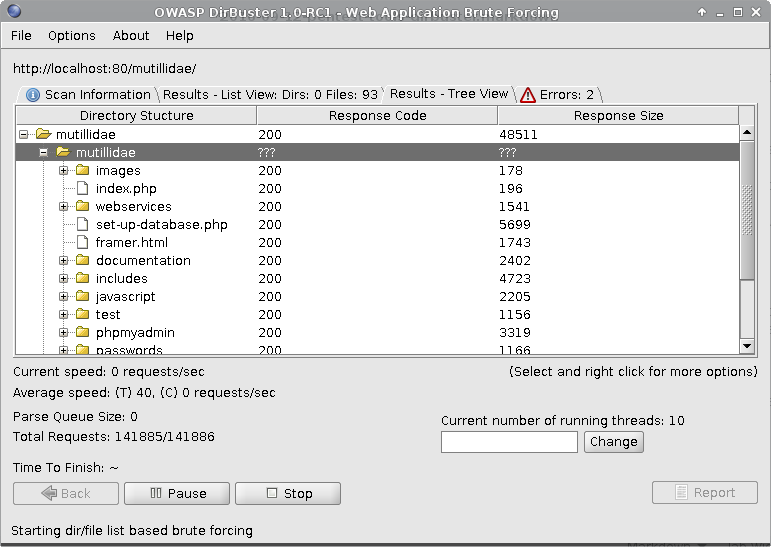
Directory Buster
Subdomain finding scripts (sublist3r)
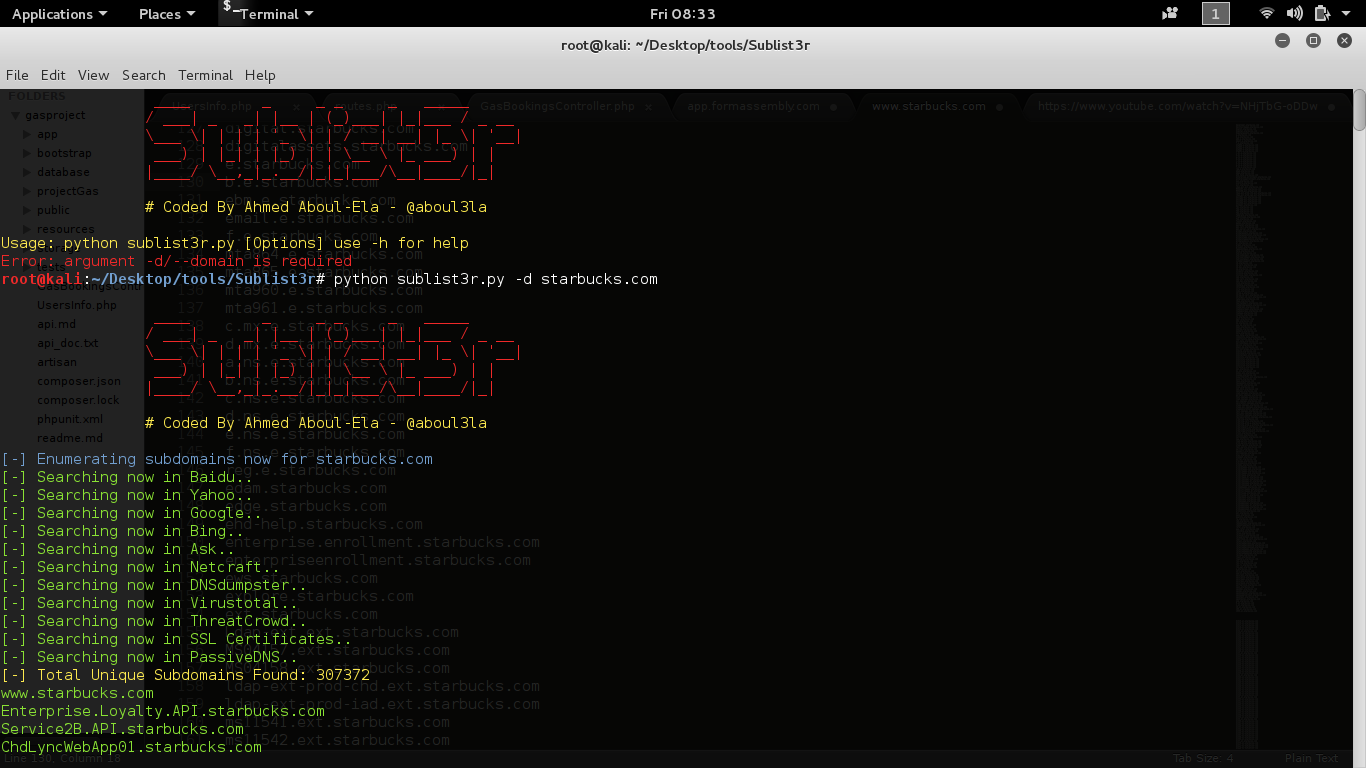
- sublist3r
It will grab data from the search engines to find the unique subdomains.
python sublist3r.py -d starbucks.com-d is for domainSubdomain finding scripts (sublist3r) cont.
Subdomain finding scripts (knockpy)
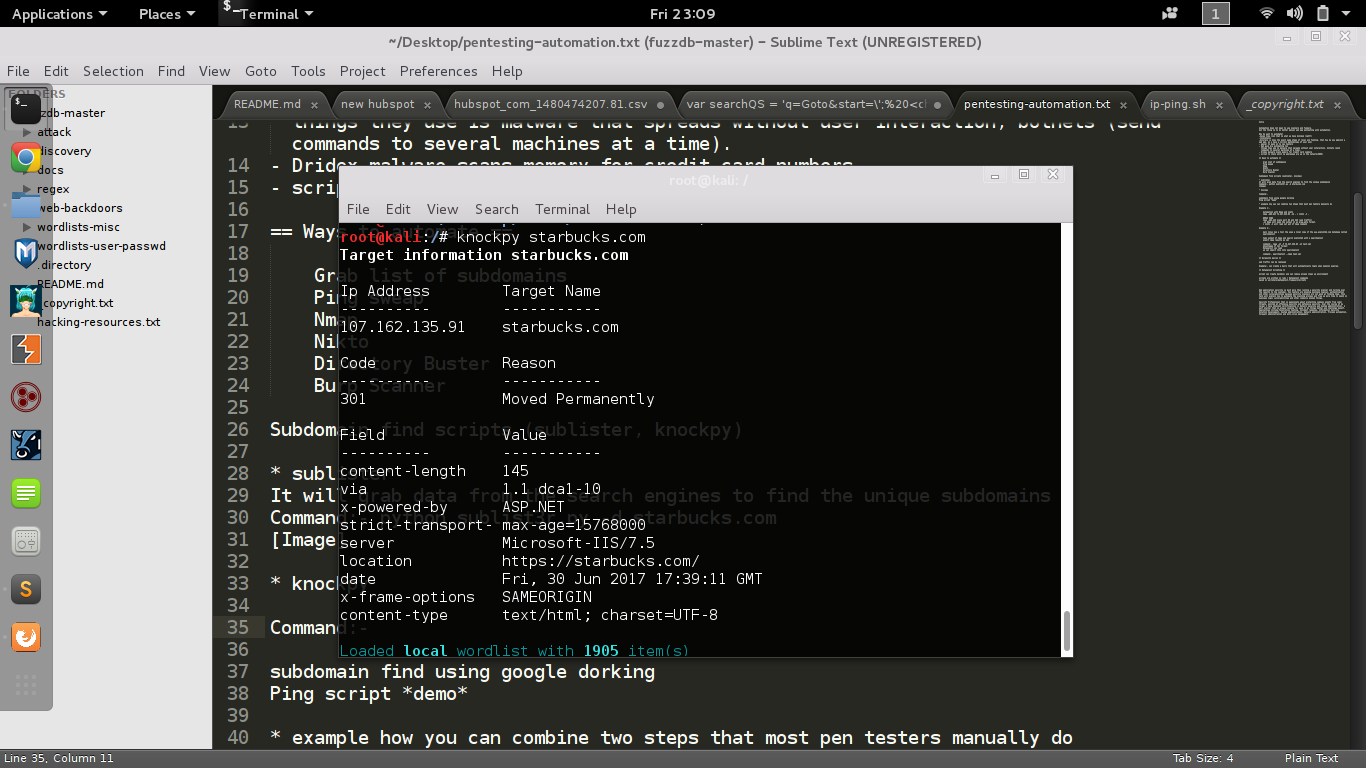
- knockpy
written in python used to enumerate subdomains.
knockpy starbucks.comknockpy -w subdomains-top1mil-5000.txt tesla.comcan take custom word list as argument.
Subdomain finding scripts (knockpy) cont.
Subdomain finding scripts (knockpy) cont.
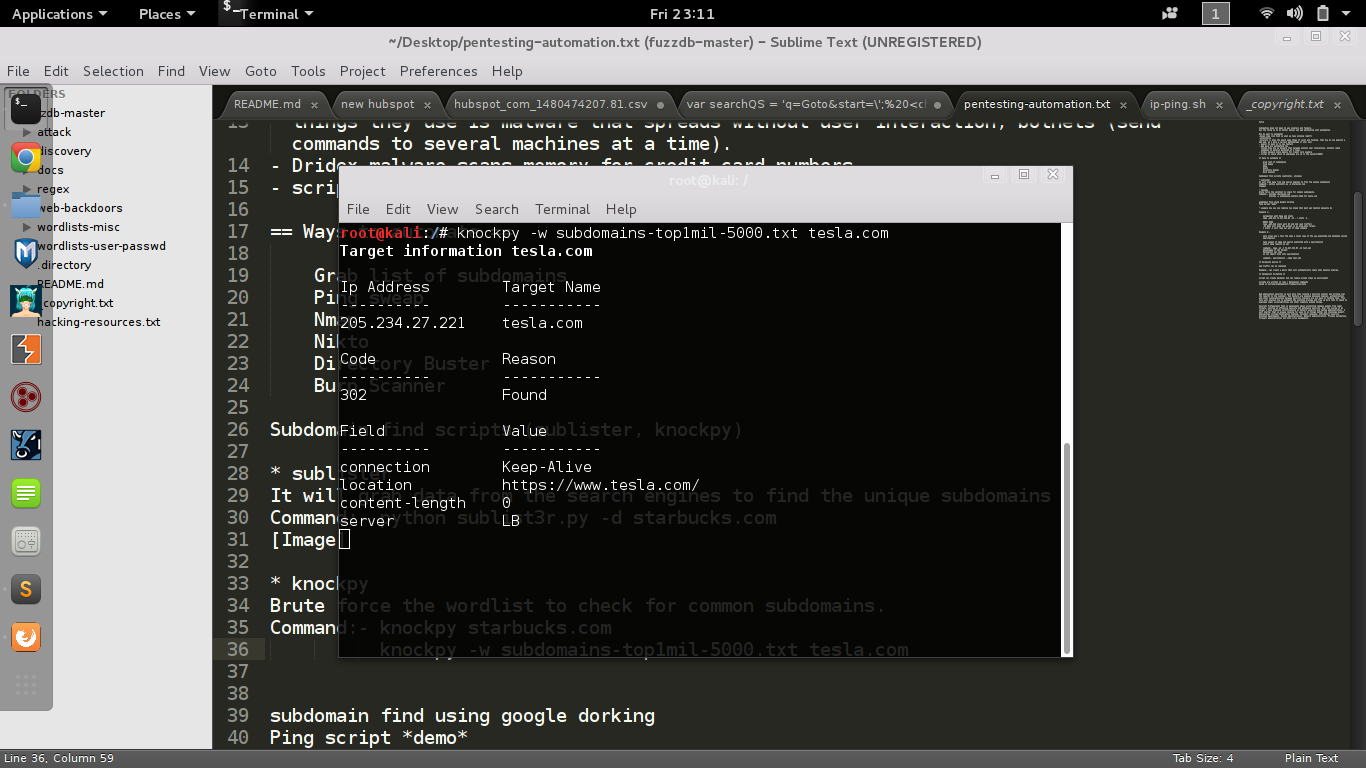
-w custom wordlistFind Subdomain using google dorking
site:starbucks.com -inurl:www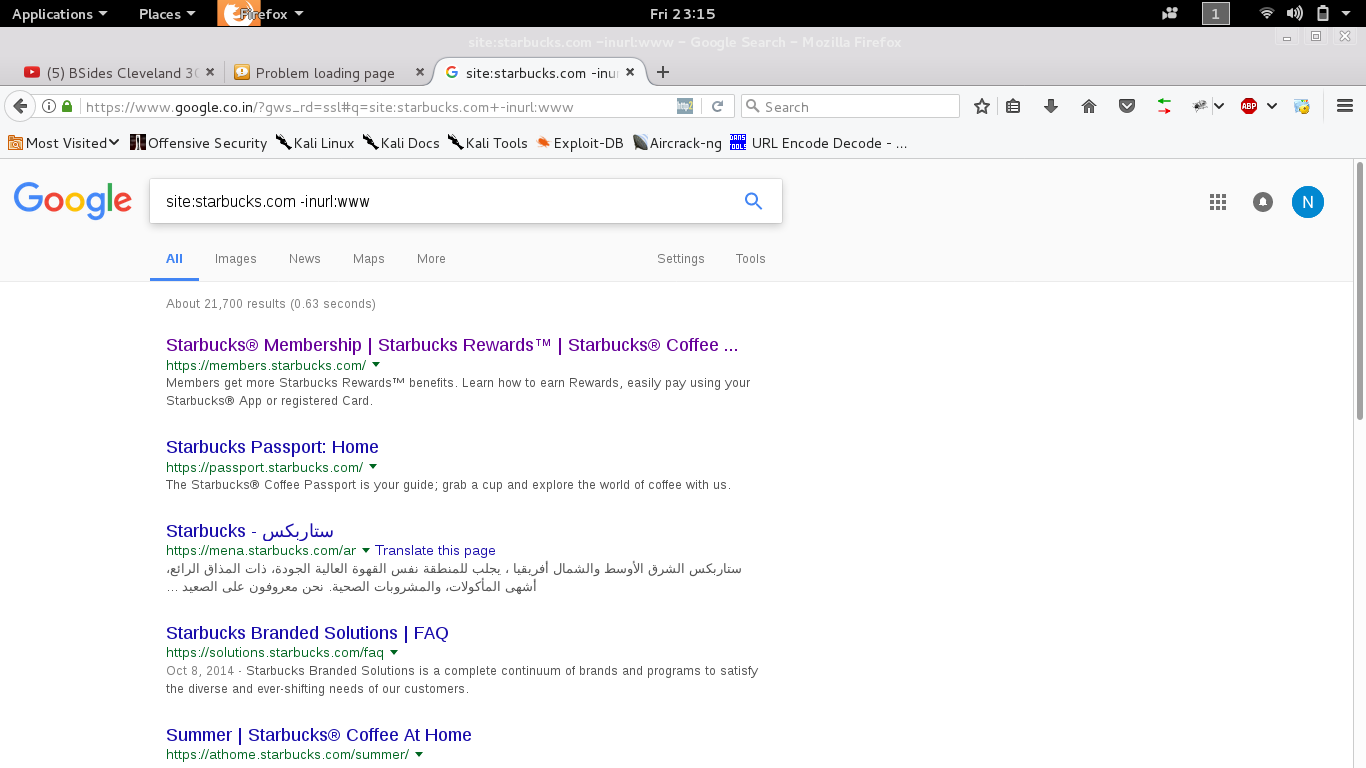
Ping sweap
for ip in $(seq 59 70); do ping -c 1 117.196.35.$ip | grep "bytes from" | cut -d" " -f4
done- script to check which ip addresses are up in the network
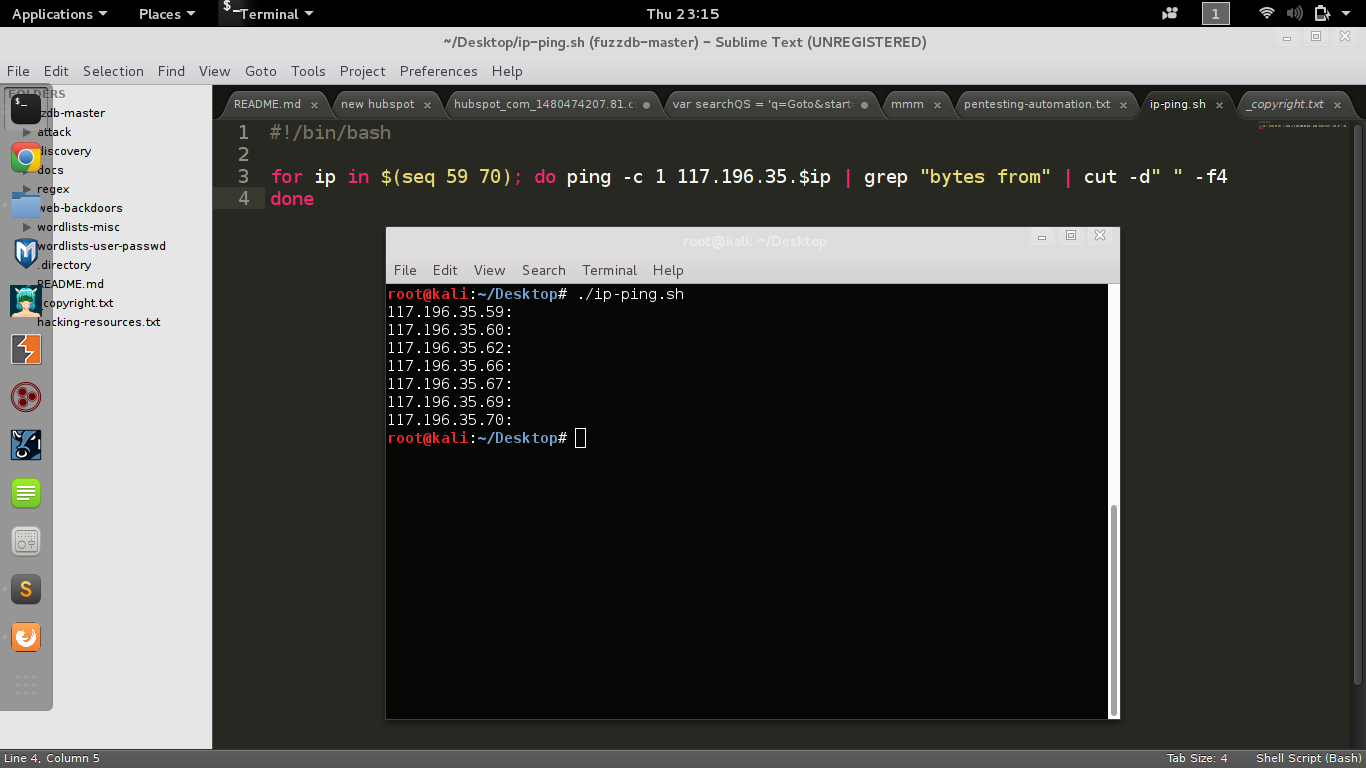
Ping sweap (break down)
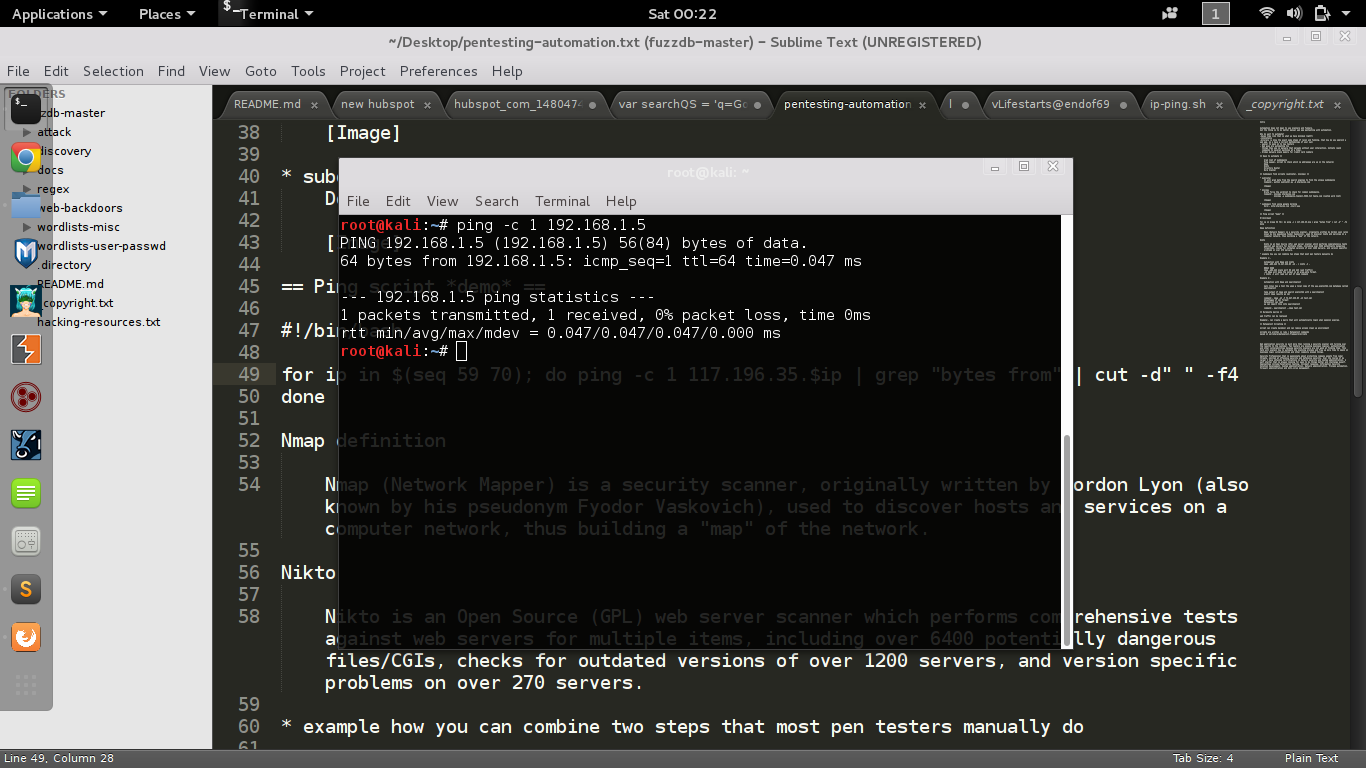
Nmap
Nmap (Network Mapper) is a security scanner, used to discover hosts and services on a computer network, thus building a "map" of the network.
Nikto
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers.
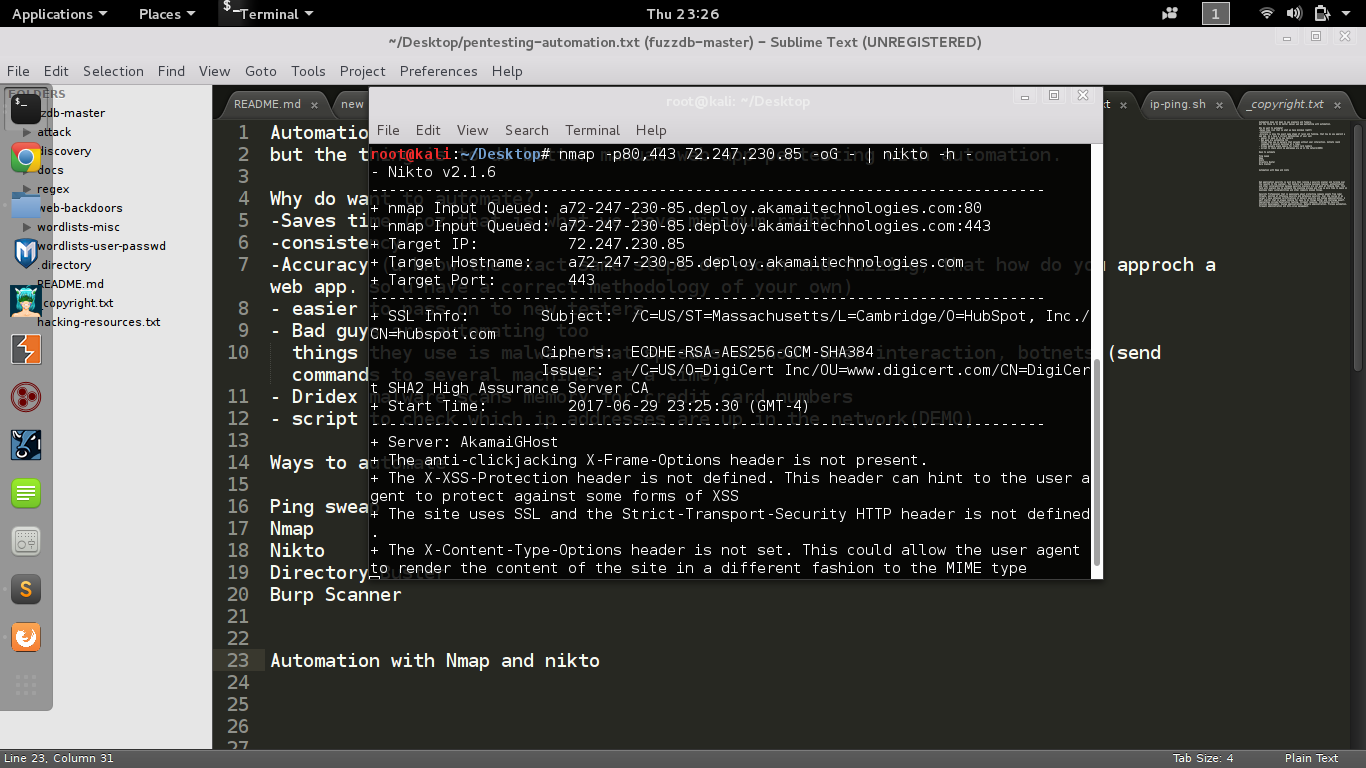
Automation with Nmap and nikto
Automation with Nmap and nikto
nmap -p80,443 72.247.230.85 -oG - | nikto -h -BREAK DOWN
- nmap -p80,443 scans port 80 and 443 (web traffic)
- -oG Nmap will make the output in an grep-able format.
- | to pipe the information into next command
- nikto -h will read output of nmap command
Automation with Nmap and nikto (cont.)
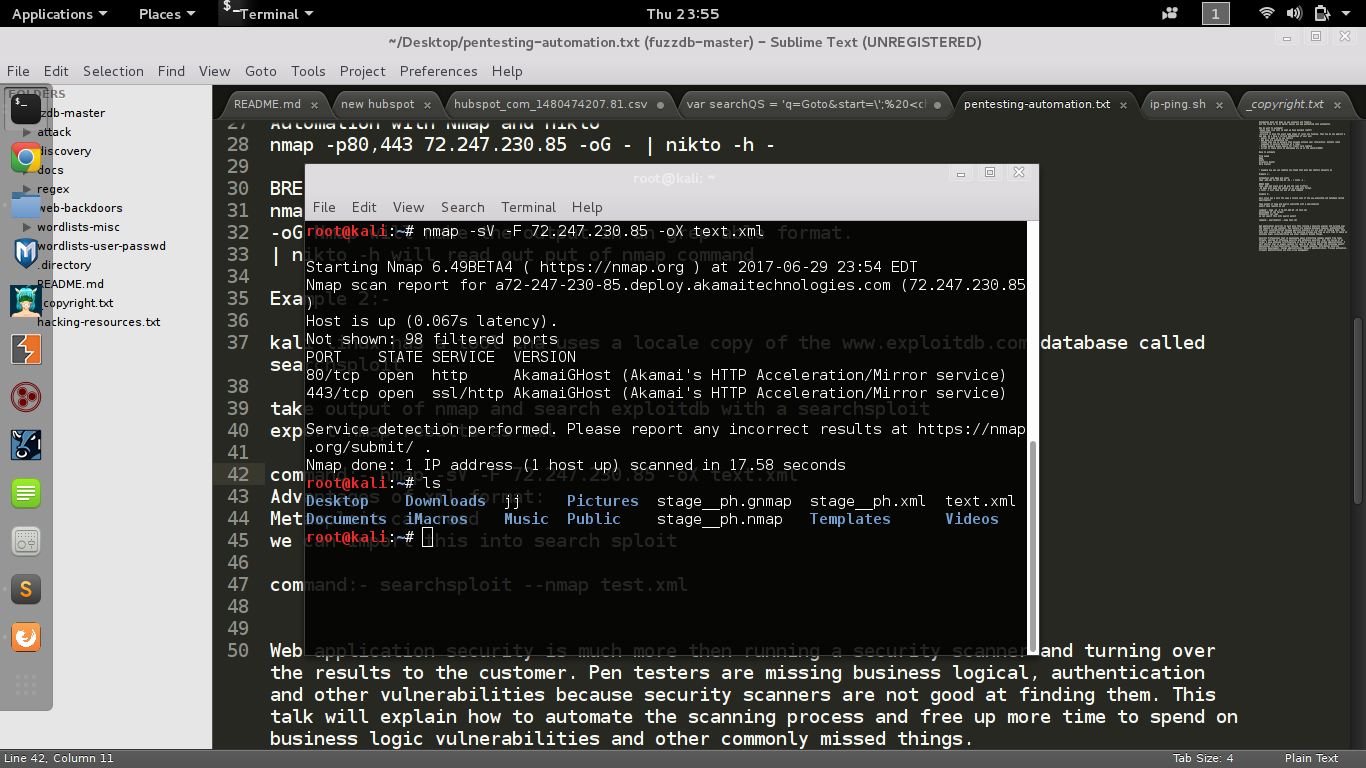
Automation with Nmap and searchsploit
Automation with Nmap and searchsploit
- kali linux has a tool tha uses a local copy of the www.exploitdb.com database called searchsploit
- searchsploit can read the xml generated from nmap
nmap -sV -F 72.247.230.85 -oX text.xmlStep 1: Generate Xml
Step 2: Pass into searchsploit
searchsploit --nmap test.xml-sV: Probe open ports to determine service/version info-F: Fast mode - Scan fewer ports than the default scan-oX output the xml versionAutomation with Nmap and searchsploit
Dirbuster
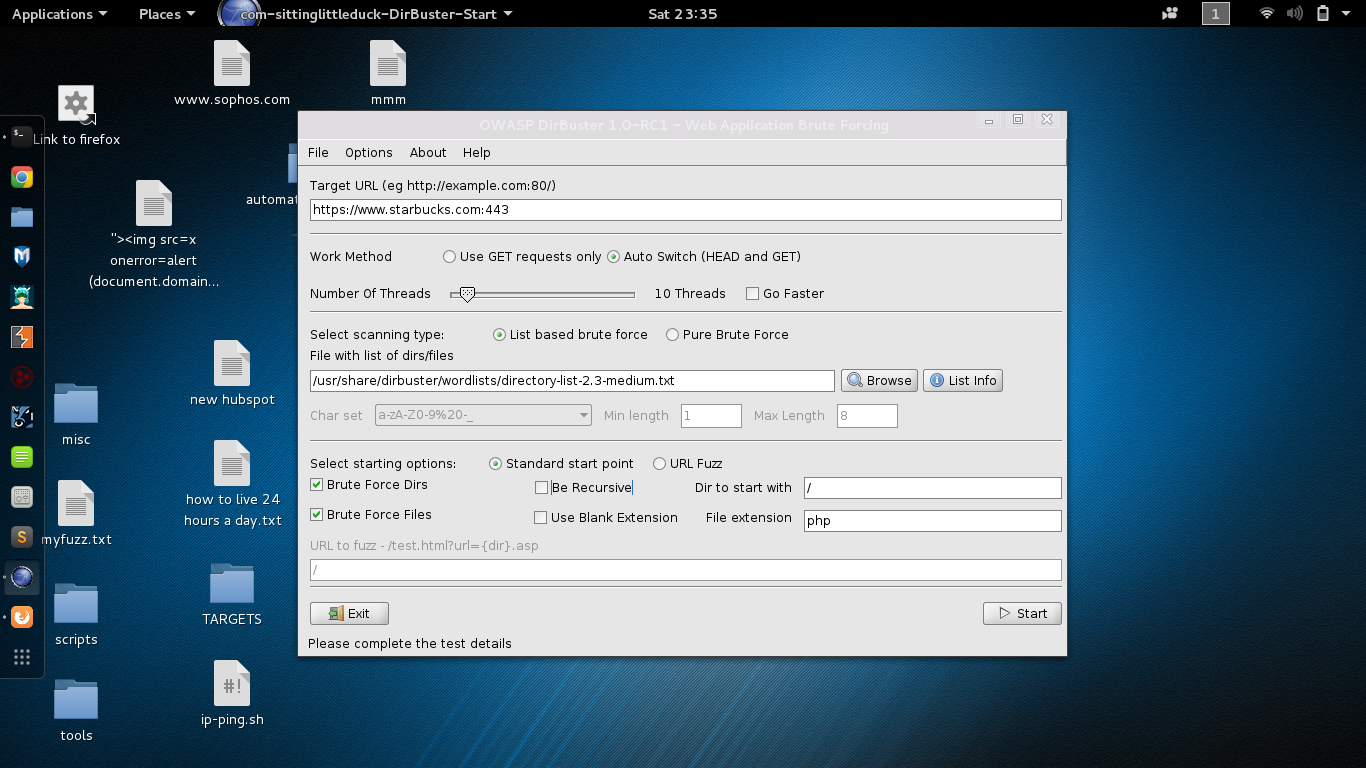
Dirbuster(cont.)