Serverless authentication with jwt
Mehul Patel,@rowdymehul


About me
- I am Mehul Patel
- Engineer at Zimbra
- Mozilla Reps Mentor
- Auth0 Ambassador
- Rust Mobilizer
- Co-founder of IDF


Source: giphy.com
What & why
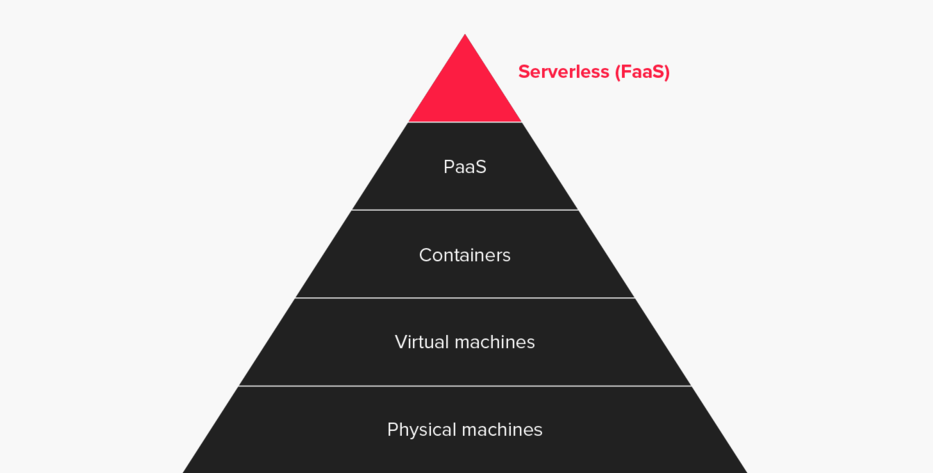
credits: DZone


credits: DZone
Focus on code, not servers
credits: auth0

what is...
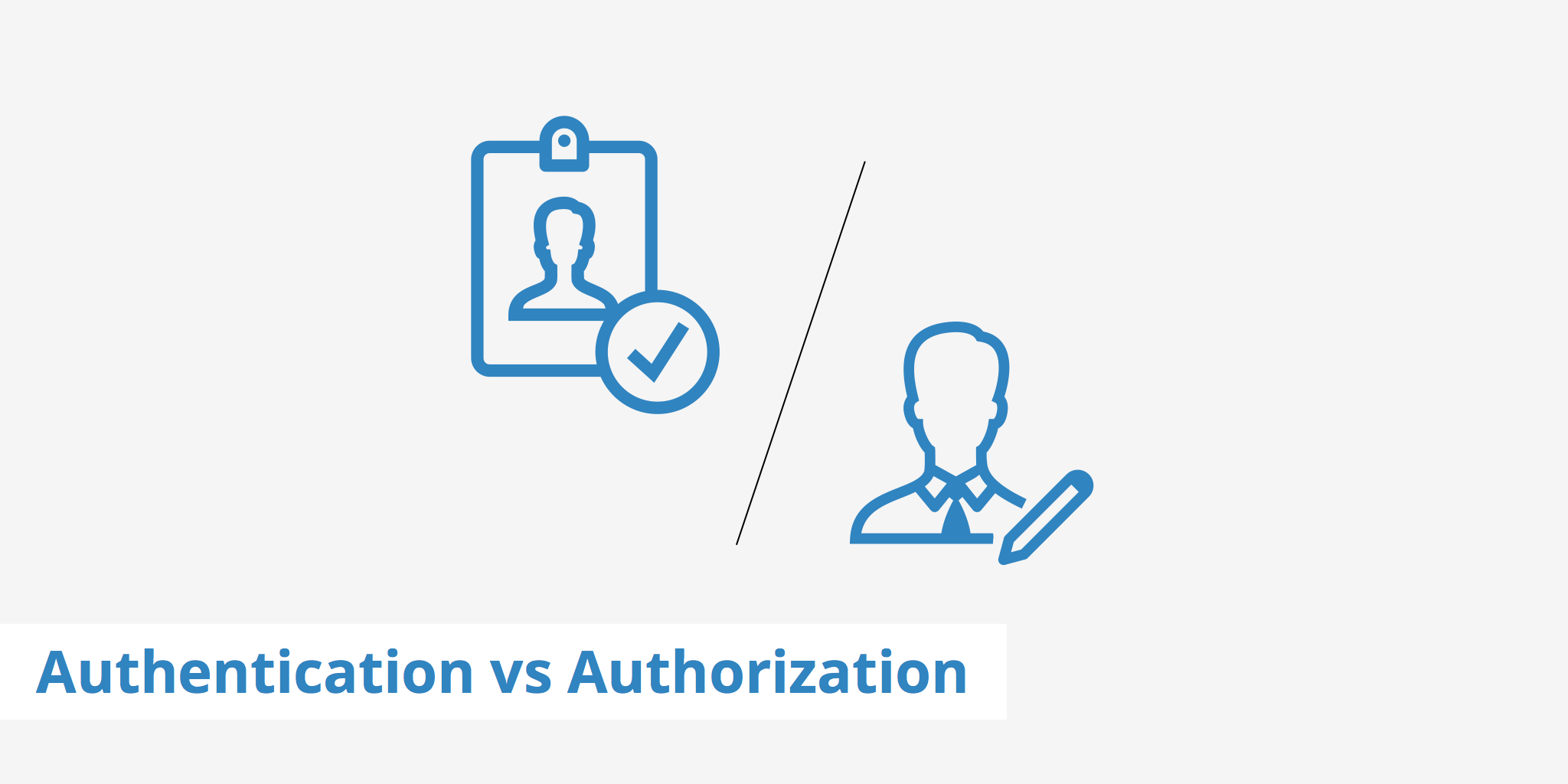
Image credits: keycdn.com

Image source: Google

Image source: softwareengineeringdaily.com
All you need is code!
Run code with an HTTP call.
No provisioning. No deployment.
credits: auth0
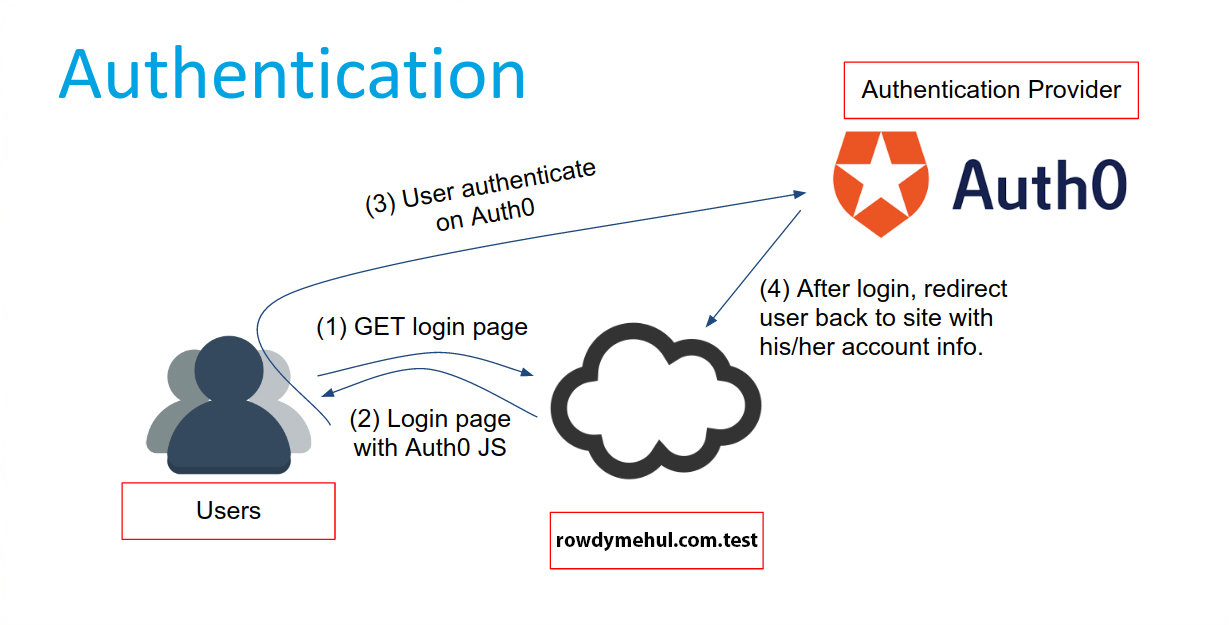
serverless authentication
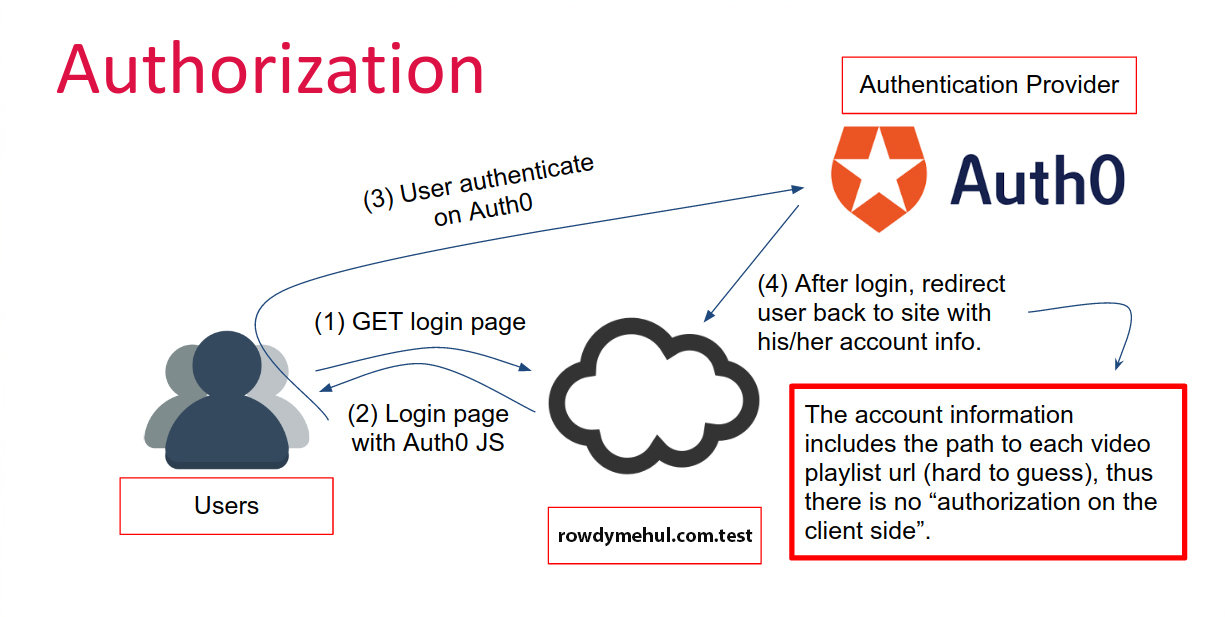
serverless authorization
Let's talk about JWT
Further, let's explain some concepts.
- Compact
- Self-contained
When should you use JSON Web Tokens?
1. Information Exchange
2. Authorization
What is the JSON Web Token structure?
- Header
- Payload
- Signature
Below is an encoded JSON Web Token:
// Token structure
header.payload.signature
// A real world token
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiYWRtaW4iOnRydWV9.TJVA95OrM7E2cBab30RMHrHDcEfxjoYZgeFONFh7HgQ
Authentication Flow
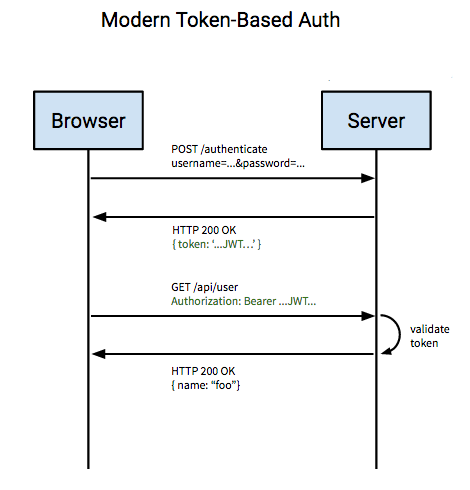
Image Source: StackOverflow
How an application uses JWT to verify the authenticity of a user.
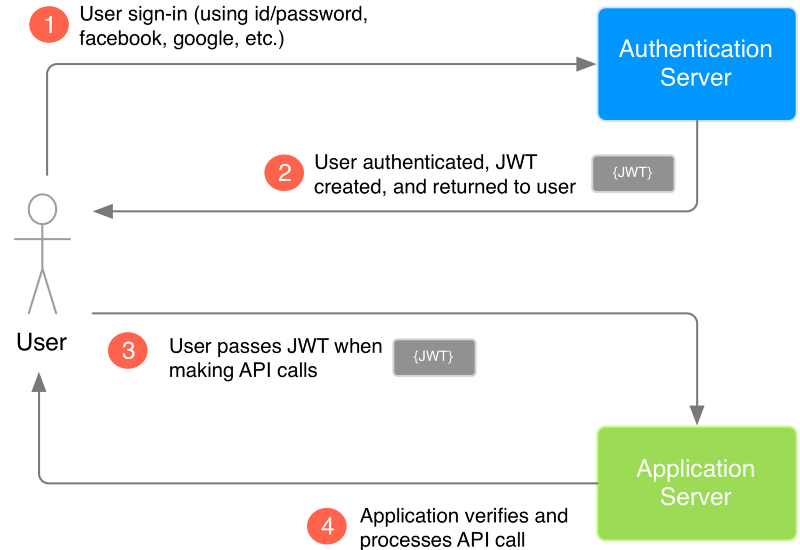
Image source: medium.com
Let's make it easy with ...


Let's take one Example...
Another example ...
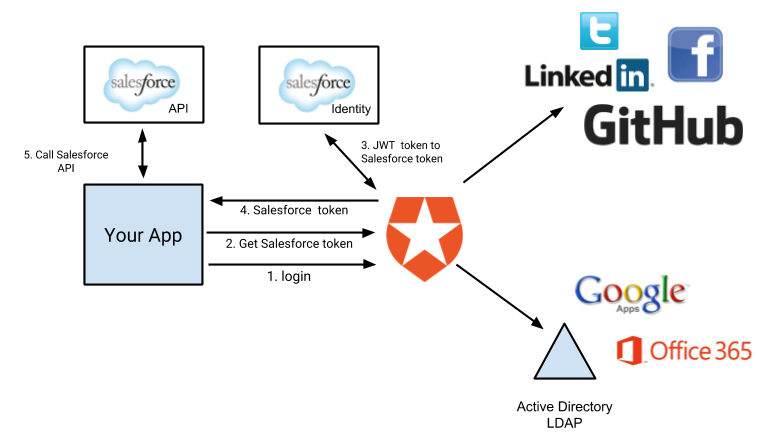
Image source: auth0/docs
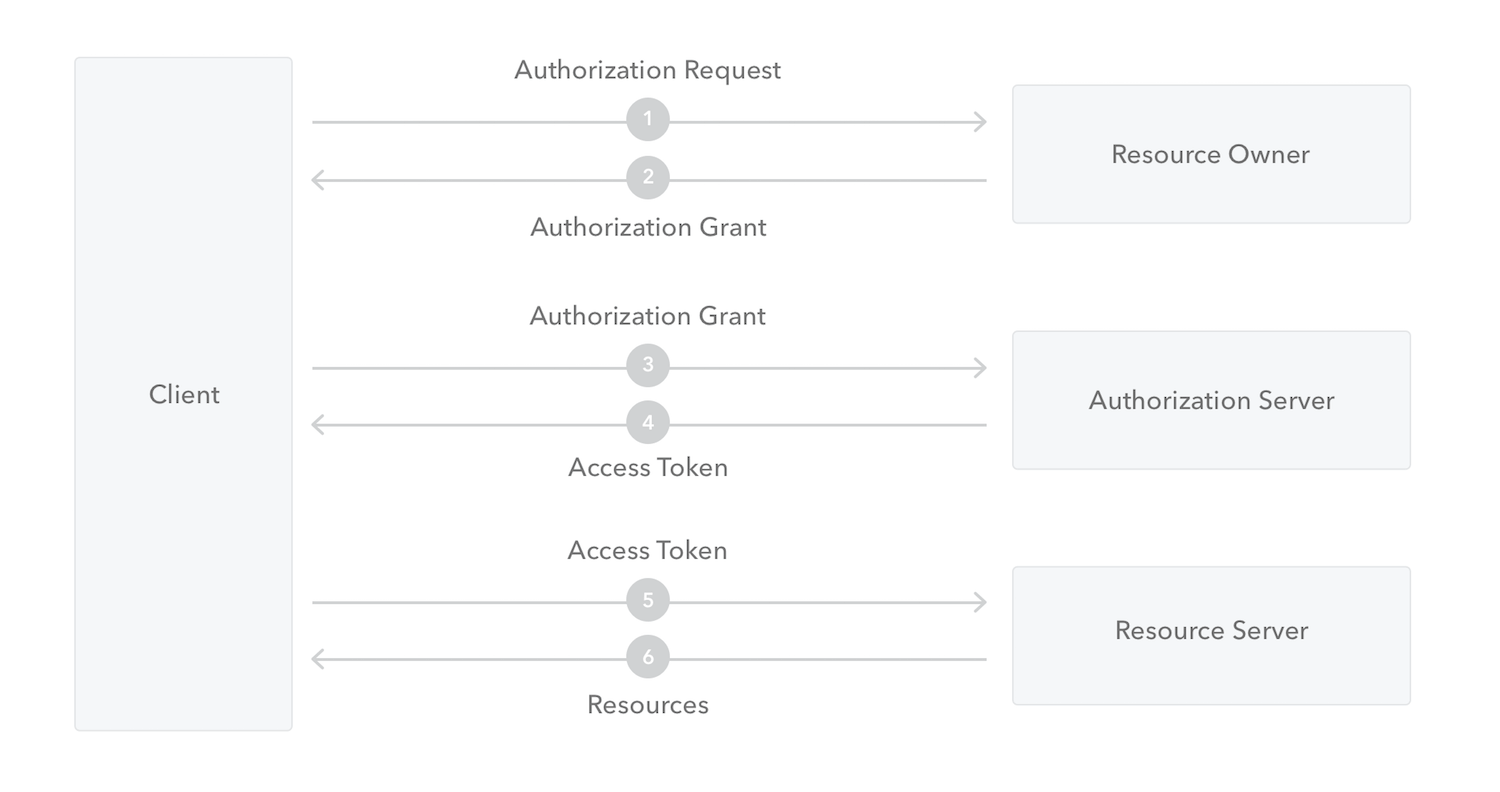
What is OAuth 2.0?
OAuth 2.0
An open standard for access delegation, commonly used as a way for Internet users to grant websites or applications access to their information on other websites but without giving them the passwords.
OAuth 2.0 roles
-
Resource Owner: the entity that can grant access to a protected resource. Typically this is the end-user.
-
Resource Server: the server hosting the protected resources. This is the API you want to access.
-
Client: the app requesting access to a protected resource on behalf of the Resource Owner.
- Authorization Server: the server that authenticates the Resource Owner, and issues Access Tokens after getting proper authorization. In this case, Auth0.
protocol flow
Visit auth0.com/opensource



Source: giphy.com


THANK YOU!
