Authentication
Luxury or Necessity?

About Me
Mohammad Shahbaz Alam
Director, Alfaaz Lingua
Full Stack Developer
Auth0 Ambassador
Mozilla Representative
GDG Ranchi Organizer
@mdsbzalam


Agenda
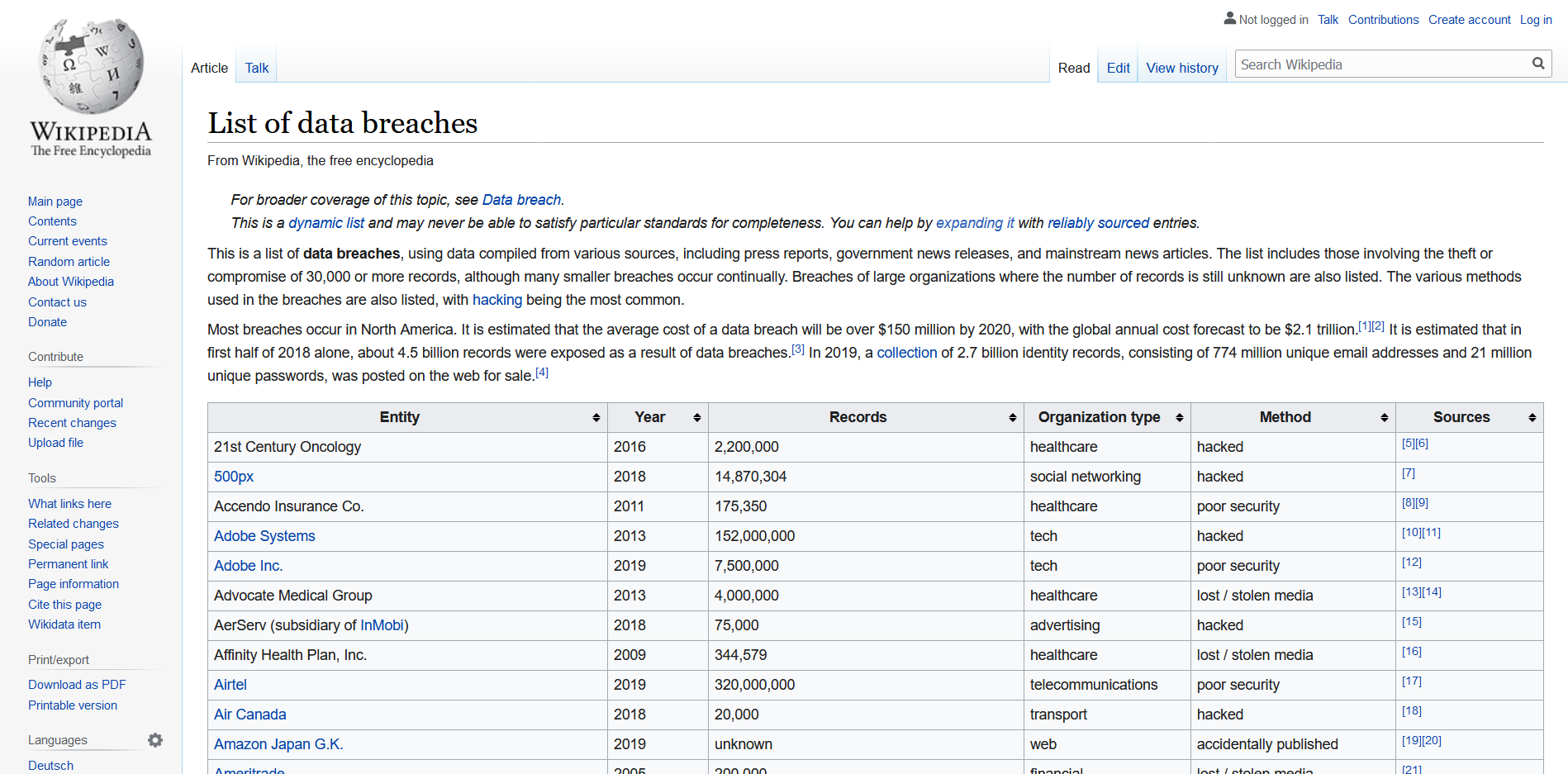
1. Biggest Data Breaches of 2020 (So far)
2. Developers and Users
3. Users - Password
4. Developers -
JWT, WebAuthn, Auth as Service
Biggest Data Breaches
So far in 2020
1. Marriott Suffers Another Credential-Based Breach
The Story
On March 31, 2020, Marriott posted an announcement that "an unexpected amount of guest information may have been accessed using the login credentials of two employees at a franchise property." That "unexpected amount" turned out to be the data of 5.2 million guests.
This news is particularly unfortunate for Marriott since it's only been two years since it discovered another massive breach, stemming from its acquisition of Starwood Hotels.
Marriott Suffers Another Credential-Based Breach
How the Breach Happened
We know that a hacker obtained the credentials of two employees at a Marriott property and used them to siphon data for roughly a month before being discovered. We don't know how that hacker obtained employee credentials, but credential stuffing and phishing are both likely culprits.
What Data Was Exposed
Help Net Security reports that the attacker accessed a wide range of personal data, including contact information, personal details like gender and birthday, and linked account data like airline loyalty programs.
Marriott Suffers Another Credential-Based Breach
The Lesson for Businesses
To protect customer data, you have to control how employees access data rigorously.
Marriott could have avoided this breach by implementing multi-factor authentication for employees attempting to access sensitive data. That way, it would have taken more than a password for the attacker to sneak into their systems.
In addition, Marriott could have gotten wise to the hacker's presence much sooner if their IAM system had monitored for suspicious behavior. Such a system would have flagged the situation —two employees at a franchise location accessing millions of guest records— as an anomaly that merited investigation.
2. Nintendo Is the Latest Victim of Credential Stuffing in Media
The Story
In April 2020, Nintendo announced that 160,000 accounts had been breached in a presumptive credential stuffing attack. Hackers had apparently been using the hijacked accounts to buy coveted digital items.
As a result of the breach, Nintendo discontinued the practice of letting users log in with their Nintendo Network ID (NNID). The company also recommended that users enable two-factor authentication to protect their data.
Nintendo is only the most recent victim of credential stuffing attacks targeting digital media. Netflix, Spotify, and Disney+ have all had similar issues in recent months and years.

Nintendo Is the Latest Victim of Credential Stuffing in Media
What Data Was Exposed
Once hackers gained access to Nintendo accounts, they could make purchases and view sensitive data like email address, birth date, and country.

How the Breach Happened
Nintendo said the compromised credentials were "obtained illegally by some means other than our service." That strongly suggests that the affected users weren't using unique IDs and passwords. So when their credentials were breached in another attack, hackers could use them to break into their Nintendo accounts.
Nintendo Is the Latest Victim of Credential Stuffing in Media
The Lesson for Businesses
Require multi-factor authentication.
Your users will thank you in the long term.

3. Slickwraps and the Case of the "White Hat" Hacker
4. Antheus Tecnologia Biometric Data Breach
5. LiveJournal Data Breach Comes Back to Haunt Users
6. LifeLabs Breach Exposes Almost Half of Canada
7. Wishbone Data Breach Puts Young Users at Risk
8. Shocking Revelations From an Australian Football Data Breach
9. CAM4 Exposes 10.88 Billion Records
10. ExecuPharm Data Stolen and Published in a Ransomware Attack
11. EasyJet Customers Hit Hard
.
.
.
USER
Awareness
PASSWORDS
Passwords should be like Joey

WHAT'S A PASSWORD?
ANYTHING THAT'S A SHARED SECRET!
PASSWORD1234
A string
RKYLHWK8@YB&YTI!8UKZH#TY?
A string
CAN BE HARD TO REMEMBER
IF COMPLEX!
A PASSWORD MANAGER CAN HELP!
CAN BE HARD TO GUESS( BY SOMEONE) IF COMPLEX!
BUT DO USE PASSWORD MANAGER SO YOU DON'T FORGET!

credit
1234
A pincode
NOT SO HARD TO GUESS
OFTEN COMBINED WITH THE MAXIMUM ALLOWED NUMBER OF ATTEMPTS!
FAIRLY EASY TO REMEMBER
USUALLY USED ONLY WITH ACCESS TO A PHYSICAL THING
(CARDS, PHONES, KEYPADS, ...)
A pattern
Passwordless ✨
ONE TIME PASSWORDS
Valid for one-time use
Often expire after a certain time
Sent directly to the user
SENT IN SMS
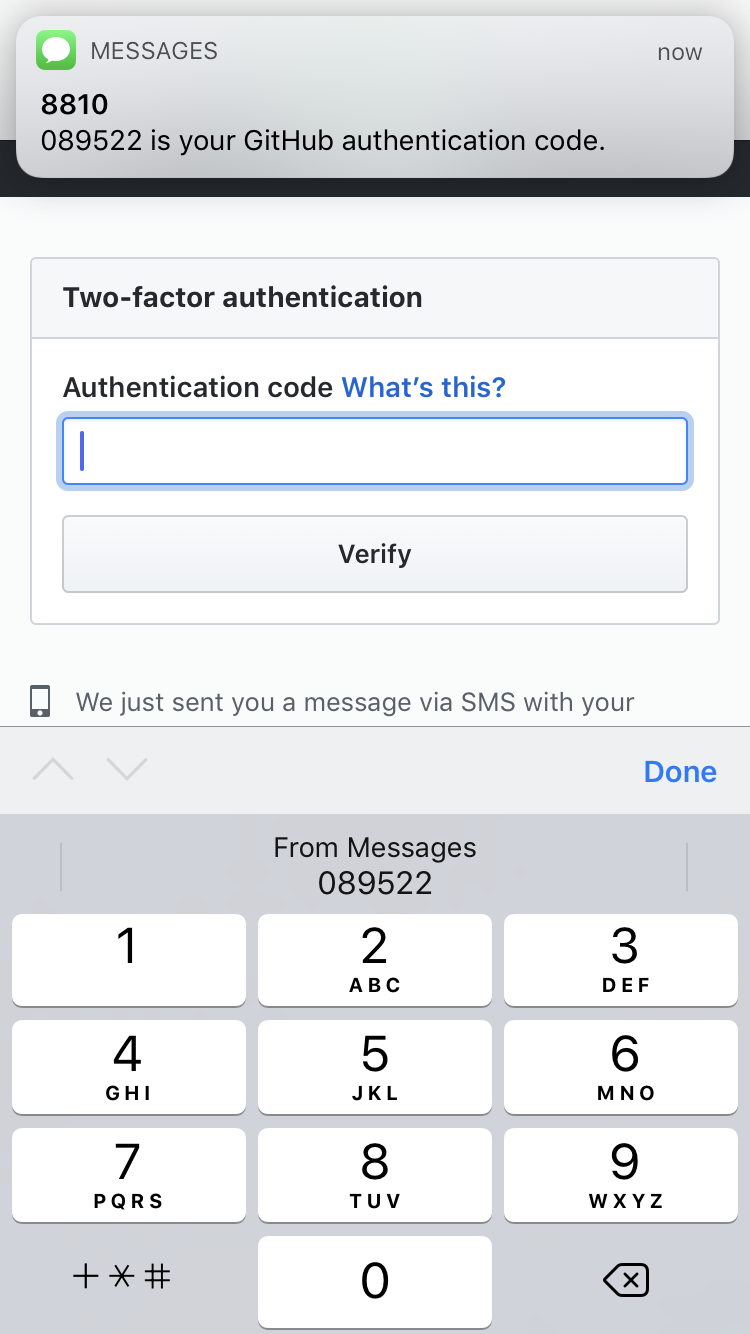
iOS and Android let you fill in the OTP with the press of a button
NOT ALL TELECOM OPERATORS TAKE SECURITY SERIOUS, SMS MESSAGES CAN BE INTERCEBTED
You need your cellphone on hand
SENT IN AN EMAIL
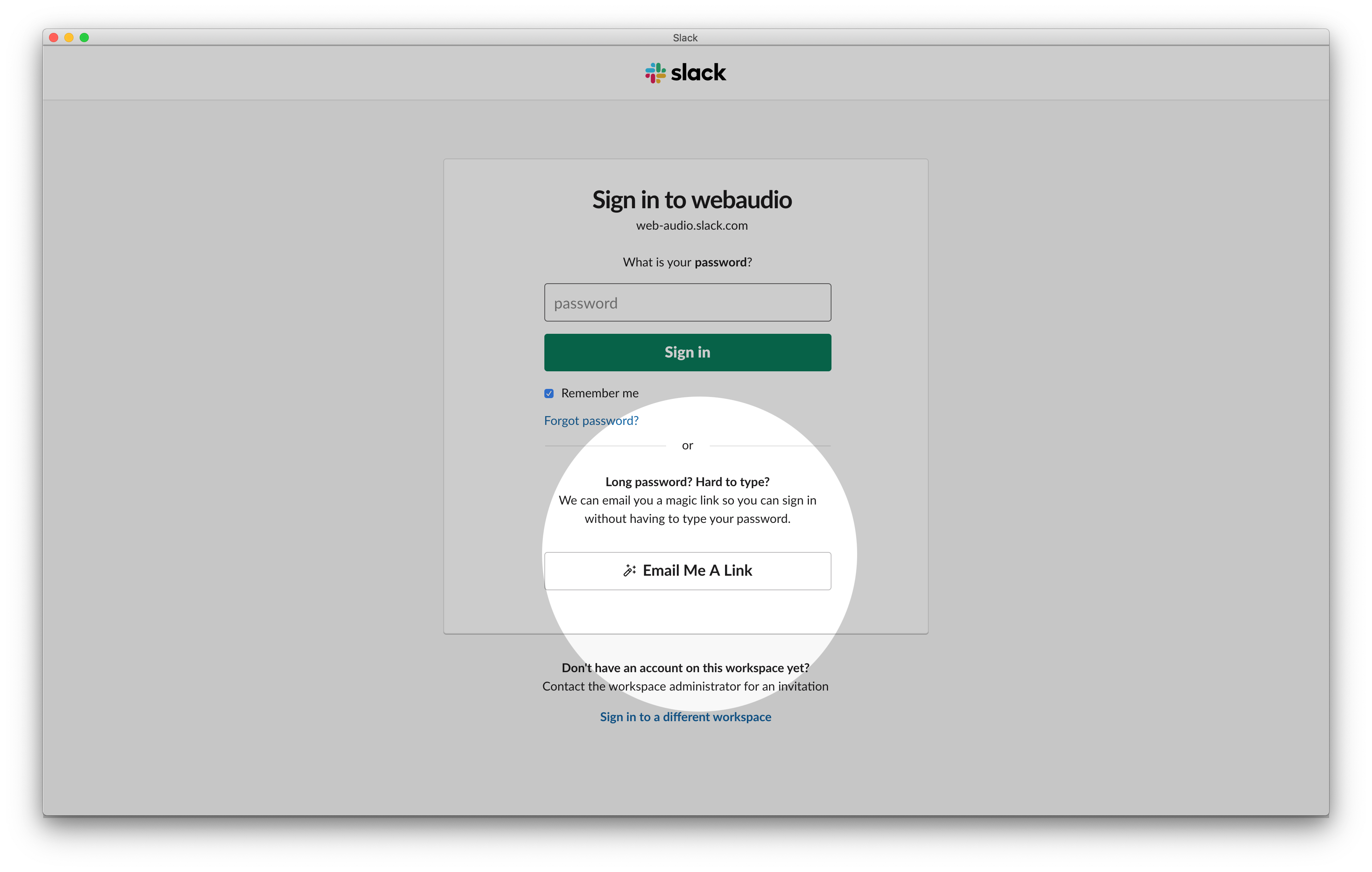
You don't need a second device
EMAILS CAN BE INTERCEPTED
AUTHENTICATOR APP
SOCIAL

ONE LESS PASSWORD TO REMEMBER
ONLY GIVE PASSWORDS TO A SERVICE YOU TRUST
YOU RELY ON ANOTHER SERVICE FOR YOUR AUTHENTICATION
OFTEN USED AS A SECOND FACTOR

HOW'S YOUR PASSWORD SHOULD BE?
So The Question for Users would be,
LIKE JOEY

LIKE JOEY
LIKE JOEY

SO DON'T SHARE IT WITH ANYONE
LIKE JOEY

LIKE JOEY
USE UPPERCASE AND LOWERCASE CHARACTER
LIKE THIS?
KXnCTowPLjkTIwQ

LIKE JOEY

Joey doesn't know French, he makes it up,
So, make your Passwords randomly
LIKE JOEY
Joey has One Chandler
Your Password should only be used on one account.

Tips for a good password
-
Use a complex password
-
Don’t use personal data
-
Don’t reuse passwords
-
Change passwords frequently
xkcd: Password Strength

So how about this?
DrTdMeToEtAeBtILePe

Easy to remember!
DrTdMeToEtAeBtILePe
Doctor told be to eat Apple but I like Pineapple


DEVELOPER
Awareness
1. JSON Web Tokens ( JWT )
2. WebAuthn
3. Authentication as a Service
JSON Web Tokens
JWT
JWT
What is JSON Web Tokens?
- Based on Web Standard ( RFC 7519 )
- securely communicate JSON Objects
- A way to encode information
- Allow shared parties to verify information is legit
- Secret-based Verification
- When secret changes then information is no more legit
- Consists of a header, payload and signature
- Self-contained
JWT
JSON Web Token

JWT
The JWT Header
The header is a JSON Object usually consisting of the type( typ ) , which is JWT, and the algorithm used for encrypting the JWT (alg ):
{
"alg": "HS256",
"typ": "JWT"
}JWT
The JWT Payload
The Payload is a JSON object that consists of user defined attributes ( called public claims ) . Some attributes are defined in the standard ( these are called reserved claims ).
{
// reserved claim
"iss": "https://myapi.com",
// public claim
"user": "mdsbzalam"
}JWT
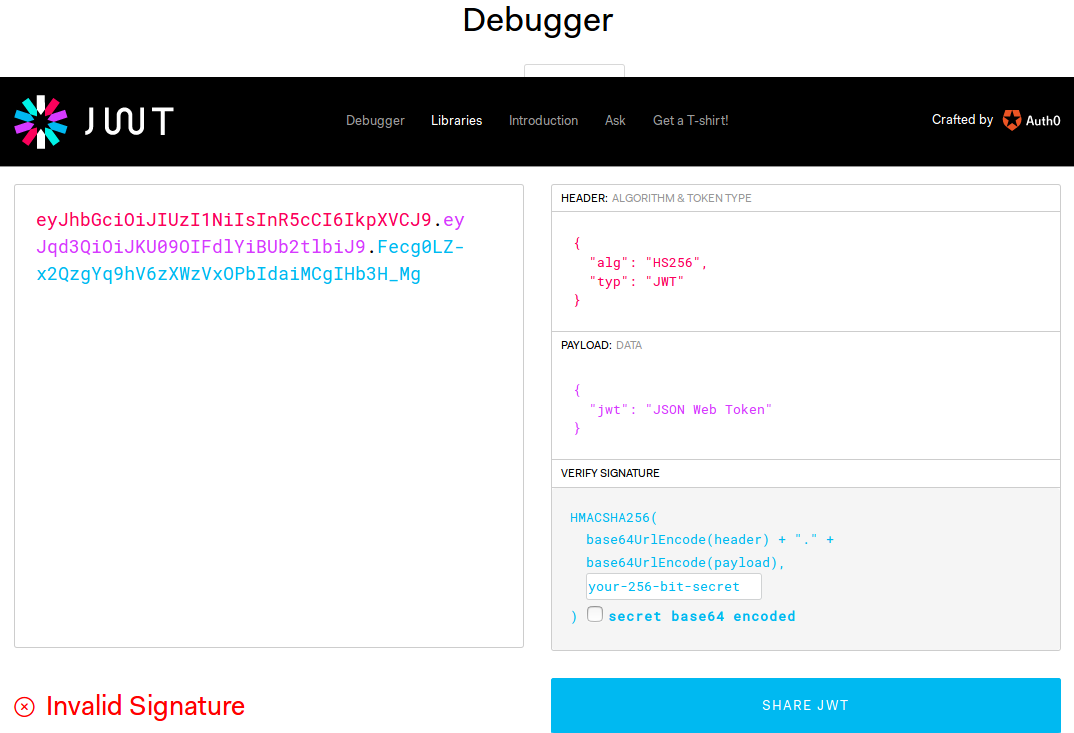
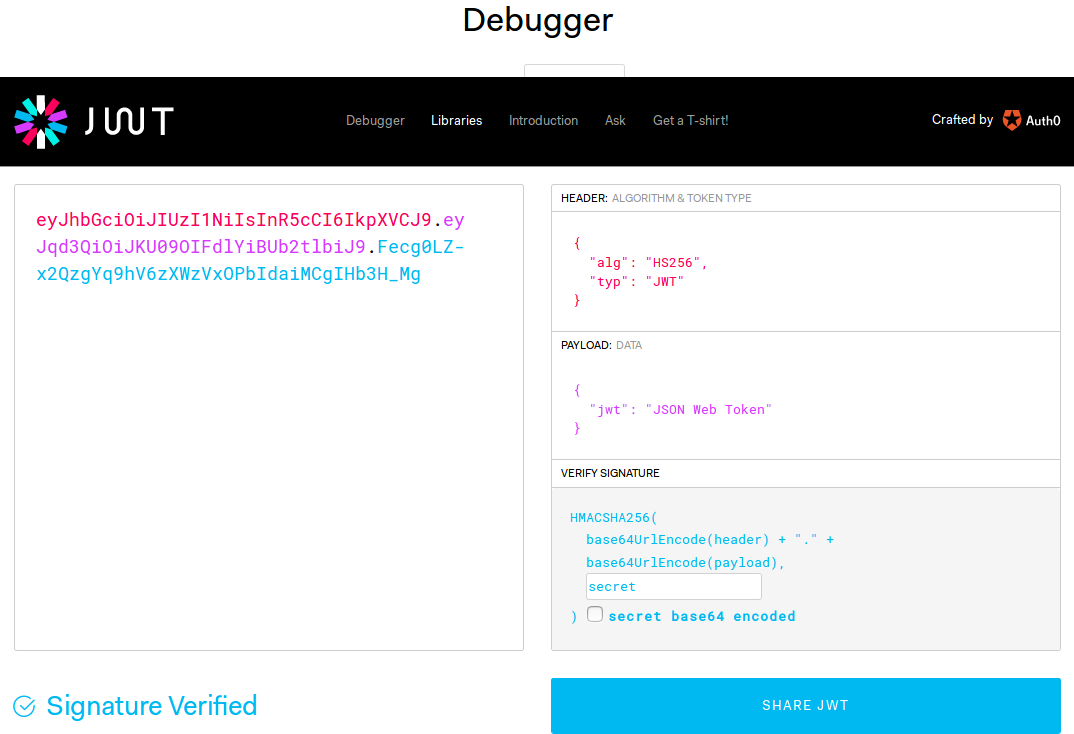
The JWT Signature
The Signature is the encoded header and payload, signed with a secret.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret
)
This accomplishes several tasks at once, including:
- Proves the identity of the sender
- Ensures the message has not changed
JWT
The JWT Token
A finished token looks like [encoded header].[encoded payload].[signature] :
JWT

The JWT Token
WEB AUTHENTICATION API 🤩
WEBAUTHN 🤩
KEY BASE AUTHENTICATION
HARDWARE AUTHENTICATION


DEMO


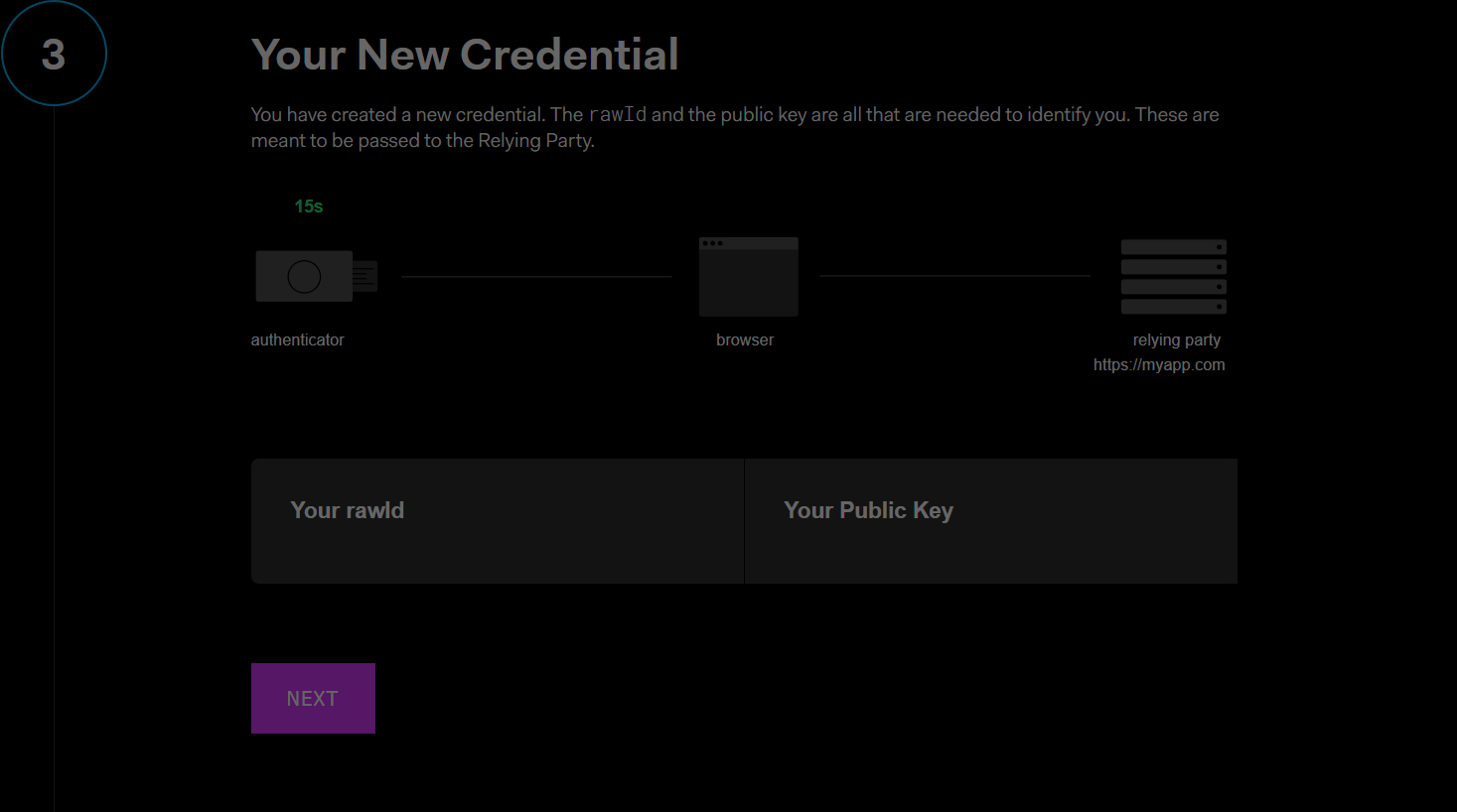
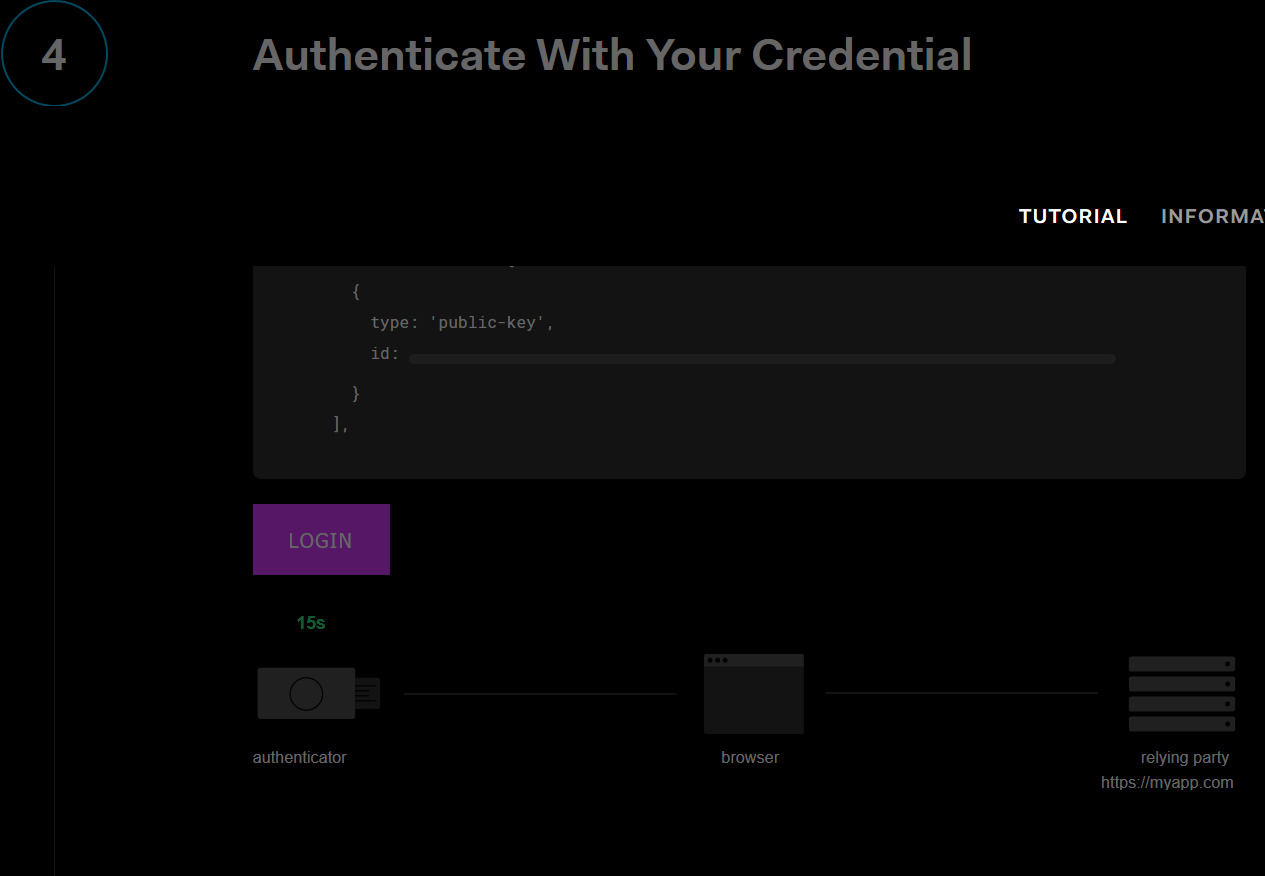
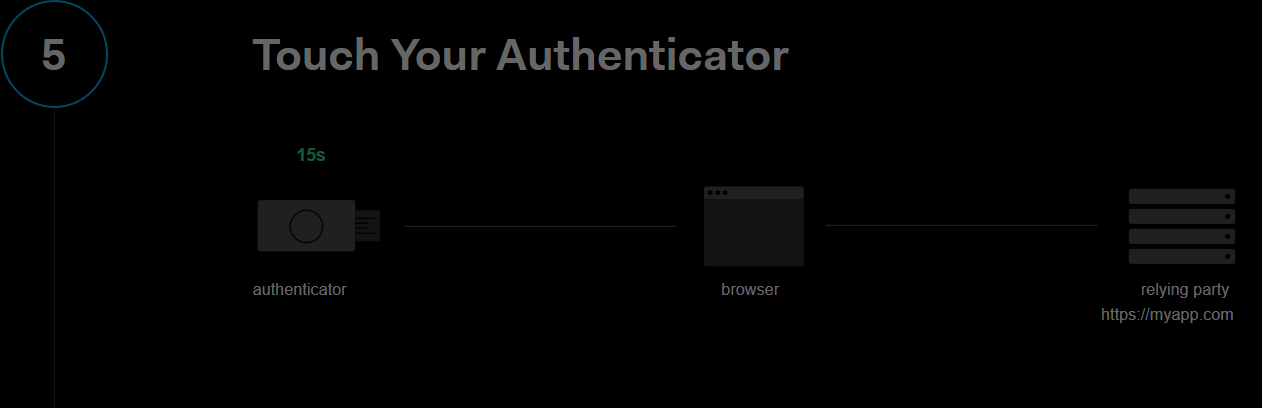

navigator.credentials
.create({
publicKey: {
// random, cryptographically secure, at least 16 bytes
challenge: base64url.decode("<%= challenge %>"),
// relying party
rp: {
name: "Awesome Corp" // sample relying party
},
user: {
id: base64url.decode("<%= id %>"),
name: "<%= name %>",
displayName: "<%= displayName %>"
},
authenticatorSelection: { userVerification: "preferred" },
attestation: "direct",
pubKeyCredParams: [
{
type: "public-key",
alg: -7 // "ES256" IANA COSE Algorithms registry
}
]
}
})
.then(res => {
var json = publicKeyCredentialToJSON(res);
// Send data to relying party's servers
post("/webauthn/register", {
state: "<%= state %>",
provider: "<%= provider %>",
res: JSON.stringify(json)
});
})
.catch(console.error);navigator.credentials.create
navigator.credentials
.get({
publicKey: {
// random, cryptographically secure, at least 16 bytes
challenge: base64url.decode("<%= challenge %>"),
allowCredentials: [
{
id: base64url.decode("<%= id %>"),
type: "public-key"
}
],
timeout: 15000,
authenticatorSelection: { userVerification: "preferred" }
}
})
.then(res => {
var json = publicKeyCredentialToJSON(res);
// Send data to relying party's servers
post("/webauthn/authenticate", {
state: "<%= state %>",
provider: "<%= provider %>",
res: JSON.stringify(json)
});
})
.catch(err => {
alert("Invalid FIDO device");
});navigator.credentials.get
Authentication as a Service
Authentication as a Service
1. Auth0
2. Firebase
3. Okta
.
.
.



Why choose them?
1. One Stop Solution to all your Authentication needs
2. Single Sign-On
3. Enterprise Connections
4. Passwordless email and SMS
5. Multi-factor Authentication
6. Brute Force Protection
7. Breached Password detection
Authentication
Is
Luxury?
or
Necessity?
So the Question is,
Resources
General JWT Resources
jwt.io
JWT Handbook
http://bit.ly/jwt-book
WebAuthn
Connect with me
Youtube
mdsbzalam@gmail.com
@mdsbzalam
Slide
@mdsbzalam

Thank you
@mdsbzalam
