ODL and Docker
Ryan Wallner
@ryanwallner
wallnerryan@gmail.com


Docker
- open-source linux container engine. "commoditize containers"
-
use cases include
- automation
- lightweight PaaS
- testing/continuos deployment
- horizontal scale for webapps, dbs, service
-
"Configure once, run many"
- escape dependency hell
run docker
once installed
sudo docker run -i -t ubuntu /bin/bash
or create a "Dockerfile"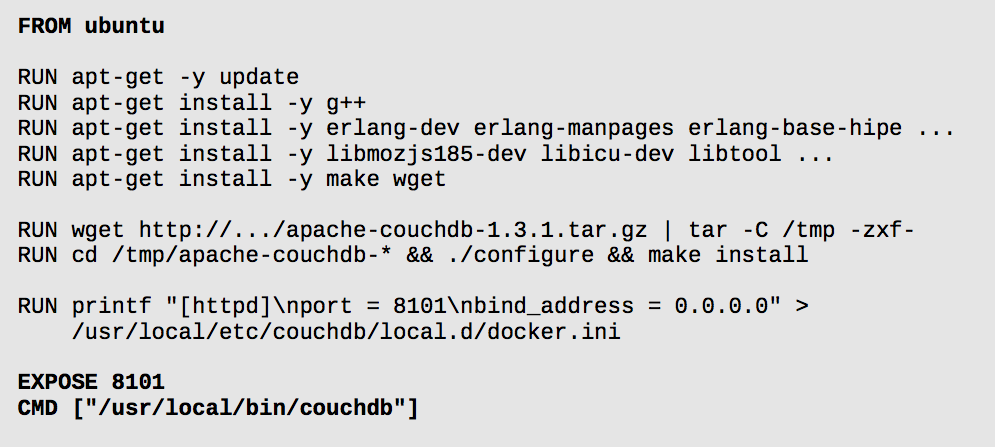

Docker Cont'd
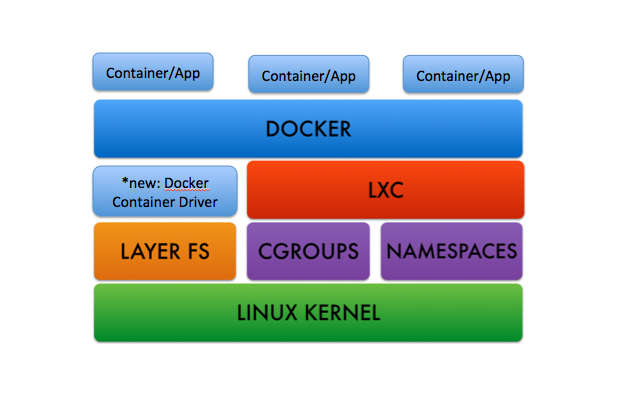
- Different than a VM
- if you know LXC/Linux Namespaces, those are the basics
- Share host kernel/libraries/binaries, no boot process
- isolation of network, mem, cpu etc through cgroups

CoW
-
unified file system ensures any changes to an application are only a "diff" of sorts.
- significant memory / resource saving. ten's of VM's vs. thousands of Containers.

union file system

At first, the top read-write layer has nothing in it, but any time a process creates a file, this happens in the top layer. And if something needs to update an existing file in a lower layer, then the file gets copied to the upper layer and changes go into the copy. The version of the file on the lower layer cannot be seen by the applications anymore, but it is there, unchanged. device-mapper
- An alternate to the AuFS dependency
- If running RedHat/CentOS/Fedora etc
- use [--storage-driver|-s]="devicemapper"
-
Uses thin provisioning, sparse file, and snapshots to achieve similar flexibility as without dm. Commit and push images as you did before.
Other options include btrfs, overlayfs etc. So far this is all been /is being talked about in the docker community.
Final product
*note, LXC dependensies are going away, latest master uses native docker (Go) driver.
cgroups
-
(on ubuntu 12.04+), cgroups available are located in /sys/fs/cgroup
- Docker containers are listed here with there cgroups
- e.g find /sys/fs/cgroup/devices -name <uuid*>
cpu, net, mem cgroups and allocation will be listed inside its dir.
"tasks" will also be listed, these are things like the running network namespace. - this netns process will be locate in /proc/<task-id>/ns/net
- Other namspaces here as well, pid uts...
namespaces
the important ones : pid, uts, net, mount
- I'll focus on the network namespace
sudo docker run -i -t ubuntu /bin/bashNSPID= $(head -n 1 $(cat /sys/fs/cgroup/devices/docker/d6c508.../tasks))mkdir -p /var/run/netnsrm -f /var/run/netns/$NSPIDln -s /proc/$NSPID/ns/net /var/run/netns/$NSPIDip netns exec $NSPID ifconfig
aufs
-
docker mounts aufs at /var/lib/docker/aufs/mnt/<uuid>
mounts rw overtop the rootfs usually ro, this union fs portion is where all the "diffs" of image to image come from.
cat /proc/mounts
none /var/lib/docker/aufs/mnt/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924 aufs rw,relatime,si=ce51a2b9063aa9a1 0 0
none /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root aufs rw,relatime,si=ce51a2b9063aa9a1 0 0
/dev/disk/by-uuid/2c1e470e-c411-4ed2-ad4d-581f3d433c55 /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root/.dockerinit ext4 ro,relatime,errors=remount-ro,data=ordered 0 0
/dev/disk/by-uuid/2c1e470e-c411-4ed2-ad4d-581f3d433c55 /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root/.dockerenv ext4 ro,relatime,errors=remount-ro,data=ordered 0 0
tmpfs /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root/etc/resolv.conf tmpfs ro,relatime,size=203428k,mode=755 0 0
/dev/disk/by-uuid/2c1e470e-c411-4ed2-ad4d-581f3d433c55 /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root/etc/hostname ext4 ro,relatime,errors=remount-ro,data=ordered 0 0
/dev/disk/by-uuid/2c1e470e-c411-4ed2-ad4d-581f3d433c55 /var/lib/docker/containers/d6c508b18f1568c964b76ce60113f8bf72062fc9a9882dc20f6447d194855924/root/etc/hosts ext4 ro,relatime,errors=remount-ro,data=ordered 0 0 use cases
| Memcached as a Service | http://bit.ly/11nL8vh |
| Push-button Deployment with Docker | http://bit.ly/1bTKZTo |
| Dokku - Docker powered mini-Heroku. The smallest PaaS | http://bit.ly/191Tgsx |
Docker Registry

Docker Networking
- not going to spend a ton of time
-
http://docs.docker.io/en/latest/use/networking/
- linux bridge, veth-pairs to container, iptables masquerading
- What about OVS?
-
https://github.com/jpetazzo/pipework
- *no "true" netvirt (no overlay impl)
-
http://docs.openstack.org/trunk/config-reference/content/docker.html

docker/iptables
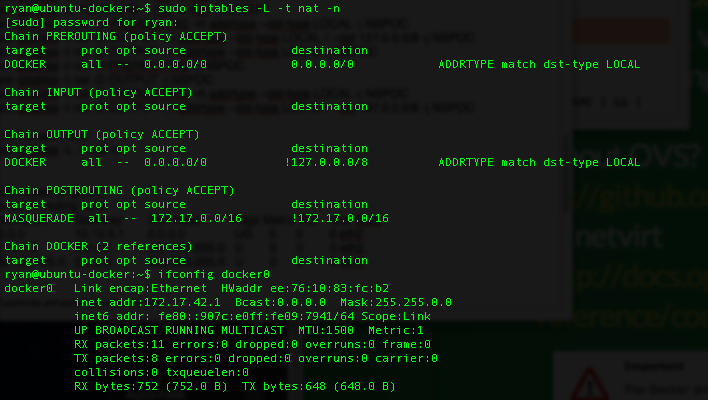
fore those who like to see the rules
#INITIAL CHAIN
sudo iptables -t nat -F DOCKER
sudo iptables -t nat -X DOCKER
sudo iptables -t nat -N DOCKER
#ADD
sudo iptables -t nat -A POSTROUTING -s 172.17.42.1/24 ! -d 172.17.42.1/24 -j MASQUERADE
sudo iptables -I FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
sudo iptables -I FORWARD -i docker0 ! -o docker0 -j ACCEPT
sudo iptables -D FORWARD -i docker0 -o docker0 -j DROP
sudo iptables -C FORWARD -i docker0 -o docker0 -j ACCEPT
sudo iptables -I FORWARD -i docker0 -o docker0 -j ACCEPT
sudo iptables -t nat -D PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
sudo iptables -t nat -D OUTPUT -m addrtype --dst-type LOCAL ! --dst 127.0.0.0/8 -j DOCKER
sudo iptables -t nat -D OUTPUT -m addrtype --dst-type LOCAL -j DOCKER
sudo iptables -t nat -D PREROUTING -j DOCKER
sudo iptables -t nat -D OUTPUT -j DOCKER
sudo iptables -t nat -A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
sudo iptables -t nat -A OUTPUT -m addrtype --dst-type LOCAL ! --dst 127.0.0.0/8 -j DOCKER current implementation...
def plug_vifs(self, instance, network_info): """Plug VIFs into networks.""" msg = _("VIF plugging is not supported by the Docker driver.") raise NotImplementedError(msg)def unplug_vifs(self, instance, network_info): """Unplug VIFs from networks.""" msg = _("VIF unplugging is not supported by the Docker driver.") raise NotImplementedError(msg)
End
- Im sure i missed things, docker community is a great one though, plenty of resources.
- Proposal
- enable docker to participate in the overlay
start a discussion
Title
Title
Title
Title
Title
Title
Title
Title
Title
Title
Title
Title
Title
Docker
- open-source container engine
- if your familiar with LXC
- ease of use, scale, orchestration
- Use cases
- automation
- escape package dependency hell
- * as a service
- scale
Docker is used for odl installs
https://wiki.opendaylight.org/view/Release/Hydrogen/Virtualization/Installation_Guide#Docker_Image
*could use for dev environment.
//TODO example