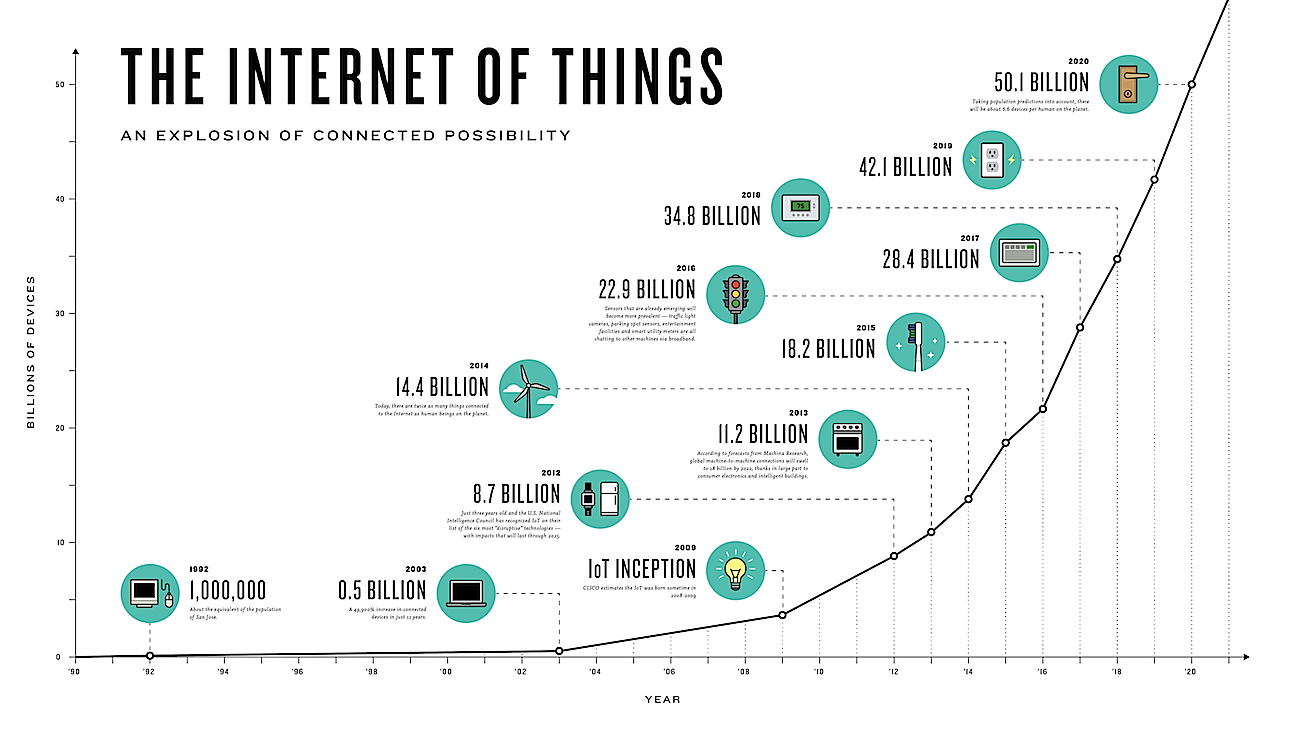
IoT
IoT
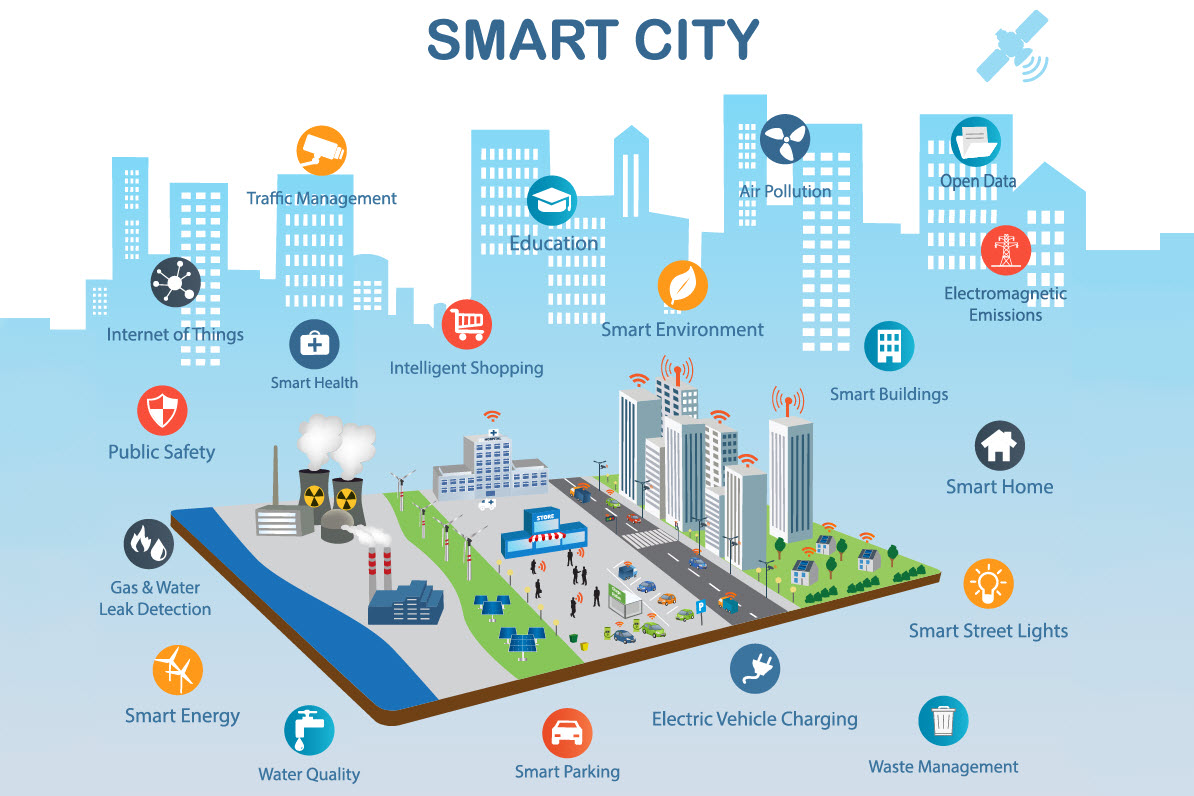

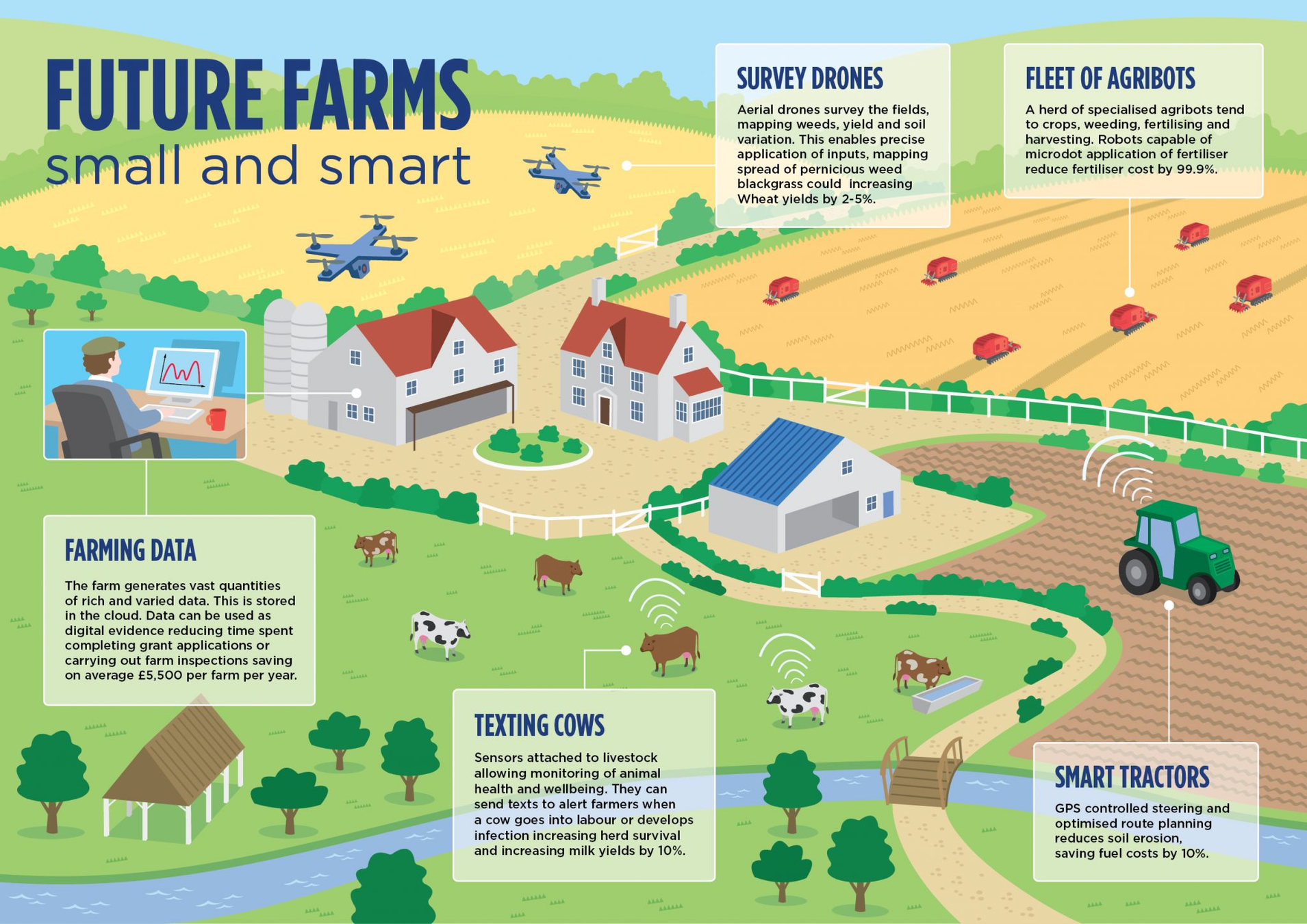

Industry 4.0
https://en.wikipedia.org/wiki/Industry_4.0
IoT
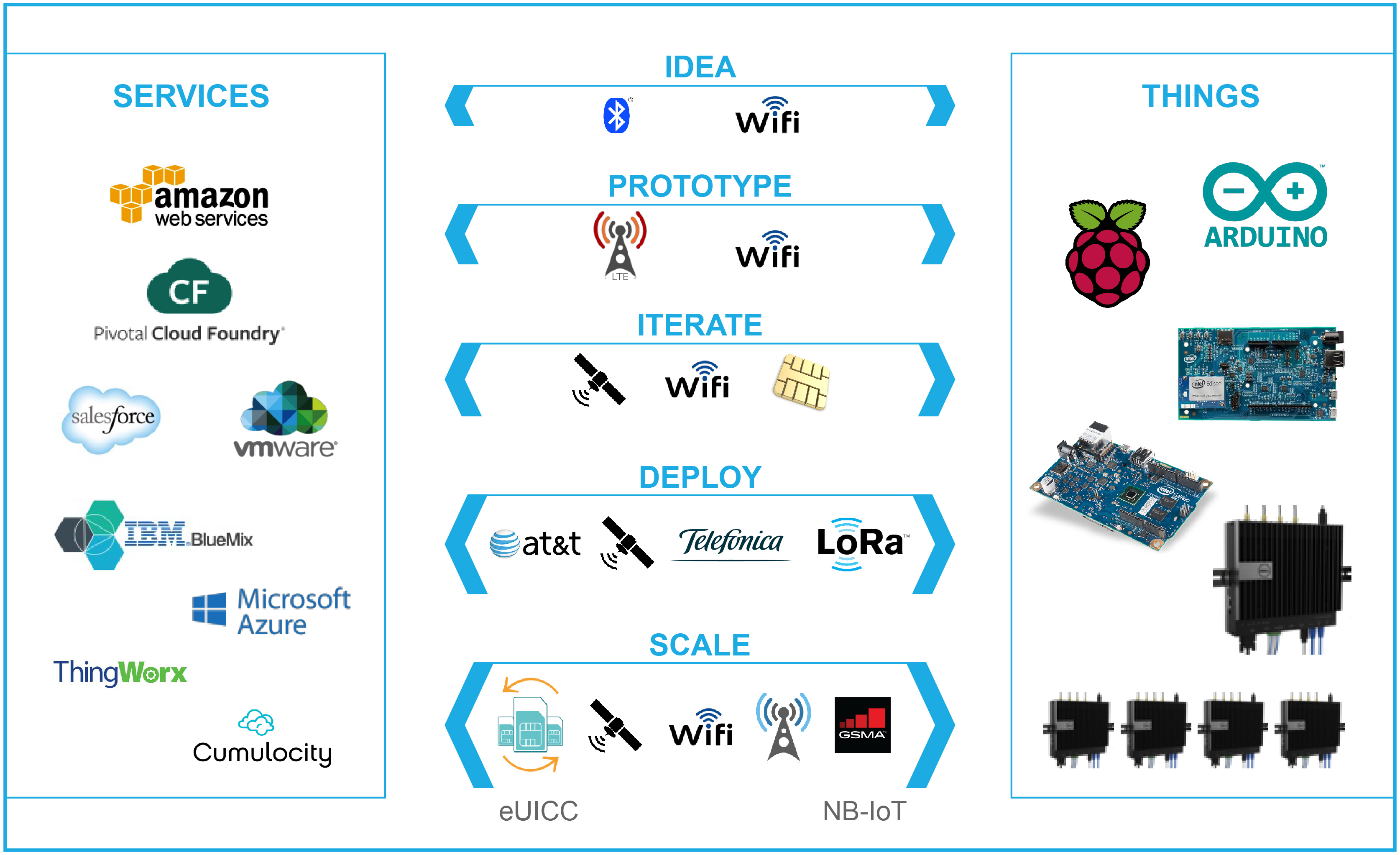
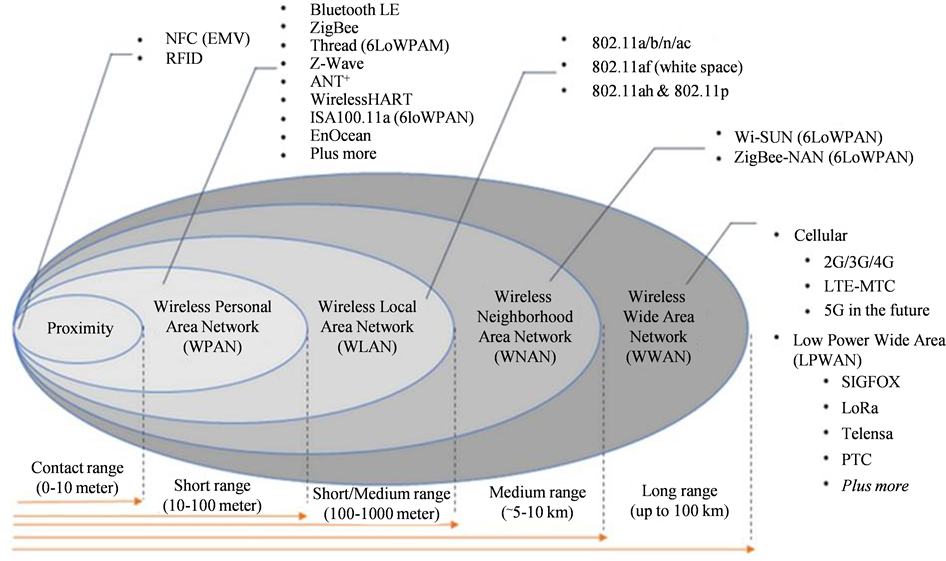
Where and Who
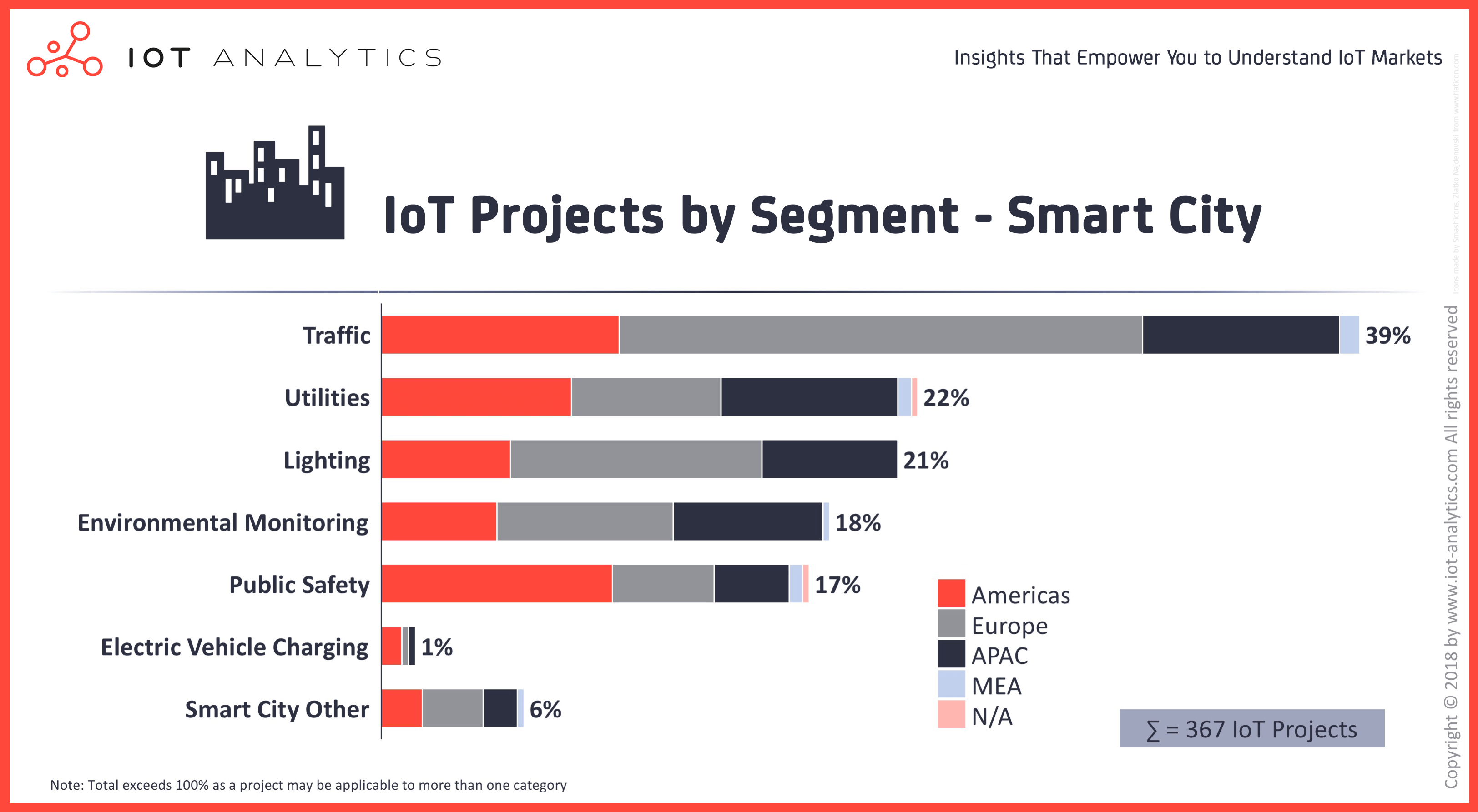
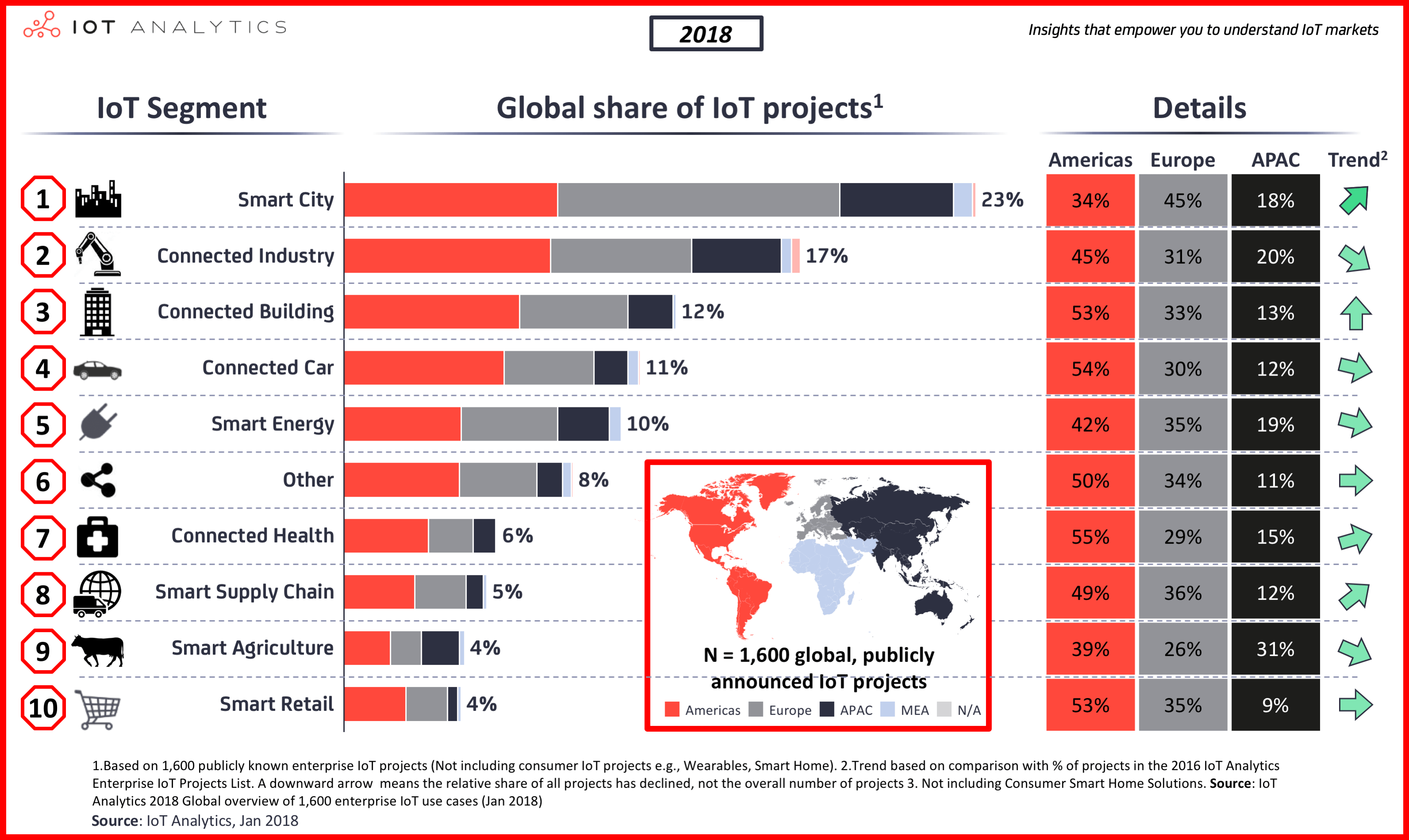
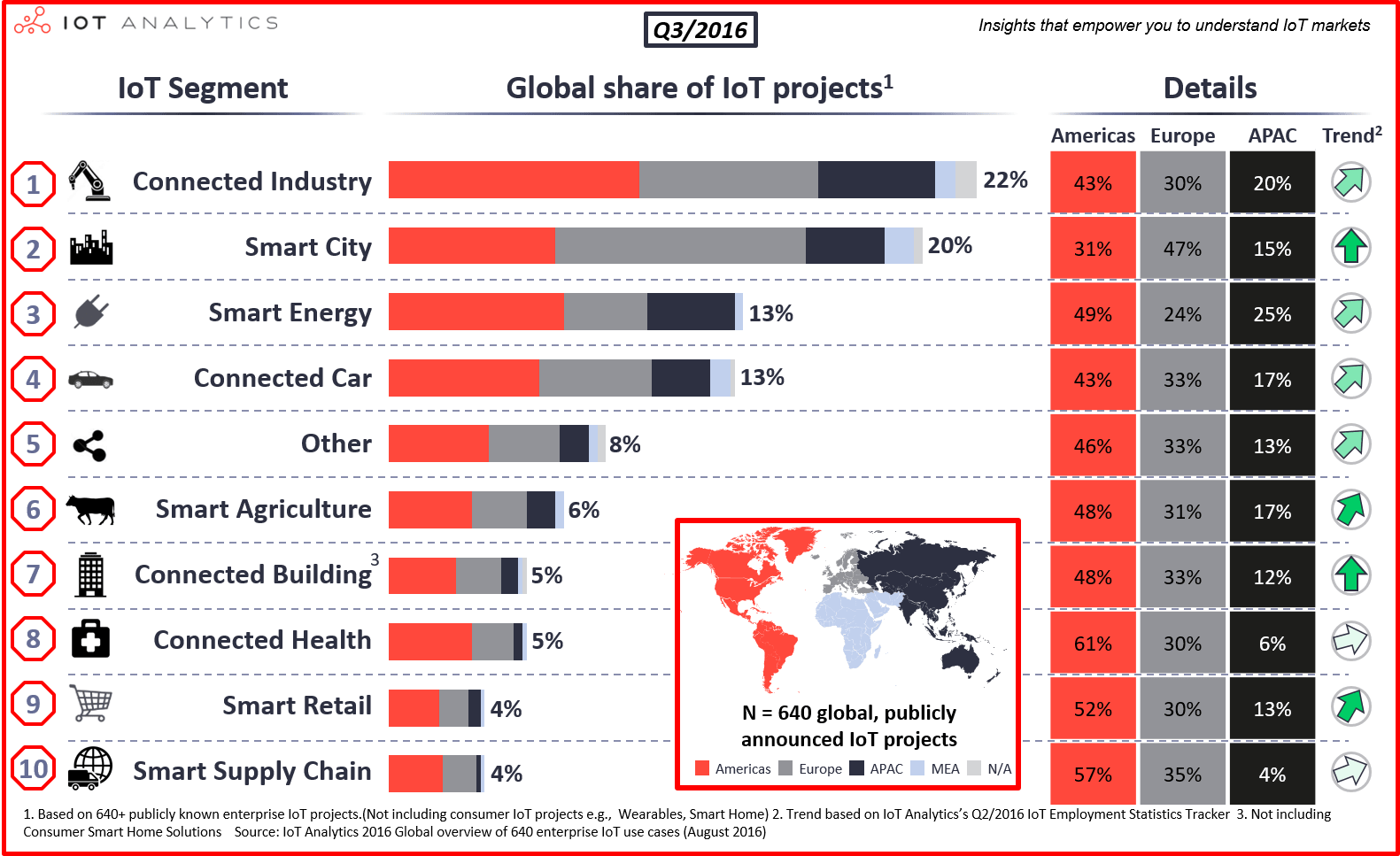
IoT Cloud
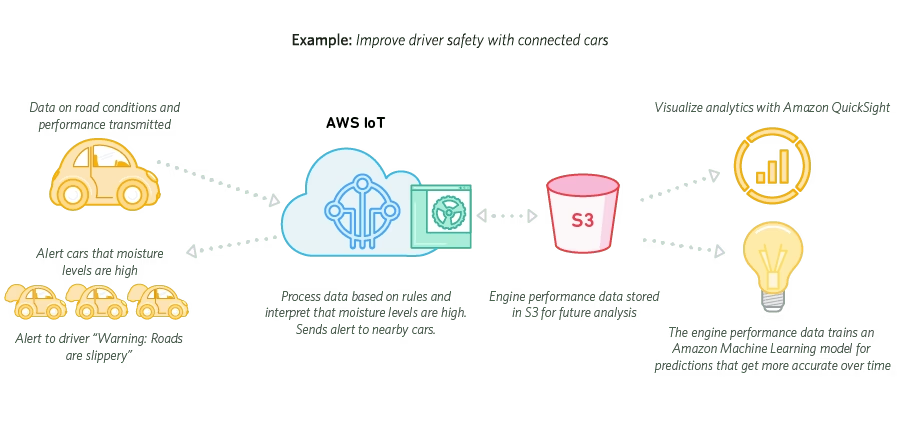
- Amazon S3
- Amazon DynamoDB
- AWS Lambda
- Amazon Kinesis
- Amazon SNS
- Amazon SQS
Amazon AWS
GOOGLE CLOUD IOT
https://cloud.google.com/solutions/iot/

Microsoft
MICROSOFT AZURE IOT HUB
https://azure.microsoft.com/en-us/services/iot-hub/
IBM
IBM WATSON IOT PLATFORM
https://www.ibm.com/us-en/marketplace/internet-of-things-cloud

ORACLE
ORACLE IOT CLOUD
https://cloud.oracle.com/en_US/iot

SALESFORCE
SALESFORCE IOT CLOUD
https://www.salesforce.com/editions-pricing/app-cloud/



Predix
Sap
CISCO IOT CLOUD CONNECT

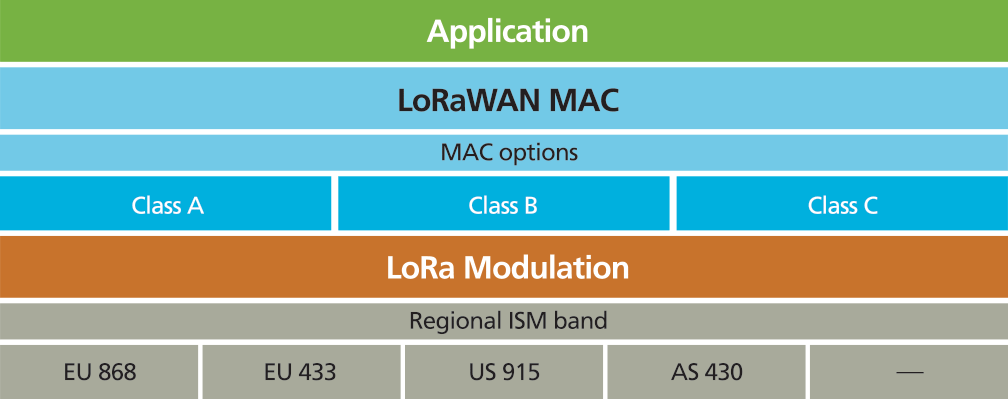
LoRa WAN
Long Range Wide Area Network


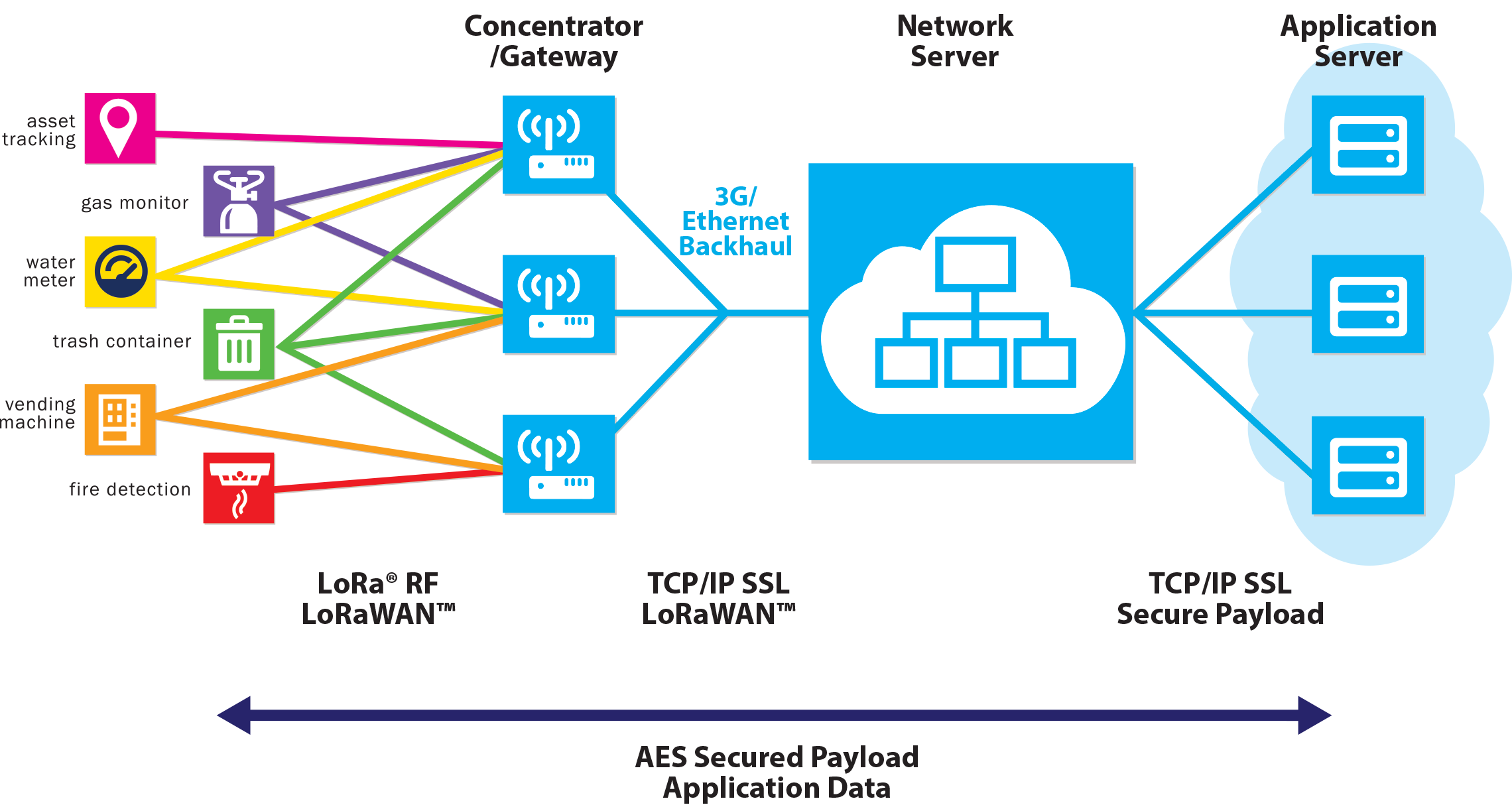
Why LoRa

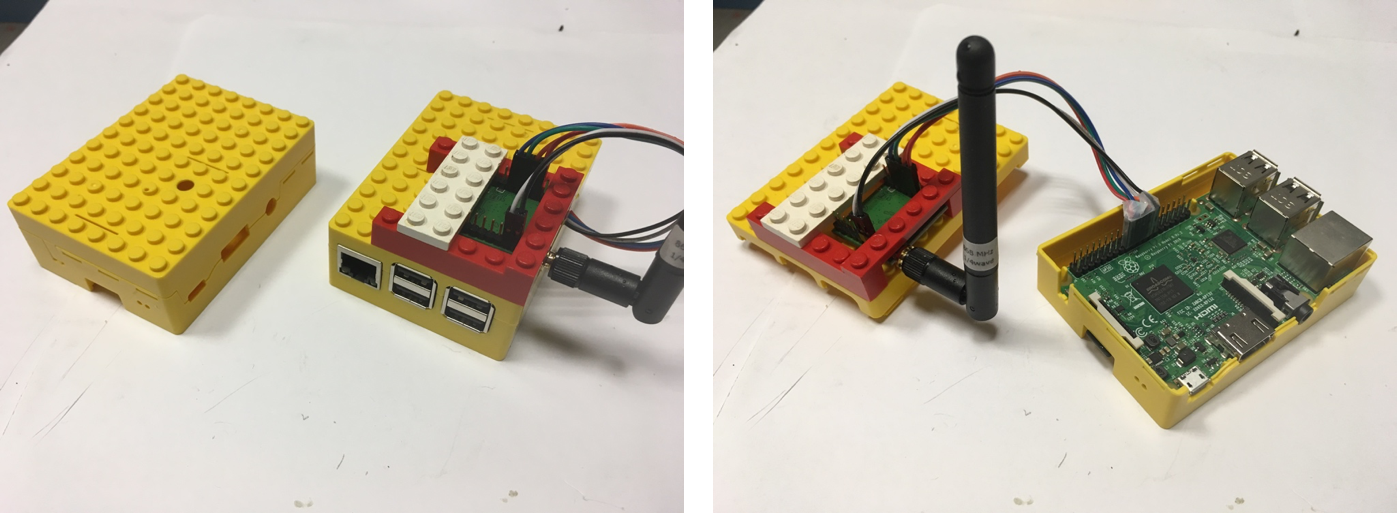
Raspberry Pi
https://www.instructables.com/id/LoRaWAN-Gateway/

http://cpham.perso.univ-pau.fr/LORA/RPIgateway.html

http://www.davidhunt.ie/lorawan-gateway-build-with-raspberry-pi/


http://www.davidhunt.ie/lorawan-gateway-build-with-raspberry-pi/

Arduino




| LoRa | |
| Module | SX1272 |
| Dual Frequency Band | 863-870 MHz (Europe) |
| 902-928 MHz (US) | |
| Transmission Power | 25 mW |
| Sensitivity | -134 dBm |
| Channels | 8 (868MHz) |
| 13 (900MHz) | |
| Range | LOS = 21km (13.4miles) |
| NLOS = +2km (1.2miles) |

FEATURESDESCRIPTION
| BAND | 868 ÷ 870 MHz |
| SENSITIVITY | -138 dBm |
| MODULATION | LoRa™ technology |
| RANGE | Urban environment 1Km / Open space 15Km |
| USER INTERFACE | 3 Buttons 5 Grove connectors (2 digital, 2 analog, 1 I2C) 1 Reset |
| OPEN SOURCE LIBRARY | Downlodable free of charge from www.udoit.eu |
LoRa Node
Development / Testing

http://lora-node.readthedocs.io/en/latest/
Features:
- On-board LoRaWAN™ Class A protocol stack
- ASCII command interface over UART
- Compact form factor 17.8 x 26.7 x 3 mm
- Castellated SMT pads for easy and reliable PCB mounting
- Device Firmware Upgrade (DFU) over UART
- 14 GPIO for control, status, and ADC
- Highly integrated module with MCU, crystal, EUI-64 Node Identity Serial EEPROM, Radio transceiver with analog front end, and matching circuitry
- Environmentally friendly, RoHS compliant
- European R&TTE Directive Assessed Radio Module

https://bitbucket.org/talk2/whisper-node-avr-lora
https://shop.clodpi.io/products/rak811-lora-sensor-node-board

LoRa Endpoint
Production
LoRa WAN
Standard
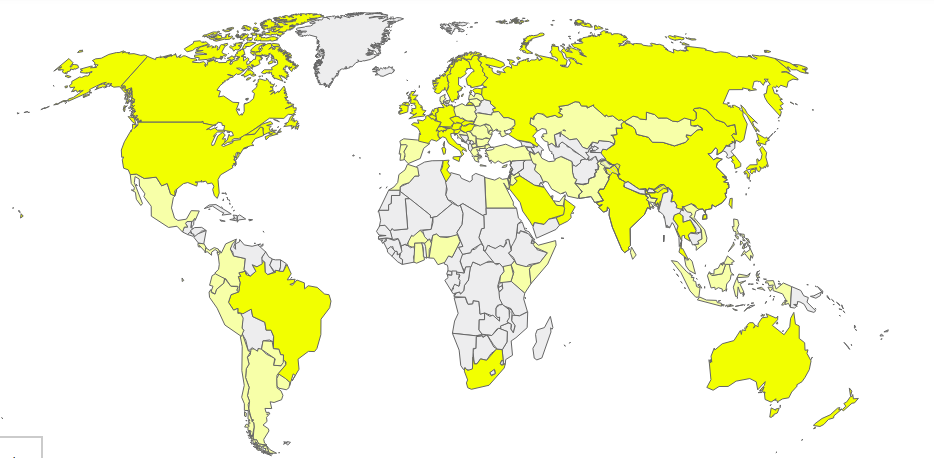
83 - Network Operators
57 - Alliance Member Operators
49 - Countries operating in
95 - Countries with LoRaWAN Deployments
Terminology
- End Device, Node, Mote - an object with an embedded low-power communication device.
- Gateway - antennas that receive broadcasts from End Devices and send data back to End Devices.
- Network Server - servers that route messages from End Devices to the right Application, and back.
- Application - a piece of software, running on a server.
- Uplink Message - a message from a Device to an Application.
- Downlink Message - a message from an Application to a Device.
End Devices
The LoRaWAN specification defines three device types. All LoRaWAN devices must implement Class A, whereas Class B and Class C are extensions to the specification of Class A devices.


EU 863-870 MHz and Duty Cycle
In Europe, LoRaWAN operates in the 863-870 MHz frequency band. European frequency regulations impose specific duty-cycles on devices for each sub-band. These apply to each device that transmits on a certain frequency, so both gateways and devices have to respect these duty-cycles. Most channels used by LoRaWAN have a duty-cycle as low as 1% or even 0.1%. As a result, the network should be smart in scheduling messages on gateways that are less busy or on channels that have a higher duty-cycle. Application developers are encouraged to keep their payloads small, do not transmit too often and avoid downlink messages if possible.
US 902-928 MHz
In the United States, LoRaWAN operates in the 902-928 MHz frequency band. Unlike the European band, the US band has dedicated uplink and downlink channels. The band is divided into 8 sub-bands that each have 8x125 kHz uplink channels, 1x500 kHz uplink channel and 1x500 kHz downlink channel. The Things Network uses the second sub-band (number 1 if you start counting at 0).
Australia 915-928 MHz
The specification of the Australian 915-928 MHz band is practically the same as the US 902-928 MHz, except that its uplink frequencies are on higher frequencies than in the US band. Its downlink channels are the same as in the US 902-928 MHz band. The Things Network uses the second sub-band (number 1 if you start counting at 0).
China 779-787 MHz and 470-510 MHz
The Chinese 779-787 MHz band behaves similar to the European bands. The 779-787 MHz band also has three common 125 kHz channels (779.5, 779.7 and 779.9 MHz). The Chinese 470-510 MHz band behaves similar to the US bands. There are 96 uplink channels and 48 downlink channels. In some regions, a subset of these channels is used by China Electric Power and can therefore not be used for LoRaWAN. The Things Network uses the eleventh sub-band (number 10 if you start counting at 0).
Addressing
Devices and applications have a 64 bit unique identifier (DevEUIand AppEUI). When a device joins the network, it receives a dynamic (non-unique) 32-bit address (DevAddr).
Security
LoRaWAN 1.0 knows three distinct 128-bit security keys. The application key AppKey is only known by the device and by the application. When a device joins the network (this is called a join or activation), an application session key AppSKey and a network session key NwkSKey are generated. The NwkSKey is shared with the network, while the AppSKey is kept private. These session keys will be used for the duration of the session.
The algorithm used for this is AES-128, similar to the algorithm used in the 802.15.4 standard. The NwkSKey is used to validate the integrity of each message by its Message Integrity Code (MIC). This MIC is similar to a checksum, except that it prevents intentional tampering with a message. For this, LoRaWAN uses AES-CMAC. The AppSKey is used for encryption of the application payload.
LoRa Alliance and Docs
- https://www.thethingsnetwork.org/docs/lorawan/
- https://www.lora-alliance.org/resource-hub
- https://www.lora-alliance.org/lorawan-certified-products
https://lora-alliance.org/lorawan-certified-products
