SYP 2018 - Porto Edition
Acknowledgments
Purpose
- Demystifying hacking
- Primer on security
- Raise awareness
$ whoami
miguel regala, full time freelancer, security researcher, part time traveler, half hacker, half mercenary, casabranca, noob surfer, gamer, bitcoin owner (rip savings)
Hacking
Hacker - hack·er
- "a person who secretly gets access to a computer system in order to get information, cause damage, etc. : a person who hacks into a computer system", from merriam-webster dictionary

Hacking in the news

- Bad guy
- Wears a hoodie
- Uses gloves
- Very bad posture!
Hacking in the media

"I'll create a GUI interface using VBA to track the IP address"

What we actually look like
Taken at H1-4420 London
What we really do

It's all about the mindset



OC Hacker

Security
- Physical
- Infrastructure
- Social Engineering
- Web

Why knock on the frontdoor..

..when you can just go around it

Weakest link

Security
Physical- Infrastructure
- Social Engineering
- Web
Infrastructure
- SCADA - Supervisory control and data acquisition
- Industrial Control System
- "Remote Control"

- Critical infrastructure

@Hoover Dam, US
Infrastructure

Somewhere @Iran..
Infrastructure
- Portugal is no exception
- From the cool guys at Binary Edge
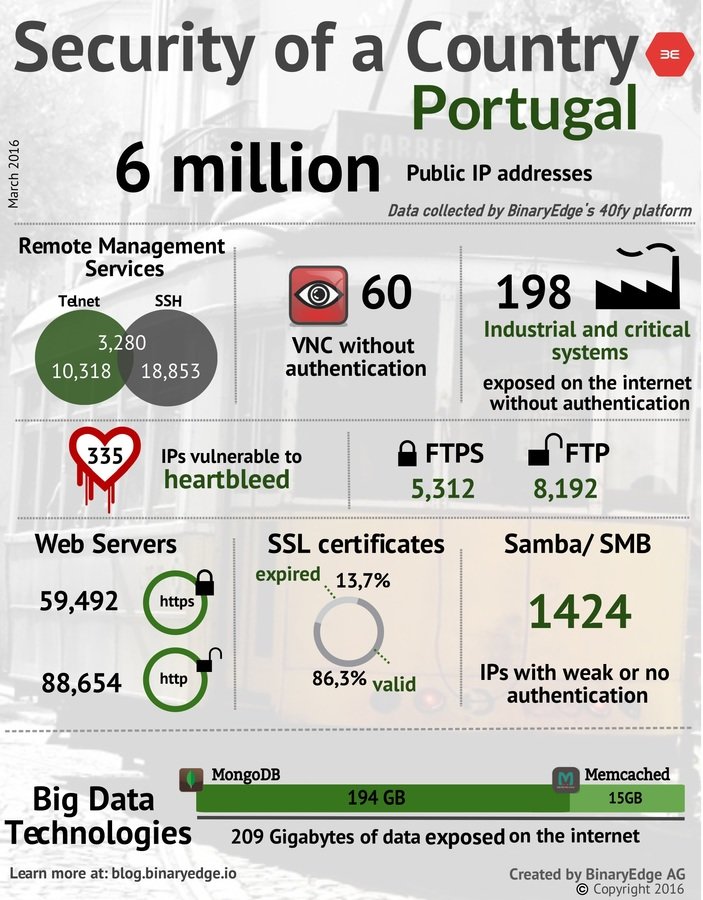
Infrastructure
Not critical but.. 😅
Security
PhysicalInfrastructure- Social Engineering
- Web
- People are always the weakest link
- SE: "any act that influences a person to take an action that may or may not be in their best interest"
- Phishing
- Pretexting
- Impersonation
$ sudo give me your password
Social Engineering

- Amazing stories
- Rumored to "start a nuclear war by whistling into a pay phone"
Social Engineering
Security
PhysicalInfrastructureSocial Engineering- Web
- Injection
- Authentication
- Authorization
- IDOR
Top flaws
In a nutshell:
- Run arbitrary code in the browser of a victim in the context of the vulnerable domain
XSS - Cross Site Scripting
<html>
<head> <title> Simple Vulnerable Page </title> </head>
<body>
<p> Your text is: hello </p>
</body>
</html>
$_GET['text']
GET https://vulnerable-website.com/home.php?text=hello
GET https://vulnerable-website.com/home.php?text=<script>prompt('hello')</prompt>
<html>
<head> <title> Simple Vulnerable Page </title> </head>
<body>
<p> Your text is: <script>prompt('hello')</script> </p>
</body>
</html>
$_GET['text']
How:
- https://vulnerable-website.com/home.php?vulnerableParam=%3c%73%63%72%69%70%74%3e%70%72%6f%6d%70%74%28%64%6f%63%75%6d%65%6e%74%2e%63%6f%6f%6b%69%65%29%3c%2f%73%63%72%69%70%74%3e
XSS - Cross Site Scripting
- Payload is URL encoded: %3c%73%63%72%69%70%74%3e%70%72%6f%6d%70%74%28%64%6f%63%75%6d%65%6e%74%2e%63%6f%6f%6b%69%65%29%3c%2f%73%63%72%69%70%74%3e
- Turns into:
<script>prompt(document.cookie)</script>
XSS - Cross Site Scripting
Stealthier:
XSS - Cross Site Scripting
Fixing:
- Encode user input
- Escape output
XSS - Cross Site Scripting
Always treat input as malicious
GET https://vulnerable-website.com/home.php?text=<script>prompt('hello')</prompt>
<html>
<head> <title> Simple Vulnerable Page </title> </head>
<body>
<p> Your text is: <script>prompt('hello')</script> </p>
</body>
</html>
htmlspecialchars($_GET['text'])
In a nutshell:
- Force the user to make an unintended action
CSRF - Cross Site Request Forgery
200 - OK
Successful transfer!
GET https://vulnerable-bank.com/transfer.php?from=me&to=alice&amount=10


200 - OK
Successful transfer!
GET https://vulnerable-bank.com/transfer.php?from=me&to=alice&amount=10


Cookie: logged=1; auth=PHNjcmlwdD5wcm9tcHQoZG9jdW1lb=
200 - OK
Successful transfer!
GET https://vulnerable-bank.com/transfer.php?from=me&to=attacker&amount=9000



https://goo.gl/cute-kittens
Solution:
- CSRF token
- Shared secret between user and web application
CSRF - Cross Site Request Forgery
200 - Login OK
Here's your CSRF token:
YXNwZG9ramFwb3NkazkwMzQ4eTRybmZta2ws52huamtv==
GET https://vulnerable-bank.com/login.php


200 - OK
Successful transfer!
GET https://vulnerable-bank.com/transfer.php?from=me&to=alice&amount=10&csrf=YXNwZG9ramFwb3NkazkwMzQ4eTRybmZta2ws52huamtv==


200 - OK
Invalid CSRF token, transfer aborted.
GET https://vulnerable-bank.com/transfer.php?from=me&to=attacker&amount=9999&csrf=??????????



https://goo.gl/cute-kittens2
Solution:
- Don't rediscover the wheel
- Search for language + csrf framework
- OWASP
CSRF - Cross Site Request Forgery
Getting into Security
CoursesCertifications-
Prejudice- inclusive field - Workshops
- Lots of self learning
Getting into Security
- Lots of self learning
- CTF - Capture the Flag
- Bug Bounty Programs
CTF - Capture the flag
- Team oriented challenge
- Get the flag, win points
- Different categories:
- Web
- Reverse Engineering
- Mobile
- Trivia
- Crypto
- etc..
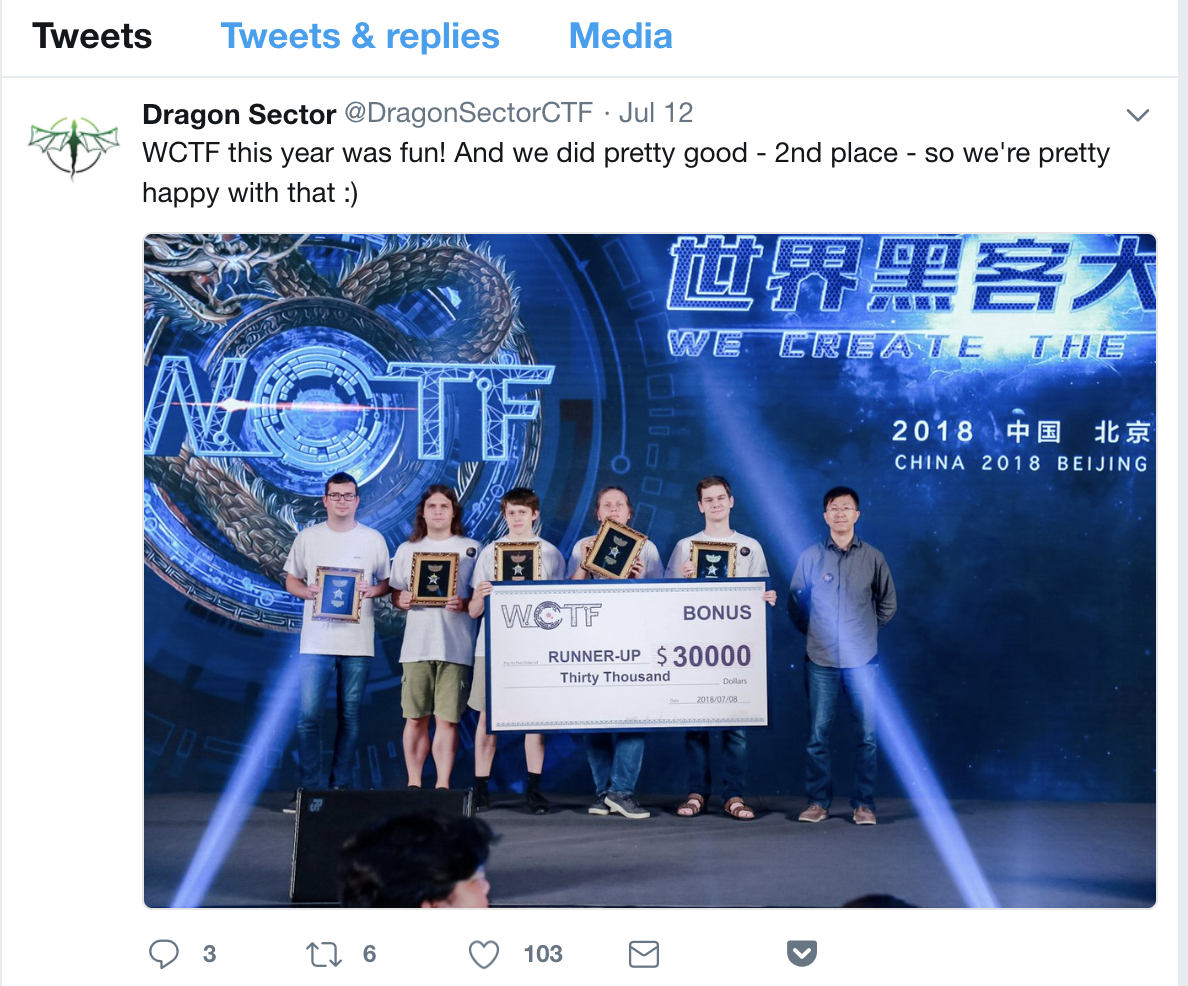
Oh. And it pays off too.
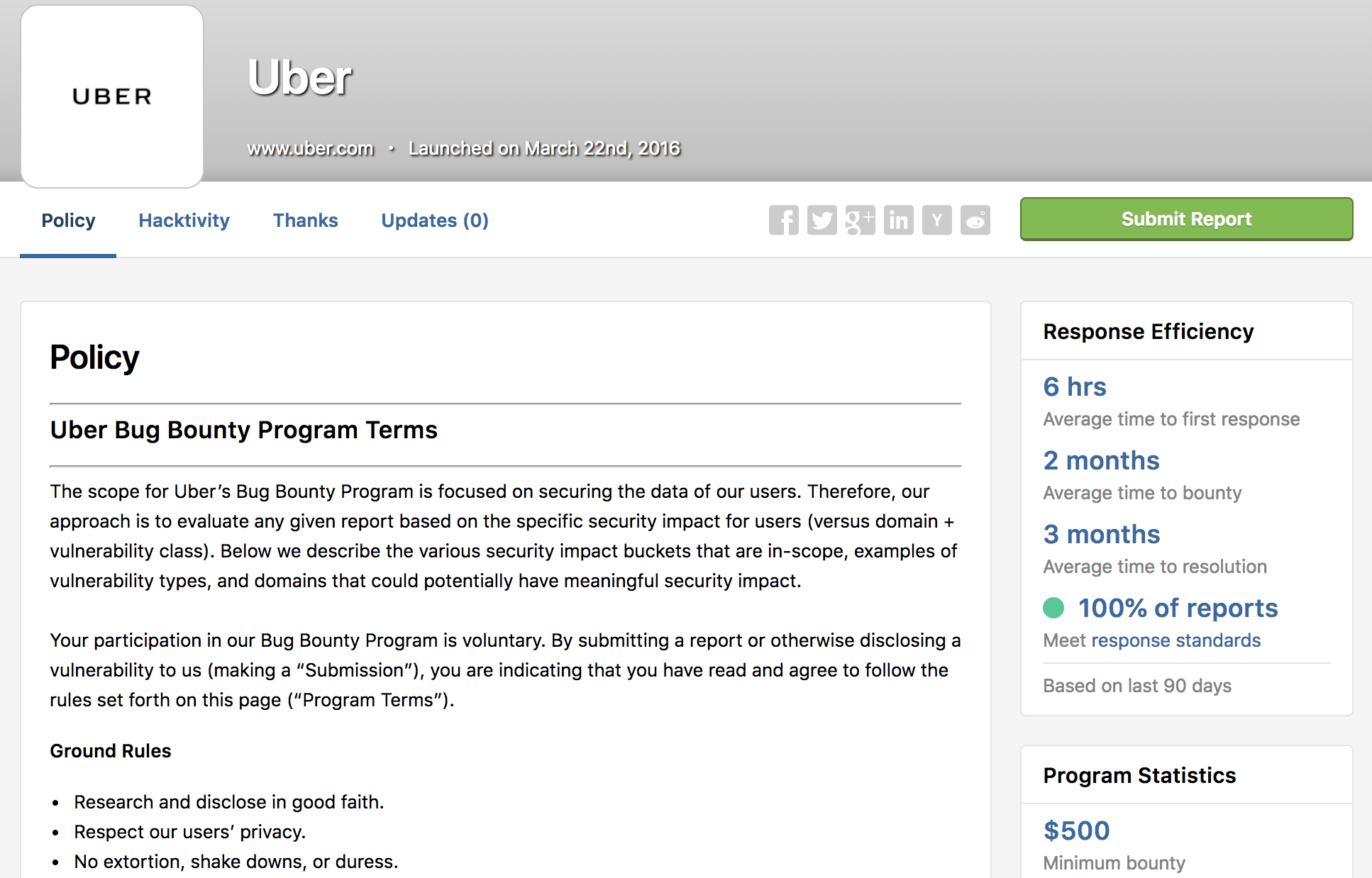
Bug Bounty Programs
- Companies say "hack me, but follow this rules"
- BB platforms mediate between the hackers and companies
- Pays lots of $$$
- HackerOne
- BugCrowd
- Cobalt.io
- Synack
- OpenBugBounty.org
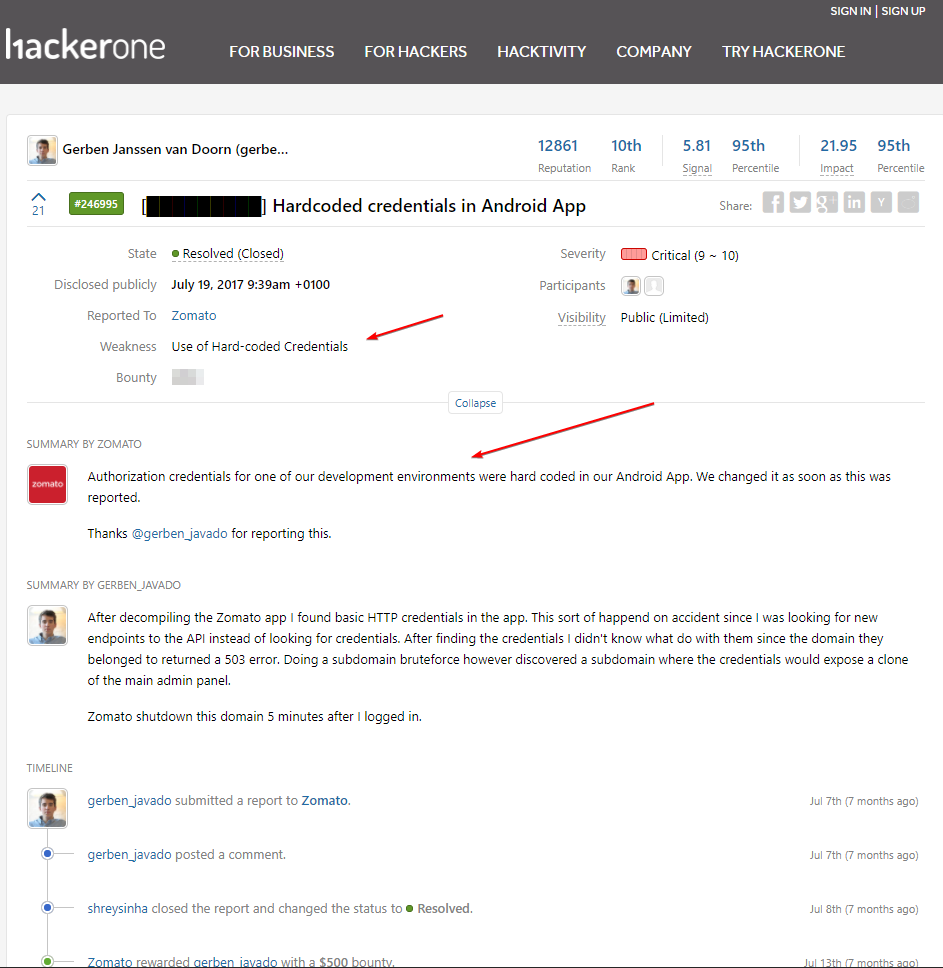
500$
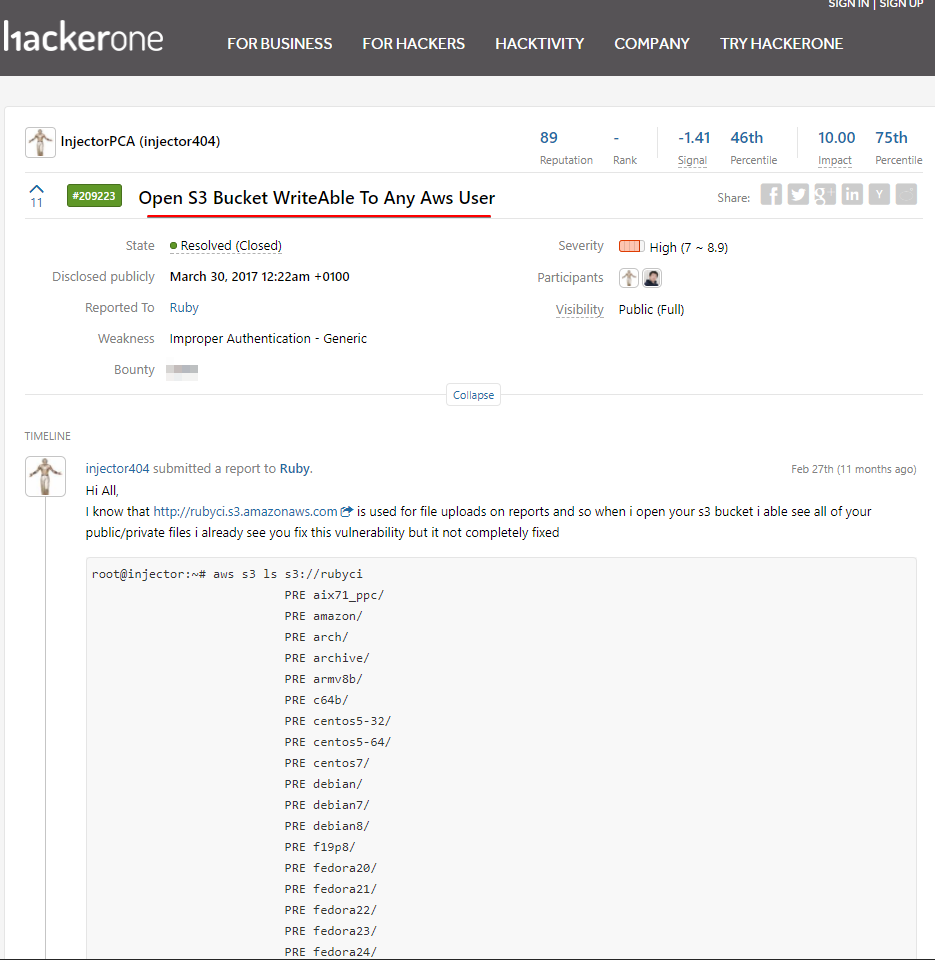
500$
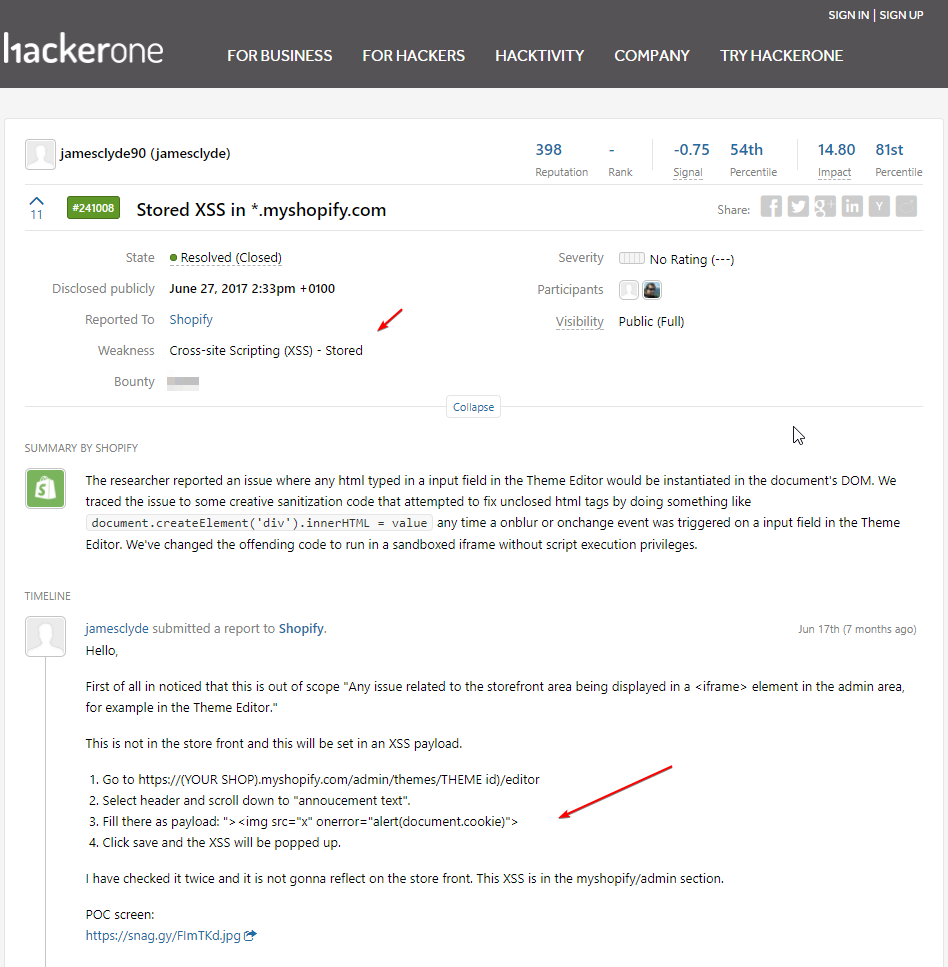
500$
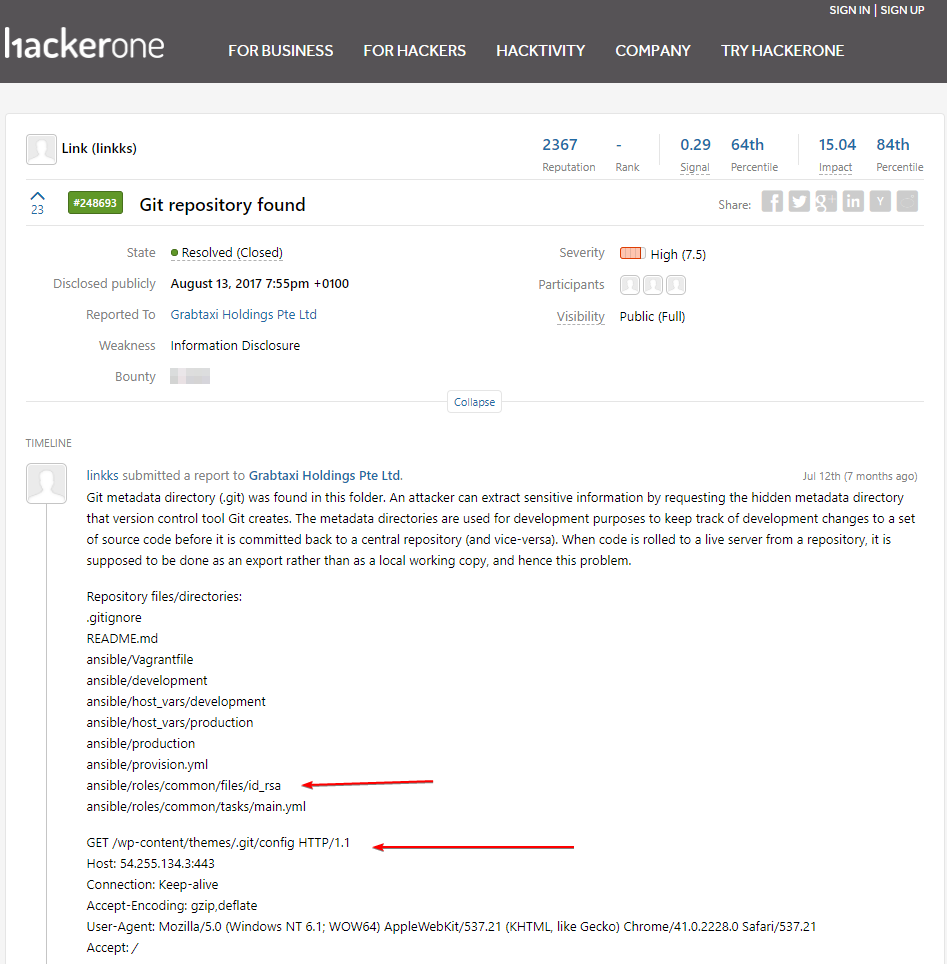
1000$
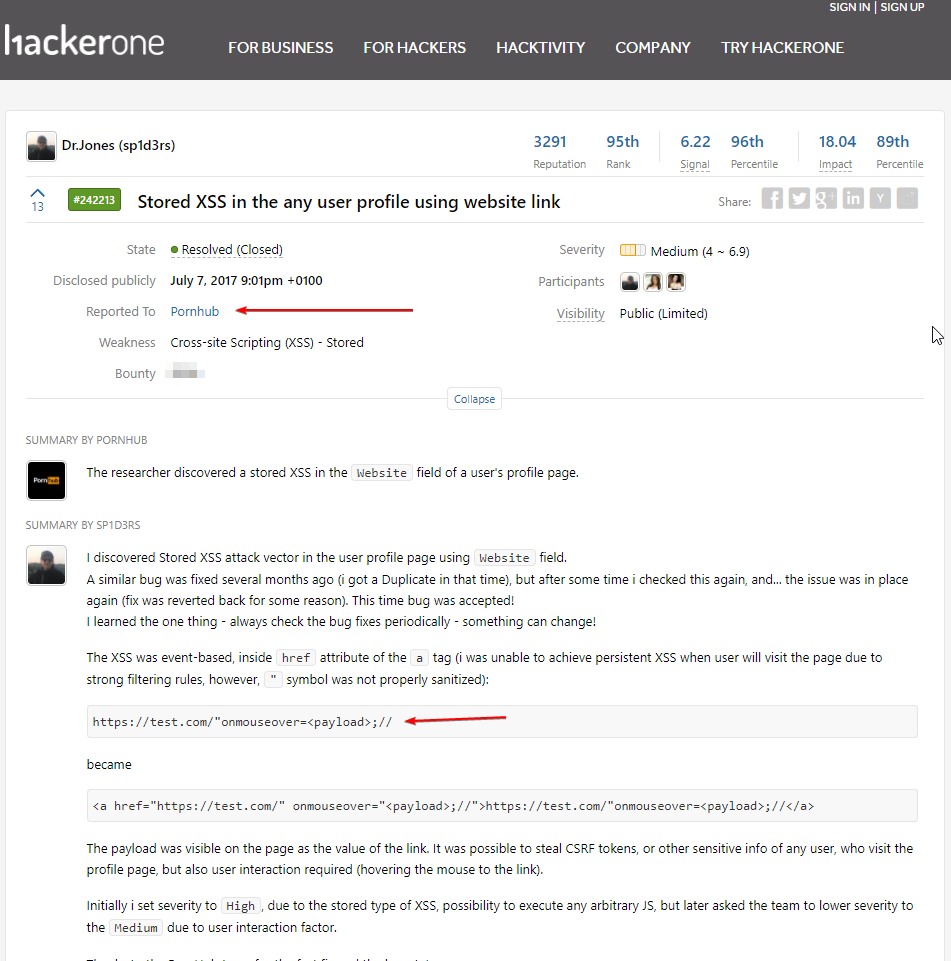
500$
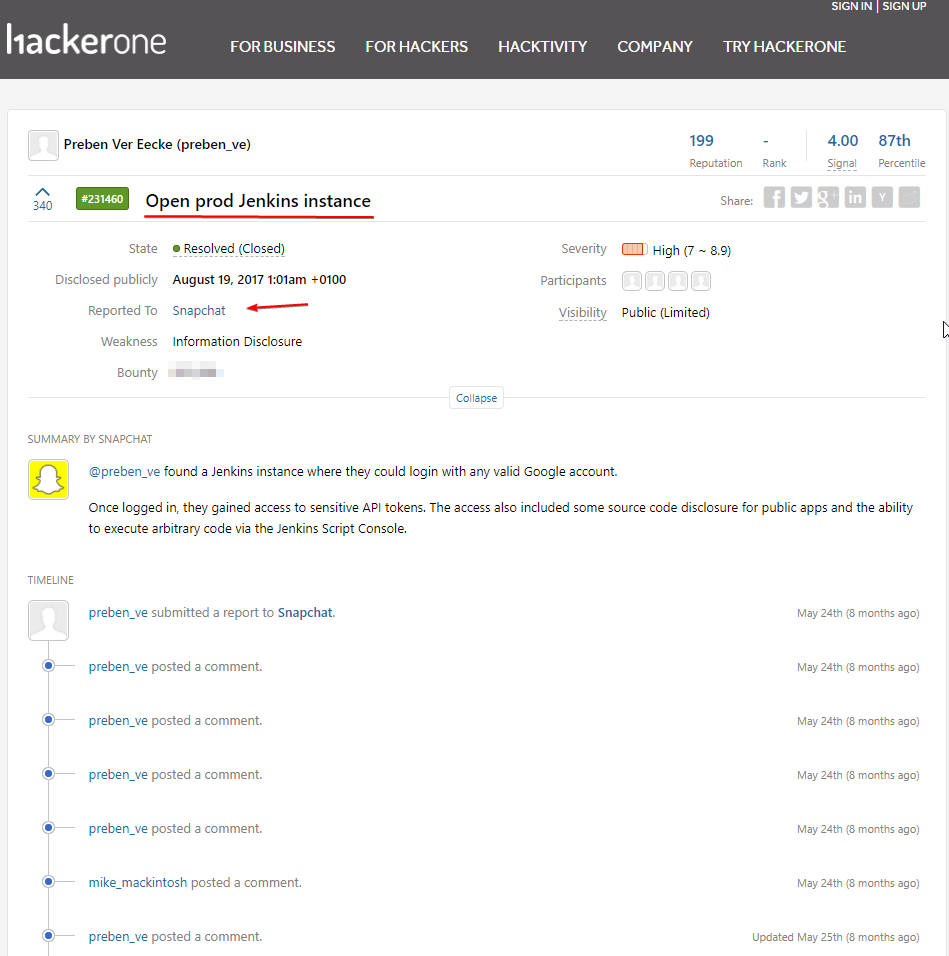
15000$
CTF vs BBP

Getting into Security
- Get social
- OWASP local chapter
- Local security meetups
- Local hackspaces
meetup.com/0xOPOSEC
Being Mindful
- Secure coding
- Get a mentor
- Be curious!
-
CSIRT (Computer Security Incident Response Team)
-
CERT (Computer Emergency Response Team)
-
Questions?