Blockchain
Distributed Ledger Technology & Smart Contracts


-
Doctoral Researcher @ Institute for Internet Security
- Head of Blockchain Research Lab
- Consultant @ Styrascosoft GbR
- Testcontainers Maintainer and Open Source Enthusiast
- Oracle Groundbreaker Ambassador
- GitKraken Ambassador
- Organizer Software Crafting Meetup Ruhr
Kevin Wittek @kiview


Historic Context
From Time-Sharing Systems to the World Computer

Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly after they and their Bell Labs colleagues invented Unix. - The Strange Birth and Long Life of Unix, https://spectrum.ieee.org/tech-history/cyberspace/the-strange-birth-and-long-life-of-unix
Trust
"We have proposed a system for electronic transaction without relying on trust."
Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System, 2008

Trust Architectures
Reflections on Trusting Trust
"To what extent should one trust a statement that a program is free of Trojan horses? Perhaps It is more Important to trust the people who wrote the software." - Ken Thompson, Turing Award Lecture, 1984

https://dl.acm.org/doi/10.1145/358198.358210
History of Utility Computing
- 1964: Multics Time-Sharing OS - MIT, Bell Labs...
- Vision of modelling computing resources after telephone and electrical utilities
- 1969 - 1989: ARPANET, Internet / World Wide Web
- 1974: Project Xanadu & Docuvers
- 2006: Cloud Computing, AWS EC2
- 2009: Bitcoin network - Decentralized state machine
- 2015: Ethereum network - Turing complete virtual machine & decentralized state machine
Blockchain
The Invention of Bitcoin and the Rise of Cryptocurrencies
Pre Bitcoin era: Hashcash
- Invented by Adam Back in 1997
- http://www.hashcash.org/hashcash.pdf
- System for throttling abuse of unmetered internet resources
- Example: E-Mail spam
- Client needs to solve CPU intensive puzzle before a valid connections is established
- Try to find counter value, so that SHA1(header) starts with 5 leading zeros
ver:bits:date:resource:ext:rand:counter
X-Hashcash: 1:20:1303030600:adam@cypherspace.org::McMybZIhxKXu57jd:ckviBitcoin: A Peer-to-Peer Electronic Cash System
- 2008: Paper published by Satoshi Nakamoto on "The Cryptography Mailing List"
- January 2009: Genesis block was mined

By Ladislav Mecir - Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=83020772
Bitcoin as a Cryptocurrency
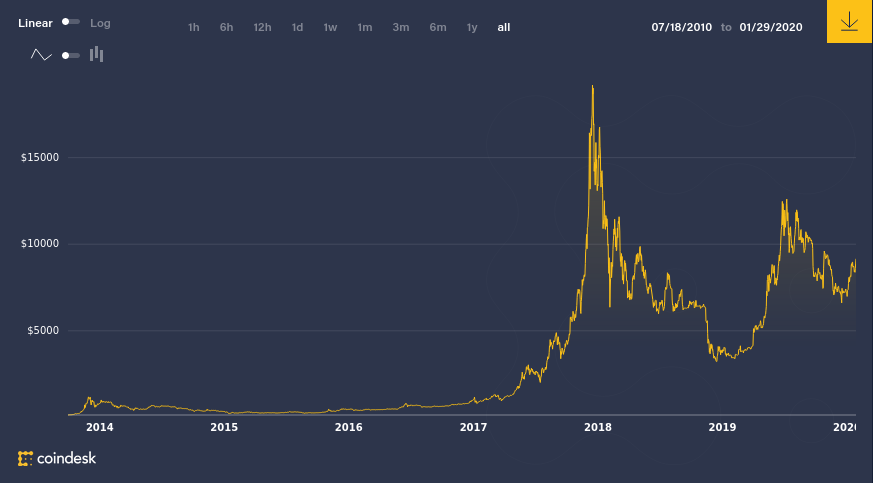
https://www.coindesk.com/price/bitcoin
List of Cryptocurrencies

https://www.coinlore.com/all_coins
Technical Properties
- Decentralized p2p network
- Public Distributed Ledger (DLT) implemented as a blockchain
- Proof-of-Work based "consensus"
- Based on hashcash's PoW algorithm
- Not BFT, but similar resilience properties
- Longest chain wins
- 51% attack possible (also happened in the past)
- Incentivized by dynamic transaction fees
Byzantine Generals Problem
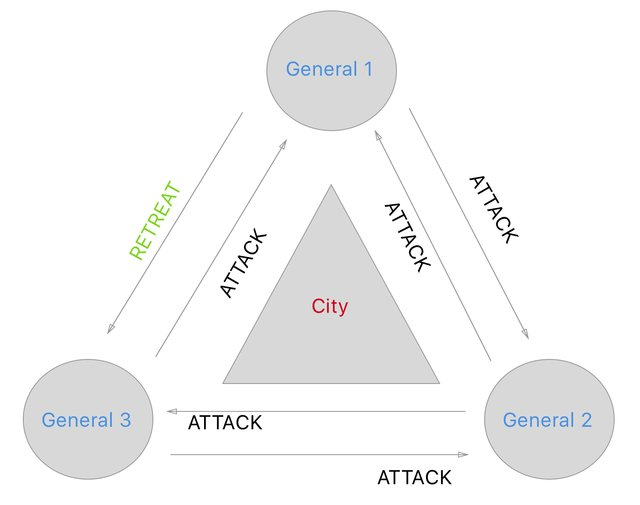
Makrakis, Georgios Michail. (2018). Evaluating the performance of Distributed Ledger - Blockchain technologies in IoT environment. 10.13140/RG.2.2.23024.10248.
Transactions
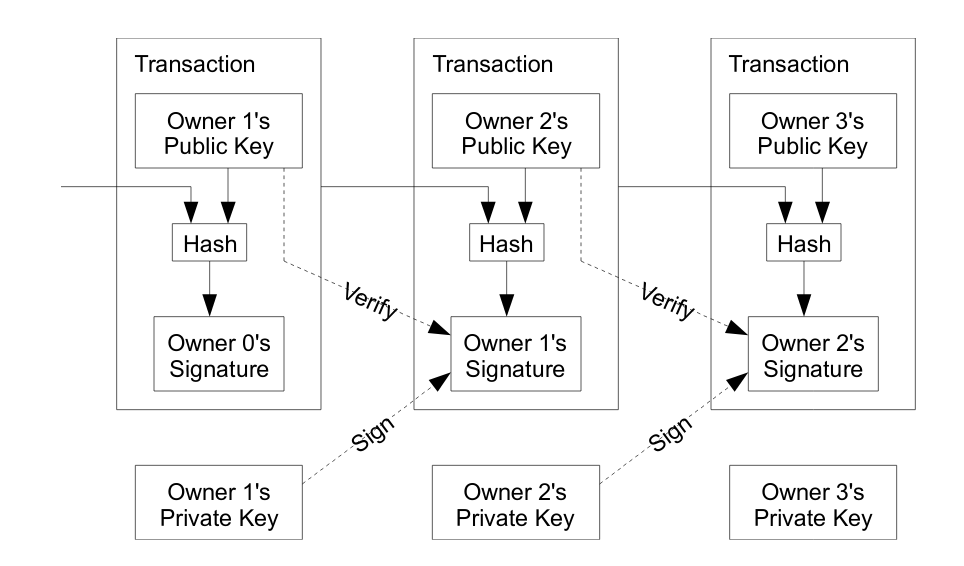
Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System, 2008
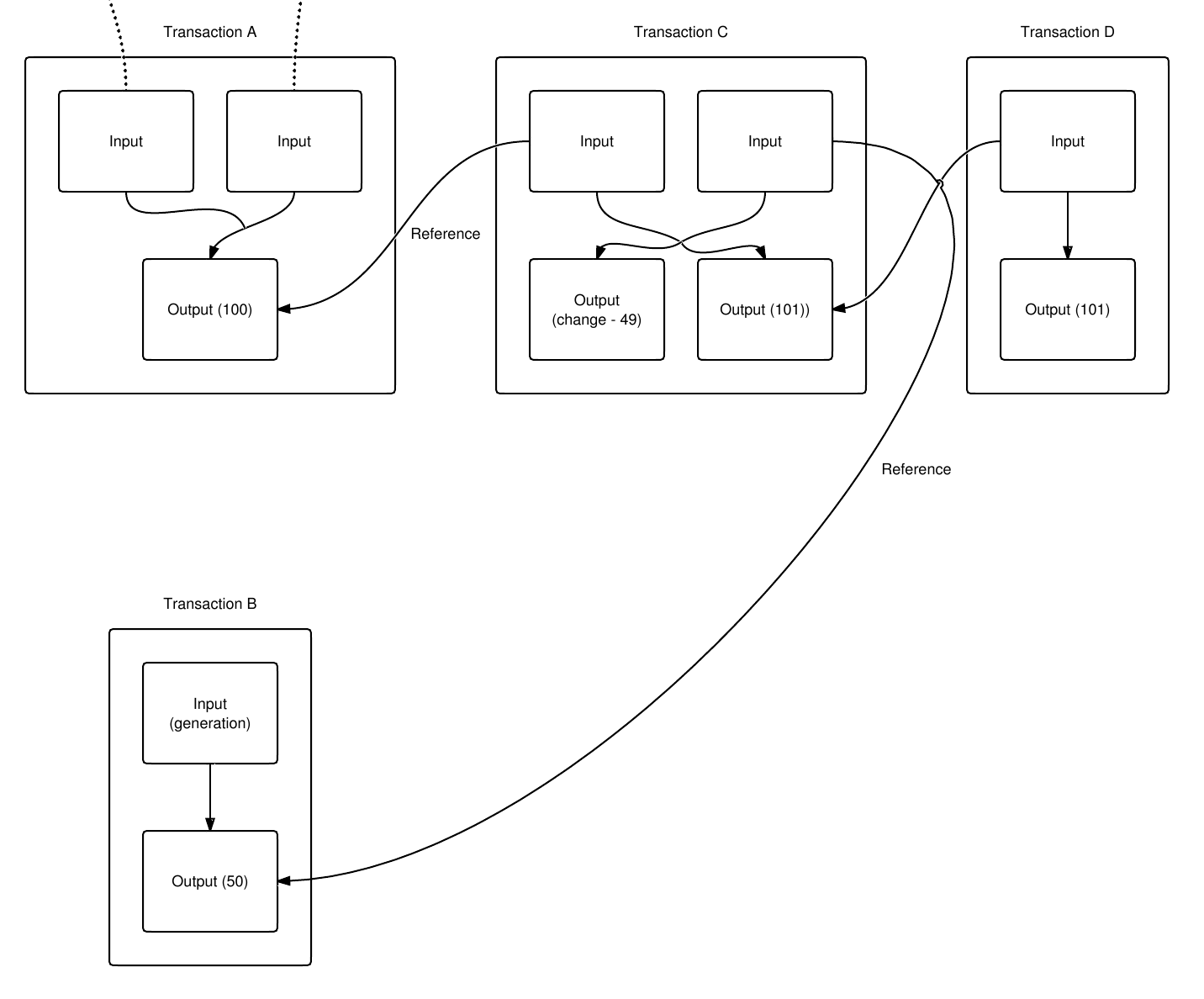
Multiple Inputs/Outpus
Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System, 2008
BTC Blockchain Data Structure
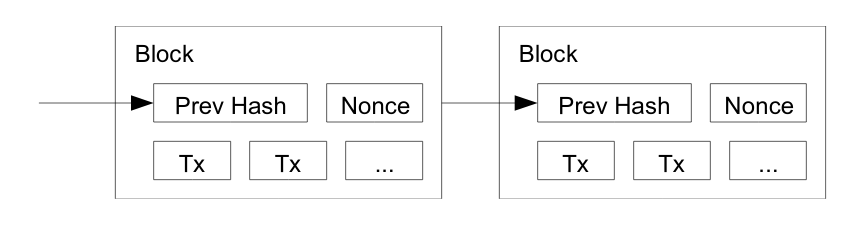
Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System, 2008
Merkle Tree
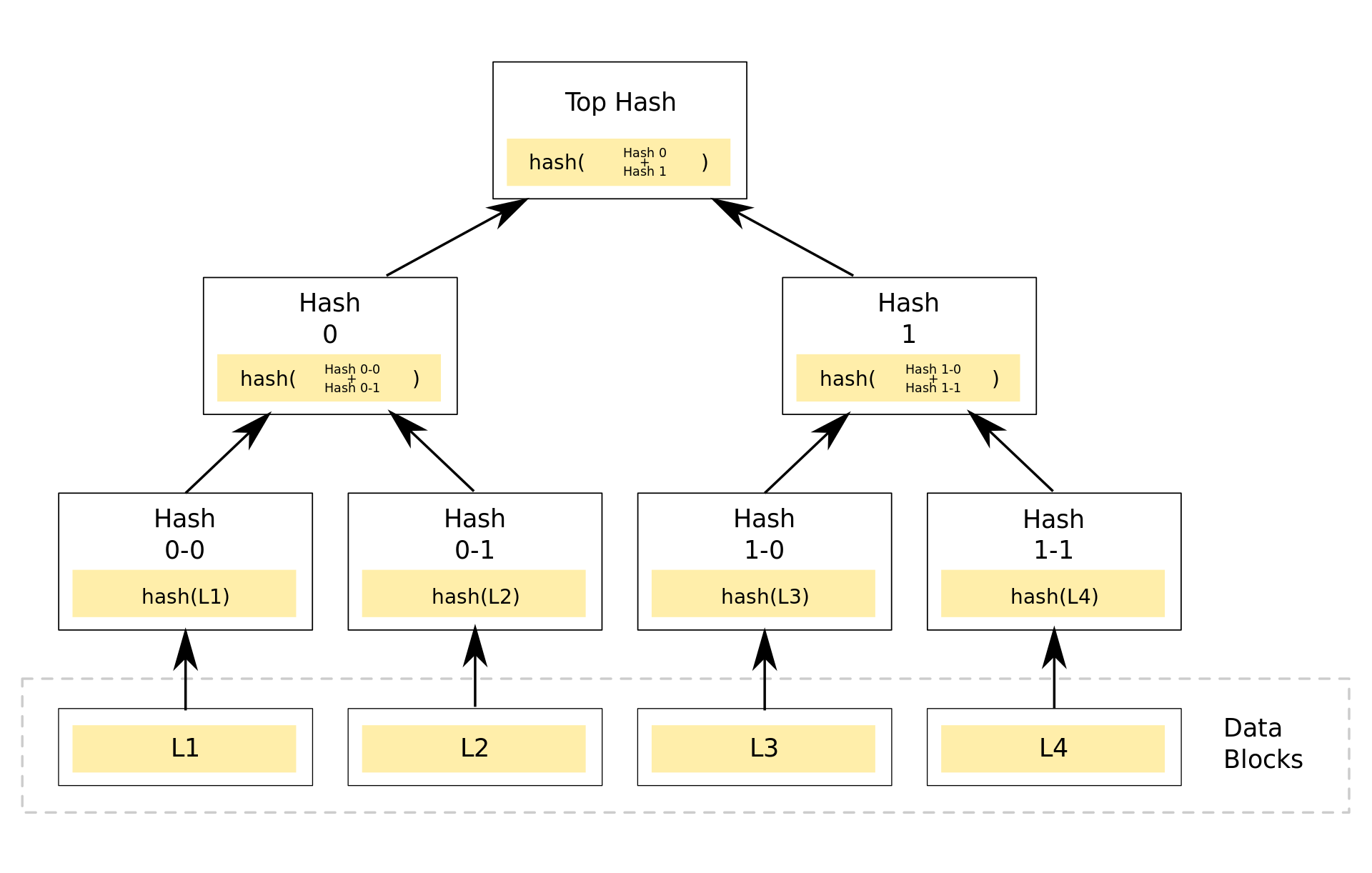
By Azaghal - Own work, CC0, https://commons.wikimedia.org/w/index.php?curid=18157888
BTC Actual Data Structure
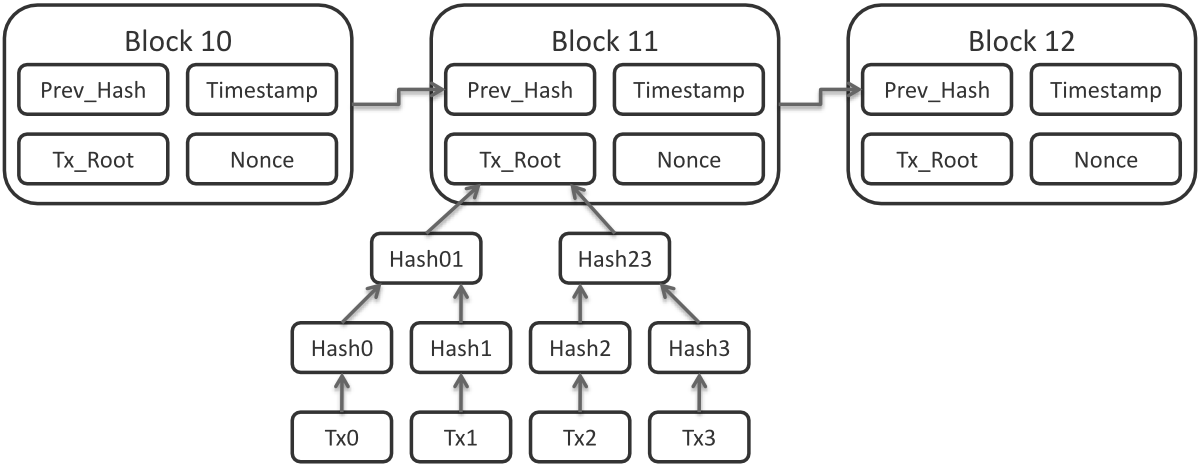
By Matthäus Wander - Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=26816937
Proof of Work
- Hash block header
- Guess/Increment nonce until hash < target is found
- Bitcoin: SHA256(SHA256(Block_Header))
- Protect against length-extension attacks, SHA-256d
- No protection against birthday attacks!
- (Extra nonce as part of merkle tree, but ignored in this example)
block_version = "01000000"
hash_prev_block = "81cd02ab7e569e8bcd9317e2fe99f2de44d49ab2b8851ba4a308000000000000"
hash_merkle_root = "e320b6c2fffc8d750423db8b1eb942ae710e951ed797f7affc8892b0f1fc122b"
time = "c7f5d74d"
target = "f2b9441a" # in bits format
nonce = get_next_nonce()
while calc_block_hash(block_version \
+ hash_prev_block \
+ hash_merkle_root \
+ time \
+ target \
+ nonce) < target:
nonce = get_next_nonce()
The Five Pillars of Open Blockchains
- Open
- Borderless
- Neutral
- Censorship-Resistant
- Public
Types of Blockchain Networks
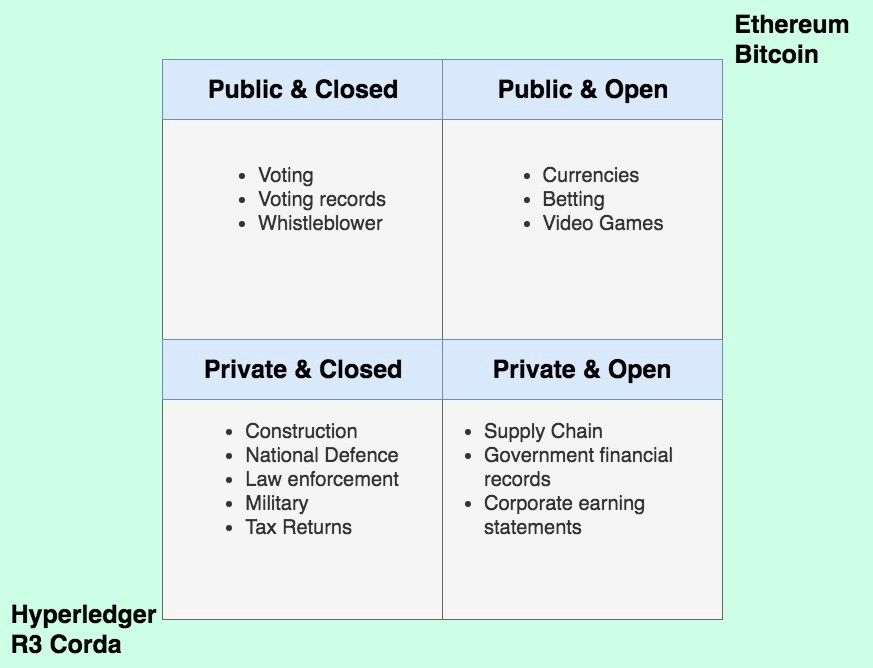
https://medium.com/coinmonks/public-vs-private-blockchain-in-a-nutshell-c9fe284fa39f
Consensus Algorithms

Smart Contracts
When Code is Law?
Code Is Law
On Liberty in Cyberspace
"[...] We should interrogate the architecture of cyberspace as we interrogate the code of Congress.
Unless we do, or unless we learn how, the relevance of our constitutional tradition will fade. The importance of our commitment to fundamental values, through a self-consciously enacted constitution, will fade. We will miss the threat that this age presents to the liberties and values that we have inherited. The law of cyberspace will be how cyberspace codes it, but we will have lost our role in setting that law." - Lawrence Lessig, https://harvardmagazine.com/2000/01/code-is-law-html

Joi Ito [CC BY (https://creativecommons.org/licenses/by/2.0)]
Origin of Smart Contracts
- Concept and term first mentioned in 1997 paper by Nick Szabo
- Formalizing and Securing Relationships on Public Networks (https://firstmonday.org/ojs/index.php/fm/article/view/548)
- Derived article "The Idea of Smart Contracts", 1997
- "A canonical real-life example, which we might consider to be the primitive ancestor of smart contracts, is the humble vending machine."
- Unlocking cryptographic keys for accessing properties (e.g. cars) as another example.
Ethereum
- First described in whitepaper by Vitalik Butekin in 2013
- Current version: https://github.com/ethereum/wiki/wiki/White-Paper
- Motivated by lack of scripting capabilities in Bitcoin
- Yellow paper defining Ethereum Virtual Machine written by Gavin Wood in 2014
- Solidity as first programming language for EVM SCs
- Executes EVM byte code
- Turing complete
- Different implementations in different languages exist
- Infrastructure for building DApps

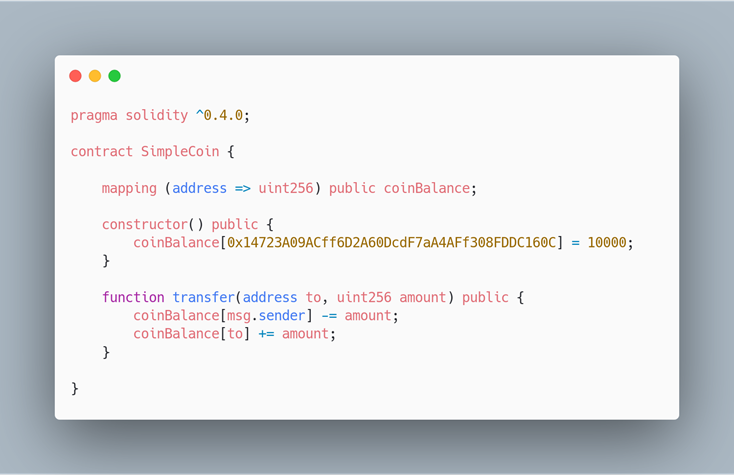
The Coin of Plenty
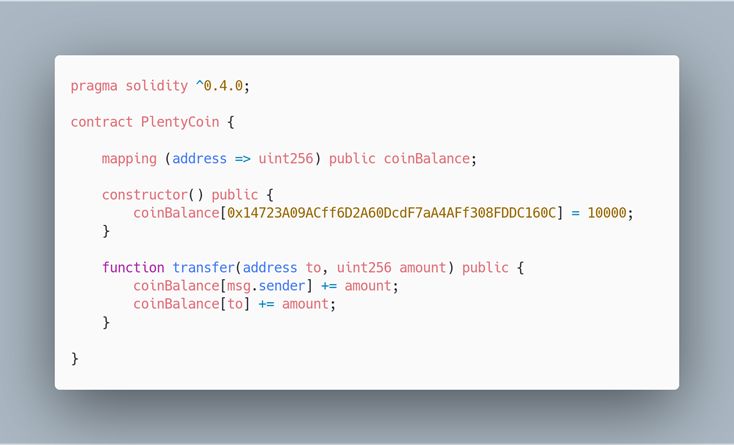
Fixed Contract
Ethereum Full Node
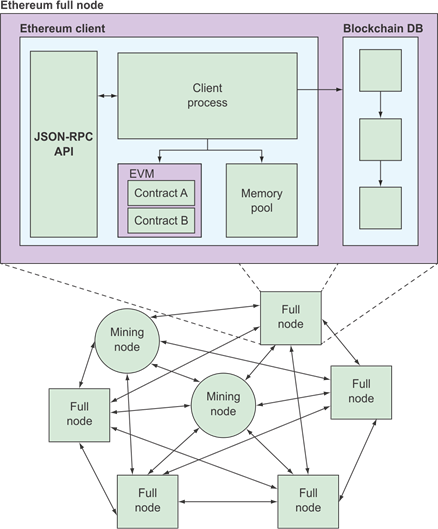
https://www.manning.com/books/building-ethereum-dapps
EVM (layers)
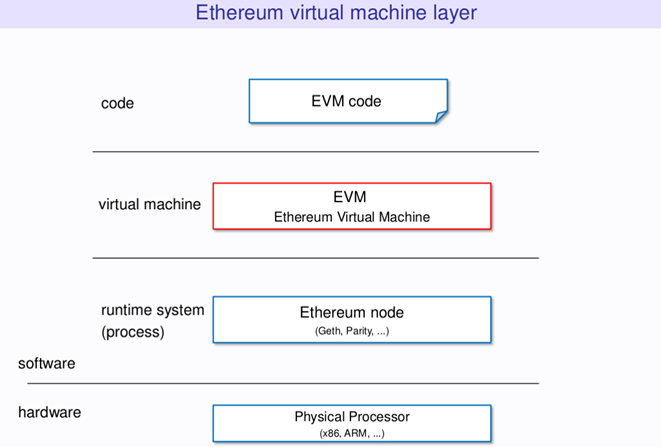
https://hackernoon.com/getting-deep-into-evm-how-ethereum-works-backstage-ac7efa1f0015
EMV (Architecture)
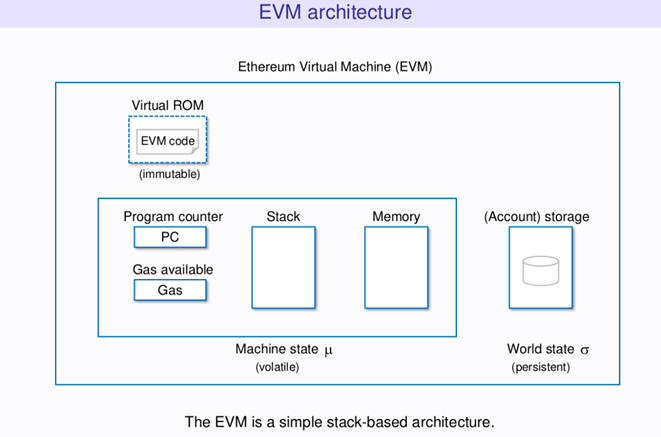
https://hackernoon.com/getting-deep-into-evm-how-ethereum-works-backstage-ac7efa1f0015
Compiling and Deploying a Solidity Contract
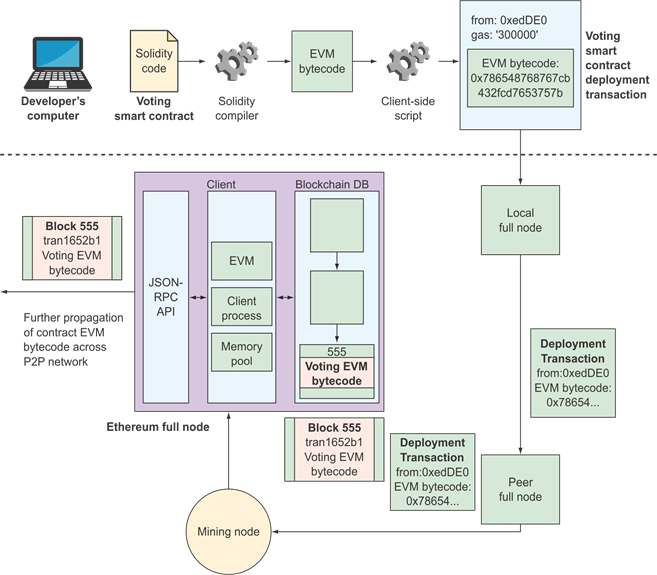
https://www.manning.com/books/building-ethereum-dapps
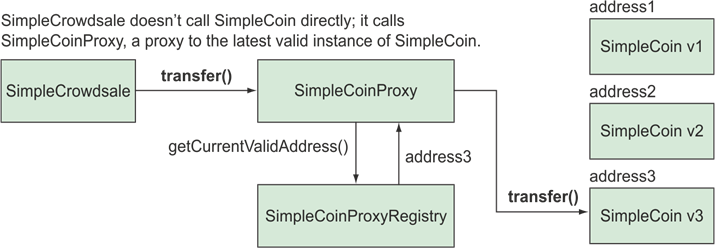
Upgradability (Proxy Pattern)
https://www.manning.com/books/building-ethereum-dapps
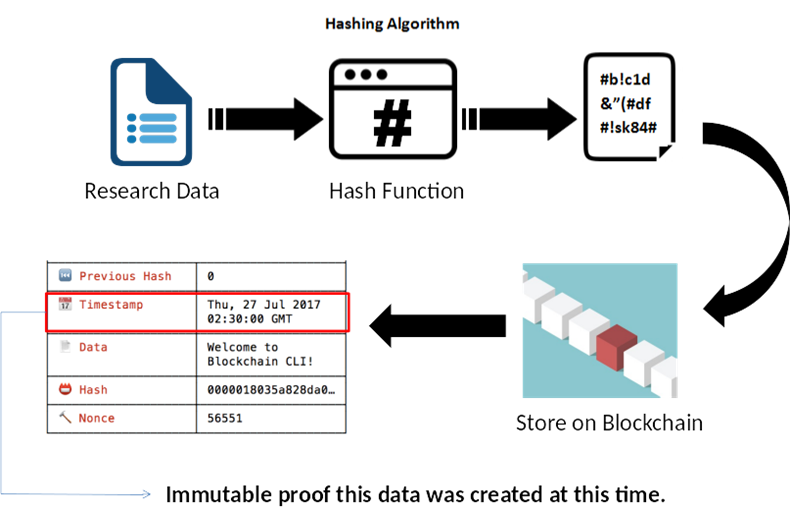
Certification of Research Data
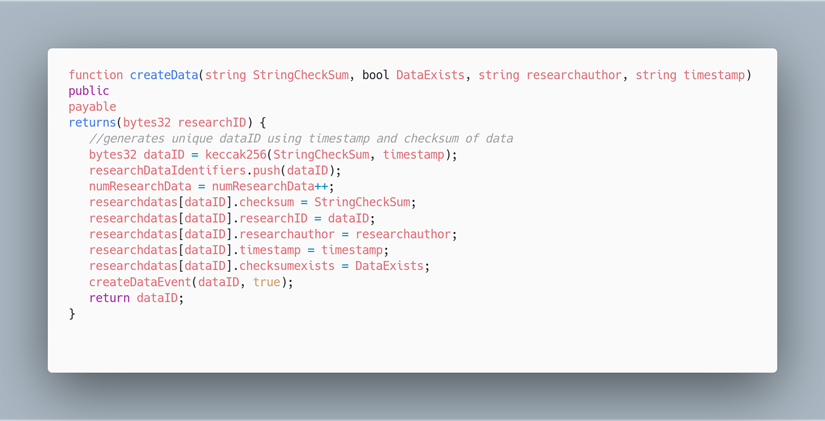
Contract certifiyResearchData(1)
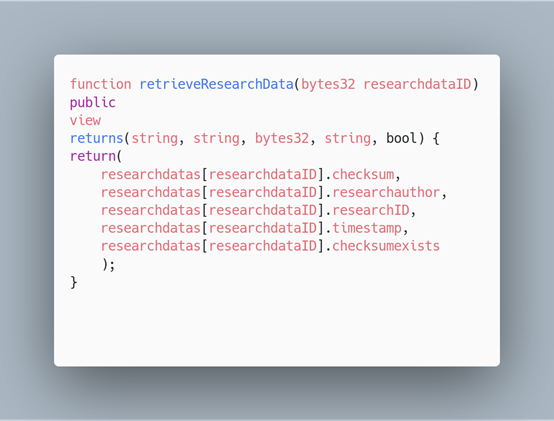
Contract certifiyResearchData(2)
DApps and non-fungible Tokens
https://www.cryptokitties.co/
Interacting with DApps
What's next?
Tangles, Token Engineering, Foundations...
Hyperledger
Linux Fonudation

https://www.hyperledger.org/
Enterprise Ethereum Alliance


https://entethalliance.org/
Other Projects
- R3 Corda
- Financial trading
- IOTA
- Uses tangle instead of chain
Project Alvarium

https://alvarium.org/
"Project Alvarium will be aimed at building Data Confidence Fabrics that deliver data from devices to applications with measurable confidence."
Self Sovereign Identity (SSI)
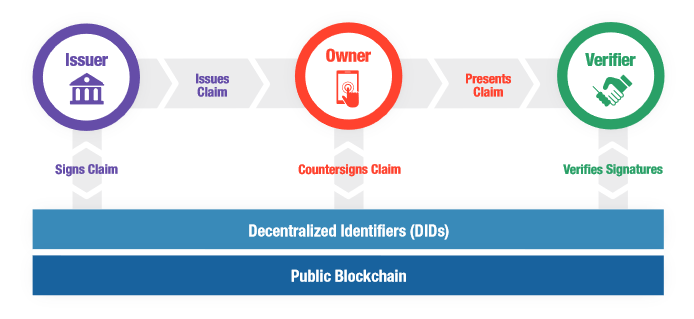
https://sovrin.org/wp-content/uploads/2018/03/Sovrin-Protocol-and-Token-White-Paper.pdf
Token Engineering
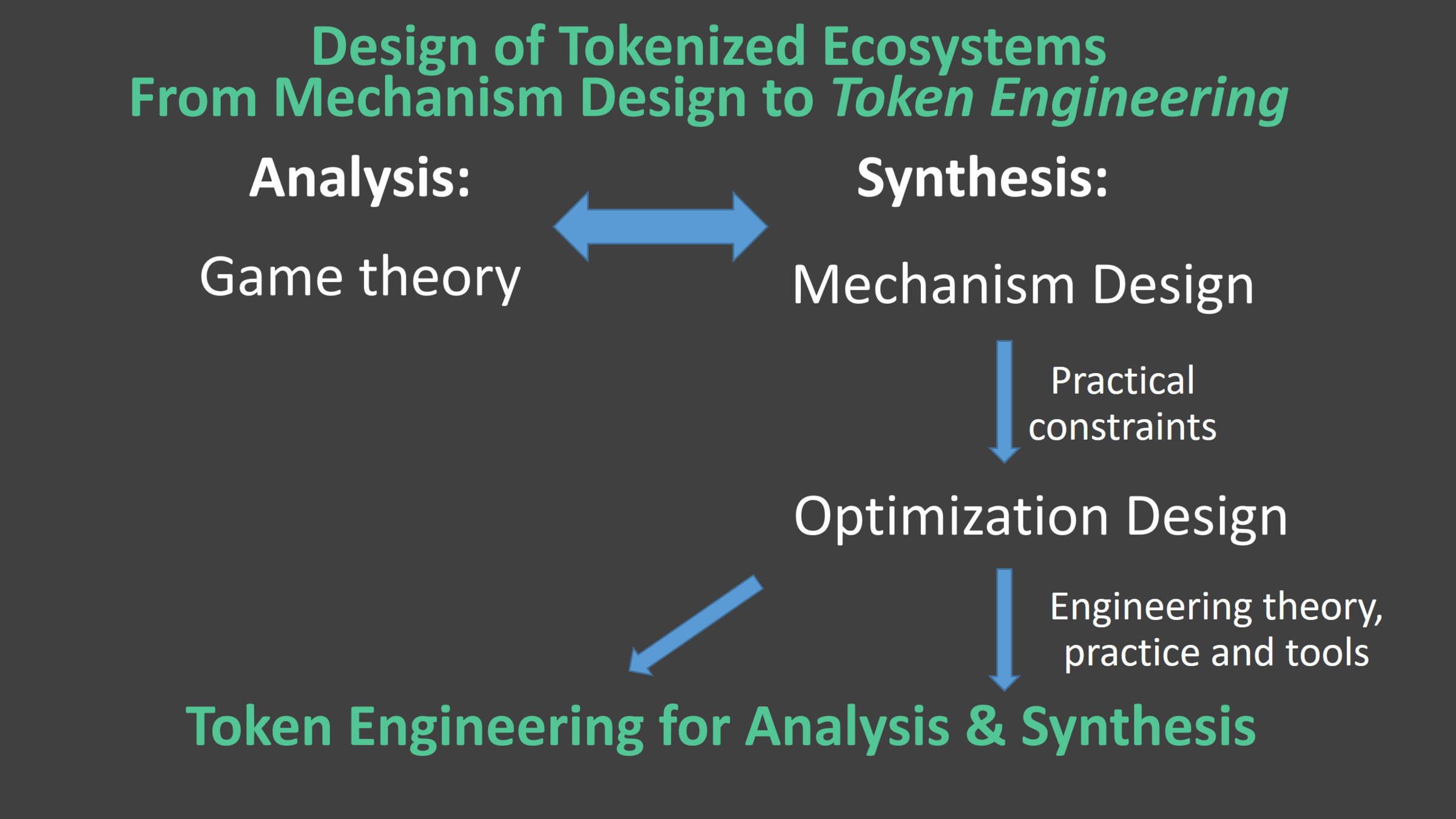
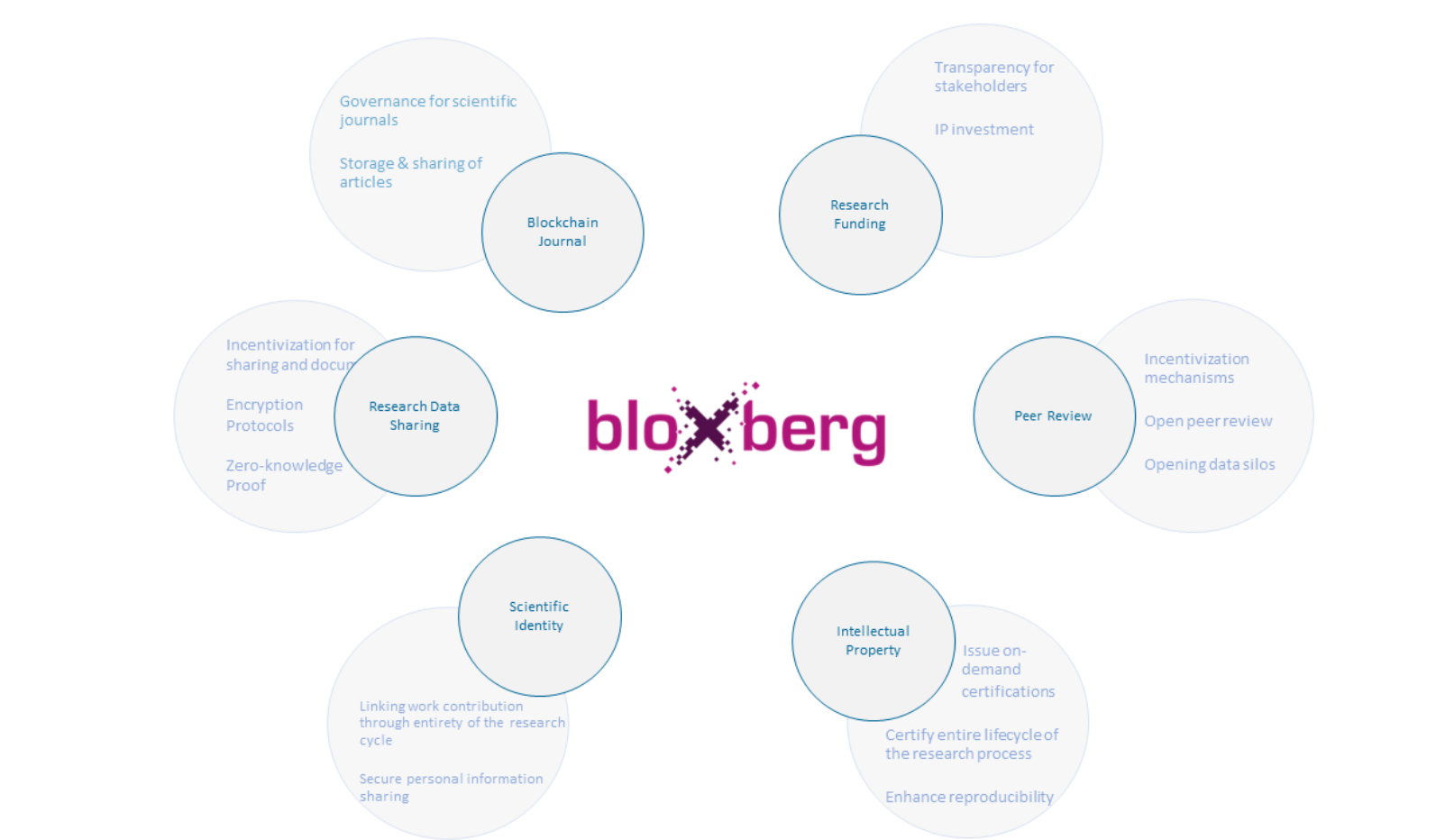
Bloxberg

Use Cases
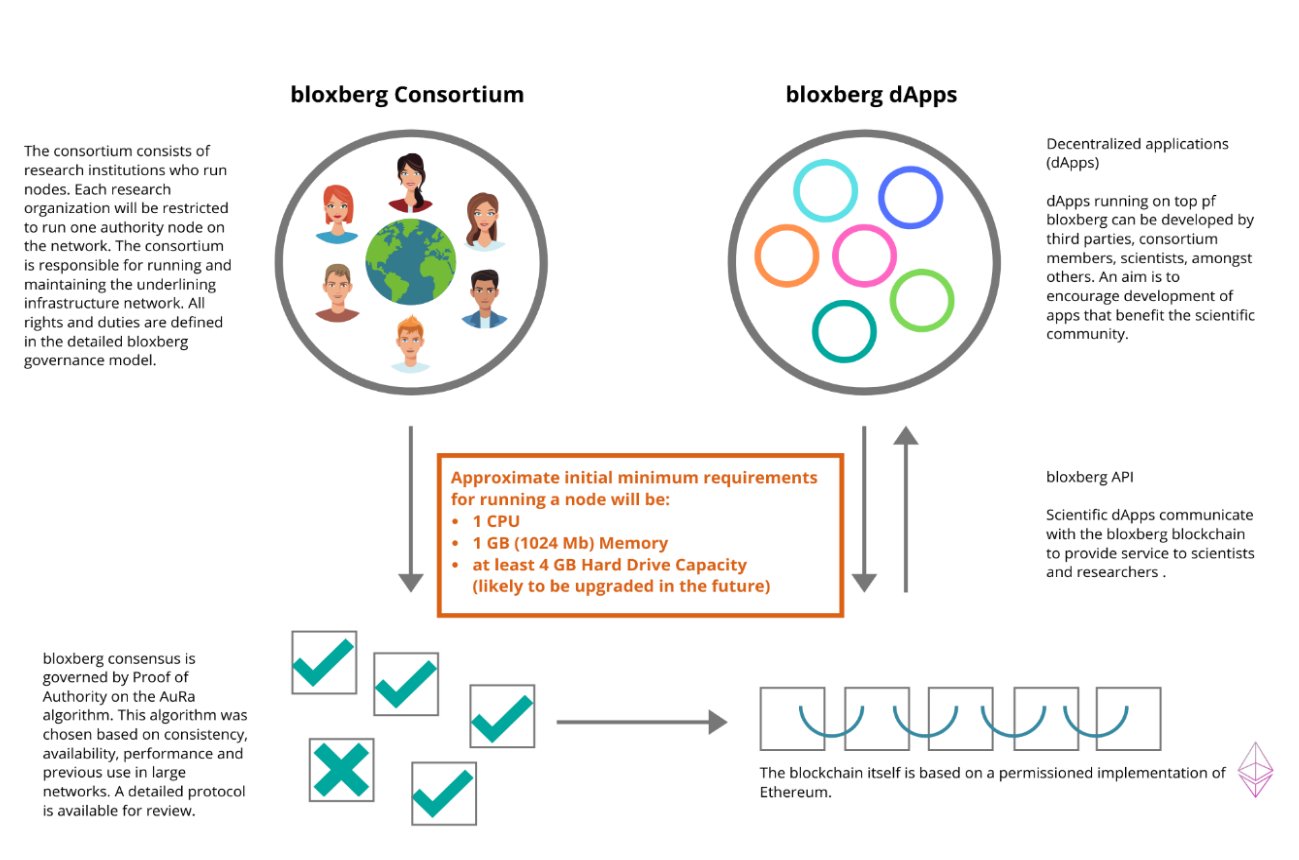
Consortium
Bloxberg Hackathon planned!
- Westfälische Hochschule
- Single-day, end of May?
- Open for students, scientists and developers
- Learn the development of DApps for Bloxberg