WordPress Security Issues and Solutions

Quiz
How many out of those approximately 63% websites use WordPress?
What % of websites don't use a CMS that we know of and monitor?
37.1%
45.5%
40%
37.1%
50%
40.5%
65.5%
40.5%
Which means 37.1% are static or use custom CMSs. And rest of them use WordPress, Joomla, Shopify, Wix, Squarespace, Godaddy CMS etc. That is approx. 63%
That is a CMS market share of 64.5%

A Quick run through on some WordPress Security issues or vulnerabilities and then we'll also take a look at some solutions.

A fEW WordPress wEBSITE Security Problems
-
Brute Force Attacks
-
SQL Injection
-
Weak Code
-
Malware
-
Denial of Service
-
Few more which I haven’t listed here.
Brute Force Attacks
This method uses the most simplest way to get access to the website, the login page.
An attacker uses a trial and error method of entering username and password combination until a successful combination is discovered.
SQL Injection
SQL which means Structured Query Language is a query language that was designed to manage data stored in relational databases.
SQL injection, or SQLi, is a type of attack on a web application that enables an attacker to insert malicious SQL statements into the web application, potentially gaining access to sensitive data in the database or destroying this data.
For example attackers can use SQL Injection to alter data, extract data, get user credentials, delete records, manipulate data etc.
Weak and Outdated Code
WordPress Core WordPress is an open source platform, which is regularly maintained and updated for security and performance optimization of the website. WordPress Plugins and Themes If the plugin or theme developer does not update the plugin or theme for a long time, it’s up to us to uninstall it or replace it. Same applies if we use a custom theme or plugins.
Malware
-
Pharma hacks -
Malicious redirects

Malware = Malicious Software
Let's take a look at some common WordPress Malware issues
Backdoors
A backdoor lets an attacker gain access to your environment through methods you would consider unusual — FTP, SFTP, WP-ADMIN, and others. Hackers can gain access to your website via the command line or even a GUI.
Malware
Pharma Hacks
Pharma hack is a very common phenomenon and it refers to a type of SEO spam where a legitimate website is used to sell illicit drugs. In this type of attack, hackers hijack websites, injects site with malware and uses site to sell illicit drugs.
Malware
Malicious Redirects
As the name suggests basically in this type of malware the website sends a user to a malicious website. To detect, one of the things you can do is check your .htaccess file.
Malware
Distributed Denial of Service
Essentially when an attacker wants to take down your website or service, they flood it with traffic from various sources to make it difficult to find out the source of the attack. They bottleneck your servers so that your normal visitors are denied service. The purpose of these requests is to slow down and eventually crash the targeted server.
Let's look at some WordPress Security Measures
Prevent SQL injection
So as we discussed earlier SQL injection attack basically takes place by interfering with the queries that an application makes to its database.
Some of the steps to avoid this include
-
input field validation -
removing unnecessary database functionality -
encrypting confidential data etc. In addition to that use a security plugin like Succuri or WordFence,
Deny Access to Sensitive files
The .htaccess file is a website configuration file that tells your server how to handle certain requests on your website. For example, how do you redirect users, password protect the admin area, protect specific directories, etc.
Options All -Indexes
<files .htaccess>
Order allow,deny
Deny from all
</files>
<files readme.html>
Order allow,deny
Deny from all
</files>
<files license.txt>
Order allow,deny
Deny from all
</files>
<files install.php>
Order allow,deny
Deny from all
</files>
<files wp-config.php>
Order allow,deny
Deny from all
</files>
<files error_log>
Order allow,deny
Deny from all
</files>
<files fantastico_fileslist.txt>
Order allow,deny
Deny from all
</files>
<files fantversion.php>
Order allow,deny
Deny from all
</files>Disable XML-RPC if you don't need it
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
</Files>To check if its enbaled on your website go to http://xmlrpc.eritreo.it/
add_filter('xmlrpc_enabled', '__return_false');
XML-RPC is a remote procedure call (RPC) protocol that enables communication between different software systems over the internet. It is commonly used by WordPress sites to allow external applications to access the site's data and perform actions on behalf of users.
However, XML-RPC can also be a potential security risk for WordPress sites, as it provides a potential entry point for hackers to launch attacks. Here are some tips for securing XML-RPC on your WordPress site:
You can disable it using the code below or by using a pluginabout XML-RPC
However, XML-RPC can also be a potential security risk for WordPress sites, as it provides a potential entry point for hackers to launch attacks. Here are some tips for securing XML-RPC on your WordPress site:
-
Disable XML-RPC: If you don't need XML-RPC functionality on your site, the easiest way to secure it is to disable it completely. You can do this by adding the following code to your site's functions.php file: add_filter('xmlrpc_enabled', '__return_false'); -
Limit access to XML-RPC: If you need to use XML-RPC, you can limit access to it by using a plugin like "Disable XML-RPC" or "Jetpack". These plugins allow you to block XML-RPC requests from specific IP addresses or user agents.
-
Use strong passwords: XML-RPC allows attackers to attempt to guess usernames and passwords using brute-force attacks. To protect against this, make sure all users have strong passwords and consider implementing two-factor authentication.
-
Use a firewall: A firewall can help protect against XML-RPC attacks by blocking suspicious traffic. You can use a plugin like "Wordfence" or "Sucuri" to add a firewall to your WordPress site.
-
Keep your WordPress site up-to-date: WordPress releases updates regularly to fix security vulnerabilities. Make sure you keep your site up-to-date with the latest version of WordPress, as well as any plugins and themes you're using.
By following these tips, you can help secure XML-RPC on your WordPress site and reduce the risk of attacks.
SCENARIOS WHERE YOU NEED XML-RPC Enabled
There are a few scenarios where a WordPress website might need XML-RPC enabled:
-
Remote publishing
-
Mobile apps
-
Jetpack
-
Integration with other systems
Overall, if you don't need to use external applications or services to manage your WordPress site, you can safely disable XML-RPC to improve your site's security. However, if you do need to use external tools or integrate with other systems, enabling XML-RPC is necessary for those use cases.
Proper Backup Solution
-
Schedule proper backups regularly
-
Store backups in the cloud, separate from your website
-
Have a easy to use backup restore plugin if possible
Remove your WordPress version number
It is WordPress' default feature to display the WordPress version of your site for tracking, however this condition can lead to security leaks on your site if you aren't running the most recent version. To remove the WordPress version in the header do the following
<meta name="generator" content="WordPress <?php bloginfo('version'); ?>" />
Or add the following to your functions.php
remove_action('wp_head', 'wp_generator');For the WordPress version number to be completely removed from your head and RSS feeds, you must add the following function to your functions.php file:
function wpbeginner_remove_version() {
return '';
}
add_filter('the_generator', 'wpbeginner_remove_version');
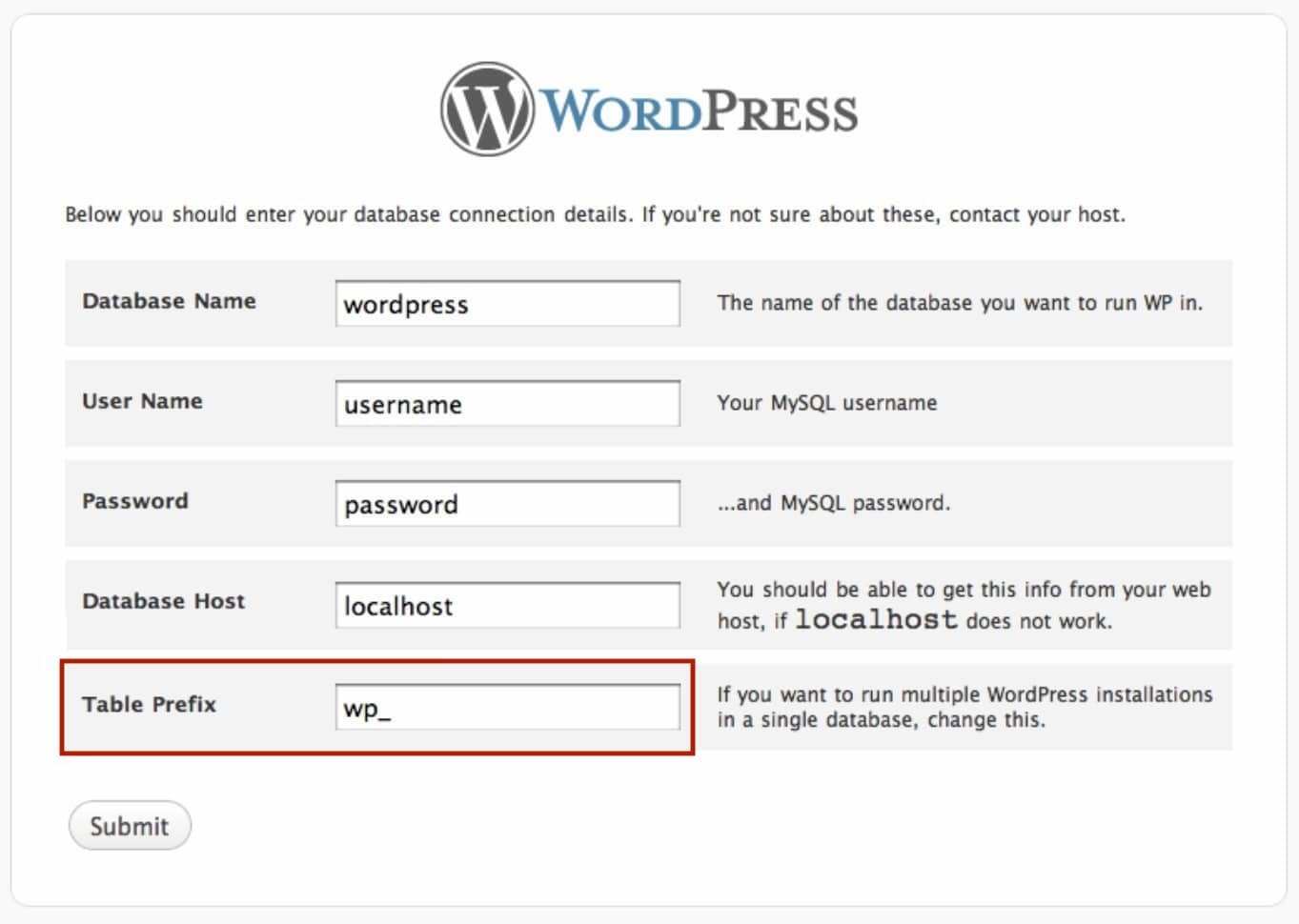
WordPress database prefix
One of the easiest ways to start with security in mind is to choose a wiser database prefix for your website when you’re setting it up. Because by default the database prefix is wp_. So instead of wp_ just type in something that’s unpredictable for example 29wp_.
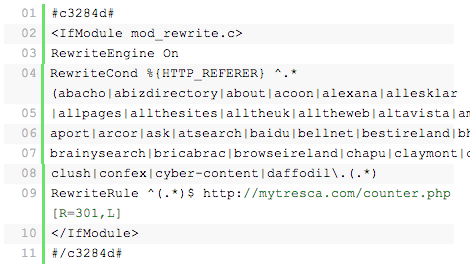
Secure WP-Includes
A second layer of protection can be added where scripts are generally not intended to be accessed by any user. One way to do that is to block those scripts using mod_rewrite in the .htaccess file. Note: to ensure the code below is not overwritten by WordPress, place it outside the # BEGIN WordPress and # END WordPress tags in the .htaccess file. WordPress can overwrite anything between these tags.
# Block the include-only files.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ - [F,L]
RewriteRule !^wp-includes/ - [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ - [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L]
RewriteRule ^wp-includes/theme-compat/ - [F,L]
</IfModule>
# BEGIN WordPressCross-Origin Resource Sharing (CORS)
Cross-Origin Resource Sharing (CORS) is a security feature implemented by web browsers to prevent malicious websites from accessing resources on a different domain.
<?php
header("Access-Control-Allow-Origin: *");
?>
<Directory /var/www/html>
# Enable CORS headers
Header always set Access-Control-Allow-Origin "*"
Header always set Access-Control-Allow-Methods "GET, POST, OPTIONS, DELETE, PUT"
Header always set Access-Control-Allow-Headers "Content-Type, X-Requested-With, Authorization"
</Directory><?php
header("Access-Control-Allow-Origin: https://example.com");
?>For specific domains
WordPress Admin Page
Let’s talk about the admin page, which most hackers try to access first. Here are some things you can do in order to make your admin login page more secure.
-
Limit Login Attempts
-
Change the login URL
-
Two factor login Authentication
-
Automatically logout idle users
-
Create a strong password and create a guide for team members
-
Remove default Username Admin/User
-
Whitelist IPs
-
WordFence
Keep the code up to date
-
WordPress Core -
Themes -
Plugins -
PHP of the server
Because WordPress is so popular and even used by huge organizations for mega websites, the hackers keep working to develop ways to circumvent the security updates in WordPress and get access to even the most uptodate WordPress websites. That’s why it’s really important to keep the WordPress core, themes and plugins up to date. If you’re using custom themes or plugins just make sure that the code is updated regularly.
Better Hosting Solutions
Website hosting easily plays the most important role in the security of the website. There are different types of hosting, shared hosting, Dedicated Server hosting, VPS Virtual Private hosting, Cloud hosting etc. A few things good web hosting companies do, prevent large scale DDOS attacks, keep their software up to date and deploy disaster recovery and accidents plans, have strong firewall and continuous supervision of the network for suspicious activity.
A few other things
Plugins for security and monitoring WP
-
Disallow file editing in the WordPress Dashboard
-
Block all image hot-linking
-
Install Google Recaptcha for form submissions
-
Install a spam protection plugin
Besides other reasons WordPress websites are vulnerable for the following obvious but not so obvious reasons.
-
Many WordPress website owners are not developers and prefer to maintain the website on their own. -
Most of the time people get so busy in the front-end of the website and creating content and just putting stuff out that they forget to do an extensive maintenance of the website.
Do a security audit regularly
Thank you! WordPress Security Issues and Solutions Author: Neha Patel Email: kpatelneha23@gmail.com Document: Google Doc