an improvement on
jtag security
using
pluggable authentication module
Mylene A. King
COE215 DESIGN OF DIGITAL SYSTEMS AND COMPUTERS
MAPUA INSTITUTE OF TECHNOLOGY
OBjectives
- To understand security risk on JTAG
- Examine prior works on improving the JTAG security
- Analyze impact on integrating PAM
- Identify advantages and disadvantage of using PAM
- Conclusion and recommendation for future works
introduction
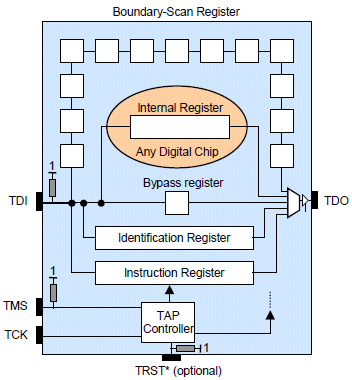
JTAG has been widely adopted by manufacturing company because of its well-known standard mechanism for in-circuit board testing. Although it provides high controllability and observability, it also poses great security challenges.
Source: Image from "Boundary Scan Tutorial" by Dr. Ben Bennetts
Source: Kurt Rosenfeld and Ramesh Karri , Attack and Defenses for JTAG
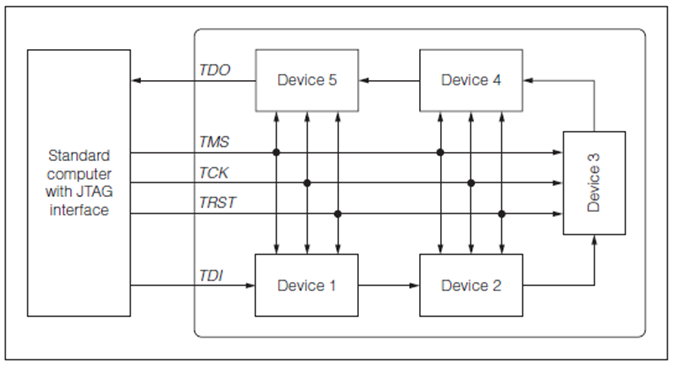
Typical Deployment of JTAG is a chain of several devices in PCB
SEcurity risks
Source: Kurt Rosenfeld and Ramesh Karri , Attack and Defenses for JTAG
Conceptual Security Model
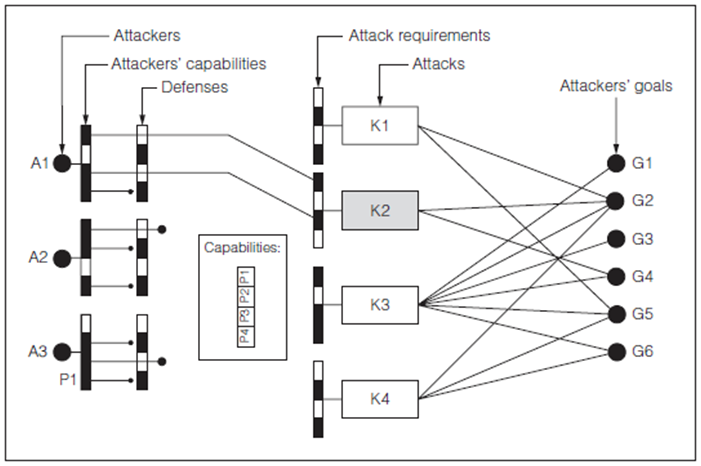
types of attacks
- Sniff secret data
- Read-out secret
- Obtain test vectors and responses
- Modify state of authentic part
- Return false responses to test
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
The attacker obtains secret data by sniffing the JTAG path
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
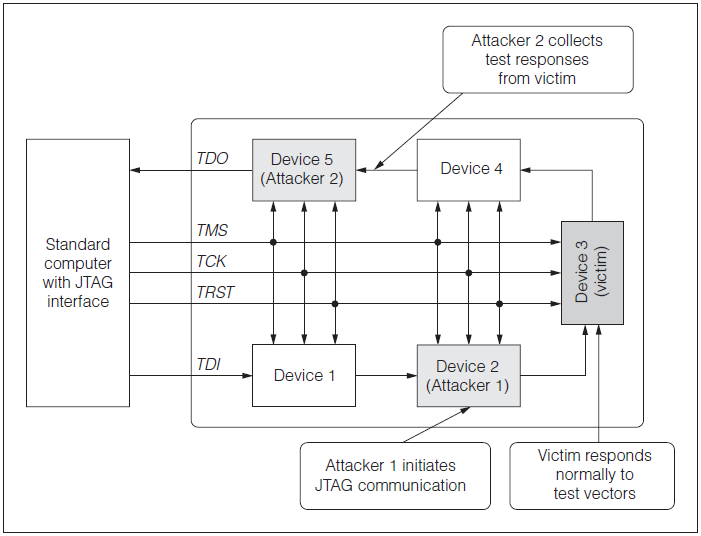
In a read-out attack, the attacker obtains an embedded secret by forcing test vectors onto the JTAG lines
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
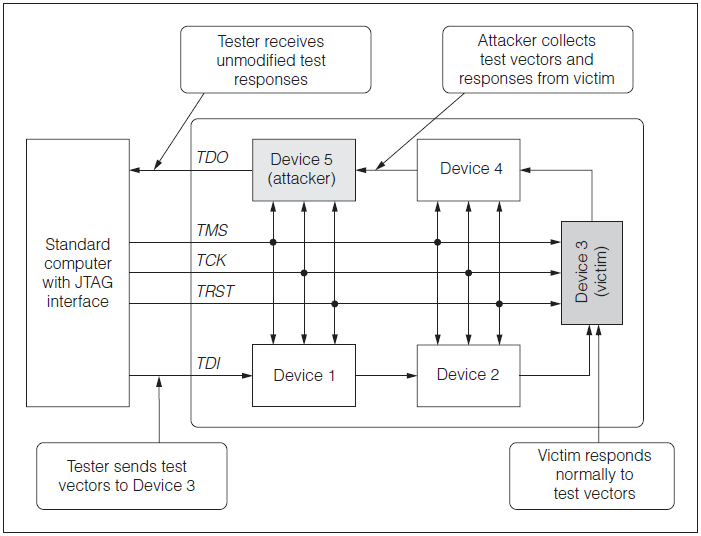
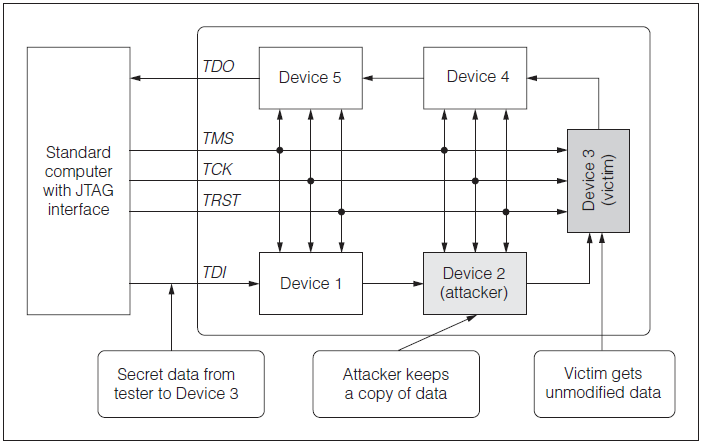
In a test vector collection attack, which can be passive, the attacker obtains a copy of the test vectors and normal responses of a chip in the JTAG chain.
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
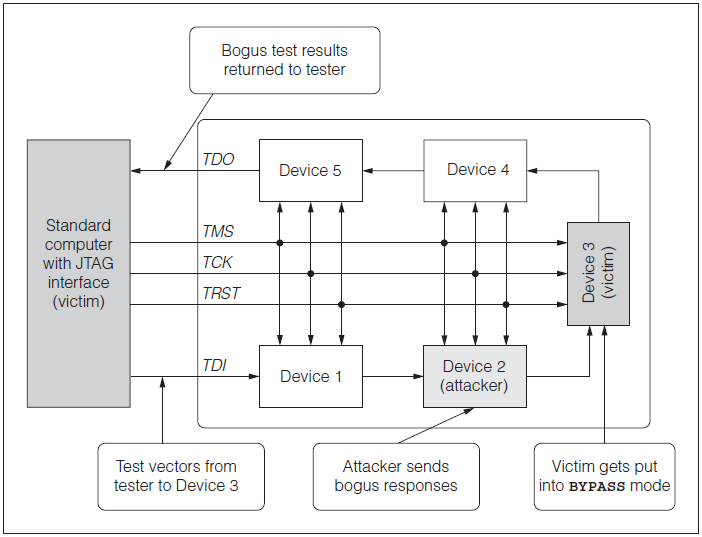
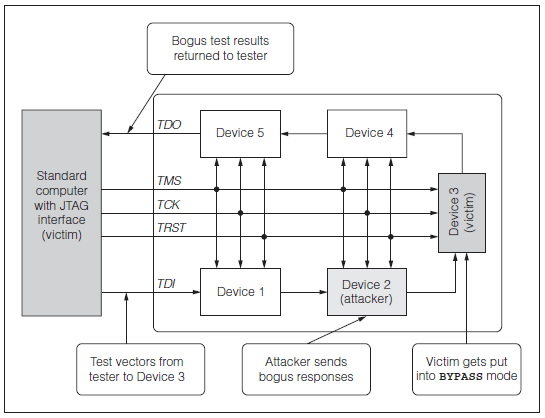
The attacker can intercept test vectors that are sent to another chip, and can send false responses to the tester.
Source: Attack and Defenses for JTAG by Kurt Rosenfeld and Ramesh Karri
Returns false responses to test
prior work on jtag security
- Rosenfeld and Karri, proposed types of defenses on different types of attacks.
- Authentication and key establishment scheme
- Secure JTAG communication protocol
-
Star topology instead of daisy chain
- Results to increase PCB complexity and cost
prior work on jtag security (cont.)
- Yang et al.3 have also proposed a DFT architecture that allows testing crypto hardware with high fault coverage yet without exposing hardcoded crypto keys to leakage.
- Novak and Biasizzo4 proposed a locking mechanism for JTAG with negligible added cost by adding lock and key registers.
Xilinx Security Solutions
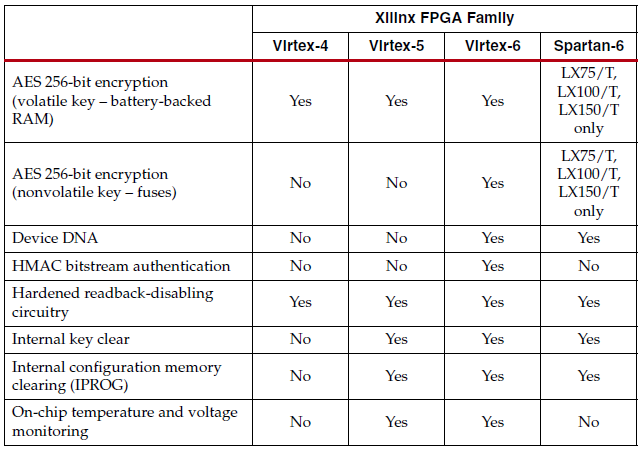
Source: Steven McNeil, Solving Today’s Design Security Concerns, 2012
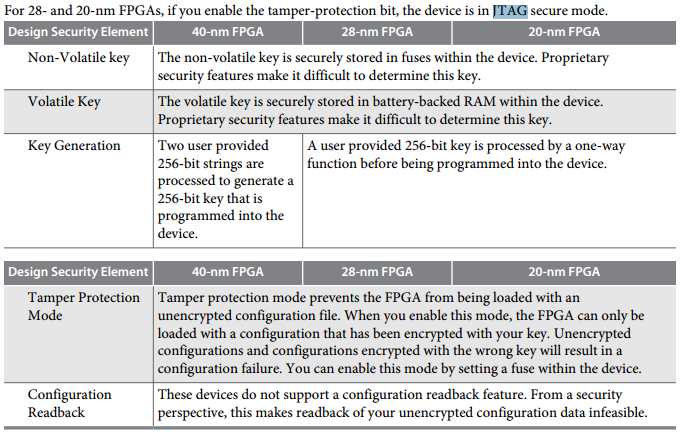
ATMEL DESIGN SECURITY APPROACH
Source: Using the Design Security Features in Altera FPGAs, 2015
what is security?
General concept of security
- Nothing is ever 100% secure
- Given enough time, resources, and motivation, an attacker can break any system
- Security must be constantly updated
- expect new way of authentication in the future
- Strength of cryptography relies on secrecy of key, not the algorithm
- It is not safe to assume that large key size will guarantee security
- Security is different depending on the needs
Source: Joe Grand, Practical Secure Hardware Design for Embedded Systems, 2004
statement of the problem
- Each of those solutions only focuses on the security mechanism, implementation of the hardware part security.
- Without thinking about how the user can access such a solution in an effective manner in terms of ease of use, administration, and practicality.
proposed scheme
- The proposed solution will provide benefits such as
- ease of use/administration
- scalability
- maintainability
- The proposed scheme will use the idea of Pluggable Authentication Module (PAM)
pluggable authentication module (PAM) IMPLEMENTATION
PAM is a framework of authentication module mostly used in Linux operating system and can also be implemented to embedded system projects.
PAM is a modular and flexible authentication management layer that sits between Linux applications and the native underlying authentication system.
PAM can be implemented with various applications without having to recompile the application when PAM configuration is changed.
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
4 tasks of authentication
- Account Management
- Authentication Management
- Password Management
- Session Management
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
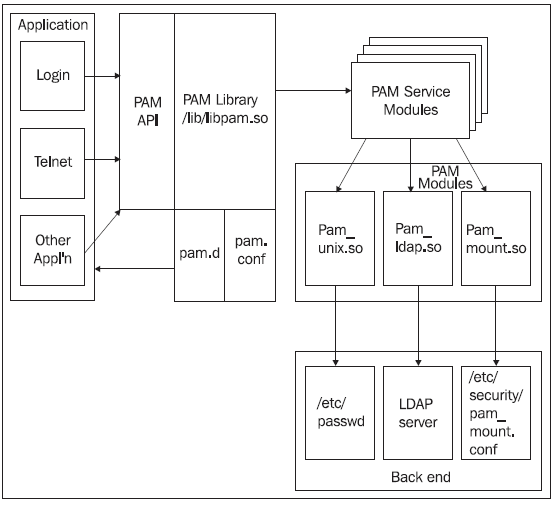
PAM Framework Architecture
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
CONTROL FLAGS
- a module can either return OK (success) or not-OK (failure)
- can change the low and how decisions are made
- List of control flags:
- Requisite
- Required
- Sufficient
- Optional
Source: Kenneth Geisshirt, Pluggable Authentication Modules, 2007
stacking
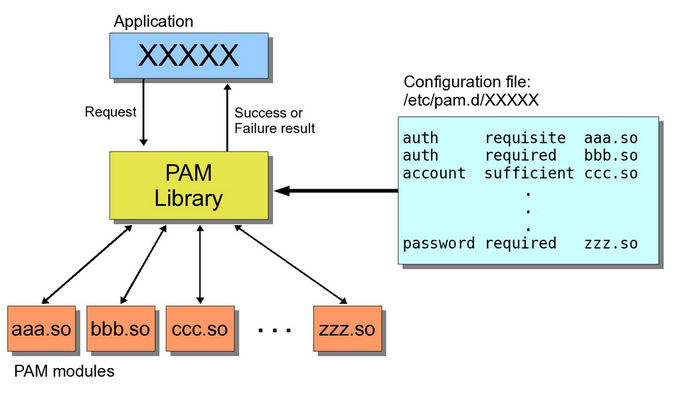
- One of the most useful concepts of PAM is the stacking of modules.
- For each management group you can define a set or a stack of modules, which are used in turn.
-
When an application calls the PAM library function, for example to authenticate, the PAM runtime will call each authentication function in each module
- one at a time like cards from stack.
-
When an application calls the PAM library function, for example to authenticate, the PAM runtime will call each authentication function in each module
Source: http://www.tuxradar.com/content/how-pam-works

proposed scheme - advantage
- PAM gives the flexibility to easily switch from one auth to another
- PAM enables modular approach in setting up authentication
- Increase security using PAM stackable authentication method
proposed pam architecture w/ jtag (HLD)
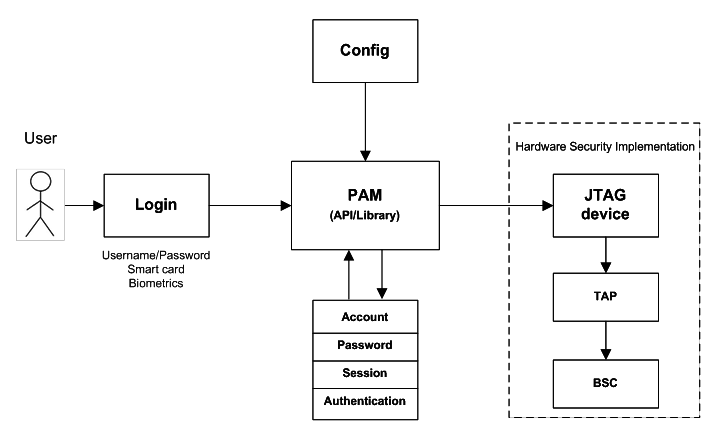
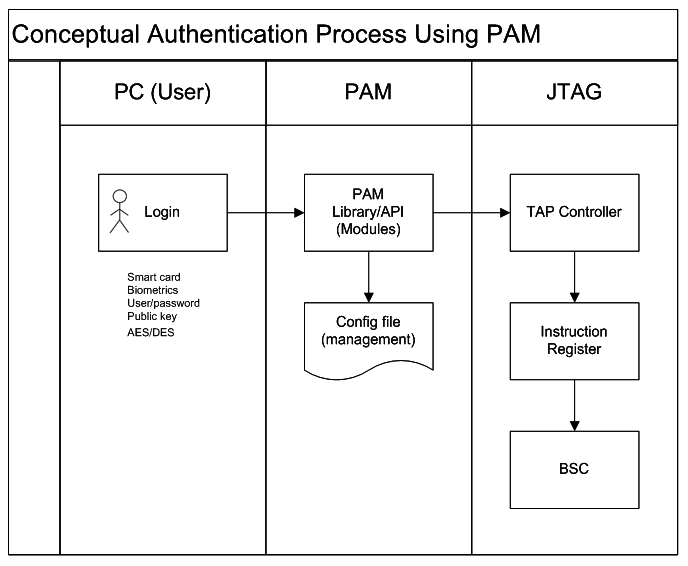
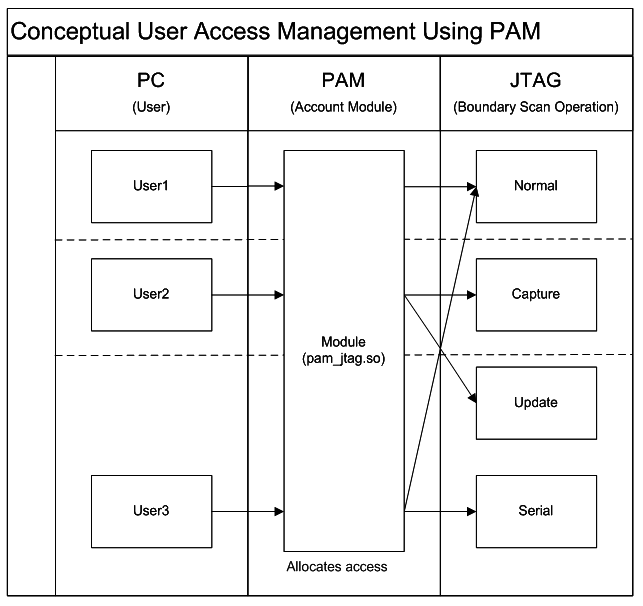
proposed scheme - disadvantage
- Dedicated authentication module is needed to be develop
- PAM maybe difficult and costly to implement for hardware projects since it is originally designed for Linux systems
- The PAM framework is complex and not very forgiving when it comes to errors
- If wrongly configured, it can easily be compromised by crackers
conclusion
The idea of PAM can be used as a standard in design & implementation of SoC in the future.
As security evolves, so as the need for new authentication method. PAM provides the ease of changing authentication by using its modular functions.