How I hacked into an encrypted service

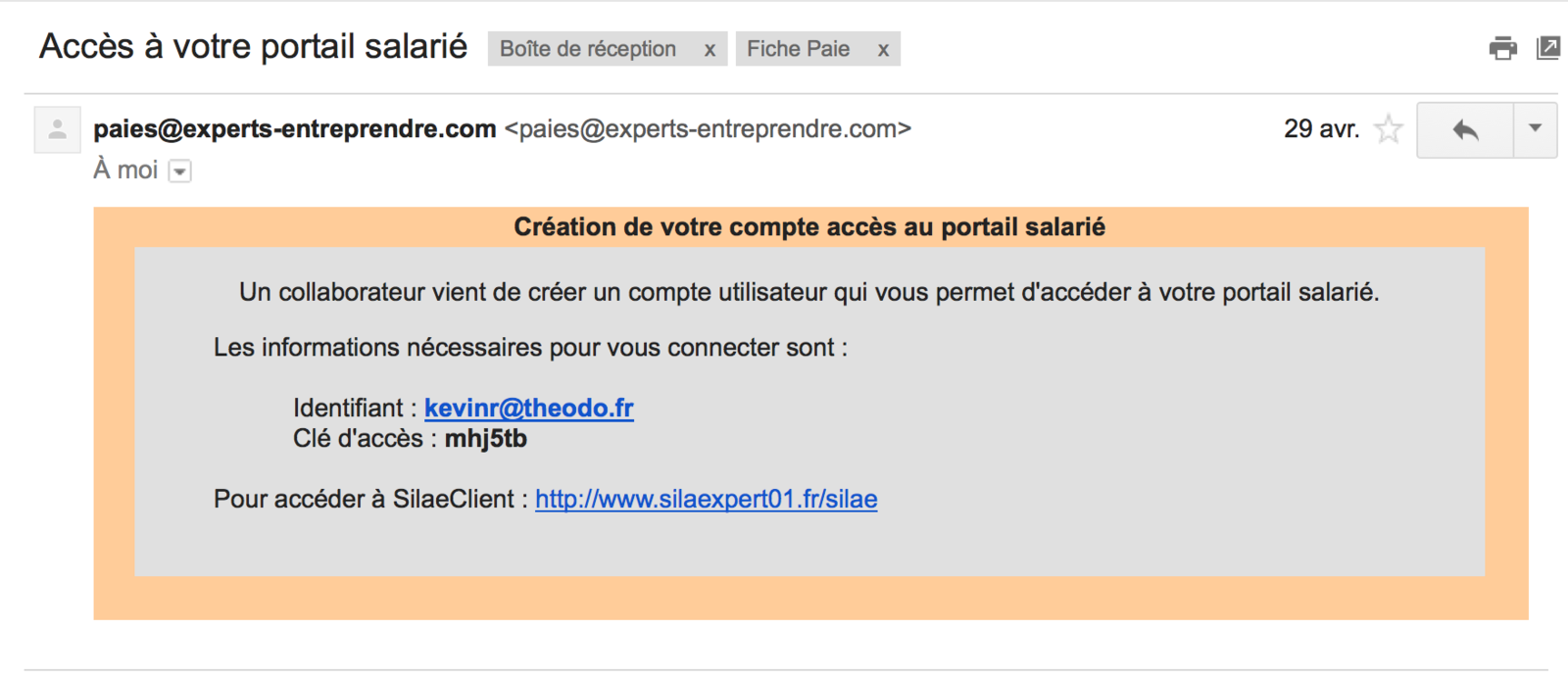
It all started with an email...
WHAAAT?

Let me double check...

OK then.
But what was that?
Let's make this thing work...
OK, it is running.
Now what?
First...
Small recap

OK, it is encrypted.
How do I decrypt it?
RSA?
- Private/Public key mechanism
- Cannot encrypt large amount of data
- 2048 bits key = max 245 bytes encoded
What about the second message?
- Base64 encoded
- Not RSA encrypted (too large)
Wait...
Am I stuck?
A clue?

Let's dig into the client!
OK, I have the code.
How does it work?
The message is self descriptive
01
Size of the key (00 01 00 00 = 256)
256 bytes = the key
Size of the IV (20 00 00 00 = 32)
32 bytes = the IV
The encrypted login request
The encryption protocol
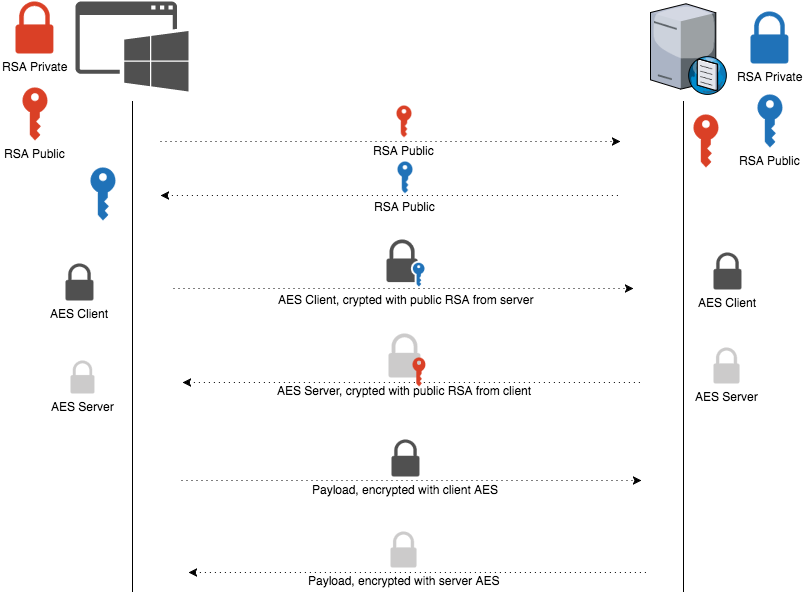
Go MITM!

Ok, I know how to make requests.

Where are we?
Intercept data
Understand the security protocol
Decrypt the exchange
Forge requests



Use the source, Luke
We had a raw request
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">http://www.silae.fr/IIWCF/AppelComResponse</a:Action>
<a:RelatesTo>urn:uuid:f9bcb8a5-24cb-4963-9621-43632d01fa49</a:RelatesTo>
</s:Header>
<s:Body>
<AppelComResponse xmlns="http://www.silae.fr/">
<AppelComResult xmlns:b="http://schemas.microsoft.com/2003/10/Serialization/Arrays" xmlns:i="http://www.w3.org/2001/XMLSchema-instance">
<b:KeyValueOfanyTypeanyType>
<b:Key i:type="c:int" xmlns:c="http://www.w3.org/2001/XMLSchema">1</b:Key>
<b:Value i:type="c:base64Binary" xmlns:c="http://www.w3.org/2001/XMLSchema">
AKzR15lw+4zEApy/4BoiSOBSJ1mIUJBNSpgYu99SDPM80mfxa9pldkka91NqQfz8
/1jMQfeQVes3Edbb82c5CpHD7zEDhe8ZtUQjOFgbHdG599Hr6inSOOaaYOzEeb9q
Q3isSXkPBY9Pxo1IQOMsEY4spiRhSsOmfk2eFdlSIo/ENjWubVNSfG63oLGCL9nY
lsUvpA/xexKLORUGgPSanFlQ5z5uTdklbgWQUp4vJyZqQWv8NXVbREC7Lco8a2Bj
9D6AnEI3Ww4jM2LGR4Yz7Xm7YCCuW+7G7Q7bBNZ3TMt3A01xb/+8dUPrkie5a76V
9se30iwwD4X/yN7ngVkZgIpUpijrSy7xxMAB0/WY+IaOM+bv5d66SST7MJ3ozjVe
W7WFMT0OP7SEDq5EGbhDo5Kuj+b7T3iuSVCwxCwnxC0SFZg4/k5rPU9rrFgoined
0a2ShX8gZEBDQlefV7xIwkfldvEIVYTRgPqk4ff37caWY/k/PEzQJOMp/FpXYE1N
9RxcYSeE371VVwyIGNljjCDVt7adHIdHvV7e5IFYmyF0/vH9zkGC3VR/jF3g6iOC
K/gkzNBlWtrrc76M1W3HPIv0MoytH0uJDENYZimHfXxn8mjSUEEjc3jOMutnwpbo
E3yCUdXWhy60k995DHI3QYEJoBZ0BZphRqG3eJnv+1KPoaprcTLp2j3IyvoO5qPl
loDTHaeaIrZiQ4QVLHzq6kE5U0GOLnjuaS01G+GNwpaj0Le3LsFFIttzRcbAJwee
rersFhfr82+XQymhYef8/UhC/CAiulYP/1j2fPPKTNcxuKvAYPvoMG3yT0IQStuO
mBLjXth1RmaWMe9xanSvan+GL85y08CA/MIUHWLNzOF2LjSE5Im130YrwtkWHjGL
eM668B1iuk3/w7h+EUSuDwf+dc1GduyDhC2Kijx2DNBxg4UHKkGjGtKUU+DVKsAr
nMoNztidcEyxNBLrewX0XQhBa0egeSzCiZIEsItoInB+Dn5fBgc/W1hFf2M5iPir1g==</b:Value>
</b:KeyValueOfanyTypeanyType>
<b:KeyValueOfanyTypeanyType>
<b:Key i:type="c:int" xmlns:c="http://www.w3.org/2001/XMLSchema">0</b:Key>
<b:Value i:type="c:int" xmlns:c="http://www.w3.org/2001/XMLSchema">2</b:Value>
</b:KeyValueOfanyTypeanyType>
</AppelComResult>
</AppelComResponse>
</s:Body>
</s:Envelope>We decrypted it
00000000 0b 00 08 24 4d 45 54 48 4f 44 45 0c 14 41 63 71 |...$METHODE..Acq|
00000010 75 69 73 69 74 69 6f 6e 42 75 6c 6c 65 74 69 6e |uisitionBulletin|
00000020 73 02 50 34 05 00 00 00 00 04 24 41 50 50 0c 0f |s.P4......$APP..|
00000030 53 69 6c 61 65 43 6c 69 65 6e 74 2e 65 78 65 02 |SilaeClient.exe.|
00000040 50 32 05 d1 95 01 00 04 24 44 4f 4d 0c 00 02 50 |P2......$DOM...P|
00000050 35 63 01 00 02 42 41 62 6b 00 00 00 04 00 1f 4f |5c...BAbk......O|
00000060 70 74 69 6f 6e 5f 4c 69 73 74 65 52 65 63 75 72 |ption_ListeRecur|
00000070 73 69 76 65 53 75 70 65 72 76 69 73 65 73 02 01 |siveSupervises..|
00000080 1e 4f 6e 67 6c 65 74 4e 61 74 75 72 65 55 74 69 |.OngletNatureUti|
00000090 6c 69 73 61 74 65 75 72 53 61 6c 61 72 69 65 02 |lisateurSalarie.|
000000a0 01 08 49 44 5f 44 52 4f 49 54 05 d1 95 01 00 12 |..ID_DROIT......|
000000b0 49 44 5f 53 55 50 45 52 56 49 53 45 55 52 5f 53 |ID_SUPERVISEUR_S|
000000c0 56 4e 05 5e 00 00 00 02 54 35 0c 29 53 49 4c 41 |VN.^....T5.)SILA|
000000d0 45 2e 43 4d 5f 53 55 50 45 52 56 49 53 49 4f 4e |E.CM_SUPERVISION|
000000e0 2b 43 53 75 70 65 72 76 69 73 69 6f 6e 43 6f 6e |+CSupervisionCon|
000000f0 74 65 78 74 65 02 50 33 05 88 40 00 00 07 24 43 |texte.P3..@...$C|
00000100 4c 41 53 53 45 0c 0f 43 4d 5f 50 41 49 50 4f 52 |LASSE..CM_PAIPOR|
00000110 54 41 49 4c 43 50 04 24 55 53 52 0c 05 33 30 36 |TAILCP.$USR..306|
00000120 37 37 02 50 31 05 b4 04 00 00 16 16 16 16 16 16 |77.P1...........|
00000130 16 16 16 16 16 16 16 16 16 16 16 16 16 16 16 16 |................|
00000140And deserialized it
{
'$METHODE': { type: 12, value: 'AcquisitionBulletins' },
P4: { type: 5, value: 0 },
'$APP': { type: 12, value: 'SilaeClient.exe' },
P2: { type: 5, value: idDroit },
'$DOM': { type: 12, value: '' },
P5:
{ type: 99,
value:
{ BA:
{ type: 0x62,
value: cSupervisionContexte } }},
T5: { type: 12, value: 'SILAE.CM_SUPERVISION+CSupervisionContexte' },
P3: { type: 5, value: idPaiSalarie },
'$CLASSE': { type: 12, value: 'CM_PAIPORTAILCP' },
'$USR': { type: 12, value: $usr },
P1: { type: 5, value: idClient }
}