Security Week 3
Attacker/Defender mindset
Imagine you are the head engineer of building ATM machines for a multibillion-dollar bank (you can assume you have infinite resources).
You have been asked by the CEO to build an unhackable/unbreakable ATM?
How would you do this? What security mechanisms would you have?
Attacker mindset
How how would you attack your atm?
Admin
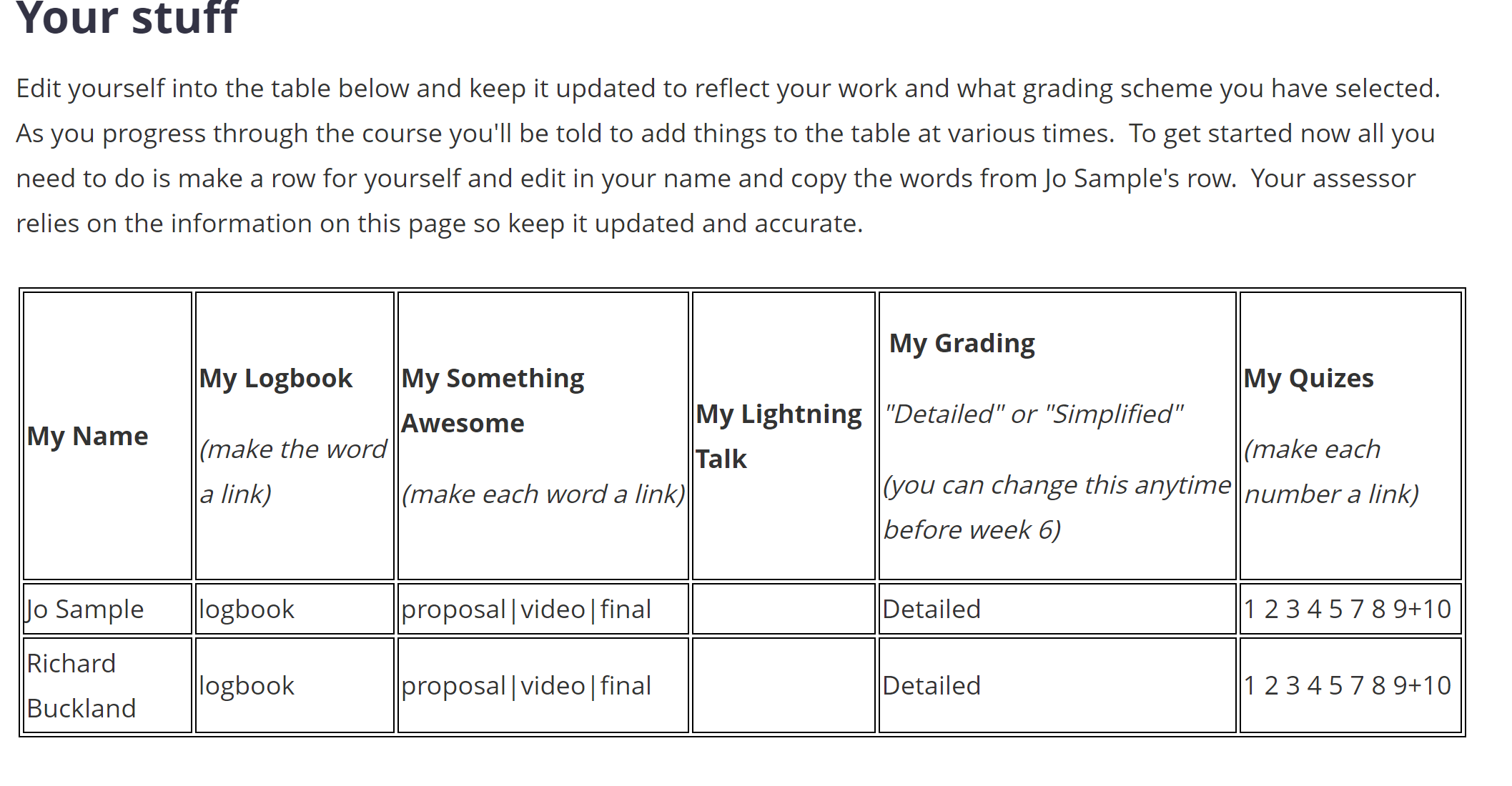
Edit yourself into the table
We need a class rep
If anyone has any concerns or feedback for me and want to remain anonymous, they can contact the class rep who will forward the message to me.
If anyone has any concerns or feedback for the course and want to remain anonymous, they can contact the class rep who will forward the message to the course admins/lecturer via cs6441@cse.unsw.edu.au
Class rep to join case study group called "StuReps"
Liam: liam.smith@unsw.edu.au
Something Awesome (SA)
Everyone should have received feedback for this. Most will require some slight modification of it.
But other than that, I'm super keen to start reading your blogs.
It's a good idea to write a weekly blog about what you did that week for it. That way you can show your progress.
General Feedback From Marking
- It is possible that some feedback has been cut off. If that has happened or you want more feedback, LMK after class.
- Please make sure you link your blogs properly. Some people linked the activity question not their blogs.
- The best way to show community building is to create a blog and put screenshots of your comments in it.
- If you want excellent for the breadth, you need to do all the activities.
- Excellent - all activities
- Good - at least half
- Partial - at least 1 activity
- Absent - missing
- The blog you use ! will be the blog I mark for depth.
Where people lost marks
- Guide on how to write your analysis case study
-
Dealing with challenges reflection. Things to include:
- how you are going in the course?
- What you have achieved?
- What you are proud of?
- How you have changed?
- Any challenges you are facing and your plans for addressing them.
- Include reference to how you are going with your something awesome. Your logbook will include a summary link to that post.
All this came straight from the course outline
How to contact me?
REvil Lightning Talk
by Michelle Wong
5 min break 🥐
Case Study Time
Doors


You are the amazing Dick Smith. Skeptic, philanthropist, all round nice guy, and former Chairman of the Civil Aviation Safety Authority Board.
In light of the German Wings incident and the earlier EgyptAir incident the Civil Aviation Safety Authority, the government statutory authority responsible for the regulation of civil aviation, has asked you to return and lead a review into physical security of airplane cockpits and controls
You have been asked to consider the main lessons that that should be learned from these and other relevant incidents and to produce a shortlist of recommendations for actions to be taken to prevent future disasters.
Your review is widely supported including by the both houses of parliament, the public, Airbus, Boing, Airservices Australia, the major airlines which fly into Australia, the Australian Federation of Air Pilots, the Australian and International Pilots Association, the AFP and ASIO. These parties are all prepared to devote considerable resources to implement your recommendations.
Your Mission
Your Mission
State and justify your top 5 recommendations. Give them in decreasing order of importance (i.e. most important first).
In making your recommendations you have been asked to consider:
- Physical security of Airplane cockpits
- Related policies and practices for air crew on board a flight
- Reevaluate the need for co-pilots to be in the cockpit
- any additional requirements to place on airline companies
- any additional requirements to place on airplane manufacturers
- any additional requirements to place on air traffic controls and on airports
- consider requiring systems to be installed on planes which allow their controls to be overriden by air traffic control towers in extreme events
- Any other such matters relevant to the physical security of the cockpit in order to prevent the re-occurrence of German Wings type incidents in the future.
Everyone to spend 5 min on their own to think about:
- What happened?
- What are the assets to protect?
- What went wrong?
- Recommendations (and justifications)
We will then go into groups, discuss what you have and come up with your top 5 recommendations
The assets we want to protect:
- Human lives (both onboard and not)
- Equipment of the airline company (inc plane)
- Black box data
- Airline reputation (confidence in the airline)
- Airline company money
- Passengers belongings (luggage)
- Mental heath of those who have survived the incident and family who have lost loved ones.
- Political diplomacy
Our Recommendation
- The company opens a channel to allow pilots to talk to someone.
- Have an eval process to check their mental health / financial records. Create ways for workers to disclose their mental health problems in a safe way. Instead of firing them -> can transition them to another role.
- Autopilot ->
Final words
What are our thoughts / oppinons of the case study?
Why is this important?
How does this relate to security?