Your Political Campaign
Needs a CISO
J0N J4RV1S
BSidesSLC 2017 slides.SecureUtah.org
Politicizing InfoSec Sucks
We've gotten to this ridiculous position where aspects of infosec have become so ridiculously politicized it's become a partisan message in order to make even basic facts.

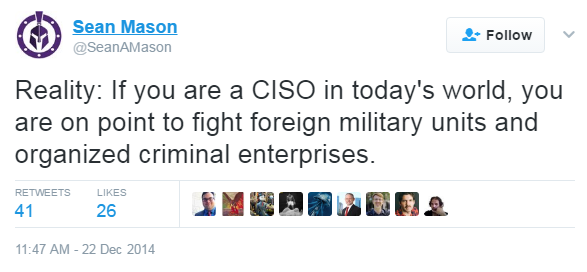
What is the CISO's role?
-
Ensure information assets and technologies are protected
-
Directs staff in developing, implementing, and maintaining processes to reduce information and IT risks
-
Respond to incidents, establish controls, manage security technologies, and direct the establishment and implementation of policies and procedures
- Usually responsible for information-related compliance (US PCI DSS, FISMA, GLBA, HIPAA, etc)
What is the CISO's role?
Today’s CISOs must not only be a technical security expert; they must also be:
- Effective risk managers with a deep understanding of the business, who can develop and drive an information security strategy and program
- Successful leaders who can instill a culture of security throughout the enterprise
- Great communicators who can seamlessly move from an internal IT meeting about firewall configurations to a presentation to the Board of Directors

What is the CISO's role?
What is the CISO's role?
2016 POTUS Campaigns
Trump
Clinton
Candidate raised......$973.2M
Super-PACs raised....$217.5M
Total, Dec '16.........$1,190.7M
Candidate raised......$564.3M
Super-PACs raised......$82.3M
Total, Dec '16...........$646.8M
Clinton staff, Aug '16.......800
Total staff, Oct '16..........5,138
Trump staff, Aug '16..........130
Total staff, Oct '16..........1,409

i can has security?

Email Servers
Candidate's Server Accidentally Leaked Résumés of More Than 20 Aspiring Interns *
Misconfigured Amazon S3 bucket
+ guess obvious file names
= anyone can download the files
CloudSec
Ex-Vendor's Server Accidentally Leaked Personal Information of Campaign Donors *
Misconfigured Amazon S3 bucket
+ former vendor did not purge data
= personal information leaked
CloudSec
-
Apply access and security controls to your data
-
Audit the controls and review the access logs
-
Know what data your vendors hold
-
Require vendors to purge data when contract ends
-
Know the value of the data you collect -
-
What's used to prove your identity to Gmail, Twitter, Facebook, and many other websites?
-
Personal email address + mobile phone number
-
Lessons Learned
Email Servers

WebSec
-
Mischief-Makers in the Middle
-
Code Injectors
-
Cookie Thieves
-
End-point Imposters
-
VPN & Tor Exit Nodes
-
-
Eavesdroppers
-
Dodgy ISPs
-
Nosy Nations
-
WiFi Snoopers
-
Perversive Trackers
-
HTTPS or GTFO
Strong end-to-end encryption defends against:

WebSec
Submit a Pull Request to Inject Arbitrary JavaScript Into a Website Donation Page *
Website loads code directly from public repo
+ repo owner changes code
= website serves arbitrary code to visitors
Submit a Pull Request to Inject Arbitrary JavaScript Into a Website Donation Page *
WebSec
A Political Appointee to a Cyber Security Position Had a Really Insecure Website *
Lend your name to a security consulting firm
+ website software is all kinds of bad
= InfoSec Twitter all in a tizzy
WebSec

WebSec
text

WebSec
-
Audit your codebase
-
Hire competent vendors
-
Audit your vendors' work
-
Secure your website if you depend on it for anything important
Lessons Learned
Email Servers

Email Servers
Happy reading!
- Hillary Clinton's email controversy
- Trump Organization uses insecure email servers
- Trump's most senior staff use a private email server
- Pence used AOL for state business and was hacked
#CampaignSec is tough...
...but what if you win?
Your family and staff are now high-value targets for every foreign intelligence agency, bored hacker, and motivated criminal group in the world!
Congratulations!



Congratulations!


Which Android phone does the President use? *




MobileSec
MobileSec
The working assumption should be that [the President's] phone is compromised by at least one—probably multiple—hostile foreign intelligence services and is actively being exploited.
Anyone around the President should presume they are being actively recorded by hostile powers, regardless of location, unless they are positive the phone is out of the room.
You've been elected to be the POTUS
+ your adversary is $NATIONSTATE
= your devices are gonna have a bad time
MobileSec
- Inventory the devices you need to defend
- You better be threat modeling
- Effectively communicate your threats
- Know when to bring in outside expertise
Lessons Learned
Credential Management


...oops
Credential Management
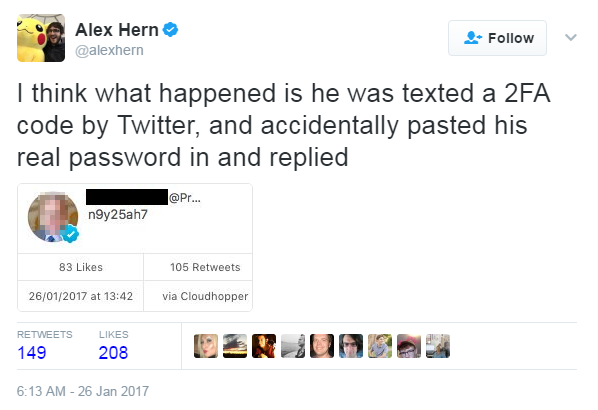
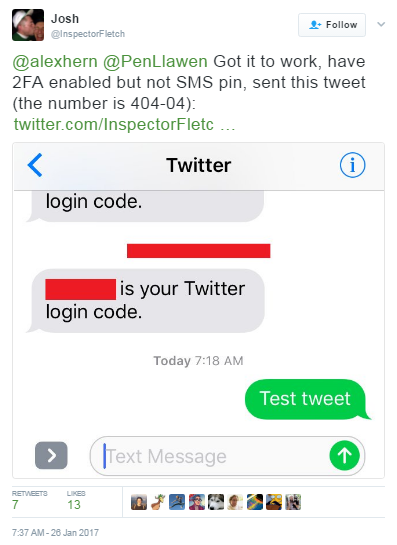
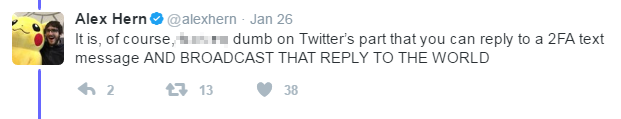
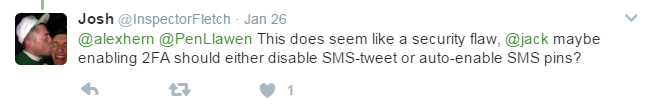
- People make mistakes - be prepared
- Audit your authentication services
- Have a plan to rotate VIP credentials
- Test your incident response plan
Lessons Learned
Blue Feed, Red Feed
See Liberal Facebook and Conservative Facebook, Side by Side
A Misinformed Citizenry
This is How Your Hyperpartisan
Political News Gets Made
“Those websites are marketing websites,” he said after looking at the content, “and the product they’re pitching is outrage.”
Fake News ain't new
A Misinformed Citizenry
1953 - National Enquirer converts to a sensationalist tabloid
American Media, Inc. owns
Star, The Globe, The National Enquirer, Weekly World News, and other similar publications

A good news article has:
- Attribution - for each fact, how does the reporter know it?
- Particularity - if the story offers specific facts, does it connect them to the thesis of the article?
- Corroboration - a reliable story based on an anonymous source will corroborate elements of the source's story in a meaningful way for the reader.
Critical analysis is critical
Do political candidates really need a CISO?
Thank you!
J0N J4RV1S
slides.SecureUtah.org