"S" is for "Secure"
HTTPS
HyperText Transfer Protocol Secure
SSL / TLS
Secure Sockets Layer
Transport Layer Security

+


=



+
=


+


=



+
=




private key
public key
Asymetric
Cryptography
Digital Signature


hash




+
=

Sign
Verify


hash



+
=
signature
== ?
handshake
client
server














+ =








+ =
+ + =











+ =






+ =





+ =






+ =






+ + =
handshake
client
server















+ =






+ =











+ =






+ =





+ =






+ =





attacker










+ + =
+ + =
Certificates
-----BEGIN CERTIFICATE-----
MIIGJjCCBQ6gAwIBAgISA+QXf7/R8dEixU+Nv8gYX46fMA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xNjExMTQwNTAwMDBaFw0x
NzAyMTIwNTAwMDBaMBcxFTATBgNVBAMTDHVuaXZhZGlzLmNvbTCCAiIwDQYJKoZI
hvcNAQEBBQADggIPADCCAgoCggIBAMHb7ldnrl9RMnjjIC0U4tqrvrpF7bGO72fe
tXb1VmK8EZxWtIp0L4+ribTpY/XVdSLkUFNHH3rr2crsblIbEsqRia8onkC6YzC5
UiVqIM9Lbqi+NjWCp6SfxfluxkzicKgNM1tvWfItR6AeoMp7uBPC+krOvW9FLd1g
1w2HrEZCeXBYjK1/8m4IH37o4vdUYnl6sGoMku8Yq5+uCREpK8m1qWpska0l+wok
fNidRzJlhyGlR+ZF9FKhE5SfC6RCaQ4bHOVcpEMGRLSqr1MBZVne+RdjJ+7/gRal
MEL49YCchdtLgOhBEb2CMAyx1lhqPkJdaLtaXKQ6f/MiWAis69eY3TOyvhd3uKg9
cY9nGggOU8ZTI2O/KpDpJu1HJr6m1myhSBmoDxd5a3Ar1Zm9HAa5q2LvqZowc+3O
fNGgRsIa1k8U3QR4P1M4hJEMjlmsv3wMFSHKtLA8ebTbheZpqxT0HZfLxy8Utri7
adB7PDdV49dvDApn5umRxIK772O/Hbn7+qALJqkOQIcKDW5YPvgUSbZwI9do800P
GcWl0My9mlgHO8I2zmlX48AUQipjF1dX/CRCLUAfQ/5Abv/4AzL26FUzxVLUWUHN
PF4fIRL41G0BQxIU+0Uejq8x94oyykb2kdial8EwniNpE33Go9alCVydd1r6hoGQ
vzrNbhg1AgMBAAGjggI3MIICMzAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYI
KwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYEFEfXCv6D
hAjWGL2SktsW0wvcDjKoMB8GA1UdIwQYMBaAFKhKamMEfd265tE5t6ZFZe/zqOyh
MHAGCCsGAQUFBwEBBGQwYjAvBggrBgEFBQcwAYYjaHR0cDovL29jc3AuaW50LXgz
LmxldHNlbmNyeXB0Lm9yZy8wLwYIKwYBBQUHMAKGI2h0dHA6Ly9jZXJ0LmludC14
My5sZXRzZW5jcnlwdC5vcmcvMEEGA1UdEQQ6MDiCFnNlY3VyZS11cy51bml2YWRp
cy5jb22CDHVuaXZhZGlzLmNvbYIQd3d3LnVuaXZhZGlzLmNvbTCB/gYDVR0gBIH2
MIHzMAgGBmeBDAECATCB5gYLKwYBBAGC3xMBAQEwgdYwJgYIKwYBBQUHAgEWGmh0
dHA6Ly9jcHMubGV0c2VuY3J5cHQub3JnMIGrBggrBgEFBQcCAjCBngyBm1RoaXMg
Q2VydGlmaWNhdGUgbWF5IG9ubHkgYmUgcmVsaWVkIHVwb24gYnkgUmVseWluZyBQ
YXJ0aWVzIGFuZCBvbmx5IGluIGFjY29yZGFuY2Ugd2l0aCB0aGUgQ2VydGlmaWNh
dGUgUG9saWN5IGZvdW5kIGF0IGh0dHBzOi8vbGV0c2VuY3J5cHQub3JnL3JlcG9z
aXRvcnkvMA0GCSqGSIb3DQEBCwUAA4IBAQCaSsks1yFmPl1nakpOlkhDnOZZsCtg
5S8PP/ddYQUX/59LrXey4IbRLrncrYp1u9XJdi5WDCgYe4tY5j0O9Un20Xm7p1q+
IRo70bfXZZZ7n00HHkeSphiS0w5ADnsbBwYXz0gejr8e7qGWYttoG03gZNE9G0u2
2HzK0OKWfmXz/I11bJXuWjcxp716A71WkX1oXWB2gwSXdf3FR/t2oZKi/bQQVSVw
QOPbu58t/LujQjAK8t2o86P47PoOIKgkyBdHOjwWq3897MOaLhj+HEIX1noWAdie
2KvuHn20O9liOEExGNMKR7gnL9XZWZGdo6RwYPuOGci6pP4+Gjh3bf5w
-----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
03:e4:17:7f:bf:d1:f1:d1:22:c5:4f:8d:bf:c8:18:5f:8e:9f
Signature Algorithm: sha256WithRSAEncryption
Issuer:
commonName = Let's Encrypt Authority X3
organizationName = Let's Encrypt
countryName = US
Validity
Not Before: Nov 14 05:00:00 2016 GMT
Not After : Feb 12 05:00:00 2017 GMT
Subject:
commonName = univadis.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:c1:db:ee:57:67:ae:5f:51:32:78:e3:20:2d:14:
e2:da:ab:be:ba:45:ed:b1:8e:ef:67:de:b5:76:f5:
56:62:bc:11:9c:56:b4:8a:74:2f:8f:ab:89:b4:e9:
63:f5:d5:75:22:e4:50:53:47:1f:7a:eb:d9:ca:ec:
6e:52:1b:12:ca:91:89:af:28:9e:40:ba:63:30:b9:
52:25:6a:20:cf:4b:6e:a8:be:36:35:82:a7:a4:9f:
c5:f9:6e:c6:4c:e2:70:a8:0d:33:5b:6f:59:f2:2d:
47:a0:1e:a0:ca:7b:b8:13:c2:fa:4a:ce:bd:6f:45:
2d:dd:60:d7:0d:87:ac:46:42:79:70:58:8c:ad:7f:
f2:6e:08:1f:7e:e8:e2:f7:54:62:79:7a:b0:6a:0c:
92:ef:18:ab:9f:ae:09:11:29:2b:c9:b5:a9:6a:6c:
91:ad:25:fb:0a:24:7c:d8:9d:47:32:65:87:21:a5:
47:e6:45:f4:52:a1:13:94:9f:0b:a4:42:69:0e:1b:
1c:e5:5c:a4:43:06:44:b4:aa:af:53:01:65:59:de:
f9:17:63:27:ee:ff:81:16:a5:30:42:f8:f5:80:9c:
85:db:4b:80:e8:41:11:bd:82:30:0c:b1:d6:58:6a:
3e:42:5d:68:bb:5a:5c:a4:3a:7f:f3:22:58:08:ac:
eb:d7:98:dd:33:b2:be:17:77:b8:a8:3d:71:8f:67:
1a:08:0e:53:c6:53:23:63:bf:2a:90:e9:26:ed:47:
26:be:a6:d6:6c:a1:48:19:a8:0f:17:79:6b:70:2b:
d5:99:bd:1c:06:b9:ab:62:ef:a9:9a:30:73:ed:ce:
7c:d1:a0:46:c2:1a:d6:4f:14:dd:04:78:3f:53:38:
84:91:0c:8e:59:ac:bf:7c:0c:15:21:ca:b4:b0:3c:
79:b4:db:85:e6:69:ab:14:f4:1d:97:cb:c7:2f:14:
b6:b8:bb:69:d0:7b:3c:37:55:e3:d7:6f:0c:0a:67:
e6:e9:91:c4:82:bb:ef:63:bf:1d:b9:fb:fa:a0:0b:
26:a9:0e:40:87:0a:0d:6e:58:3e:f8:14:49:b6:70:
23:d7:68:f3:4d:0f:19:c5:a5:d0:cc:bd:9a:58:07:
3b:c2:36:ce:69:57:e3:c0:14:42:2a:63:17:57:57:
fc:24:42:2d:40:1f:43:fe:40:6e:ff:f8:03:32:f6:
e8:55:33:c5:52:d4:59:41:cd:3c:5e:1f:21:12:f8:
d4:6d:01:43:12:14:fb:45:1e:8e:af:31:f7:8a:32:
ca:46:f6:91:d8:9a:97:c1:30:9e:23:69:13:7d:c6:
a3:d6:a5:09:5c:9d:77:5a:fa:86:81:90:bf:3a:cd:
6e:18:35
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
47:D7:0A:FE:83:84:08:D6:18:BD:92:92:DB:16:D3:0B:DC:0E:32:A8
X509v3 Authority Key Identifier:
keyid:A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1
Authority Information Access:
OCSP - URI:http://ocsp.int-x3.letsencrypt.org/
CA Issuers - URI:http://cert.int-x3.letsencrypt.org/
X509v3 Subject Alternative Name:
DNS:secure-us.univadis.com, DNS:univadis.com, DNS:www.univadis.com
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
Policy: 1.3.6.1.4.1.44947.1.1.1
CPS: http://cps.letsencrypt.org
User Notice:
Explicit Text: This Certificate may only be relied upon by Relying Parties and only in accordance with the Certificate Policy found at https://letsencrypt.org/repository/
Signature Algorithm: sha256WithRSAEncryption
9a:4a:c9:2c:d7:21:66:3e:5d:67:6a:4a:4e:96:48:43:9c:e6:
59:b0:2b:60:e5:2f:0f:3f:f7:5d:61:05:17:ff:9f:4b:ad:77:
b2:e0:86:d1:2e:b9:dc:ad:8a:75:bb:d5:c9:76:2e:56:0c:28:
18:7b:8b:58:e6:3d:0e:f5:49:f6:d1:79:bb:a7:5a:be:21:1a:
3b:d1:b7:d7:65:96:7b:9f:4d:07:1e:47:92:a6:18:92:d3:0e:
40:0e:7b:1b:07:06:17:cf:48:1e:8e:bf:1e:ee:a1:96:62:db:
68:1b:4d:e0:64:d1:3d:1b:4b:b6:d8:7c:ca:d0:e2:96:7e:65:
f3:fc:8d:75:6c:95:ee:5a:37:31:a7:bd:7a:03:bd:56:91:7d:
68:5d:60:76:83:04:97:75:fd:c5:47:fb:76:a1:92:a2:fd:b4:
10:55:25:70:40:e3:db:bb:9f:2d:fc:bb:a3:42:30:0a:f2:dd:
a8:f3:a3:f8:ec:fa:0e:20:a8:24:c8:17:47:3a:3c:16:ab:7f:
3d:ec:c3:9a:2e:18:fe:1c:42:17:d6:7a:16:01:d8:9e:d8:ab:
ee:1e:7d:b4:3b:d9:62:38:41:31:18:d3:0a:47:b8:27:2f:d5:
d9:59:91:9d:a3:a4:70:60:fb:8e:19:c8:ba:a4:fe:3e:1a:38:
77:6d:fe:70
Certificate content
- Serial Number
- Validity period
- Subject
- Public Key
- Issuer
- Signature
Subject:
commonName = univadis.com
Issuer:
commonName = Let's Encrypt Authority X3
organizationName = Let's Encrypt
countryName = US
X509v3 Subject Key Identifier:
47:D7:0A:FE:83:84:08:D6:18:BD:92:92:DB:16:D3:0B:DC:0E:32:A8
X509v3 Authority Key Identifier:
keyid:A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1
Subject:
commonName = Let's Encrypt Authority X3
organizationName = Let's Encrypt
countryName = US
Issuer:
commonName = DST Root CA X3
organizationName = Digital Signature Trust Co.
X509v3 Subject Key Identifier:
A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1
X509v3 Authority Key Identifier:
keyid:C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10
Subject:
commonName = DST Root CA X3
organizationName = Digital Signature Trust Co.
X509v3 Subject Key Identifier:
C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10
X509v3 Basic Constraints: critical
CA:TRUECertificate Authority
$ head -3 /etc/ssl/certs/DST_Root_CA_X3.pem
-----BEGIN CERTIFICATE-----
MIIDSjCCAjKgAwIBAgIQRK+wgNajJ7qJMDmGLvhAazANBgkqhkiG9w0BAQUFADA/
MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT
$ openssl x509 -in /etc/ssl/certs/DST_Root_CA_X3.pem -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
44:af:b0:80:d6:a3:27:ba:89:30:39:86:2e:f8:40:6b
Signature Algorithm: sha1WithRSAEncryption
Issuer: O=Digital Signature Trust Co., CN=DST Root CA X3
Validity
Not Before: Sep 30 21:12:19 2000 GMT
Not After : Sep 30 14:01:15 2021 GMT
Subject: O=Digital Signature Trust Co., CN=DST Root CA X3
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:df:af:e9:97:50:08:83:57:b4:cc:62:65:f6:90:
82:ec:c7:d3:2c:6b:30:ca:5b:ec:d9:c3:7d:c7:40:
c1:18:14:8b:e0:e8:33:76:49:2a:e3:3f:21:49:93:
ac:4e:0e:af:3e:48:cb:65:ee:fc:d3:21:0f:65:d2:
2a:d9:32:8f:8c:e5:f7:77:b0:12:7b:b5:95:c0:89:
a3:a9:ba:ed:73:2e:7a:0c:06:32:83:a2:7e:8a:14:
30:cd:11:a0:e1:2a:38:b9:79:0a:31:fd:50:bd:80:
65:df:b7:51:63:83:c8:e2:88:61:ea:4b:61:81:ec:
52:6b:b9:a2:e2:4b:1a:28:9f:48:a3:9e:0c:da:09:
8e:3e:17:2e:1e:dd:20:df:5b:c6:2a:8a:ab:2e:bd:
70:ad:c5:0b:1a:25:90:74:72:c5:7b:6a:ab:34:d6:
30:89:ff:e5:68:13:7b:54:0b:c8:d6:ae:ec:5a:9c:
92:1e:3d:64:b3:8c:c6:df:bf:c9:41:70:ec:16:72:
d5:26:ec:38:55:39:43:d0:fc:fd:18:5c:40:f1:97:
eb:d5:9a:9b:8d:1d:ba:da:25:b9:c6:d8:df:c1:15:
02:3a:ab:da:6e:f1:3e:2e:f5:5c:08:9c:3c:d6:83:
69:e4:10:9b:19:2a:b6:29:57:e3:e5:3d:9b:9f:f0:
02:5d
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Subject Key Identifier:
C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10
Signature Algorithm: sha1WithRSAEncryption
a3:1a:2c:9b:17:00:5c:a9:1e:ee:28:66:37:3a:bf:83:c7:3f:
4b:c3:09:a0:95:20:5d:e3:d9:59:44:d2:3e:0d:3e:bd:8a:4b:
a0:74:1f:ce:10:82:9c:74:1a:1d:7e:98:1a:dd:cb:13:4b:b3:
20:44:e4:91:e9:cc:fc:7d:a5:db:6a:e5:fe:e6:fd:e0:4e:dd:
b7:00:3a:b5:70:49:af:f2:e5:eb:02:f1:d1:02:8b:19:cb:94:
3a:5e:48:c4:18:1e:58:19:5f:1e:02:5a:f0:0c:f1:b1:ad:a9:
dc:59:86:8b:6e:e9:91:f5:86:ca:fa:b9:66:33:aa:59:5b:ce:
e2:a7:16:73:47:cb:2b:cc:99:b0:37:48:cf:e3:56:4b:f5:cf:
0f:0c:72:32:87:c6:f0:44:bb:53:72:6d:43:f5:26:48:9a:52:
67:b7:58:ab:fe:67:76:71:78:db:0d:a2:56:14:13:39:24:31:
85:a2:a8:02:5a:30:47:e1:dd:50:07:bc:02:09:90:00:eb:64:
63:60:9b:16:bc:88:c9:12:e6:d2:7d:91:8b:f9:3d:32:8d:65:
b4:e9:7c:b1:57:76:ea:c5:b6:28:39:bf:15:65:1c:c8:f6:77:
96:6a:0a:8d:77:0b:d8:91:0b:04:8e:07:db:29:b6:0a:ee:9d:
82:35:35:10
$ curl -I https://www.univadis.com
curl: (60) SSL certificate problem: unable to get local issuer certificate
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
$ docker run --rm -ti debian bash
$ apt-get update
$ apt-get install -y --no-install-recommends curl
$ apt-get install -y --no-install-recommends ca-certificates
$ curl -I https://www.univadis.com
HTTP/1.1 200 OK
DV
Domain Validation
~ 150$
/year
OV
Organisation Validation
~ 250$
/year
EV
Extended Validation
~ 450$
/year


https://github.com/letsencrypt/letsencrypt
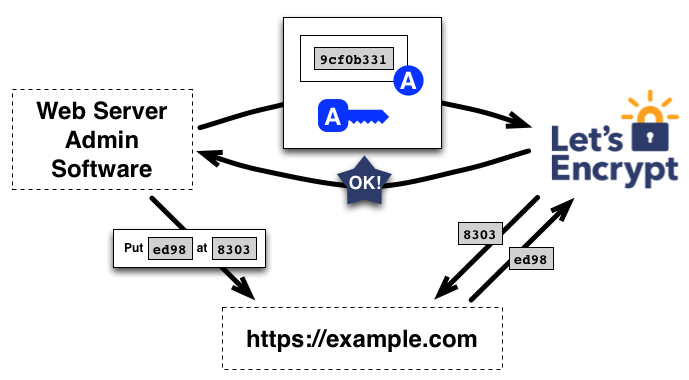
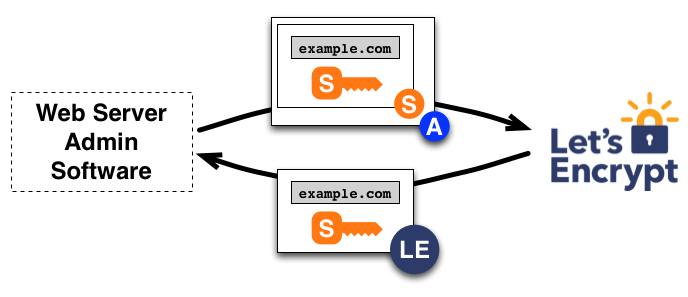
Pro
- free
- fully automated
- not auth required
- SANs
Con
- 90 days validity
- no wildcard
- no OV / EV
select algorithms
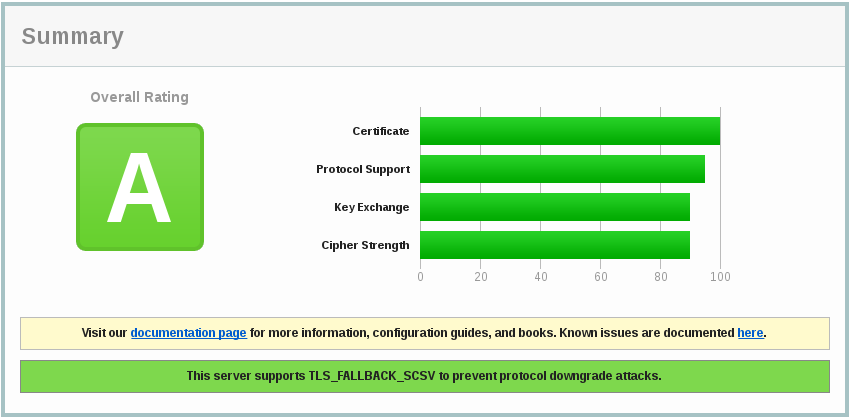
https://www.ssllabs.com/ssltest/
# apache2.conf
SSLHonorCipherOrder on
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDHE-ECDSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
https://mozilla.github.io/server-side-tls/ssl-config-generator/
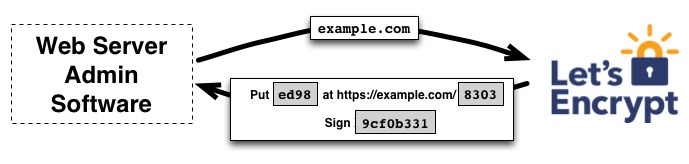
Architecture
Web Server
Pro:
- Easy to setup
Con:
- Not scalable
Load Balancer
Web Server
Web Server
Pro:
- Only one certificate
Con:
- Man in the middle attack
Load Balancer
Web Server
Web Server
Pro:
- fully secured
Con:
- Many certificate locations
- No session balancing
Load Balancer
Web Server
Web Server
Reverse Proxy
Questions ?
One more thing
What others know
What I know
What I think
What I know
Reallity
Knowledge
Aptus talk #1 ?
- Cryptography symmetric and asymmetric
- What's docker, how it works
- Docker in production, how to scale, and monitor
- End 2 End encryption
- Javascript Event Loop and promise
- Javascript advanced with ES6
- AngularJs, React, Redux and co.
- Mongodb and it aggregation framework
- Security vulnerabilities and OWASP
- Git and successful branching model
- Functional testing with gherkin language
- Photography
- ...