Networking
Data-Link Layer
Data-Link (Layer 2)
- Groups Data into frames (layer 3 - packets)
- Responsible for point-to-point communications
- Each point is called a 'node.' Nodes aren't always computers. They can be Fitbits, routers, light switches, and more.
Layer 2 Protocols
- Ethernet (wired/WiFi)
- USB (Universal Serial Bus)
- Bluetooth
- CAN-Bus (Cars and industrial equipment)
- I2C (Communication in-circuit)
Data-Link Sublayers
- Media Access Control (MAC)
- Logical Link Control (LLC - not used much now, allowed TCP/IP to share the line with other protocols)
Network Topology

Point-to-Point
Network Topology
Line

Network Topology
Bus

Network Topology
Ring

Network Topology
Star

Network Topology
Star - Reality

Network Topology
Mesh (one hop)

Network Topology
Fully Connected

Media Access Control
- Carrier Sense Multiple Access with Collision Detection
- CSMA/CD
- Older wired Ethernet works this way.
- Wi-Fi works this way
- Listen, see if anyone is talking. If no one is, talk.
- Detect if another node started talking. If so, stop, wait random time, try again.
- Like normal talking.
Media Access Control
- Early in networking, engineers said "Let people talk when they want to? That's crazy! Must be more formal."
- Token-Ring competed with Ethernet
- A 'token' was passed around a ring topology, and only the node with the token could talk.
- Like a 'speaking stick'
- Good in 'real-time' systems, as Ethernet could have unpredictable delays.
Media Access Control
- Avoiding collisions with Ethernet?
- In wired communications, use a 'star' topology. No shared media, no collisions.
Data-Link Protocols
- A protocol is an exact agreement on how we pass data
- Anyone following the protocol should be able to communicate with anyone else following that same protocol.
- If a lot of people use a protocol, it is called a standard protocol, or just standard.
- Opens competition. For example, any vendor can make devices that hook up to WiFi.
Data-Link Protocols
- Wired Networks - Ethernet standards grouped under IEEE 802.3
- WiFi - Ethernet standards grouped under IEEE 802.11
- Vehicles and Industrial Equipment - CAN-bus standards administered by ISO
- USB connections: Multiple companies came together. 1.0, 2.0, 3.0, etc.
- Bluetooth: Started as IEEE, now multiple companies work together.
Wired Ethernet
- Current Standard is IEEE 802.ab that runs at 1 Gbit per second, backwards compatible.
- Divide by 8 to get gigabyte per second = 125 MByte/sec
- Gb = Gigabit / GB = Gigabyte
- There a required gap between frames, preamble, plus overhead = 118 MByte/second
- Newer standard is 802.3ae Fast Ethernet at 10Gb/second.
- Older standard is 100 Mb/s = 802.3u Fast Ethernet
- Note - Not all wired is Ethernet!
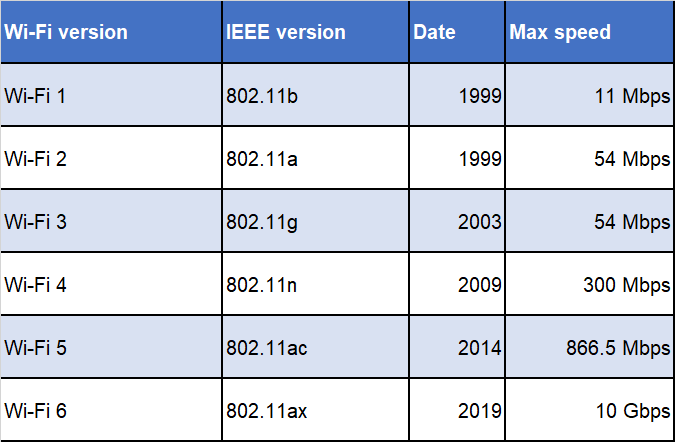
Wi-Fi Standards
- Original standard was 802.11
- Next ones added letters. Like 802.11b.
- Got confusing with all the letters. Starting in 2018, new standard that is consumer-friendly.
Wi-Fi Standards
Wireless
What Kind of WiFi am I Running?
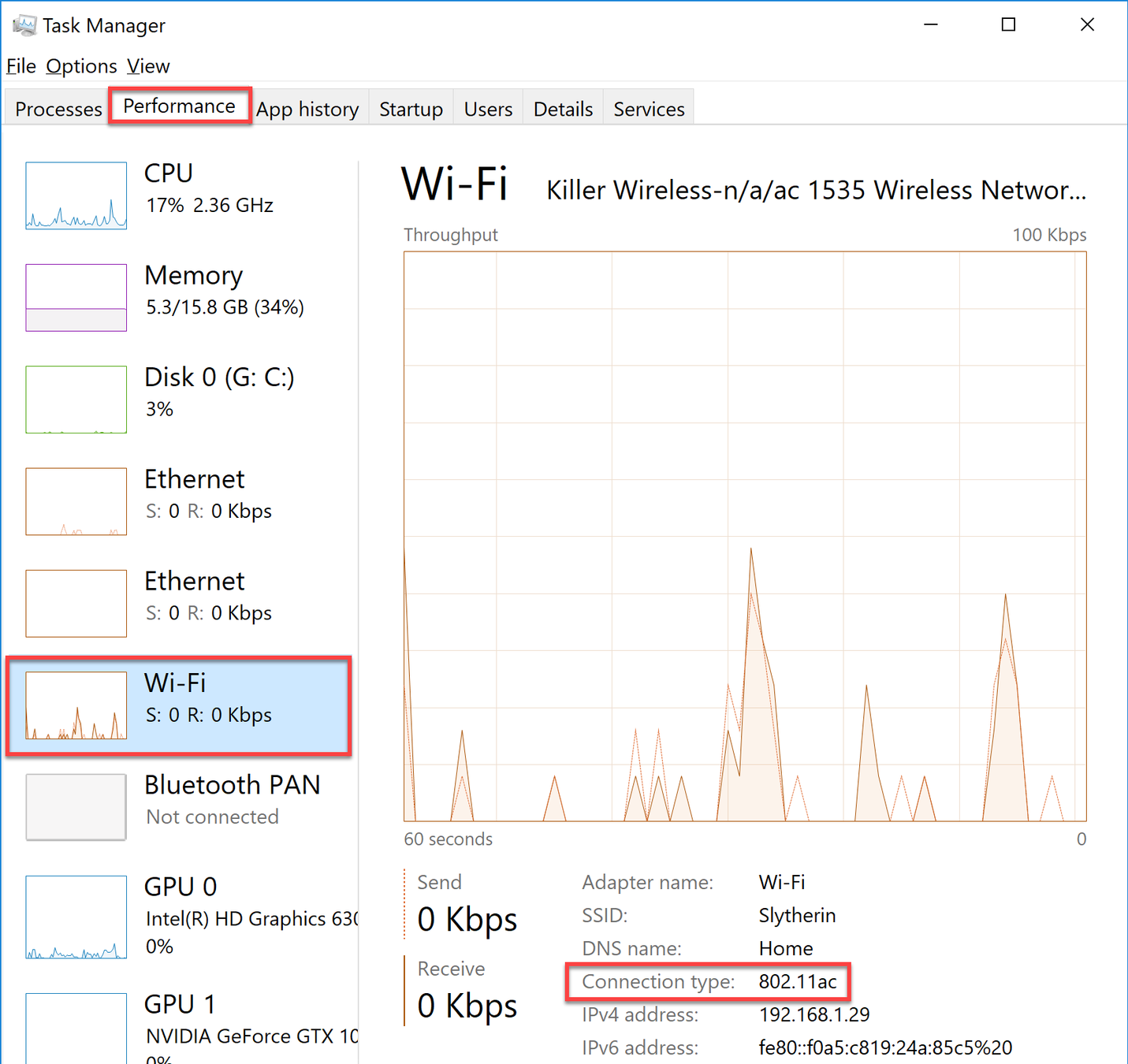
Service Set Identifier (SSID)
- WSID is the name when you try to connect to Wi-Fi
- Sending out the SSID is called a 'broadcast'
- You can turn this off. People can still connect if they know the name. A bit more secure, but less convenient.
Wireless Security
- None. Completely unencrypted. Anyone can see all traffic, and anyone can connect. Open access.
- Wired Equivalent Privacy (WEP) - Original 'secure' protocol. Now has known vulnerabilities. Don't use this.
- Wi-Fi Protected Access (WPA) - Outdated. Don't use.
- Wi-Fi Protected Access version 2 (WPA2) - Current standard. Use this.
- Wi-Fi Protected Access version 3 (WPA3) - Updated 2018 standard. Only use if you know all devices can support it.
Wireless Security - WPA2/3
- You can select one of two modes.
- PSK - Pre-shared key. You give someone a password and they can access the Internet. Great for coffee shops, small business.
- Quick set-up.
- Someone leaves you don't want to have access to the network? Reset everyone's key.
- Can't really tell who's connected.
- Enterprise - Everyone logs in with their own user id and password.
- Need a professional to set up and integrate with login system.
- You get logs of who's connected.
- One person leaves? Just disable that one account.
WPA Encryption Standards
- Temporal Key Integrity Protocol - TKIP
- Older, don' use.
- Advanced Encryption Standard - AES
- Use this.
WPA - Summary
- Small place - Use WPA2-PSK (AES)
- Medium or larger - Use WPA2-Enterprise (AES)
The Ethernet Frame
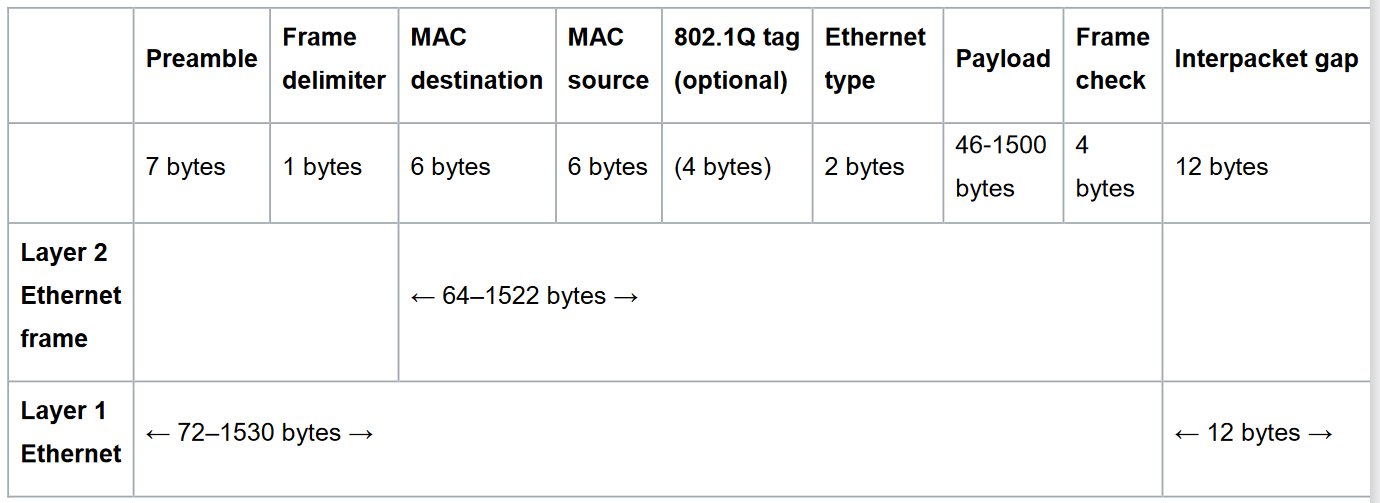
Preamble
- Alternating 1's and 0's
- 7 bytes
- 7 x 8 = 56 of 10101010101010...
- Allows Manchester Encoding to time the gap between each transition.
Frame Delimiter
- One byte
- Ends with two ones in a row
10101010 10101010 10101010 10101010 10101010 10101010 10101010 10101011
Preamble
Delimiter