LXC, Docker
& CoreOS
Sfeir Info Days, April 2014
Christoph Meier, Sfeir Benelux
Change Log
- 2014-07:
Update dockerfile for demo app
Fix type in demo code
Fix images after docker site update
- 2014-04:
Initial release for SID
LinuX Containers
What's LXC ?
History
-
started by Google in 2006
-
merged into kernel version 2.6 in 2007
- many improvements since
- stable since kernel version 3.8 in 2013
Goal
offer the same level of isolation and control as a VM
without the downside of running a guest OS
Virtual Machines
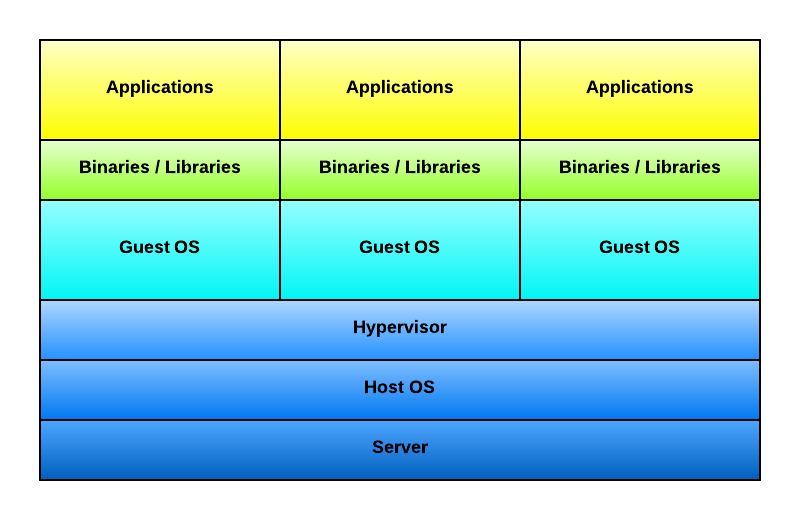
LXC
Container
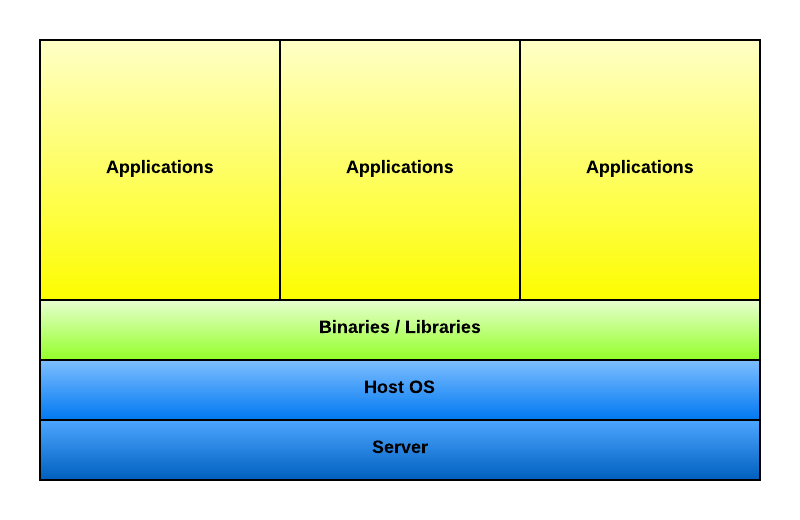
- host provides kernel + core
- filesystem, network, etc are shared
- but you control what and how you share
Features
-
Kernel namespaces
- Control groups (cgroups)
-
Apparmor and SELinux profiles
-
Seccomp policies
-
Chroots (using pivot_root)
- Kernel capabilities
namespaces
isolate processes from one another
- filesystem: read only, read write, share, slave, private
- networking: root, bridge, socket activation
- process: ps
- etc
cgroups
control resource allocation to processes
- I/O: limit reads / writes
- CPU: limit CPU usage
- Memory: limit total memory available
Performance
- processes are isolated BUT run on the host
- CPU = native performance
- Memory = almost native performance
- Networking = small overhead
- I/O = small overhead
Summary
- LXC != lightweight VM
- run on host but still isolated
- share kernel + core
- share resources
- not portable
- specific configurations
LXC alone is not enough but it is the backbone
we needed to build the next generation systems
Docker
What's docker ?
Why ?
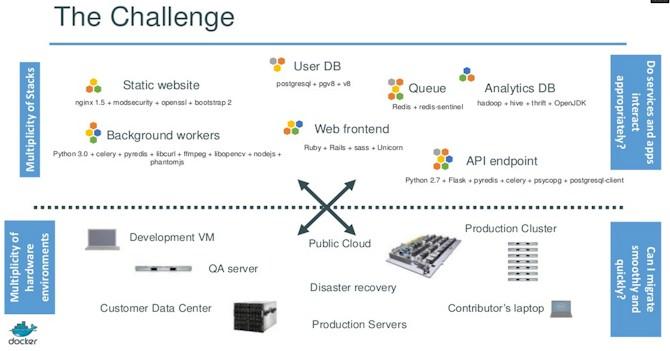
The challenge
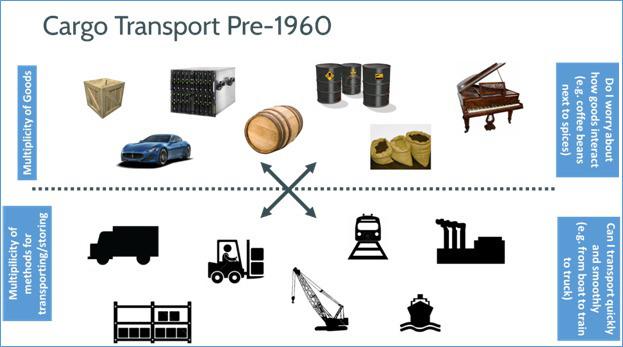
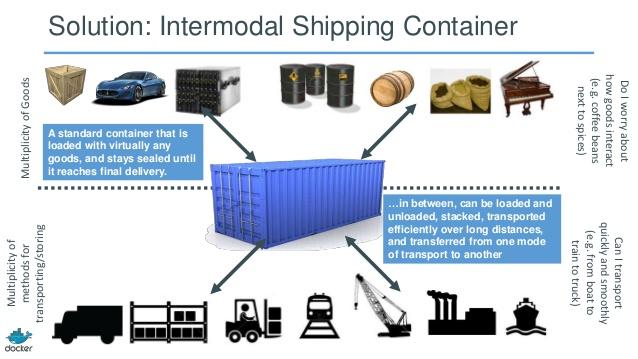
Analogy
Shipping container
Docker container
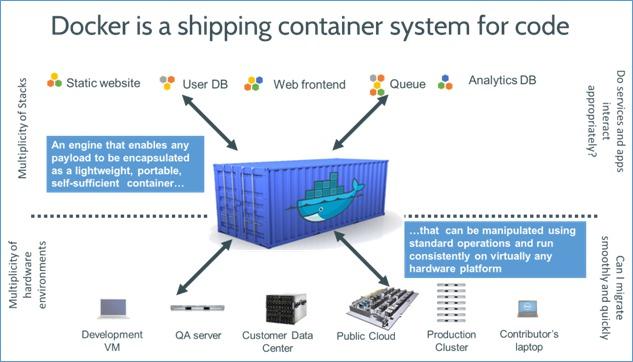
Main Features
- encapsulate anything & its dependencies
- run on virtually and hardware
-
resource, network & content isolation
- standard operations: stop, start, etc
- lightweight
- quick to move and manipulate
- repository
- versioning
- automation
Basic Functions
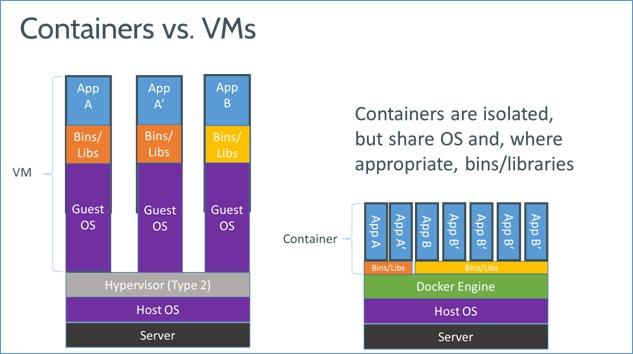
How does it work ?
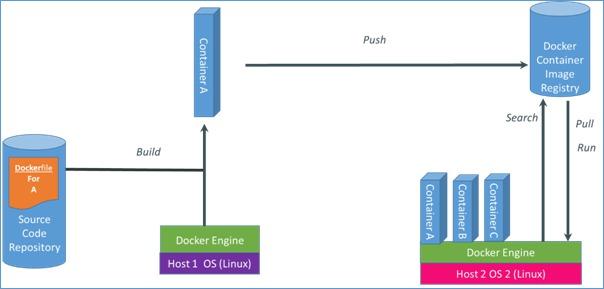
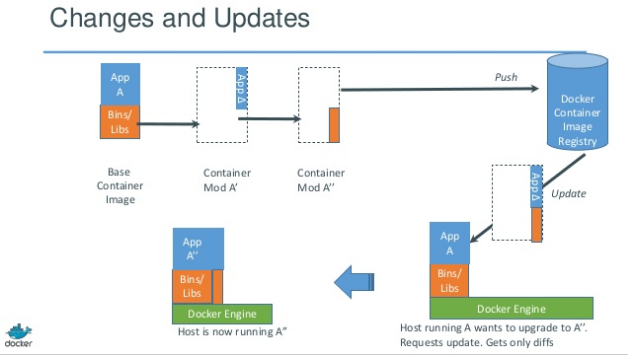
Lightweight containers
Demo
Install boot2docker
- lightweight Linux based on Tiny Core Linux
- made specifically to run Docker containers
- runs completely from RAM
- weighs ~27MB
- boots in ~5s
Mandatory "Hello World"
$ boot2docker init$ boot2docker upStarting boot2docker-vm...Started.
$ docker run ubuntu:latest /bin/echo hello worldhello world$ docker ps -a
$ docker run -d ubuntu:latest /bin/sh -c "while true; do echo ping; sleep 1; done"bd45aacc39$ docker ps$ docker attach bd45aacc39$ docker logs bd45aacc39
Sample App
- node.js & npm must be installed
- express is installed with npm
- only 2 files (available on github)
$ git clone https://github.com/meier-christoph/sid-docker-demo-app.git$ cd sid-docker-demo-app$ npm install$ node app
Build Docker Container
using a Dockefile
- instructions for provisioning
- base image
- libraries & applications
- process to run
- resources (exposed and/or required)
$ docker build -t meierc/sid-docker-demo-app .$ docker images
$ docker run -d -p 8080:8888 meierc/sid-docker-demo-app $ boot2docker ssh -L 8080:localhost:8080Share Container
$ docker login$ docker push meierc/sid-docker-demo-app
$ docker run -d -r 8080:8888 meierc/sid-docker-demo-appBest Practices
- build images in layers !!!
- use tags !!!
- don't use 'latest'
- don't use apt-get upgrade
Things to improve
- container logs
- monitoring in general
- container linking
- container versioning
Summary
- containers made easy
- repeatable builds
- portable containers
- re-use images / layers
- public and private repositories
- standard interface for ops (stop, start, etc)
Docker provides a layer of abstraction between
the OS and the applications.
What about an OS that supports docker out of the box ?
CoreOS
What's CoreOS ?
Linux distribution designed to run services
at scale and high resilience.
Features
- kernel & core
- ~160MB RAM
- fast boot time
- no package manager
- read only
- docker
- etcd
- systemd
- fleet
- cloud-config
Update OS
The core filesystem is read only, how do you update CoreOS ?
- download entire image of update
- install in offline root partition
- restart on new root partition
- previous images is still available for easy rollback
Install & Update Apps
All applications run inside docker containers
- all libraries and dependencies are in the container
- no more version conflicts or side effects
- install app = run new container
- update app = update container
- fast, only a few seconds
- easy to test
- easy to rollback
etcd
distributed key value store
- master election
- distributed by raft protocol
- > 1000 writes / second
- easy listen for changes
- store configurations
- connection details
- etc.
systemd
init system for starting, stopping and managing processes
- units = lifecycle
- service = app
- target = run level
[Unit]
Description=My Advanced Service
After=etcd.service
After=docker.service
[Service]
ExecStart=/bin/bash -c '/usr/bin/docker start -a apache || /usr/bin/docker run -name apache -p 80:80 coreos/apache /usr/sbin/apache2ctl -D FOREGROUND'
ExecStartPost=/usr/bin/etcdctl set /domains/example.com/10.10.10.123:8081 running
ExecStop=/usr/bin/docker stop apache
ExecStopPost=/usr/bin/etcdctl rm /domains/example.com/10.10.10.123:8081
[Install]
WantedBy=multi-user.targetfleet
systemd for entire cluster
- deploy container on arbitrary host
- distribute services across cluster
- multiple instances of same service
- re-schedule on failure
- systemd + extra fields
subgun-http.1.service
[X-Fleet]
X-Conflicts=subgun-http.*.servicesubgun-presence.1.service
[X-Fleet]
X-ConditionMachineOf=subgun-http.1.service
cloud-config
configure users, networking, etc. on startup
- makes adding hosts to the cluster easy
- configure once, use everywhere
- all hosts are identical
- easy to maintain
#cloud-config coreos: etcd: name: node001 discovery: https://discovery.etcd.io/<token> addr: $private_ipv4:4001 peer-addr: $private_ipv4:7001units: - name: etcd.service command: start - name: fleet.service command: start
Summary
- next generation OS
- distributed
- easy updates
- easy to configure
Things to improve
- etcd integration
- configd
- fig