Adopting
Network Service Mesh
with Meshery
Lee Calcote
Girish Ranganathan
Prem Sankar
@lcalcote
leecalcote
@ingenious_g
girishranganathan
@premsankar
gpremsankar







Lee
Calcote

Girish Ranganathan
Prem Sankar


Harshini Mohandass



layer5.io/books

Available
at

It's meshy out there
layer5.io/landscape
Service Mesh Abstractions
Service Mesh Interface (SMI)
Multi-Vendor Service Mesh Interoperation
Hamlet



Service Mesh Abstractions

+

Service Mesh Interface (SMI)
+

Multi-Vendor Service Mesh Interoperation
Hamlet

Adopter’s Dilemma
Which service mesh to use?
What's the catch? Nothing's for free.
Playground
WHICH SERVICE MESH SHOULD I USE AND HOW DO I GET STARTED?
Learn about the functionality of different service meshes and visually manipulate mesh configuration.
Performance Benchmark
WHAT OVERHEAD DOES BEING ON THE SERVICE MESH INCUR?
Benchmark the performance of your application across different service meshes and compare their overhead.
layer5.io/meshery
Service Mesh Architectures
Service Mesh Planes
Data Plane
- Touches every packet/request in the system.
- Responsible for service discovery, health checking, routing, load balancing, authentication, authorization, and observability.
Ingress Gateway
Egress Gateway
A collection of pipes and proxies
Service Mesh Planes
No control plane? Not a service mesh.
Control Plane
- Provides policy, configuration, and platform integration.
- Takes a set of isolated stateless sidecar proxies and turns them into a service mesh.
- Does not touch any packets/requests in the data path.
Data Plane
- Touches every packet/request in the system.
- Responsible for service discovery, health checking, routing, load balancing, authentication, authorization, and observability.
Ingress Gateway
Egress Gateway
Service Mesh Planes
Control Plane
Data Plane
- Touches every packet/request in the system.
- Responsible for service discovery, health checking, routing, load balancing, authentication, authorization, and observability.
- Provides policy, configuration, and platform integration.
- Takes a set of isolated stateless sidecar proxies and turns them into a service mesh.
- Does not touch any packets/requests in the data path.
You need a management plane.
Ingress Gateway
Management
Plane
- Provides monitoring, backend system integration, expanded policy and application configuration.
Egress Gateway
Pilot
Citadel
Mixer
Control Plane
Data Plane
istio-system namespace
policy check
Foo Pod
Proxy Sidecar
Service Foo
tls certs
discovery & config
Foo Container
Bar Pod
Proxy Sidecar
Service Bar
Bar Container
Out-of-band telemetry propagation
telemetry
reports
Control flow
application traffic
Application traffic
application namespace
telemetry reports
Istio Architecture

Galley
Ingress Gateway
Egress Gateway
Control Plane
Data Plane
octa-system namespace
policy check
Foo Pod
Proxy
Sidecar
Service Foo
discovery & config
Foo Container
Bar Pod
Service Bar
Bar Container
Out-of-band telemetry propagation
telemetry
reports
Control flow
application traffic
Application traffic
application namespace
telemetry reports
Octarine Architecture

Policy
Engine
Security Engine
Visibility
Engine

+
Proxy
Sidecar

+
Control Plane
Data Plane
linkerd-system namespace
Foo Pod
Proxy Sidecar
Service Foo
Foo Container
Bar Pod
Proxy Sidecar
Service Bar
Bar Container
Out-of-band telemetry propagation
telemetry
scarping
Control flow during request processing
application traffic
Application traffic
application namespace
telemetry scraping
Architecture
destination
Prometheus
Grafana
tap
web
CLI
proxy-api
public-api
Linkerd
proxy-injector
Configuration
Security
Telemetry
Control Plane
Data
Plane
service mesh ns
Foo Pod
Proxy Sidecar
Service Foo
Foo Container
Bar Pod
Proxy Sidecar
Service Bar
Bar Container
application traffic
http / gRPC
application namespace
meshery.io
Ingress Gateway
Egress Gateway

Management
Plane
meshery
adapter
gRPC
kube-api
kube-system




Out-of-band telemetry propagation
Control flow
Application traffic

A Mesh for Meshes
L3 (IP)
L2 (Ethernet, MPLS, etc.)
L7 (HTTP/2 etc.)
L4 (Streams - TCP / Datagrams - UDP)
service meshes
Network Service Mesh
Payloads handled by Kubernetes Services/ Istio/Service Mesh
Payloads handled by NSM
NSM - within a node
Dataplane (kernel/vswitch)
cross-connect
Application
pod
NSM
Init container
NSM Manager
VPN
Gateway
Pod
(NSE)
1. Request (connection)
7. Reply
2. Request (connection)
3. Reply
4. Create & inject interface
5. Create & inject interface
6. cross connect
Node
NSM - multi node
Dataplane (kernel/vswitch)
tunnel
Sarah's
pod
NSM
Init container
NSM Manager
VPN
Gateway
Pod
(NSE)
1. Request (connection)
11. Reply
4. Request (connection)
5. Reply
6. Create & inject interface
9. Create & inject interface
10. create tunnel
Node 1
Node 2
NSM Manager
Dataplane (kernel/vswitch)
3. Request
(connection)
7. create tunnel
8. Reply
K8S API Server
2. Select based on NetworkServiceEndpoint
NetworkService

@lcalcote
layer5.io/meshery
CPU Usage - Namespace
Appa Pod
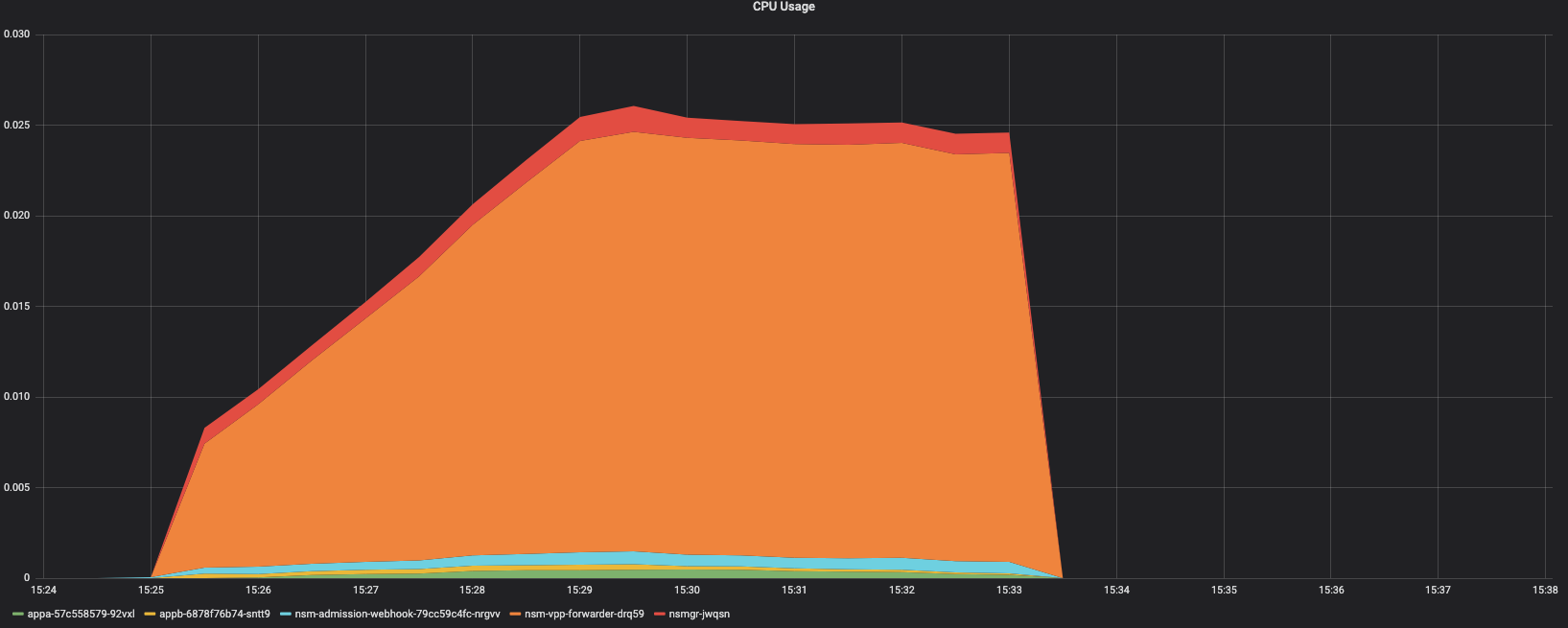
Appb Pod
NSM adminission Webhook
NSM VPP forwarder
NSM Mgr
@lcalcote
layer5.io/meshery
Memory Usage - Namespace
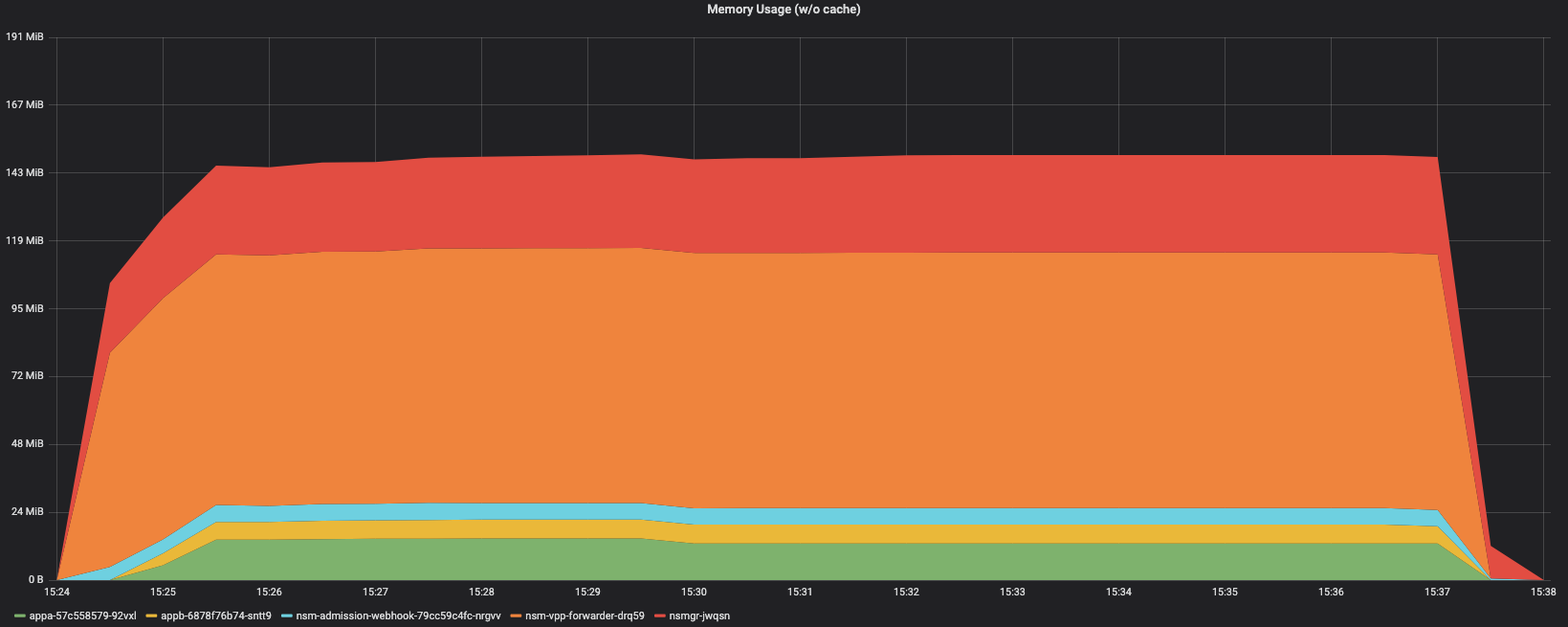
Appa Pod
Appb Pod
NSM adminission Webhook
NSM VPP forwarder
NSM Mgr
@lcalcote
layer5.io/meshery
Pod CPU Usage - NSE
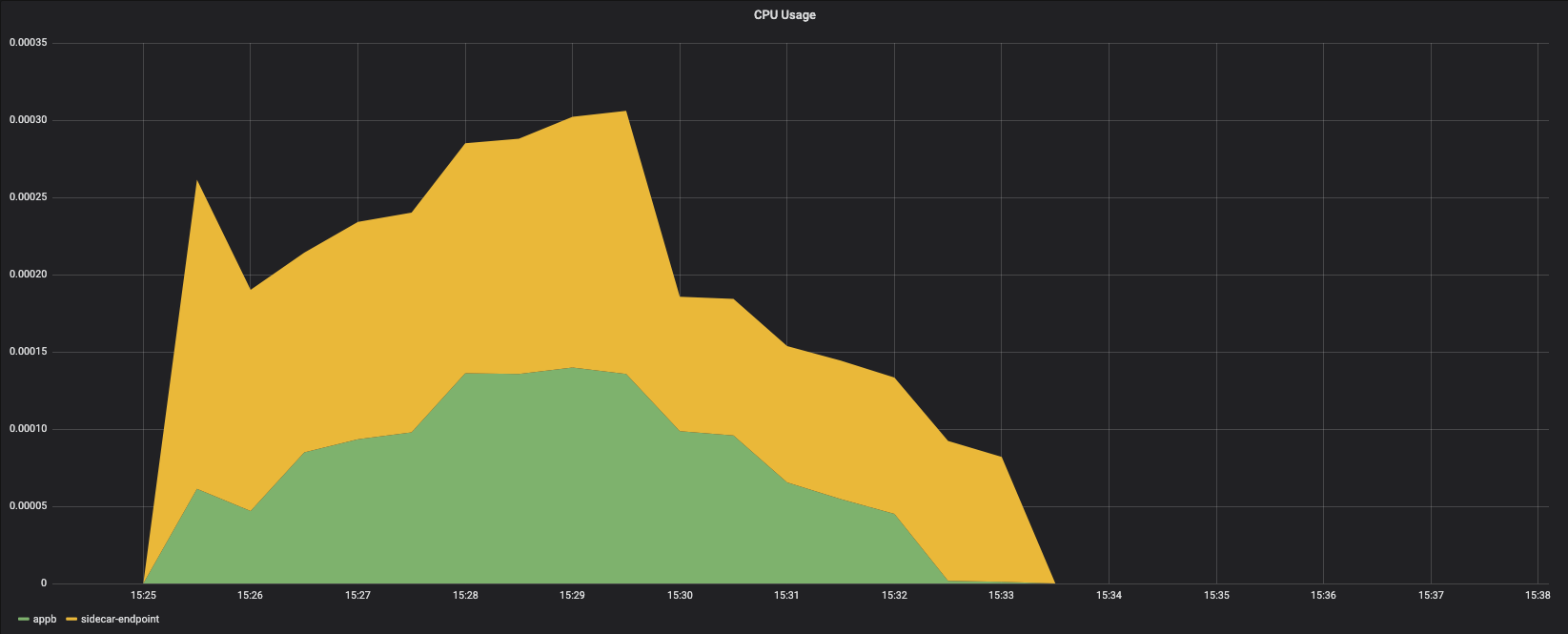
Appb
Sidecar
endpoint
@lcalcote
layer5.io/meshery
Pod CPU Usage - NSC
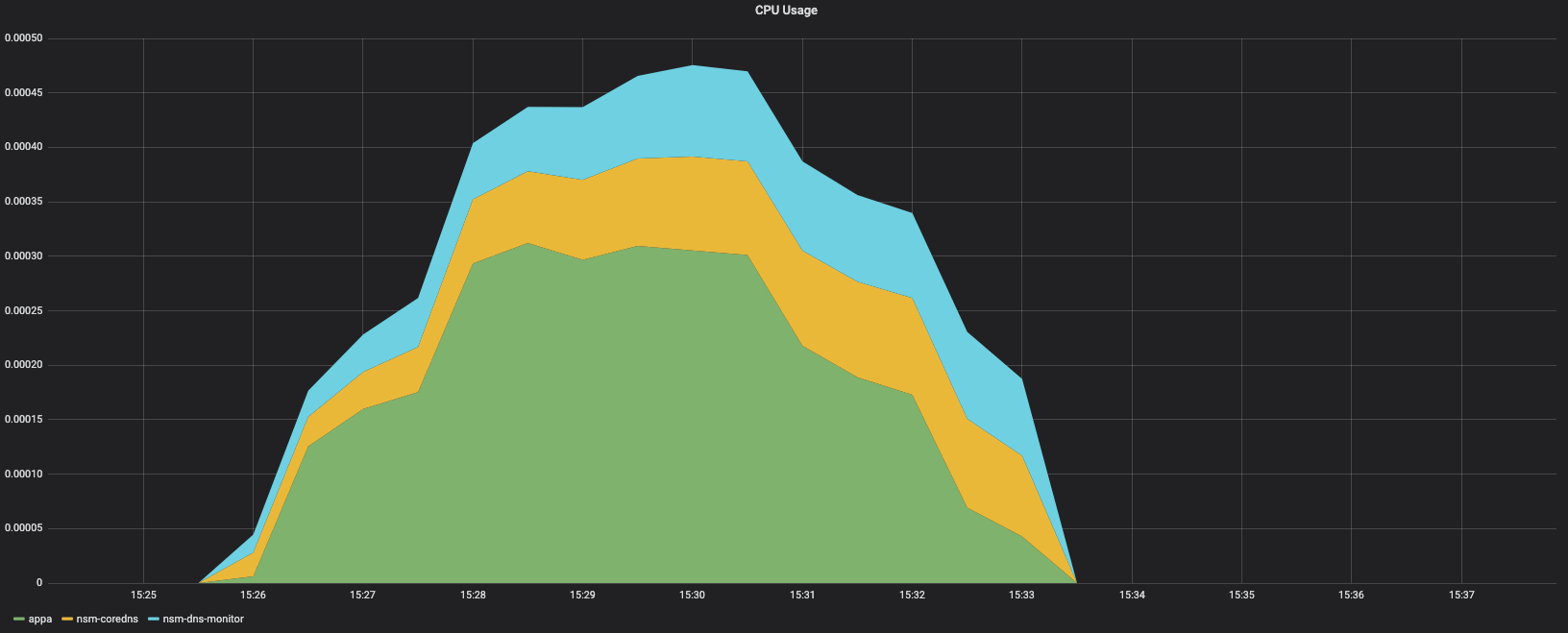
Appa
NSM
CoreDNS
NSM
DNS Monitor
@lcalcote
layer5.io/meshery
Pod Memory Usage - NSE
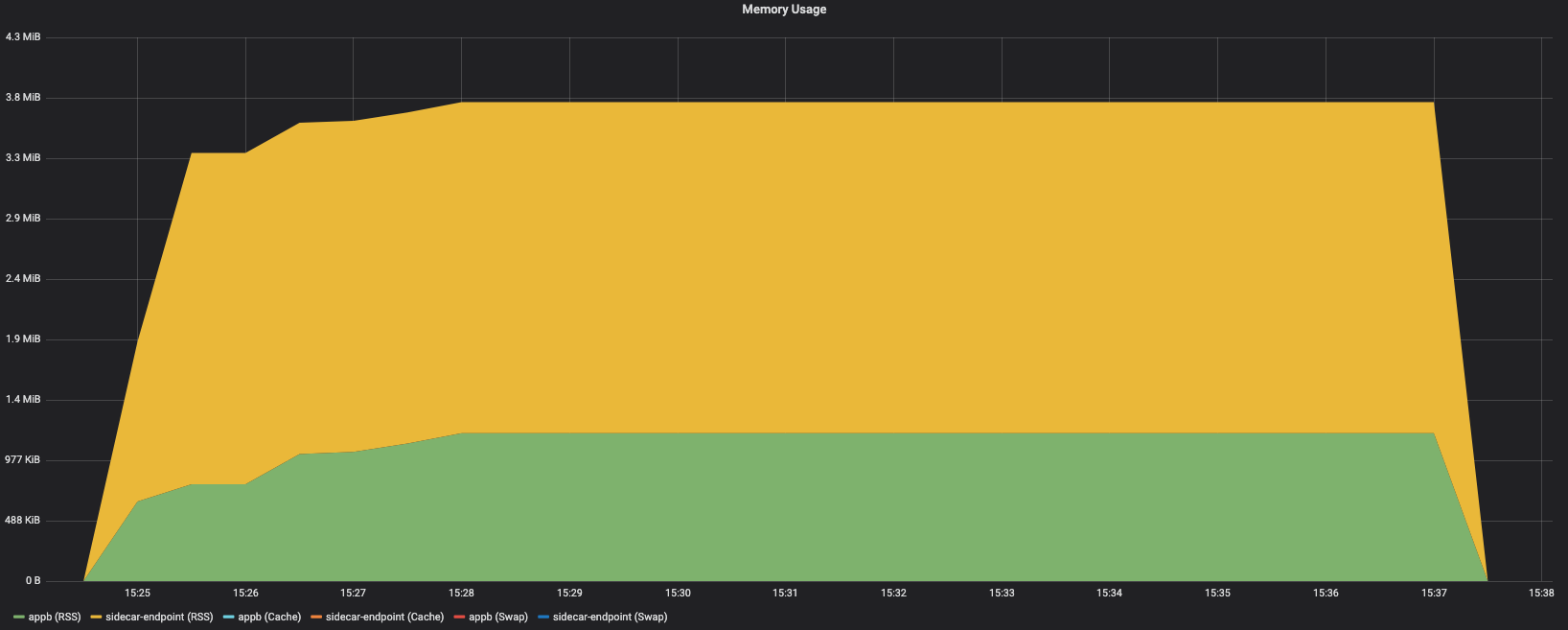
Appb
Sidecar
endpoint
@lcalcote
layer5.io/meshery
Pod Memory Usage - NSC
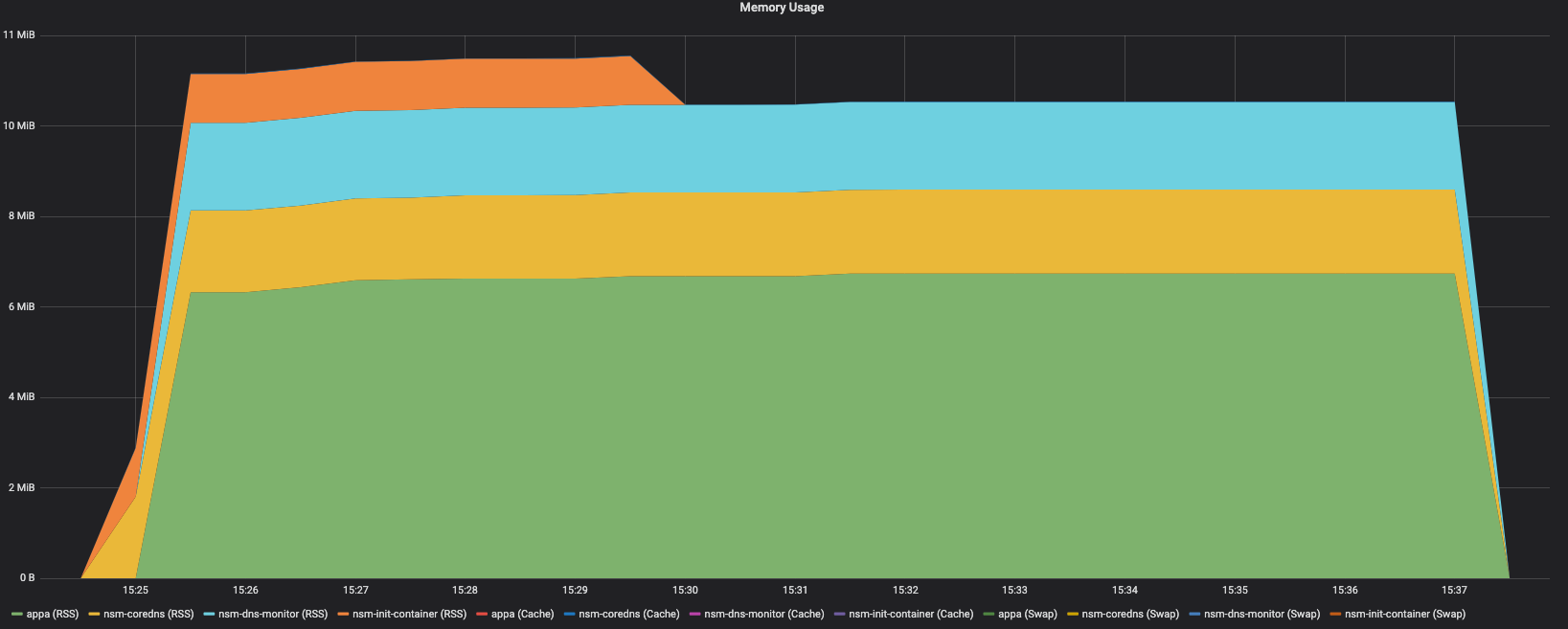
Appa
NSM
CoreDNS
NSM
DNS Monitor
NSM init
container
@lcalcote
layer5.io/meshery
Control Plane Memory

Istio
Linkerd
Consul
@lcalcote
layer5.io/meshery
Pod CPU Usage



Application resource consumption


@lcalcote
layer5.io/meshery
Control Plane CPU

Istio
Linkerd
Consul


Lee Calcote
cloud native and its management



layer5.io/subscribe

Girish Ranganathan
distributed systems, golang, operating at-scale,

Service Mesh Benchmark Specification
A project and vendor-neutral specification for capturing details of:
-
Environment / Infrastructure
-
Number and size of nodes, orchestrator
-
-
Service mesh and its configuration
-
Service / application details
Bundled with test results.

github.com/layer5io/service-mesh-benchmark-spec

@lcalcote
layer5.io/meshery
Client
Edge Cache
Istio Gateway
(envoy)
Cache Generator
Collection of VMs running APIs
service mesh
Istio VirtualService
Istio VirtualService
Istio ServiceEntry
Situation:
- existing services running on VMs (that have little to no service-to-service traffic).
- nearly all traffic flows from client to the service and back to client.
Benefits:
- gain granular traffic control (e.g path rewrites).
- detailed service monitoring without immediately deploying a thousand sidecars.
Ingress
Out-of-band telemetry propagation
Application traffic
Control flow
Proxy per Node
Service A
Service A
Service A
linkerd
Node (server)
Service A
Service A
Service B
linkerd
Node (server)
Service A
Service A
Service C
linkerd
Node (server)
Advantages:
-
Less (memory) overhead.
-
Simpler distribution of configuration information.
-
primarily physical or virtual server based; good for large monolithic applications.
Disadvantages:
-
Coarse support for encryption of service-to-service communication, instead host-to-host encryption and authentication policies.
-
Blast radius of a proxy failure includes all applications on the node, which is essentially equivalent to losing the node itself.
-
Not a transparent entity, services must be aware of its existence.
Control Plane
Data Plane
Node
NSM Manager
NSM Domain
Foo Container
Node
NSM Manager
NSM Domain
Bar Container
Out-of-band telemetry propagation
Control flow during request processing
application traffic
Application traffic
application namespace
telemetry scraping
Architecture
destination
Prometheus
Grafana
NSMe
domain
client
proxy-api
public-api
Network
Service
Mesh
Kubernetes API Server
layer5.io/books

Advantages:
-
Good starting point for building a brand-new microservices architecture or for migrating from a monolith.
Disadvantages:
-
When the number of services increase, it becomes difficult to manage.

Router "Mesh"

Fabric Model
Advantages:
-
Granular encryption of service-to-service communication.
-
Can be gradually added to an existing cluster without central coordination.
Disadvantages:
-
Lack of central coordination. Difficult to scale operationally.

Ingress or Edge Proxy
Advantages:
-
Works with existing services that can be broken down over time.
Disadvantages:
-
Is missing the benefits of service-to-service visibility and control.
NSM - multi node
NSMgr 2
Node 2
Cluster 2
NSMgr 1
Node 1
Cluster 1
eNSM 1
eNSM 2
VIM
VM
VM
VM
A project and vendor-neutral specification for capturing details of:
-
Environment / Infrastructure
-
Number and size of nodes, orchestrator
-
-
Service mesh and its configuration
-
Service / application details
Bundled with test results.
Control Plane
Data Plane
Foo Pod
Proxy Sidecar
Service Foo
Foo Container
Bar Pod
Proxy Sidecar
Service Bar
Bar Container
Out-of-band telemetry propagation
telemetry
scarping
Control flow during request processing
application traffic
Application traffic
application namespace
telemetry scraping
Architecture
Network Service Registry
Prometheus
Network Service Endpoint (NSE)
domain
client
public-api
Network
Service
Mesh
Network Service Client (NSC)
@lcalcote
layer5.io/meshery
Control Plane CPU

Istio
Linkerd
Consul