Serverless Auckland Meetup
Mehul Patel,@rowdymehul

Identity 101, Serverless, Architecture and its Authentication.
About Me
Mehul Patel
* Engineer @ Zimbra
* Technical Evangelist
* Auth0 Ambassador
* Mozilla Reps Mentor
* CAC @ Mozilla
* GDG Nashik Organizer
* Rust Hacks @rusthack
@rowdymehul


Agenda
1. Serverless
2. Authentication & Authorization
3. JWT
4.OAuth
5. SAML
6. Deployment
Serverless
Serverless
What is Serverless?
Serverless, is an execution model where the cloud provider is responsible for executing a piece of code by dynamically allocating the resources. The code is typically run inside stateless containers that can be triggered by a variety of events including http requests, database events, queuing services, monitoring alerts, file uploads, scheduled events (cron jobs), etc. The code that is sent to the cloud provider for execution is usually in the form of a function. Hence serverless is sometimes referred to as “Functions as a Service” or “FaaS”.
Serverless
What is Serverless?

Serverless
What is Serverless?
Let me break it down!
Serverless
What is Serverless?
- Serverless is an execution model
- Cloud providers execute the code
- by allocating resources dynamically
- the code runs inside Stateless containers
- triggered by event( http request, cron job)
- code sent to cloud providers are in the form of functions
- hence "Function as a Service" or "Fass"
Serverless
Traditional Architecture
- we are charged for keeping the server up
even when we are not using
- responsible for uptime and maintenance of the server and all its resources.
- responsible for applying the appropriate security updates
- we need to manage scaling
Serverless

in Serverless?
Serverless
Why Serverless?
Just like wireless internet has wires somewhere, serverless architectures still have servers somewhere.
What ‘serverless’ really means is that, as a developer, you don’t have to think about those servers.
You just focus on code.
Serverless
Serverless Cloud Providers






Serverless
What you can do with serverless application
- Build APIs
- Data processing
- Custom automation
Serverless
Core Concepts
- Functions
- Services
- Events
The Game plan
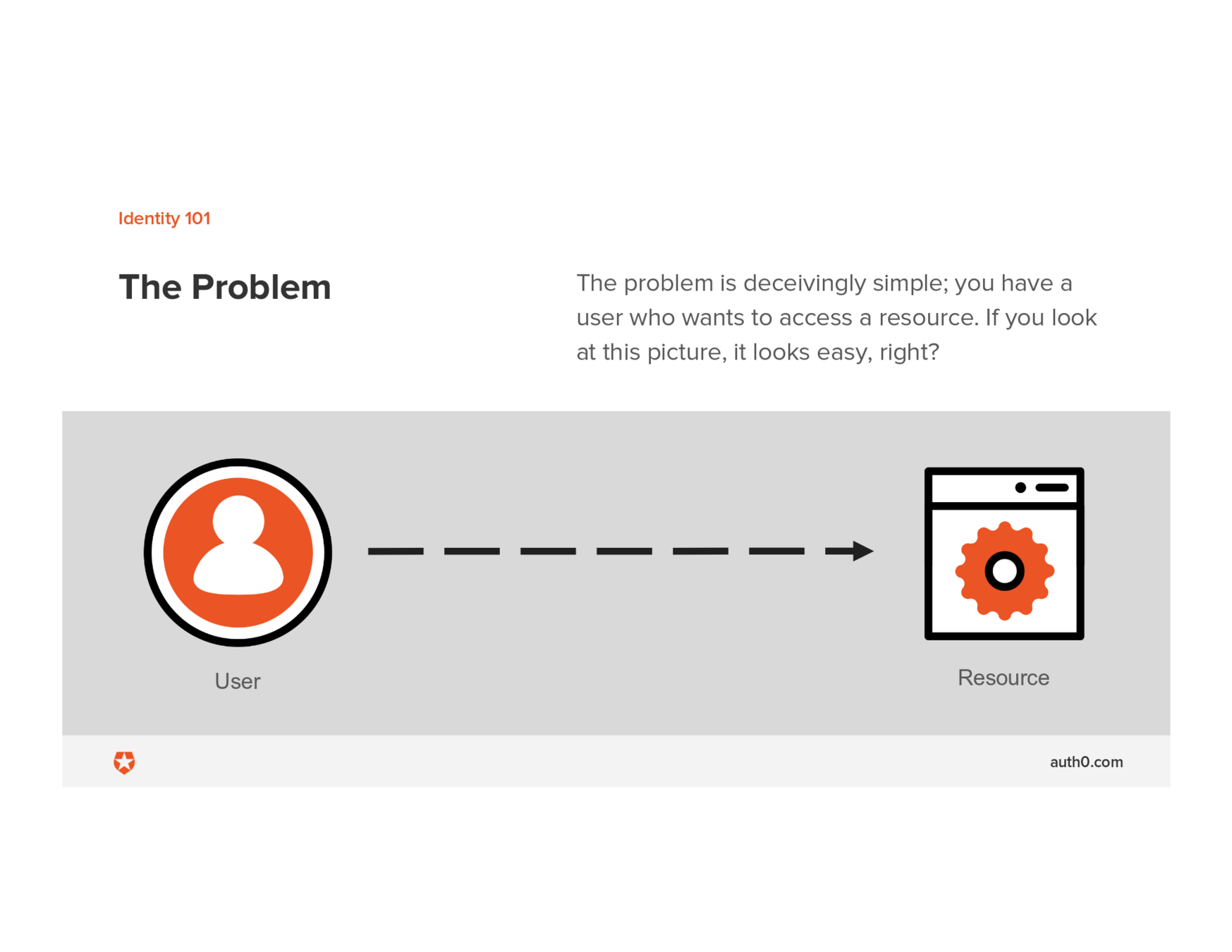
1. The Problem
2. The Role of Open Standards

Authentication & Authorization
Authentication & Authorization
Difference
Difference

Authentication & Authorization
Serverless
Authentication
Serverless Authentication
Authentication & Authorization
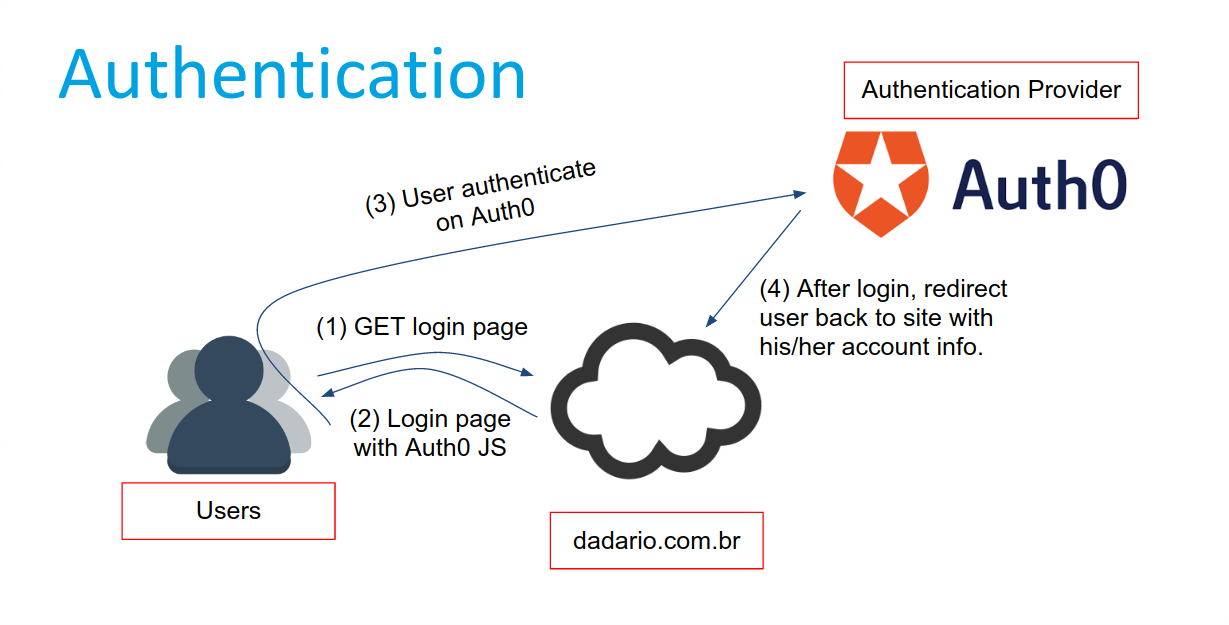
source: dadario.com.br
Serverless
Authorization
Serverless Authorization
Authentication & Authorization
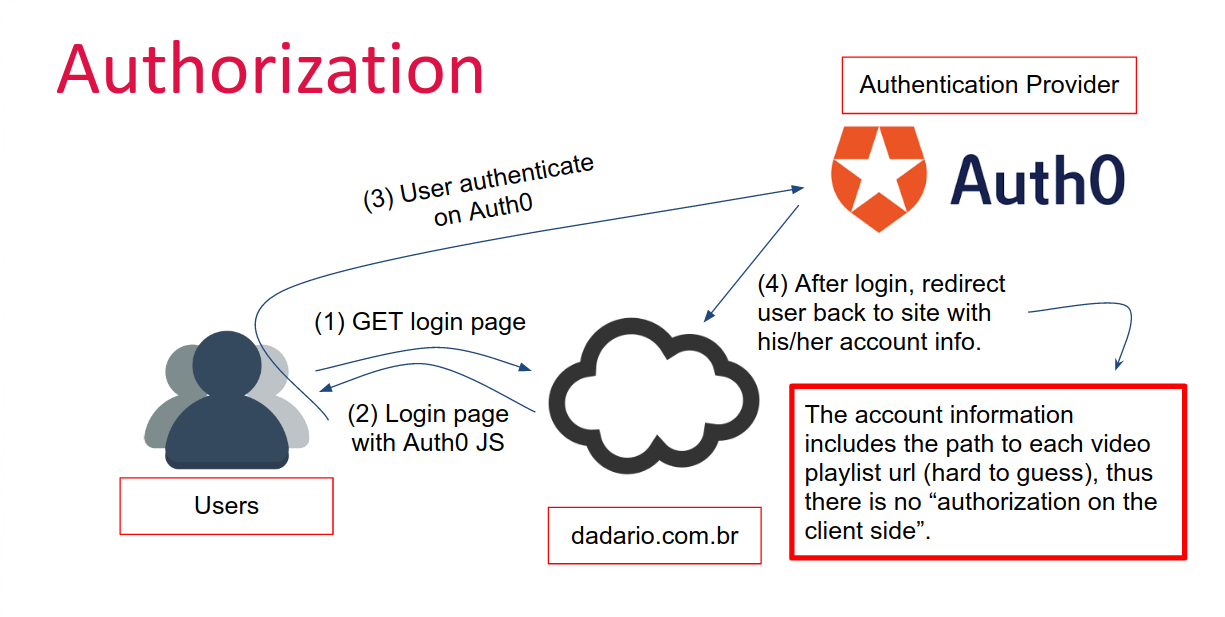
source: dadario.com.br
JSON Web Token
JWT
What is JSON Web Tokens?
- A way to encode information
- Securely communicate JSON Objects
- Secret-based Verification
- Consists of a header, payload and signature
- Self-contained
JWT
JSON Web Token

JWT
The JWT Header
The header is a JSON Object usually consisting of the type( typ ) , which is JWT, and the algorithm used for encrypting the JWT (alg ):
{
"alg": "HS256",
"typ": "JWT"
}JWT
The JWT Payload
The Payload is a JSON object that consists of user defined attributes ( called public claims ) . Some attributes are defined in the standard ( these are called reserved claims ).
{
// reserved claim
"iss": "https://myapi.com",
// public claim
"user": "rowdymehul"
}JWT
The JWT Signature
The Signature is the encoded header and payload, signed with a secret.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret
)
This accomplishes several tasks at once, including:
- Proves the identity of the sender
- Ensures the message has not changed
JWT
The JWT Token
A finished token looks like [encoded header].[encoded payload].[signature] :
JWT

The JWT Token
How an application uses JWT to verify the authenticity of a user.
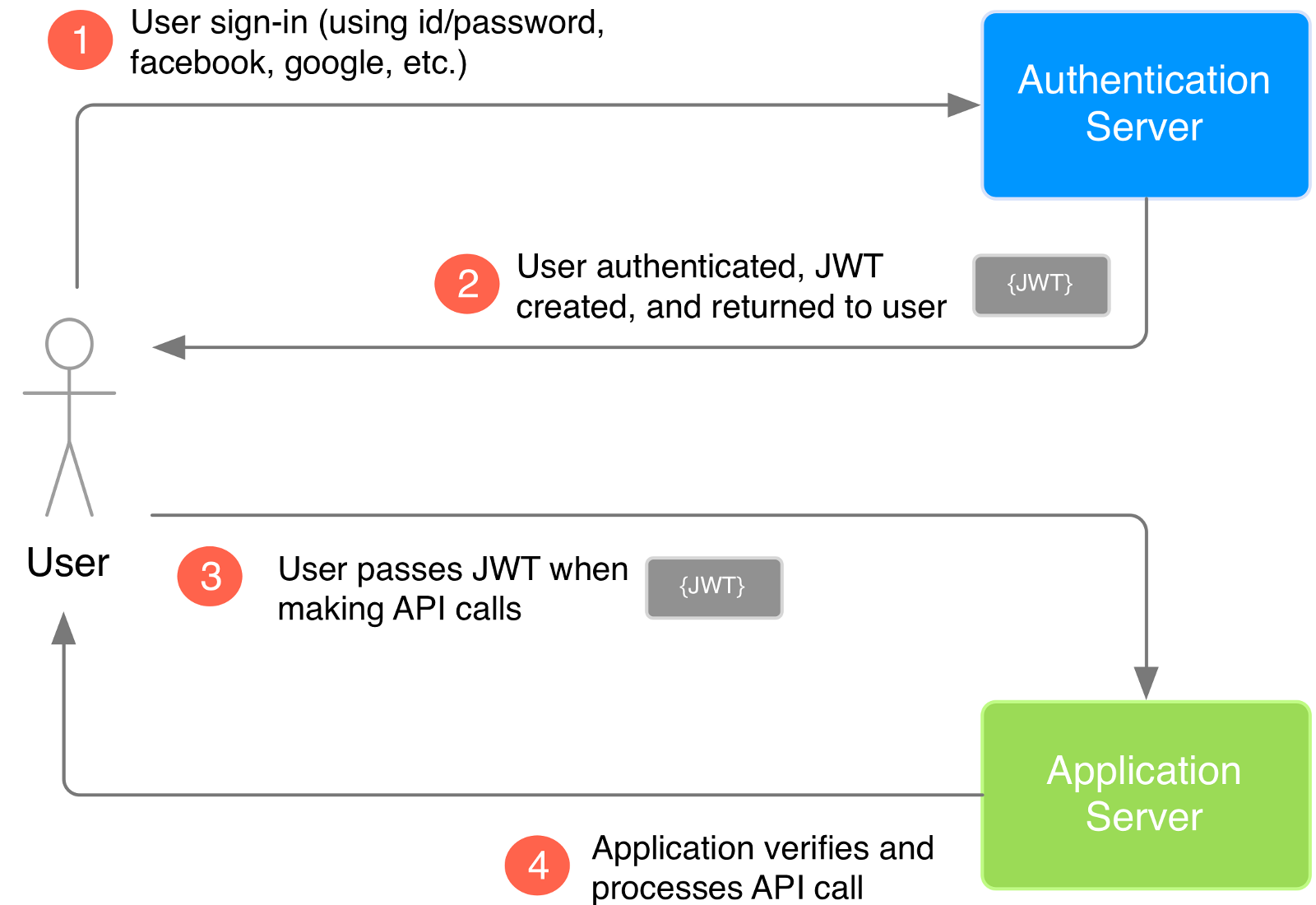
Credits: Medium
OAuth
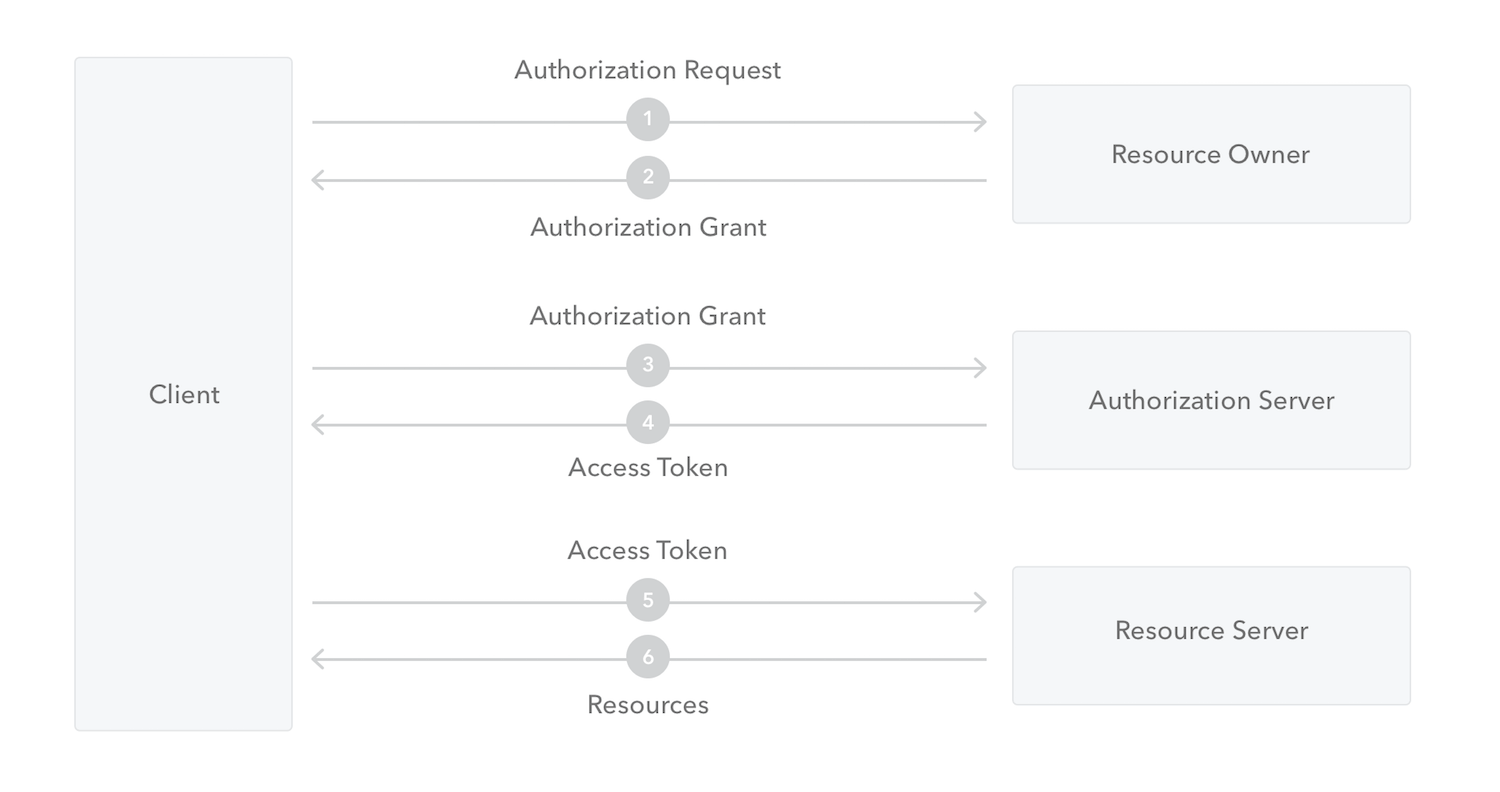
OAuth 2.0
An open standard for access delegation, commonly used as a way for Internet users to grant websites or applications access to their information on other websites but without giving them the passwords.
OAuth 2.0 roles
-
Resource Owner: the entity that can grant access to a protected resource. Typically this is the end-user.
-
Resource Server: the server hosting the protected resources. This is the API you want to access.
-
Client: the app requesting access to a protected resource on behalf of the Resource Owner.
- Authorization Server: the server that authenticates the Resource Owner, and issues Access Tokens after getting proper authorization. In this case, Auth0.
Protocol flow
SAML
Security Assertion Markup Language (SAML) is an XML-based framework for authentication and authorization between two entities: a Service Provider and an Identity Provider.
Benefits of SAML Authentication
- Standardization
- Improved User Experience
- Increased Security
- Loose Coupling of Directories
- Reduced Costs for Service Providers
<soap:Envelope xmlns:soap='http://www.w3.org/2003/05/soap-envelope'>
<soap:Header>
<context xmlns='urn:ServerlessAKL'>
<authToken type='SAML_AUTH_PROVIDER'>b07b804c-7c29-ea16-7300-4f3d6f7928ac</authToken>
</context>
</soap:Header>
<soap:Body>
<SomeRequest xmlns='urn:ServerlessAKL'>…</SomeRequest>
</soap:Body>
</soap:Envelope>The user’s client sends a SOAP request containing an assertion identifier to the ServerlessAKL server
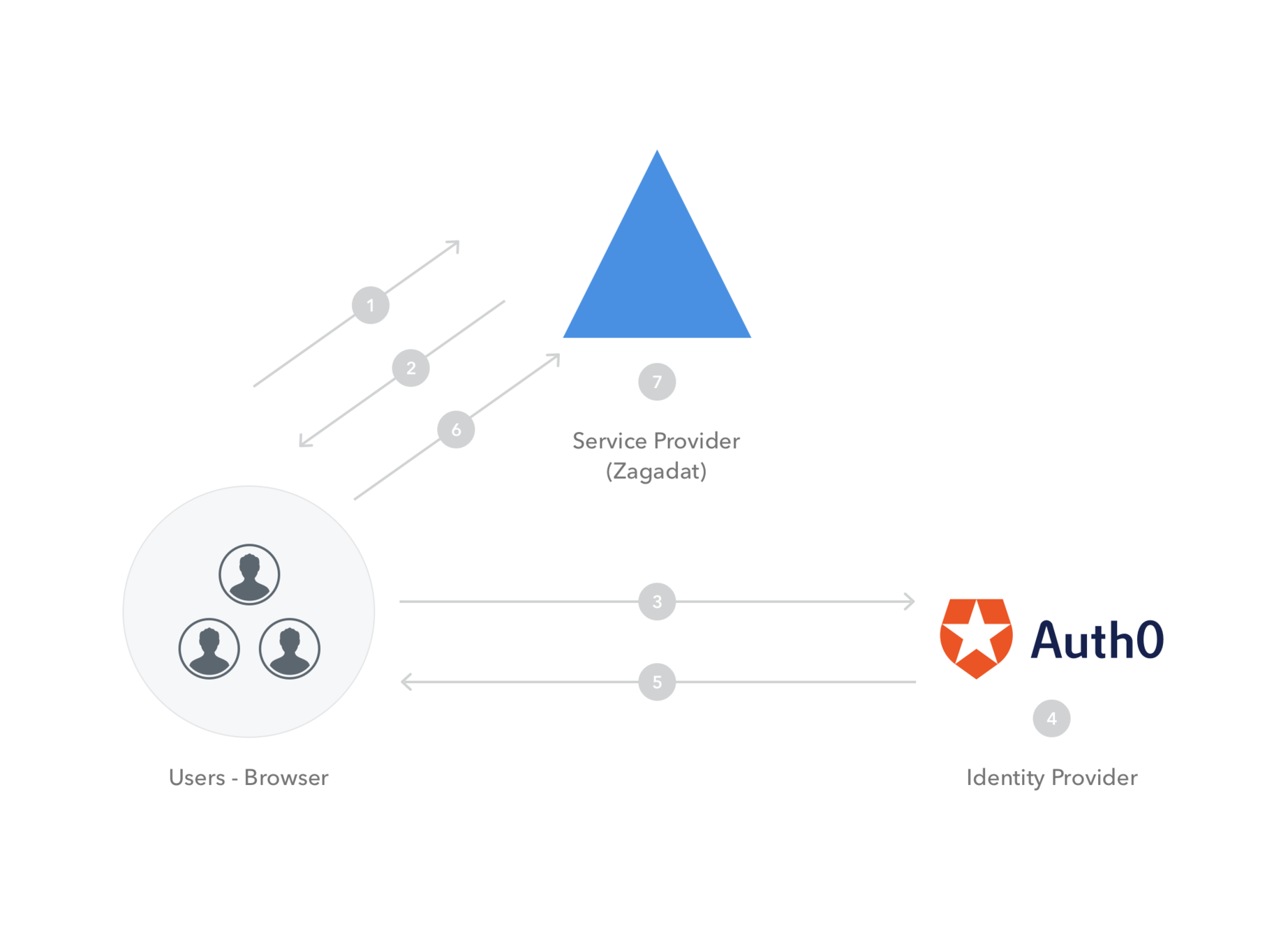
Process Flow diagram
Image Source: Auth0 Blog
Deployment

Demo
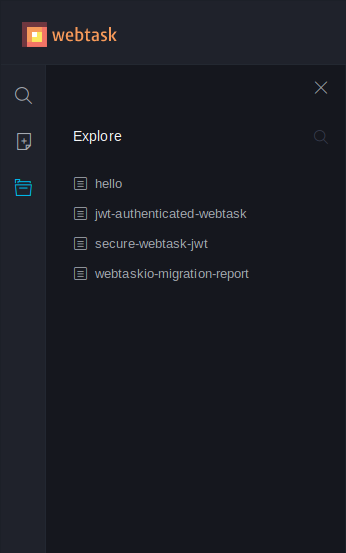
webtask.io
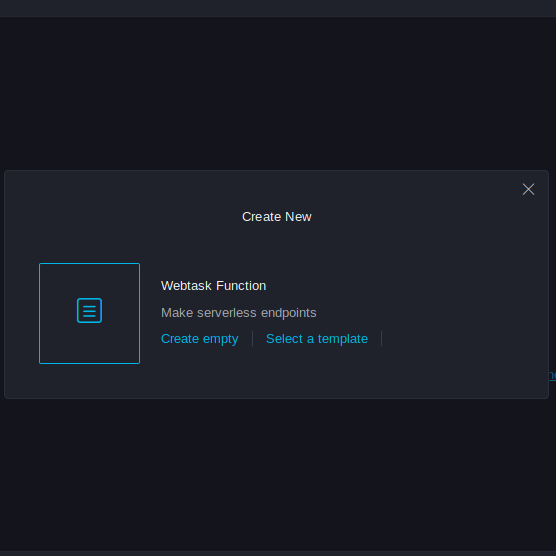
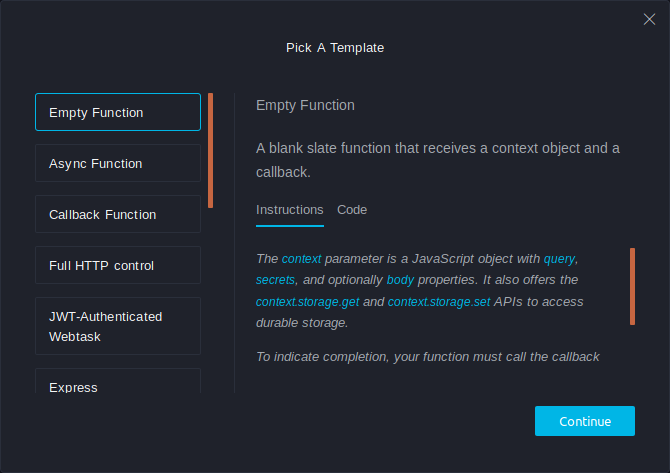
Demo
Demo
Resources
General JWT Resources
jwt.io
JWT Handbook
http://bit.ly/jwt-book
WebTask
webtask.io
Connect with me
facebook.com/therowdymehul
@rowdymehul
@rowdymehul
https://in.linkedin.com/in/rowdymehul
way2mehul@gmail.com

THANK YOU!

