TDOH-PIPE 201704
資訊安全讀書會
早上好!我是洋蔥
應該還是有人不認識我

讀書會歡迎大家
踴躍參與討論!
文件上傳漏洞
Unrestricted File Upload
顧名思義
駭客可以任意把檔案傳到伺服器上面去
可以幹嘛?
正確使用

不正確使用?


發生了什麼事!?

哎呀今天講上傳漏洞
一定是被你傳上去啦

駭客可以幹嘛?
- 上傳可執行的文件,例如:PHP、JSP
- 上傳釣魚網頁
- 偷資料
- 當跳板
- 把機器搞到當機
- 幫學校系統修 bug (?
- etc

Some Upload Vul on exploit-db
怎麼發生?
可能出現的狀況
- 未檢查檔案類型
- 檔名沒過濾路徑
- 伺服器設定有誤
- etc...
我們來看看怎麼寫上傳
來看網路上的一段範例扣
<?php
if ($_FILES["file"]["error"] > 0){
echo "Error: " . $_FILES["file"]["error"];
}else{
echo "檔案名稱: " . $_FILES["file"]["name"]."<br/>";
echo "檔案類型: " . $_FILES["file"]["type"]."<br/>";
echo "檔案大小: " . ($_FILES["file"]["size"] / 1024)." Kb<br />";
echo "暫存名稱: " . $_FILES["file"]["tmp_name"];
if (file_exists("upload/" . $_FILES["file"]["name"])){
echo "檔案已經存在,請勿重覆上傳相同檔案";
}else{
move_uploaded_file($_FILES["file"]["tmp_name"],"upload/".$_FILES["file"]["name"]);
}
}他們用什麼判斷類型?
$_FILES['userfile']['type']
$_FILES['userfile']['type']
The mime type of the file, if the browser provided this information. An example would be "image/gif". This mime type is however not checked on the PHP side and therefore don't take its value for granted.
最常出現的問題
不要信任 MIME Type
使用者端的資料都不可信
- 只檢查 MIME
- 只檢查副檔名
- 只檢查檔頭
Check if is a actual image
<?php
$target_dir = "uploads/";
$target_file = $target_dir . basename($_FILES["fileToUpload"]["name"]);
$uploadOk = 1;
$imageFileType = pathinfo($target_file,PATHINFO_EXTENSION);
// Check if image file is a actual image or fake image
if(isset($_POST["submit"])) {
$check = getimagesize($_FILES["fileToUpload"]["tmp_name"]);
if($check !== false) {
echo "File is an image - " . $check["mime"] . ".";
$uploadOk = 1;
} else {
echo "File is not an image.";
$uploadOk = 0;
}
}
?>可是瑞凡,官方說別用
getimagesize()

Do not use getimagesize() to check that a given file is a valid image.

其實最危險的是 Google
web常见攻击六——文件上传漏洞
安全的图片验证类型可以这样写$uploaded_ext == “jpg” || $uploaded_ext == “JPG” || $uploaded_ext == “jpeg” || $uploaded_ext == “JPEG”),呵呵,也不难是吧,其实有些事情就这么简单,只是我们不知道而已。
<?php
if (isset($_POST['Upload'])) {
$target_path = DVWA_WEB_PAGE_TO_ROOT."hackable/uploads/";
$target_path = $target_path . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_ext = substr($uploaded_name, strrpos($uploaded_name, '.') + 1);
$uploaded_size = $_FILES['uploaded']['size'];
if (($uploaded_ext == "jpg" || $uploaded_ext == "JPG" || $uploaded_ext == "jpeg" || $uploaded_ext == "JPEG") && ($uploaded_size < 100000)){
if(!move_uploaded_file($_FILES['uploaded']['tmp_name'], $target_path)) {
echo '';
echo 'Your image was not uploaded.';
echo '';
} else {
echo '';
echo $target_path . ' succesfully uploaded!';
echo '';
}
}
else{
echo '';
echo 'Your image was not uploaded.';
echo '';
}
}
?>;
還有什麼情況
- 資料夾權限設置錯誤
- 資料庫隱碼攻擊
- 未阻擋上傳設定檔
正確的檔案檢查方式
finfo_open
課堂練習
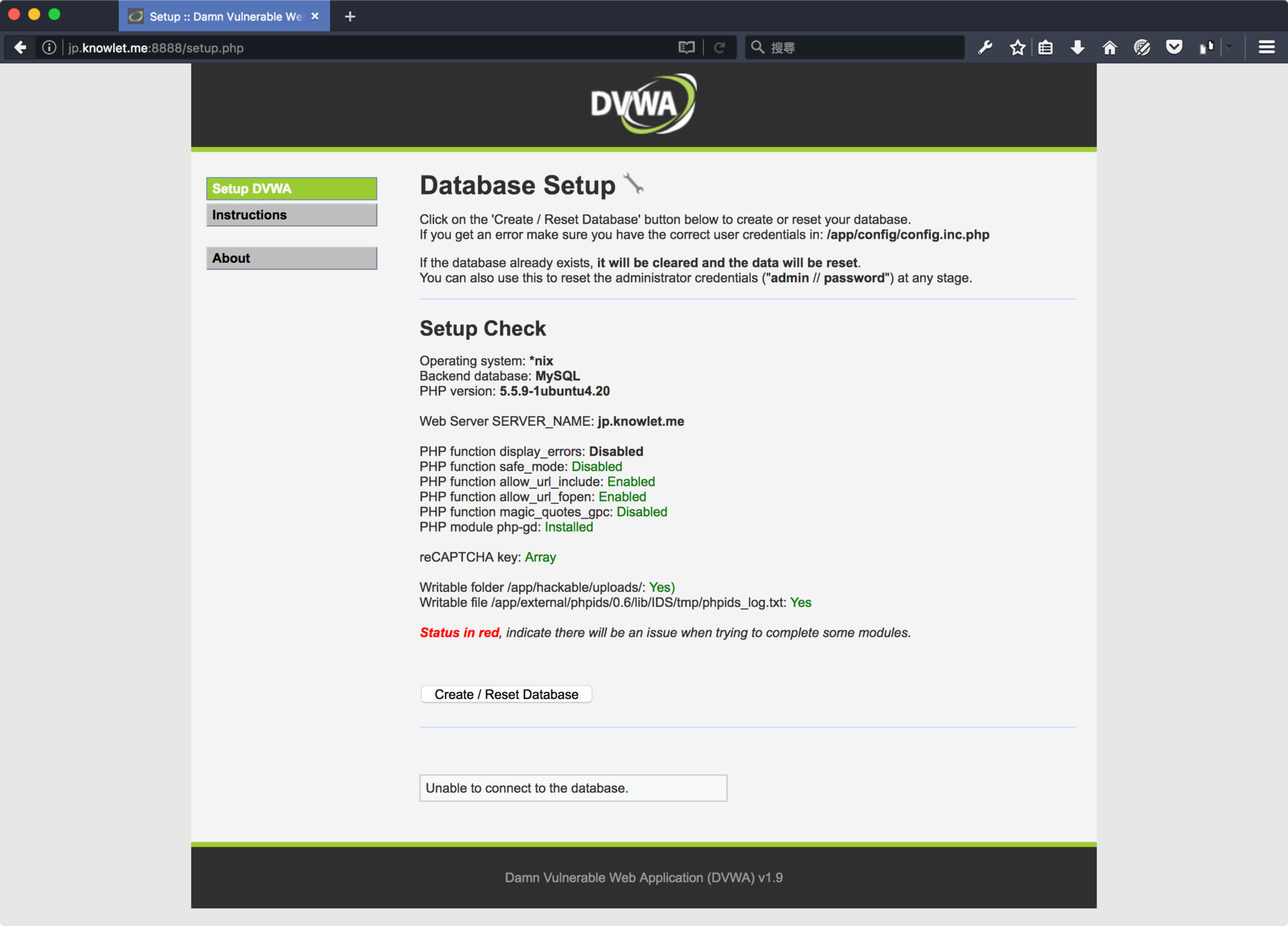
環境安裝
備用環境
DVWA 設定
Create / Reset Database
admin
password
左下角 DVWA Security
Security Level 改 Low