Application Security
Where left is the right direction
About me
Software Developer
Application Security
Agile Enthusiast
Open source contributions
I am
I do
I am
I do
About me
Software Developer
Application Security
Agile Enthusiast
Open source contributions
I am
I do
I am
I do
Agenda
Definition
Why?
How?
Who?
Definition
Wikipedia
Application security encompasses measures taken to improve the security of an application often by finding, fixing and preventing security vulnerabilities.
Gary McGraw
"...maintains that application security is a reactive approach, taking place once software has been deployed. Software security, on the other hand, involves a proactive approach, taking place within the pre-deployment phase."
Wikipedia
finding
fixing
preventing
Gary McGraw
application security reactive approach
software security proactive approach
Why?
Implementation bugs
Architectural bugs
Inexpensive
Expensive
Cost to fix bugs
Cost to fix bugs
Left
Right
Cost to fix bugs


How to?
Software Development Life Cycle
SDLC
Design
Code
Learning
Habits
How?
Design
Code
Learning
Habits
How?
How to?
Security by Learning
Training
Security by learning

Capture the flag
Security by learning

Consulting
Security by learning


Security by learning

$ docker run tyro/challengeDesign
Code
Learning
Habits
How?
How to?
Secure by Design
Architecture Review
Secure By Design

Attack Trees


Secure By Design
Security Features
Secure By Design


Secure By Design

Design
Code
Learning
Habits
How?
How to?
Secure Code
Code Review
Secure Code

Static Analysis
Secure Code

Dependency Management
Secure Code


Secure Code
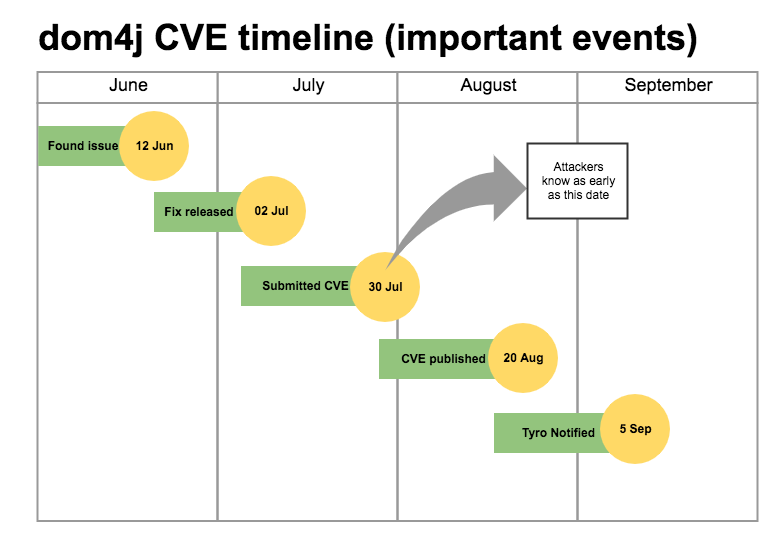
Design
Code
Learning
Habits
How?
How to?
Security Habits
Define Contracts
Security Habits

Build Pipeline

Security Habits
Pen Testing

Security Habits
Bug Bounty

Security Habits

Security Habits

How to?
Software Development Life Cycle
Reviewed!
SDLC Reviewed
Attack Trees
Security Features
Architecture Review
Code Review
Static Analysis
Dependency Management
Training
CTFs
Consulting
Contracts
Build Pipeline
Pen Testing
Bug bounty
Monitoring
Visibility
Drills


Infrastructure as Code

Who?
Responsibility

Accountability

Lessons


Title Text
