Secure Conflict-free Replicated Data Types
Manuel Barbosa, Bernardo Ferreira, João Marques, Bernardo Portela, and Nuno Preguiça. 2021. Secure Conflict-free Replicated Data Types. International Conference on Distributed Computing and Networking 2021
Novelty: new cryptographically secure CRDT protocols for Registers, Sets, Counters, and Bounded Counters
Overview
Method: add encryption over standard CRDT protocols, or partial homomorphic encryption for counters which assume to perform arithmetics as part of the protocol
Constraint/Need: CRDTs should be computable server-side, by servers that do not possess the decryption key
SUPPORTED TOPOLGY
Principals:
- clients with a shared encryption means*
- clients using a secure connection to a server*
- server(s)
- not just relays for client messages, but databases that store the documents
- CRDTS handled by servers, to allow replication to multiple servers, allowing geo-distributed applications
Supported operations:
- client-server setup/[query/update]
- server-server setup/propagation
- server merge (local operation)
*establishement of it is out of the scope of this paper
Honest-But-Curious adversaries: SERVERS
- adversary follows faithfully the protocol, but tries to learn information from its execution
- a reasonable model in specific settings:
- trusted parties under legal constraints
- auditing can be done, with repercussions
THREAT MODEL
Malicious adversaries: NONE
- may behave arbitrarily, but still bound by cryptographic constraints
Trusted parties: USERS
RegisteR
Done via regular encryption
COUNTER
Done via homomorphic encryption, limited to addition thanks to the addition of a plaintext Lamport Clock
Done via regular encryption, plus enventual leakage of the operation and a label for each stored/checked value
SET
BOUNDED COUNTER
Similar to counter, with a delegated invariant check to the client upon updates
RegisteR
COUNTER
SET
BOUNDED COUNTER
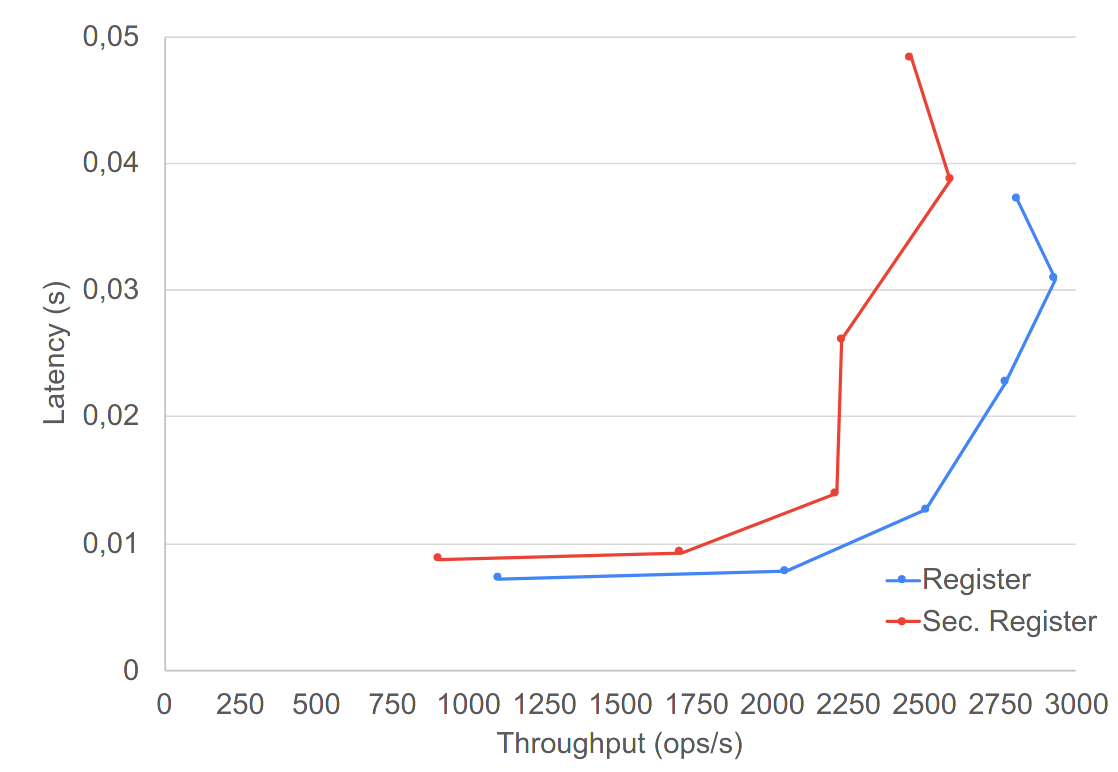
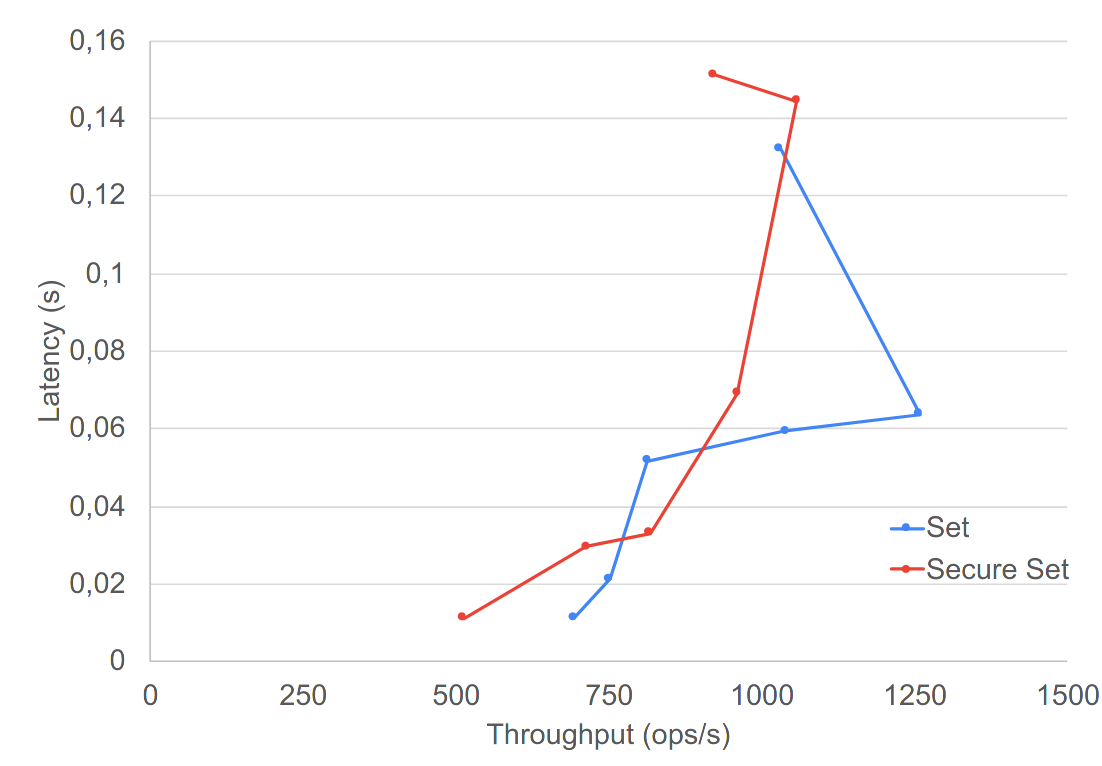
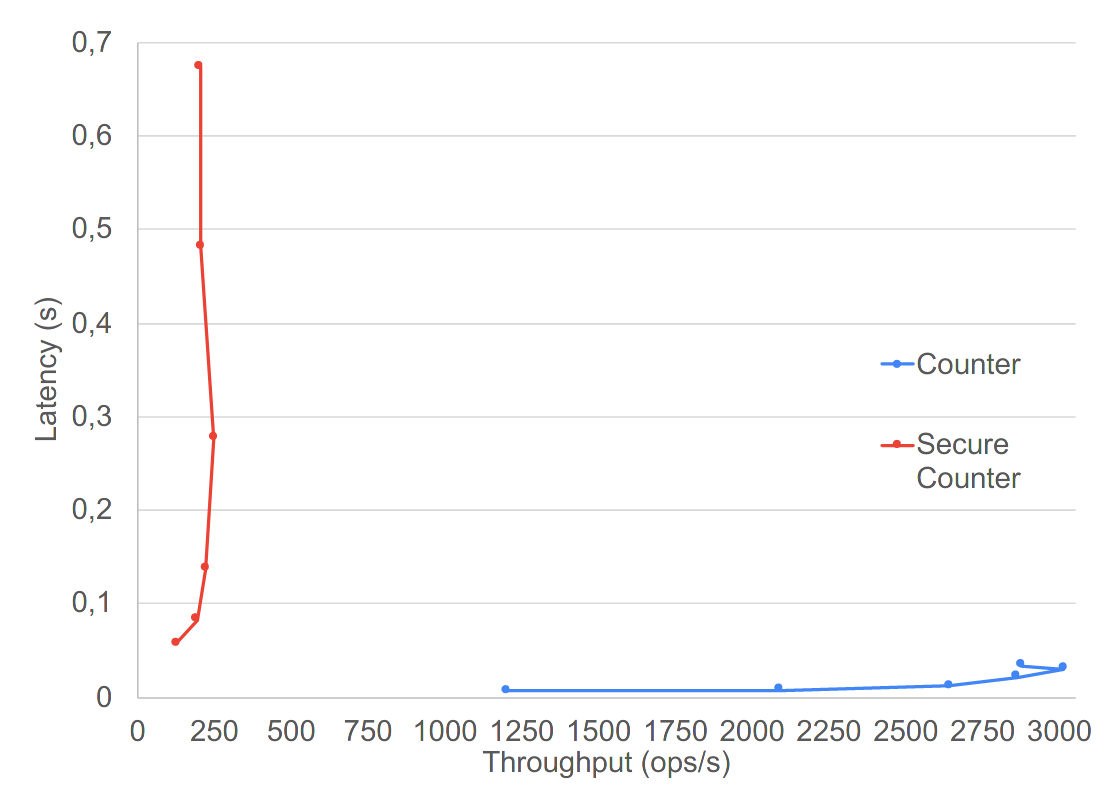
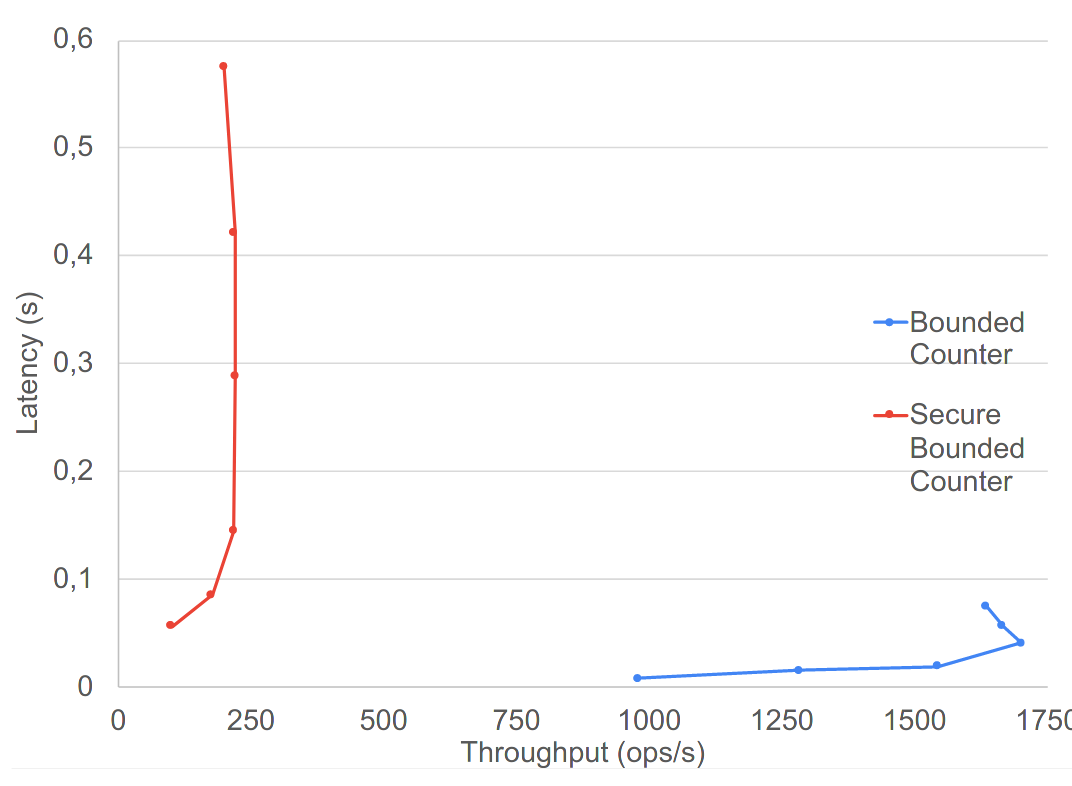
lower is better ; more to the right is better
Secure CRDT
CRDT
graphs taken from Secure Conflict-free Replicated Data Types. International Conference on Distributed Computing and Networking 2021, Manuel Barbosa, Bernardo Ferreira, João Marques, Bernardo Portela, and Nuno Preguiça. 2021.
MACRO PERFORMANCE
Average lantency increase of 20 to 38% on their demonstrator
No major outlier in latency, even for create-heavy test cases
Throughput reduction of 5%
DISCUSSION
The system leaks some information to keep operations reasonably costly
Clients are tasked with invariant checking for bounded counters ; similarly constrained structures derived from set/registers would also rely heavily on client verification a posteriori
Users have to be trusted: how to audit operations ; how to enforce authorization/rights on invariants on later synchronization?