Trustable oracles towards trustable blockchains
Pedro Duarte da Costa
Supervisor:
Filipe Figueiredo Correia
Second Supervisor:
Hugo Sereno Ferreira
pedro.duartecosta@fe.up.pt


16 July 2019
Master in Informatics and Computing Engineering
Blockchain
Smart Contracts
Shared distributed ledger
Strong consistency guarantees
Deterministic
Blockchain applications
Automated and decentralized contracts
The terms are written in code
2
The smart contract connectivity problem
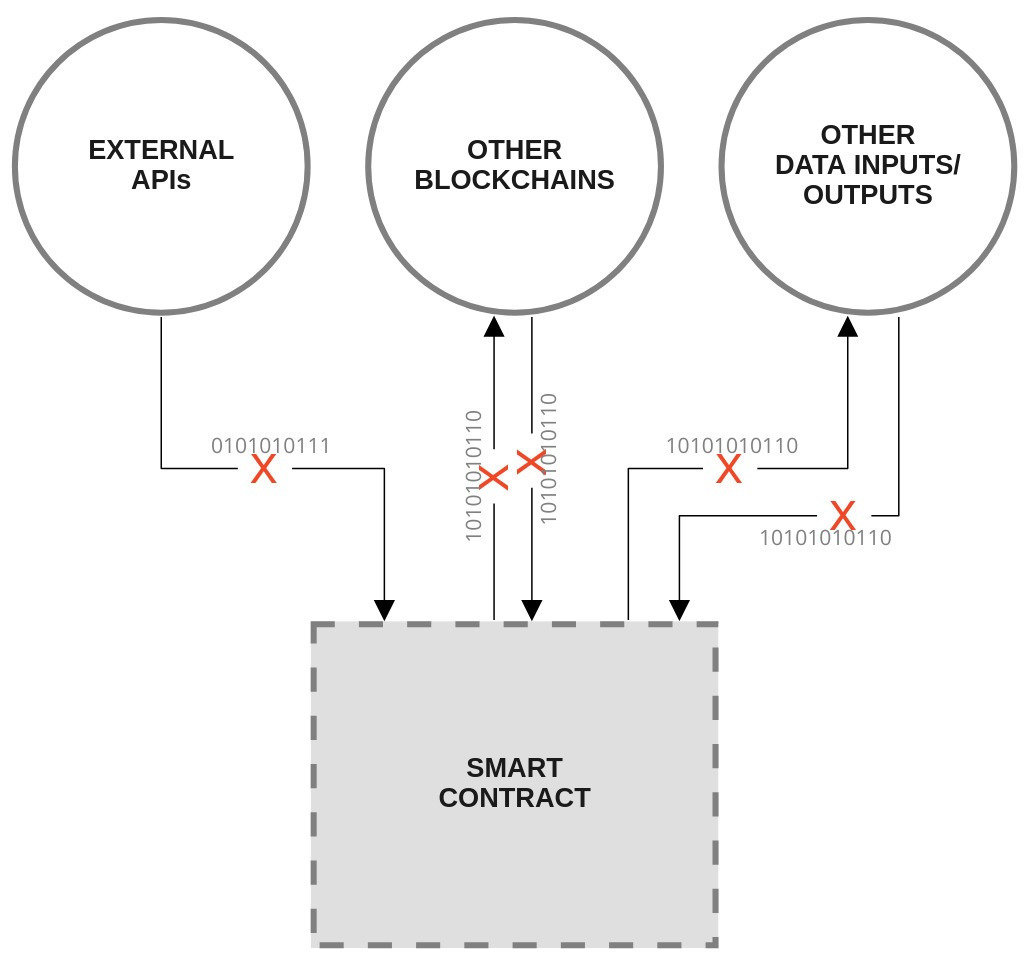
The blockchain is deterministic. Once a transaction is validated we can be sure that it will remain unchanged.
But the internet is non-deterministic, thus contracts cannot directly query the internet.
3
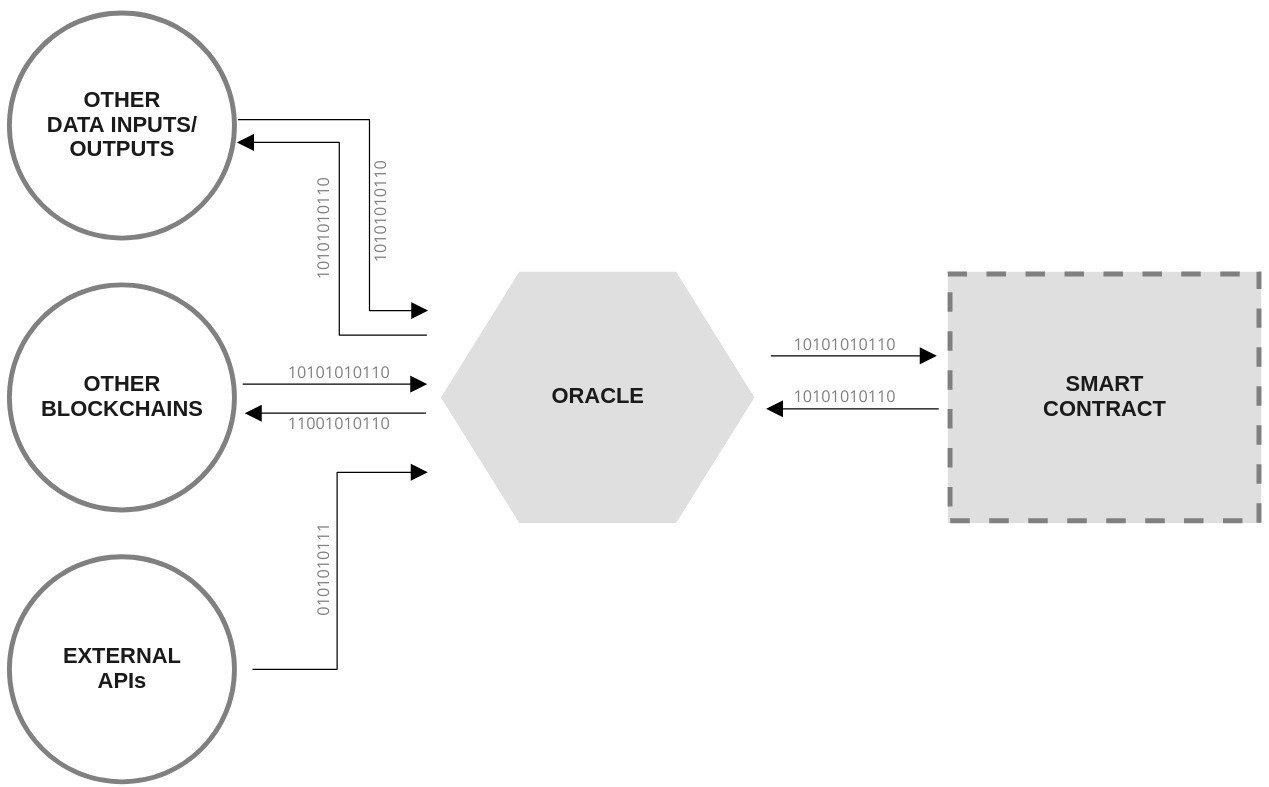
Oracles
4
Problem
Trusting oracles to be reliable and honest.
5
Systematic Literature Review
RQ1: What kind of blockchain oracles have been proposed?
RQ2: What are the research trends on blockchain oracles?
6
(("blockchain" OR "block chain" OR "block-chain")
AND
("oracles" OR "oracle" OR "middle-ware" OR "middleware" OR "middle ware" OR "datafeed" OR "data feed" OR "data-feed"))Search query
Systematic Literature Review
7
Findings
- Town Crier [ZCC+16] - Utilizes trusted hardware to serve source authenticated.
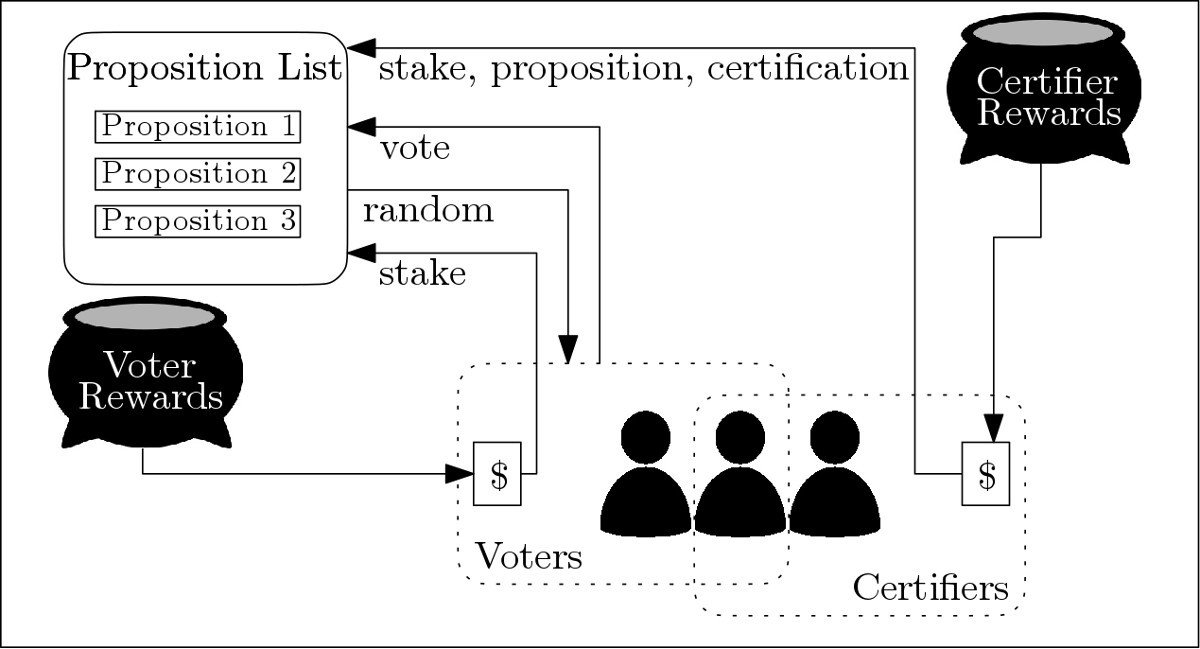
- Astrae [ABV+18] - Decentralized incentive-based network with submitters, voters and certifiers
- Gilroy Gordon [Gor17] - Protocol for sensor data authenticity and integrity in a IoT network
- Francisco Monroy [Mon18] - Gambling protocol based on incentives using a pool of 7 oracles.
- J. Eberhardt [EH18] - Proposes a systematic classification of off-chain computation oracles.
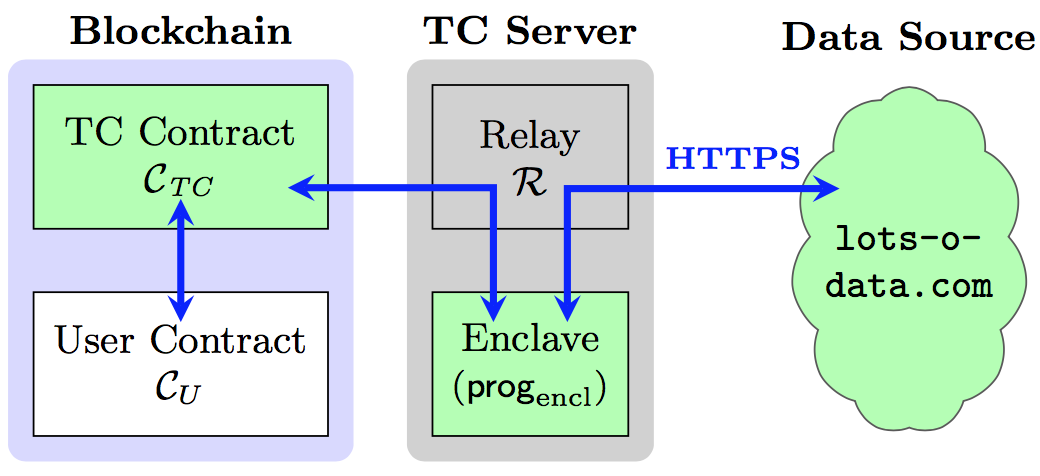
Town Crier Architecture
Aestrae Architecture
8
Commercial products and projects
- Oraclize.it (provable) [Ora18] - Utilizes authenticity proofs to guarantee oracle honesty
- ChanLink [EJN17], - Decentralized network of oracles to guarantee availability and query multiple data sources
- Schelling Coin [Vit14] - Decentralized network that rewards participants that submit answers closest to the median of all submitted
- TrueBit [TR17] - System of solvers and verifiers, monetarily incentivized to check on each other's answers.
9
RQ1: What kind of blockchain oracles have been proposed?
-
Software-based Oracles - Mostly use authenticity proofs to prove their honesty
-
Hardware-based Oracles - Similar to software-based oracles but take advantage of hardware trusted execution environments, such as Intel SGX
-
Consensus-based Oracles - Utilize a network of peers and to achieve consensus by wisdom-of-the-crowd solutions or incentive-based ones.
10
RQ2: What are the research trends on blockchain oracles?
-
Academic research focuses mostly on consensus-based or hardware-based solutions, ex: Astrae and Town Crier.
-
Whereas the industry researches and develops authenticity proofs levaring both software and hardware-solutions, ex: TLSNotary, Android Proof, Ledger Proof, etc.
11
Analysis of Authenticity Proofs
| Proof | Requires specific hardware | Can query the web | Future-proof | Currently used in production |
|---|---|---|---|---|
| TLSNotary | x | x | ||
| TLS-N | x | x | ||
| Ledger Proof | x | x | x | |
| Android Proof | x | x | x | x |
| Town Crier | x | x | x | x |
12
Systematization of Oracle Architectures
13
Desiderata
- Fast time-to-market
- Keeping trust standards
- Data-feed fault tolerance
- Data veracity
- Lower smart contract costs
- Lower oracle complexity
- Oracle decentralization
- Oracle ownership decentralization
14
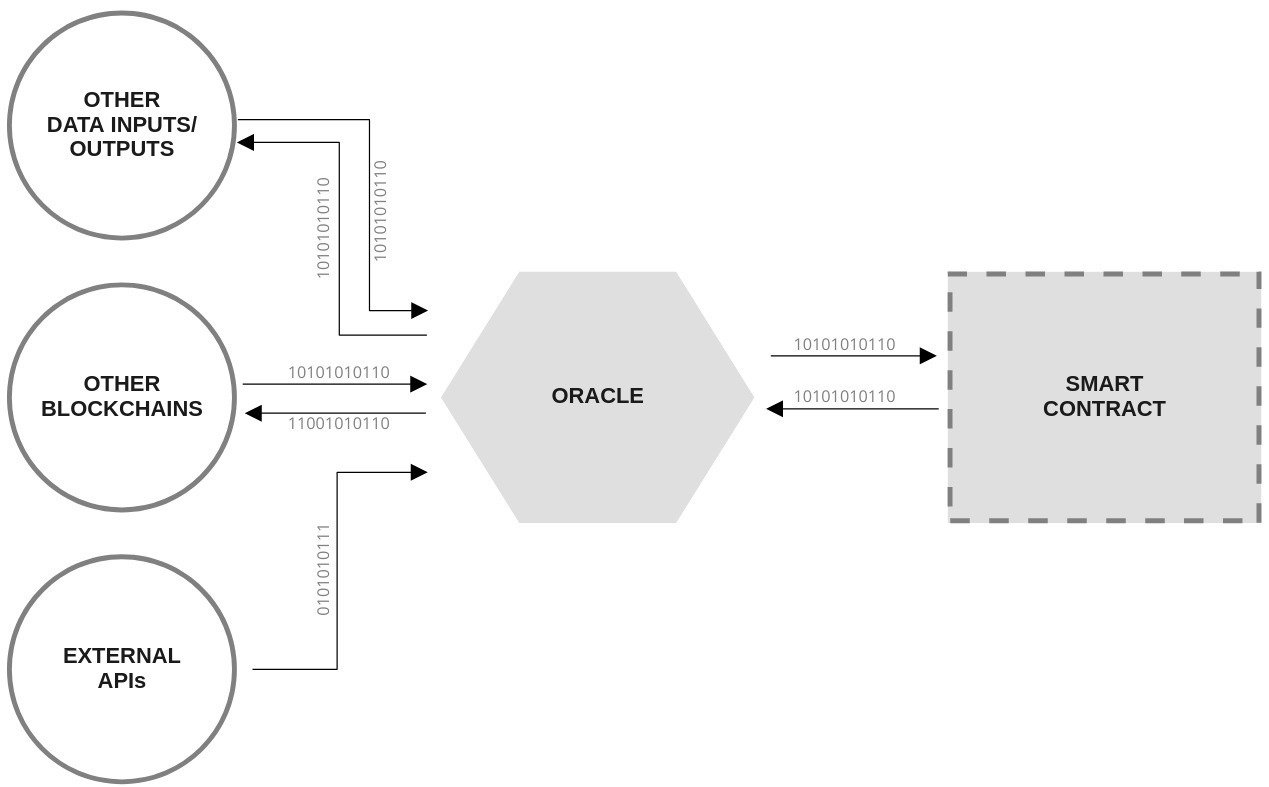
Analysing trust
Trusting oracle behavior
Trusting the data-feed
Off-chain
On-chain
15
Oracle as a Service w/ Single Data Feed
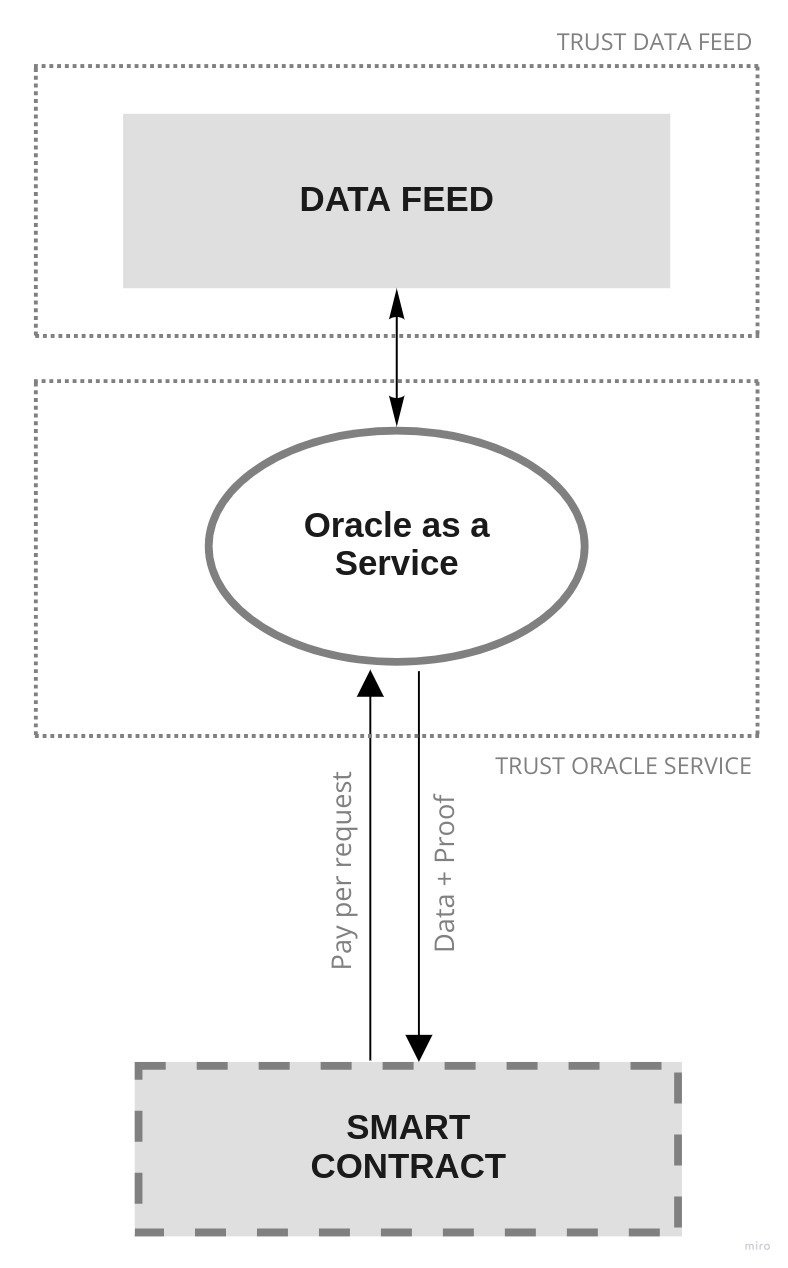
Forces
- Fast time-to-market
- Trust
Resulting context
- No data-feed availability guarantees
- Single source of data
- Centralized oracle node
- Single oracle owner
- Burden of checking proofs
Known uses
Oraclize.it (provable.xyz)
16
Oracle as a Service w/ Multiple Data Feeds
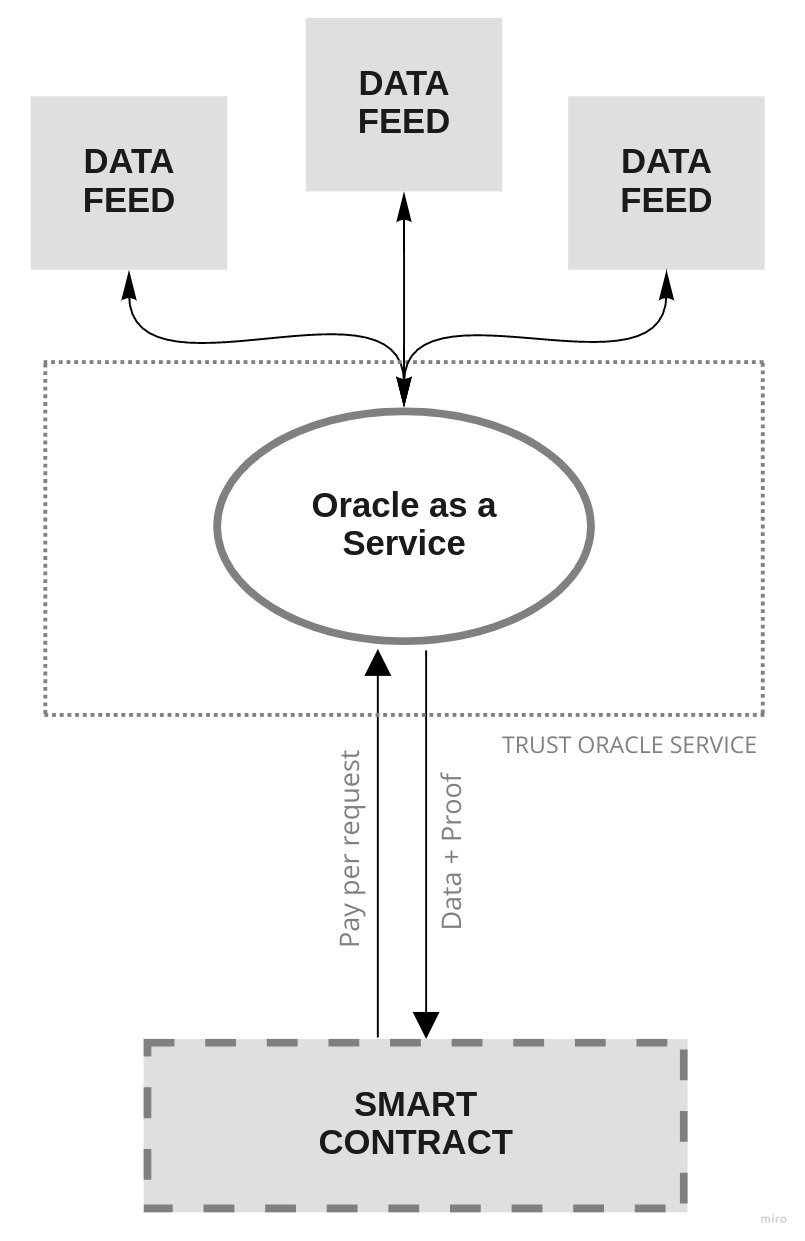
Forces
- Fast time-to-market
- Trust
- Data-feed increased availability
-
Multiple sources of truth
Resulting context
- Centralized oracle node
- Single oracle owner
- Burden of checking proofs
Known uses
ChainLink
17
Single-Party Self-Hosted Oracle
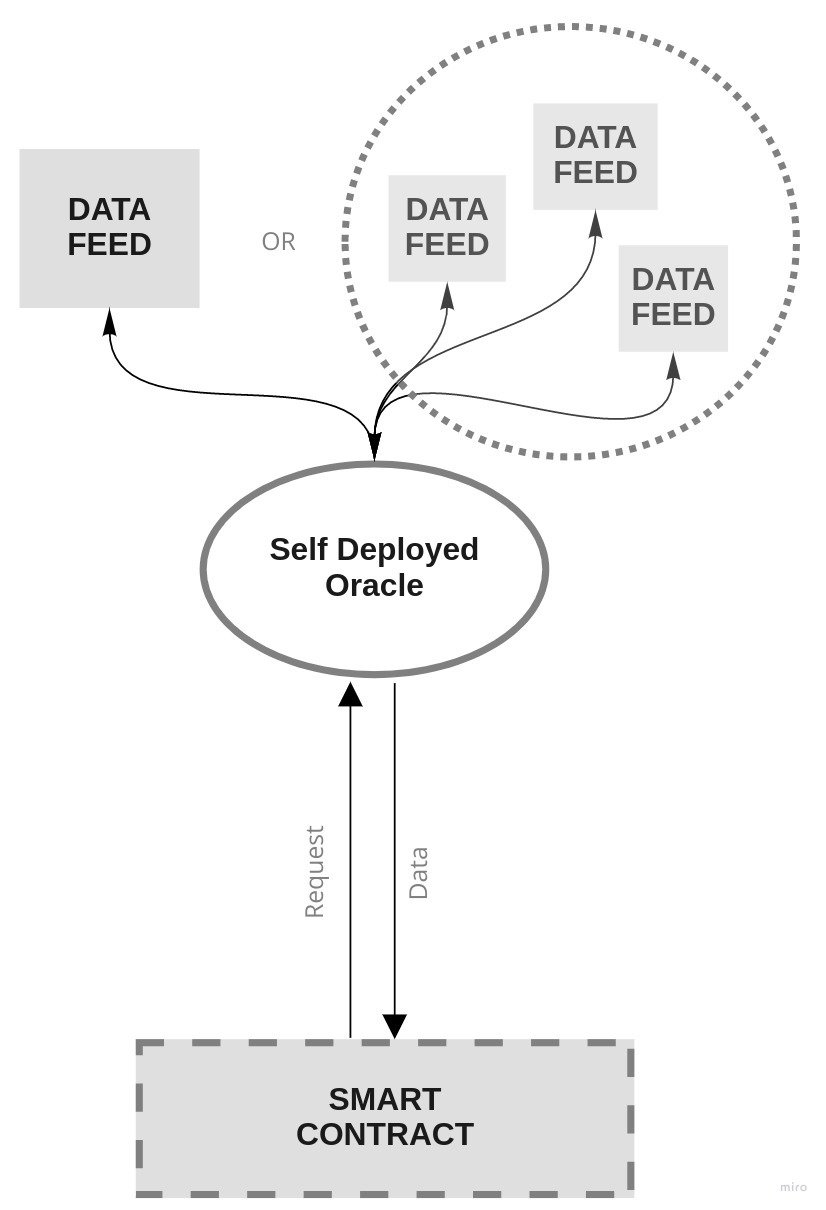
Forces
- Cost optimization
- Trust
- Data-feed increased availability
- Multiple sources of truth
Resulting context
- Centralized oracle node
- Single oracle owner
Known uses
gardeneroracle.io
18
Multi-Party Self Hosted Oracle

Forces
- Cost optimization (no proofs)
- Trust
- Data-feed increased availability
- Multiple sources of truth
- Decentralized oracle nodes
Resulting context
- Increased costs when using multiple nodes
Known uses
n/a
19
Summary
| OaaS w/SDF | OaaS w/MDF | SP-SHO | MP-SHO | |
|---|---|---|---|---|
| Fast time-to-market | X | X | ||
| Keeping trust standards | X | X | X | X |
| Data-feed fault tolerance | X | X | ||
| Data veracity | X | X | ||
| Lower smart contract costs | X | X | ||
| Lower oracle complexity | X | X | ||
| Oracle decentralization | X | |||
| Oracle ownership decentralization | X |
20
Implementing a Self-hosted Oracle
21
The Unlicense
A license with no conditions whatsoever which dedicates works to the public domain.
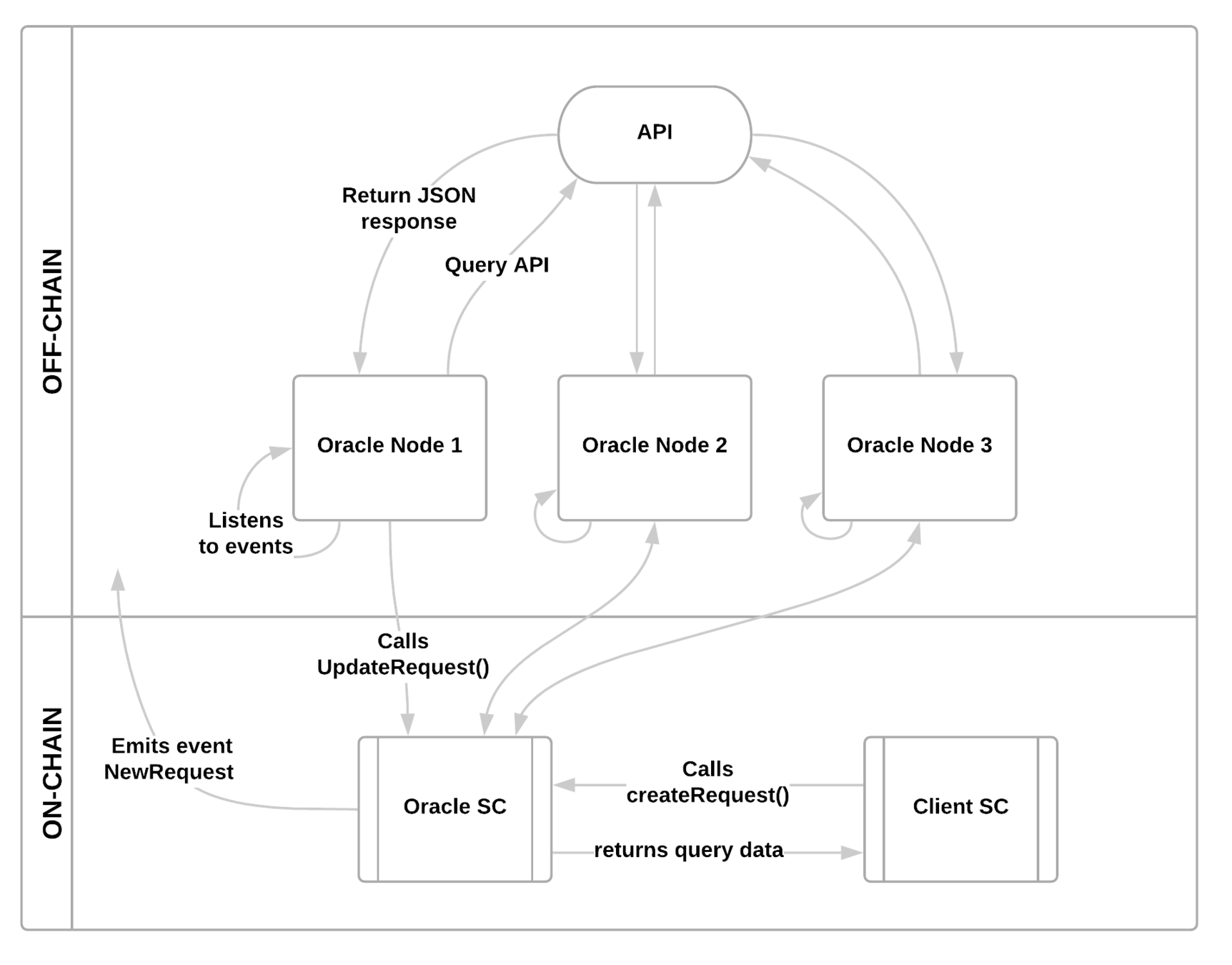
Architecture
22
contract Oracle {
Request[] requests; //list of requests made to the contract
uint currentId = 0; //increasing request id
uint minQuorum = 2; //minimum number of responses
uint totalOracleCount = 3; //hardcoded oracle count
// defines a general api request
struct Request {
uint id; //request id
string urlToQuery; //API url
string attributeToFetch; //json attribute (key)
string agreedValue; //value from key
mapping(uint => string) anwers; //answers provided by the oracles
mapping(address => uint) quorum; //oracles which will query the answer
//(1=oracle hasn't voted, 2=oracle has voted)
}
...
}On-chain oracle contract
23
function createRequest (
string memory _urlToQuery,
string memory _attributeToFetch
)
public {
uint length = requests.push(Request(currentId, _urlToQuery, _attributeToFetch, ""));
Request storage r = requests[length-1];
// Hardcoded oracle addresses
r.quorum[address(0x6c2339b46F41a06f09CA0051ddAD54D1e582bA77)] = 1;
r.quorum[address(0xb5346CF224c02186606e5f89EACC21eC25398077)] = 1;
r.quorum[address(0xa2997F1CA363D11a0a35bB1Ac0Ff7849bc13e914)] = 1;
// launch an event to be detected by oracle outside of blockchain
emit NewRequest (
currentId,
_urlToQuery,
_attributeToFetch
);
// increase request id
currentId++;
}Making a request
24
function updateRequest (
uint _id,
string memory _valueRetrieved
) public {
Request storage currRequest = requests[_id];
//check if oracle is in the list of trusted oracles
//and if the oracle hasn't voted yet
if(currRequest.quorum[address(msg.sender)] == 1){
currRequest.quorum[msg.sender] = 2; //marking that this address has voted
//iterate through "array" of answers until a position if free and save the retrieved value
uint tmpI = 0;
bool found = false;
while(!found) {
//find first empty slot
if(bytes(currRequest.anwers[tmpI]).length == 0){
found = true;
currRequest.anwers[tmpI] = _valueRetrieved;
}
tmpI++;
}
Reaching consensus (1)
25
uint currentQuorum = 0;
//iterate through oracle list and check if enough oracles(minimum quorum)
//have voted the same answer has the current one
for(uint i = 0; i < totalOracleCount; i++){
bytes memory a = bytes(currRequest.anwers[i]);
bytes memory b = bytes(_valueRetrieved);
if(keccak256(a) == keccak256(b)){
currentQuorum++;
if(currentQuorum >= minQuorum){
currRequest.agreedValue = _valueRetrieved;
emit UpdatedRequest (
currRequest.id,
currRequest.urlToQuery,
currRequest.attributeToFetch,
currRequest.agreedValue
);
}
}
}
}Reaching consensus (2)
26
Implementation attributes
Fast time-to-market?- Keeping trust standards
- Data-feed fault tolerance
- Data veracity
- Lower smart contract costs
- Lower oracle complexity (in comparison to using proofs)
- Oracle decentralization
- Oracle ownership decentralization
27
Contributions
- Systematic literature review (paper to be submitted)
- Analysis of authenticity proofs
- Systematization of oracle architectures
- Implementing a multi-party self-hosted oracle
28
References
[Gor17] Gilroy Gordon. Provenance and authentication of oracle sensor data with blockchain lightweight wireless network authentication scheme for constrained oracle sensors. 2017.
[Mon18] Francisco Javier Andrés Montoto Monroy. Bitcoin gambling using distributed oracles in the blockchain. 2018.
[Ora18] Oraclize.it. Oraclize Documentation, 2018.
[ABV+18] John Adler, Ryan Berryhill, Andreas Veneris, Zissis Poulos, Neil Veira, and Anastasia Kastania. Astraea: A Decentralized Blockchain Oracle. aug 2018.
[ZCC+16] Fan Zhang, Ethan Cecchetti, Kyle Croman, Ari Juels, and Elaine Shi. Town Crier: An Authenticated Data Feed for Smart Contracts. Technical report, 2016.
[EH18] Jacob Eberhardt and Jonathan Heiss. Off-chaining Models and Approaches to Offchain Computations. In Proceedings of the 2nd Workshop on Scalable and Resilient Infrastructures for Distributed Ledgers - SERIAL’18, pages 7–12, New York, New York, USA, 2018. ACM Press.
[EJN17] Steve Ellis, Ari Juels, and Sergey Nazarov. ChainLink A Decentralized Oracle Network. Technical report, 2017.
[TR17] Jason Teutsch and Christian Reitwießner. A scalable verification solution for blockchains. Technical report, 2017.
[Vit14] Vitalik Buterin. SchellingCoin: A Minimal-Trust Universal Data Feed, 2014.
29
Obrigado
Pedro Duarte da Costa
pedro.duartecosta@fe.up.pt