SSl Termination in a hardware security module (HSM)
BRief history of cryptgraphy
Read Simon Singh's "The Code Book"
- 1500 BC - clay tablets in Mesopotamia encrypted a craftmans recipe for pottery
- Greeks and Romans both used ciphers e.g. Caesar Cipher
- Spartan military use a Skytala
- Arabs documented cryptanalysis (for breaking ciphers)
- WWII Enigma
Skytala

MODERN Cryptography 101
What is encryption? Encryption is a method for encoding data (plaintext) in a way that is not reversible (ciphertext) without being authorized to do so.Authorization is achieved by the sharing of a "key" used to unlock the encrypted message and turn it back into plaintext.
Various encryption algorithms exist in the public domain
There are two types of cryptography, Asymmetric (public/private key) and Symmetric Cryptography.
Asymmetric CRYPTOGRAPHY
Asymmetric cryptography is where different keys are used to encrypt and decrypt the data. A public key is used to encrypt data, where as a private key is used to decrypt the same data.
A person may share their public key so that anyone can send them encrypted data, but only they can decrypt it.
This method is employed in "hashing". This is where data is turned into a "signature" via a "one-way" hashing algorithm. This algorithm will always generate the same result when presented with the same data.
A person receiving data with a signature can use the signature to verify that the message has not been altered in transit.
An example of asymmetric cryptography is digital signature algorithms (such as ECDSA, Elliptic Curve Digital Signature Algorithm or MD5 (used to hash passwords in PostgreSQL database)
e.g. PGP email signatures (find an email from DD, it uses the SHA hashing algorithm to generate signatures)
Asymmetric Cryptography is also used to derive/exchange a shared key (e.g. Diffie-Hellman key exchange)
Symmetric Cryptography
Symmetric encryption is where the same key is used to encrypt and decrypt data. This requires keeping the key secret at all times, so the key must be shared in a secure way.
SSL uses this type of encryption for session traffic (more on this in a minute).
An example of symmetric key cryptography is the algorithm AES256, an encryption algorithm with a 256 bit key.
Symmetric Cryptography is much faster than Asymmetric Cryptography, but requires the pre-sharing of a private key in a secure way, this is a security vulnerability.
Shared Symmetric keys are usually derived using Asymmetric Cryptography such as Diffie-Hellman. This process is referred to as Key Exchange.
There are multiple types of encryption mechanisms available, such as block and stream ciphers, but these are outside the scope of this talk.
SSL? Whats dat?
Ssl vs tls
SSL (Secure Socket Layer) is the pre-decessor of TLS (Transport Layer Security). It is communication between a browser and a webserver over an encrypted tunnel.
It uses "x.509 certificates" (containing pre-shared keys and prime numbers signed by a Root CA (certificate authority) using a digital signature algorithm), so use Asymmetric Cryptography in order to establish session keys, at which point the connection uses Symmetric encryption algorithms to encrypt session traffic.
Your browser contains the public keys of the Root CAs around the world in order to verify the SSL certificates signatures.
Your browser verifies the signature of the certificate before exchanging the sessions keys with the server.
If the signature verification fails, you get a warning message in the browser asking you whether you want to continue (add security exception)
When a Root CA is breached, such as DigiNotar in Holland, hackers can generate SSL certificates that appear to be valid, for malicious websites

DigiNotar should have run it's SSL cert generation tools inside an HSM, not just generate keys using an HSM
What is an HSM?
- Secure execution environment for cryptoprocessing
- Contains Crypo-Acceleration hardware
- Either PCIe or rack mounted server
- Cryptographic material only exists "in the clear" within the secure hardware boundary (FIPs Boundary)
- The FIPs boundary is the part of the HSM that is approved by NIST (US government approval body, part of the NSA)
- Requirements exist for devices to be compliant with FIPs at various levels
- Rack mounted HSM's are capable of 7000+ crypto operations per second
A few nice piccies
Rack mounted HSM server - nShield Connect

70% of the worlds chip-and-pin transactions go through one of these (or something similar - Payment HSM)
PCI card
This PCIe card can be mounted within a server
hsm use cases
- Banks use HSMs for chip-and-pin verification
- Certificate Authority root CA private key storage
- Database decryption key storage
- Key generation
- only need to export the public key in the clear, private key can be encrypted then exported for storage
- Time stamping
- Your internet banking SSL connection terminates inside an HSM
SSL Termination
- Session keys can be generated within the FIPs boundary of an HSM
- HSM's can run a SSL webserver within it's secure boundary
- An HSM can exist on a boundary to a data centre, decrypting SSL traffic before passing the data to an app server inside the data centre
- The app server should only be accessible from within the data centre or only perform operations with non-sensitive data.
- Business logic can be run inside some HSMs if custom operations on sensitive-data is needed
- The SSL certificate can be stored and served from within the HSM
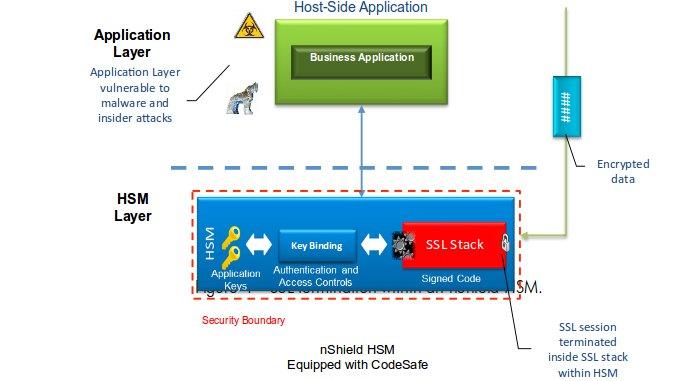
This removes one attack vector from your architecture
HSM API
HSMs expose an API to allow the development of applications that need cryptographic processing
Applications have to be "enrolled" in order to talk to an HSM
During enrolment, an application will be given a public key generated as part of a key pair generation inside the HSM which it will use to communicate with the HSM
A web application that talks to an SSL end point within an HSM is such an application
Using the secure execution environment of an HSM means sensitive information such as credit card details never have to exist in the clear.
Sensitive data can be stored encrypted in a database and only decrypted inside the HSM when they need to be used.
summary
- HSMs move sensitive code inside a secure boundary
- HSMs have various use cases including SSL termination
- HSMs should be used as part of a secure architecture i.e. moving application logic into a data centre communicating via an HSM
- HSMs perform high numbers of crypto operations per second
- HSM API can be used to extend applications inside a secure boundary
- Amazon AWS now offers cloud based HSMs


