HTTP/2.0

The Future of HTTP
What began as a simple, one-line protocol for retrieving hypertext quickly evolved into a generic hypermedia transport, and now a decade later can be used to power just about any use case you can imagine.
However, HTTP has struggled under the weight of it's success as we have increasing demands form web applications.
The primary goals for HTTP/2 are to reduce latency by:
- Data compression of HTTP headers
- HTTP/2 Server Push.
- Pipelining of requests
- Fixing the head-of-line blocking problem in HTTP 1.x
-
Multiplexing multiple requests over a single TCP connection
It is important to note that HTTP/2 is extending, not replacing, the previous HTTP standards.
Multiplexing
With HTTP/1.x, if the client wants to make multiple parallel requests to improve performance, then multiple TCP connections must be used;
This snapshot captures multiple streams in flight within the same connection:
- The client is transmitting a DATA frame (stream 5) to the server
- While the server is transmitting an interleaved sequence of frames to the client for streams 1 and 3.
- As a result, there are three parallel streams in flight!

Server Push
The server can now send multiple responses for a single client request.
That is, in addition to the response to the original request, the server can
push additional resources to the client, without the client having to request each one explicitly!
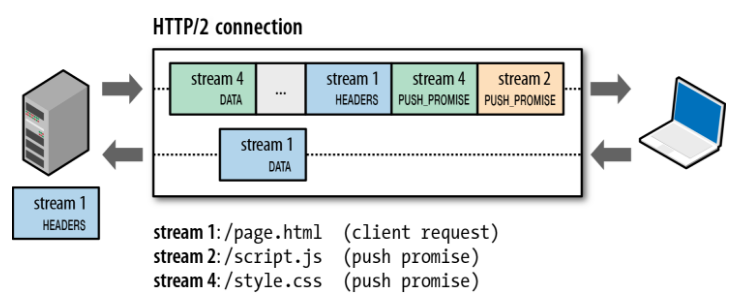
HTTP/2 breaks away from the strict request-response semantics and enables one-to-many and server-initiated push workflows that open up a world of new interaction possibilities both within and outside the browser.
HTTP/2 Crash Course
Firstly, many clients and browsers are not planning on implementing the ability to use HTTP/2 over plain-text, even though this is in the protocols specification. So we will need to make
// lets generate a 2048 bit private key for our server
// note that we specify the key passphrase as ‘x’ using the flag ‘-passout pass:x’
$ mkdir node-http && cd node-http
$ openssl genrsa -des3 -passout pass:x -out server.pass.key 2048
// We now need to remove the passphrase from this key so it can be loaded
// into our HTTP server, we then remove the original key:
$ openssl rsa -passin pass:x -in server.pass.key -out server.key
$ rm server.pass.key// Now we need to generate the certificate signing request in order to
// validate who we are
$ openssl req -new -key server.key -out server.csr
// Finally, we can (self) sign our certificate:
$ openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crtGenerating a TLS certificate
You now should have three extra files within the node-http2 directory:
- server.crt — Your new TLS certificate
- server.key — Your TLS certificate private key
-
server.
csr — Your TLS certificate signing request
$ npm install spdyBuilding Our HTTP/2 Server
Let’s start by installing the npm module
Create an app.js file and require spdy and fs
let options = {
key: fs.readFileSync(__dirname + '/server.key'),
cert: fs.readFileSync(__dirname + '/server.crt')
};Specify the locations of the certificate and private key we just created:
'use strict';
let spdy = require('spdy'),
fs = require('fs');