CTF - Guide To Practice
Agenda
- Find a Job
- Rules & Challenges
- Recon
- Web Vulnerabilities
- Pwnable
- Cryptography
- Forensic
- Show case: SQL Injection
src: https://trailofbits.github.io/ctf/intro/careers.html
Career Opportunities
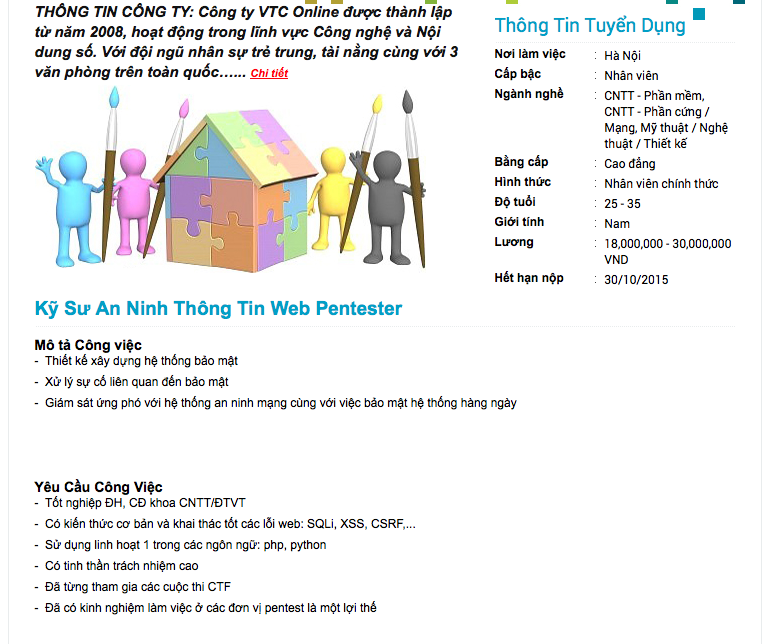
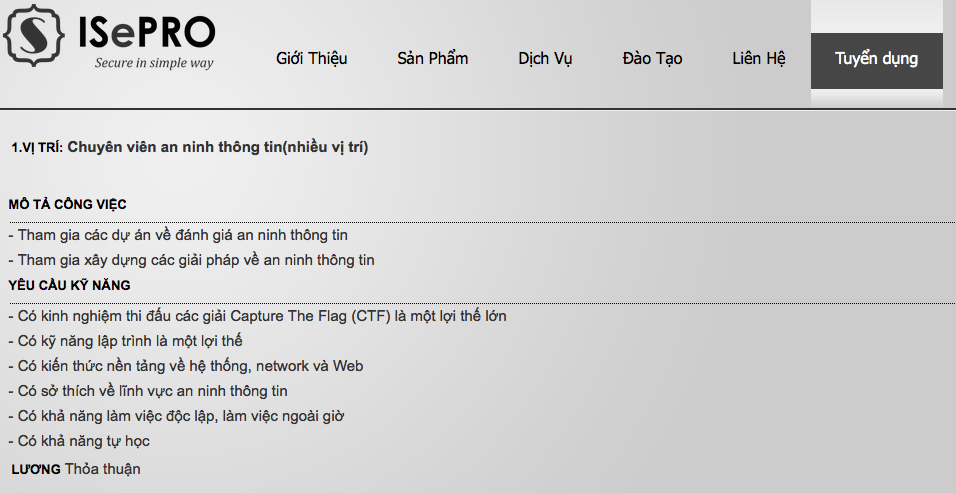
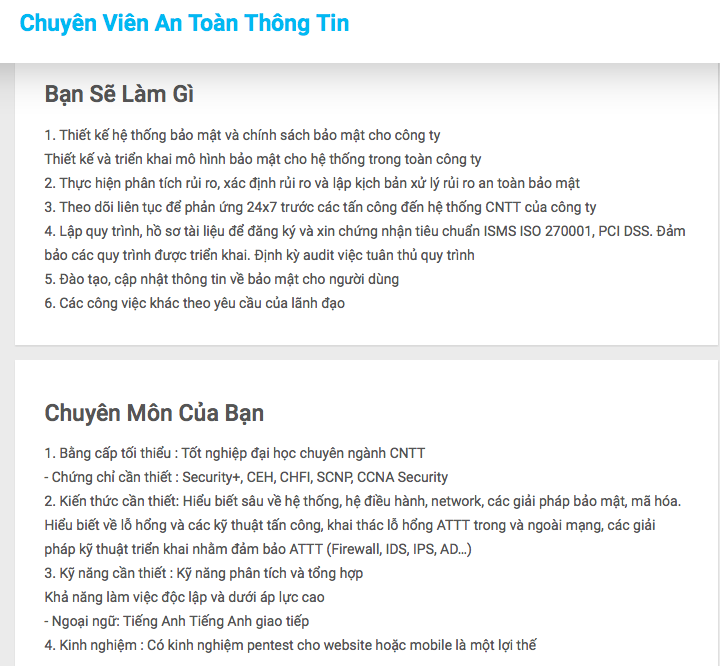
Role & Available Positions
- Application Security (code audits/app assessments)
- Attacker (offensive)
- Compliance
- Forensics
- Incident Handler
- Manager
- Network Security Engineer
- Penetration Tester
- Policy
- Researcher
- Reverse Engineer
- Security Architect
src: https://trailofbits.github.io/ctf/intro/careers.html
Meet People
- Get a club (school club) - Share your workloads.
- Learn from friends. Learn by doing.
- Attend to local meeting organized by Big Players for career opportunities. (VNISA, BKAV)
- Follow international conferences for vulnerabilities trending (BlackHat USA DefCon)
If you think 4 steps are too much works. Go read step 1.
Capture The Flag
If you want to acquire and maintain technical skills and you want to do it fast, then you should play in a CTF or jump into a wargame
In general, it is far more productive to spend time playing in a CTF, then using your final standing as proof that you're capable.
- Trail of Bits Guide
Again, Why CTF ?
- "World Cup" For Hackers.
- Best defend = think offensively.
- Divided into 2 main categories:
- Jeopardy . Question & Answer format
- Attack - Defense. Patching & Attack Format
- Famous CTF games are beneficial.


Jeopardy
- Challenge-based format.
- Online-competitions.
- Recon
- Web App
- Cryptography
- Pwnable
- Reverse Engineering
- Forensic (Network/File)
- Duration: 4 Hours - 2 Days
- Solve the challenges to get the flag.
- Flag format depends on event type.
- Ex: D4y_L4_Fl@g_va_no_0_co_space
- Ex: CTF{Day_Cung_l@_1_Flag}
- Ex: Flag_202cb96
Learn from write-ups is encouraged.
Reconnaissance
- Related Fields: Business Intelligence, Network Intelligence, Search Engine Hacking, FOCA, DNS Reconnaissance, Network Scanning.
- Conan-based challenges. Finding information by observations.
- Tools Recommendation
- Facebook/ Linked in/ Twitter Search
- Bing/ Google search
- Recon-ng (framework)
- CTF games that have Recon
- Ex: http://ctf-for-beginners.blogspot.com/2015/09/write-up-csaw-ctf-2015-recon-alexander.html
- Practice: http://hackeracademy.com/module/business-intelligence
Web Vulnerabilities
- Auditing Web App. Familiar with OWASP.
- Top 10 - 2013. (Still Valid till now)
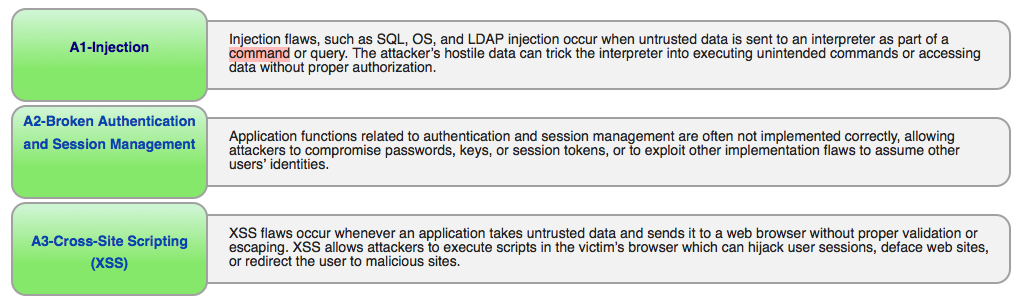
- Ex. http://resources.infosecinstitute.com/n00bz-ctf-challenge-2-practical-website-hacking/
Pwnable
- Read the binary source code & Reverse/Exploit the Operation.
- Very Tricky. Including Buffer Overflow, String format (Remmember CWE 170? ).
-
Tools & Knowledge Recommendations.
- Assembly Language
- Control the EIP (Extended Instruction Pointer)
- Debuggers: GDB, PEDA
- Disassemblers: IDA-PRO, objdump
- Radare2 (Reversing Framework)
- Ex: https://ctf-team.vulnhub.com/picoctf-2014-no-overflow/
- Ex: https://ctf-team.vulnhub.com/backdoor-ctf-2015-forgot/
Cryptography
- Given a string, decode it
- Encrypted methods:
- Transposition:
- Rail Fence
- Substitution
-
Mono-Alphabetic Cipher: Same substitutions will be used.
- Caesar. Ex. A will be encrypted with K
-
Poly-Alphabetic Cipher: Different substitutions will be used.
- Vigenere. Ex. A can be encrypted with K, S.
-
Mono-Alphabetic Cipher: Same substitutions will be used.
- Other:
- Base64, ROT13, Dancing Man (Sherlock Home)
- Visual Cryptography, Steganography
- Transposition:
T I I A E R T
H S S S C E
TIIAERTHSSSCE
encrypted text
Forensic
- Given a file, a packet or an image, find the flag
- Information are hidden within the given file,
- Tools & Knowledge Recommendation
- Common File Structure (PNG, JPEG, BMP, GIF, EXE, RAR)
- HexEditor
- File Inspection:
- binwalk/ strings/ file/ grep
- pngcheck for meta-data & filter type check
- Steganography Inspection:
- StegExpose for LSB check/ Stegsolve.
- foremost for embedded files.
- Network Traffic Sniffing:
- wireshark/tshark/tcpdump
Show time !
Topology
- Automated Scan with SQLMap
- Manual Error-based SQL Injection
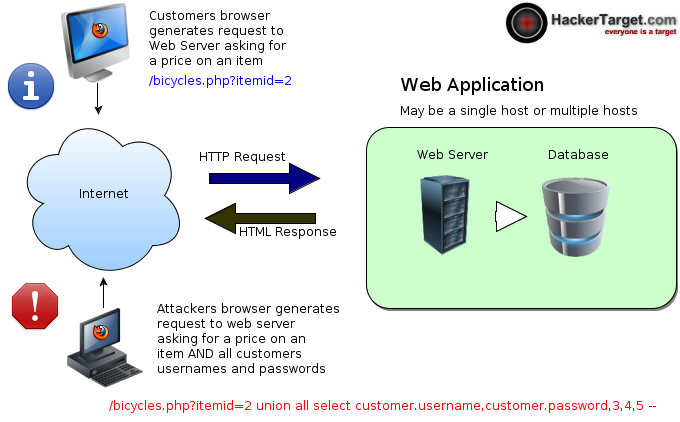
source: medium.com