Unboxing cryptography
Daniela Matos de Carvalho @sericaia
Jan, 14th
Hello 👋

(source https://media.giphy.com/media/14kqI3Y4urS3rG/giphy.gif)
Why Cryptography
Crypto | graphy
"hidden" "to write"
|
What is Cryptography
plaintext
ciphertext
"I want water"
"kudh123y43grfdsjh323jhrgs"
?
plaintext
ciphertext
"I want water"
"kudh123y43grfdsjh323jhrgs"
plaintext
"I want water"
encryption
decryption
What is Cryptography
How: A bit of history

"attack!"
"exxego!"
(Image source https://upload.wikimedia.org/wikipedia/commons/thumb/8/8f/Gaius_Iulius_Caesar_%28Vatican_Museum%29.jpg/440px-Gaius_Iulius_Caesar_%28Vatican_Museum%29.jpg)
Marcus Antonius
(Roman General)
?
(Image source https://upload.wikimedia.org/wikipedia/commons/thumb/8/8f/Gaius_Iulius_Caesar_%28Vatican_Museum%29.jpg/440px-Gaius_Iulius_Caesar_%28Vatican_Museum%29.jpg)
shift (a e)

"attack!"
"exxego!"
Marcus Antonius
(Roman General)
How: A bit of history
Common
mistakes
(naming)
Hashing
Encrypting
Encoding
Obfuscating
Signing
?
Obfuscating
(image source: https://www.flickr.com/photos/daquellamanera/206181168)
Obfuscating
Example: code obfuscation
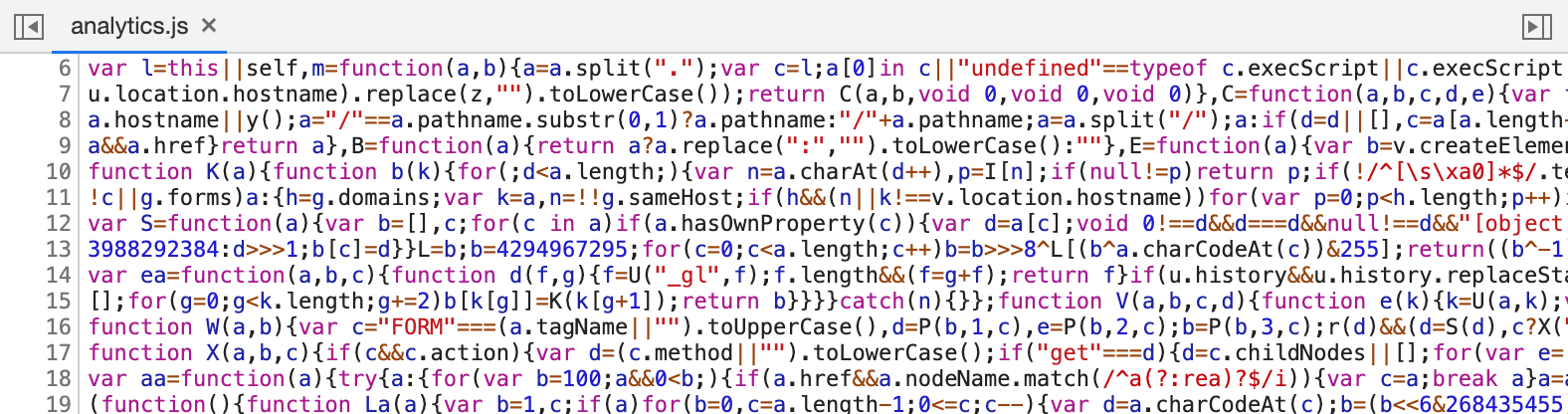
Encoding
(image source: https://www.flickr.com/photos/wapster/4479756238)

Encoding
Example: URL
will be turned into
Encoding
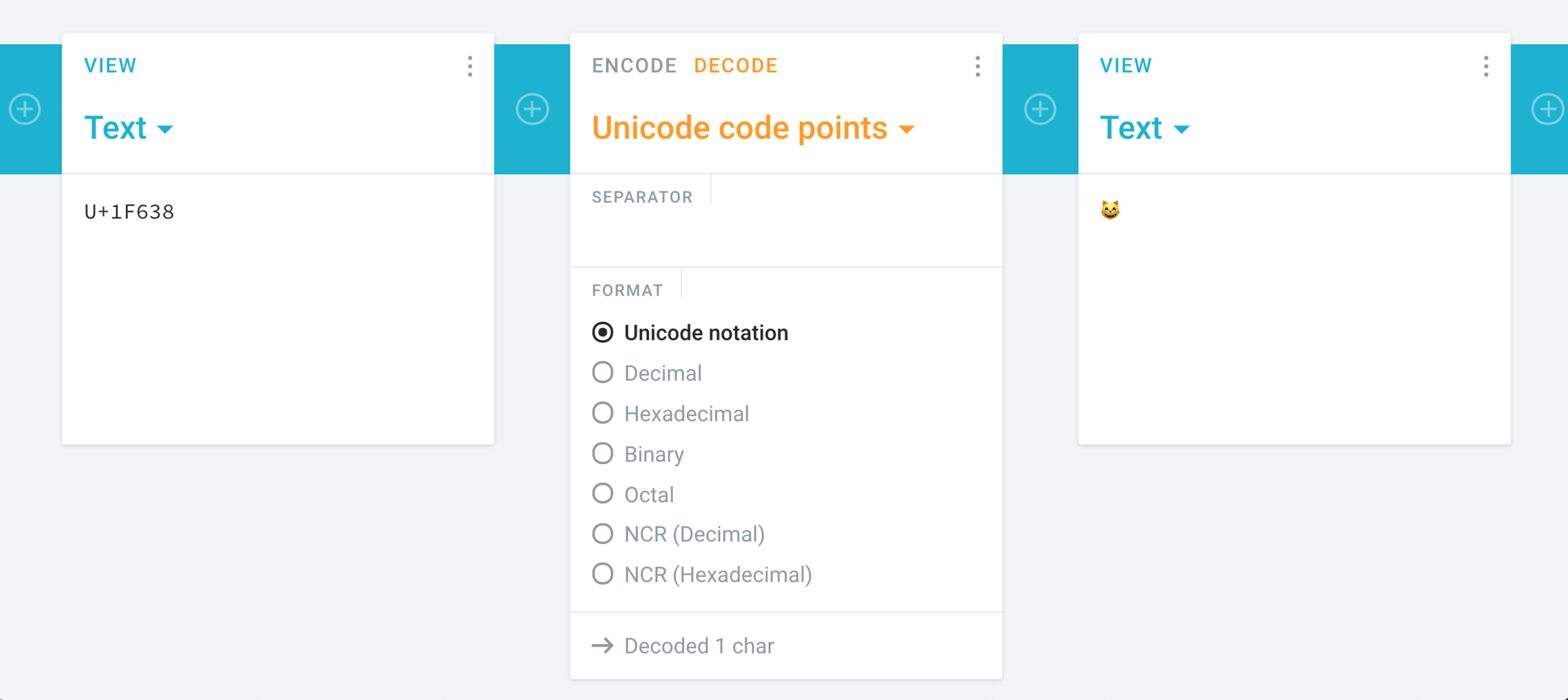
Example: emoji
Encoding
Example: Image encoding
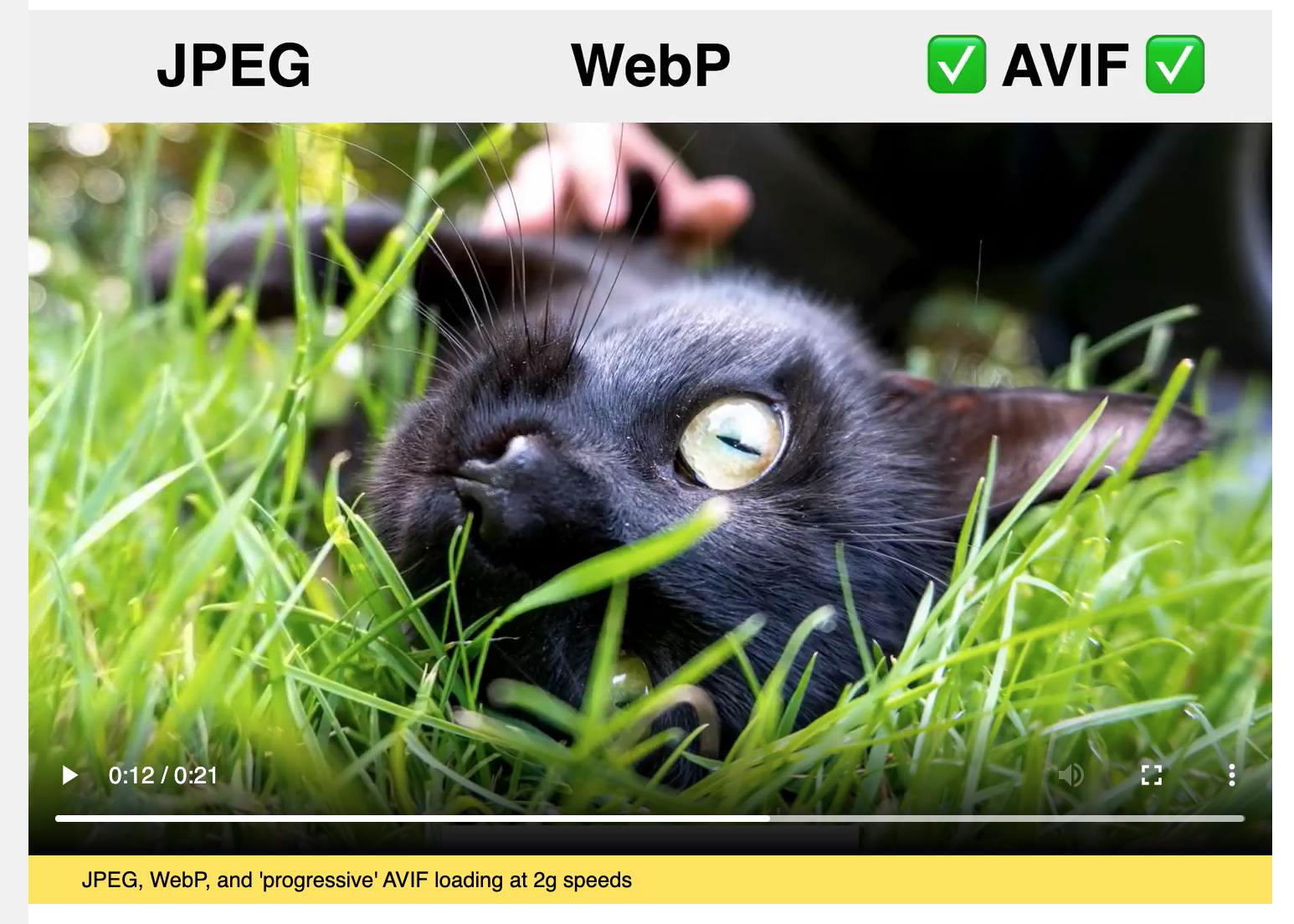
(image source: https://jakearchibald.com/2020/avif-has-landed/)
Hashing

(image source https://media.giphy.com/media/xT5LMO521BqYaz0TxS/giphy.gif)
Example: Subresource Integrity
<link
rel="stylesheet"
href="https://stackpath.bootstrapcdn.com/bootstrap/4.3.1/css/bootstrap.min.css"
integrity="sha384-ggOyR0iXCbMQv3Xipma34MD+dH/1fQ784/j6cY/iJTQUOhcWr7x9JvoRxT2MZw1T"
crossorigin="anonymous"
/>It works by allowing you to provide a cryptographic hash that a fetched resource must match. (MDN)
Hashing
Example: password hashing
Hashing
password
hash
pw2hbPj3
rrE89xF8
pw2hbPj3
...
azMYigjy46F7gAYm
CNoa6Cfe6KHd3L5B
azMYigjy46F7gAYm
Example: password hashing
Hashing
salt
password
hash
pw2hbPj3
rrE89xF8
pw2hbPj3
...
g7Kkosc5HEeTnmgq
eJNmGYYj8z7SaFm5
aFCSdgAR55YBfxm8
ar8o8R7k
65kpfRMQ
L3GJS9gg
hashing ~ "one way encryption"
Encrypting
(image source https://www.flickr.com/photos/152175890@N03/35958764831)


(gif source https://giphy.com/gifs/americangrit-john-cena-fox-tv-l1J3vV5lCmv8qx16M/links)
Encrypting
Confidentiality can be obtained using encryption to render the information unintelligible except by an authorized entity who uses an appropriate key to decrypt the encrypted information.
National Institute of Standards and Technology (NIST)
Symmetric and Asymmetric Encryption
Symmetric Encryption
(same key)
plaintext
ciphertext
"I want water"
"kudh123y43grfdsjh323jhrgs"
plaintext
"I want water"
encryption
decryption
Symmetric Encryption
(same key)
ciphertext
encryption
decryption
👩
👨




plaintext
Asymmetric Encryption
(public & private key)
plaintext
ciphertext
"I want water"
"kudh123y43grfdsjh323jhrgs"
plaintext
"I want water"
encryption
decryption
public key
private key
👩
👨
Asymmetric Encryption
(public & private key)
John
private




public
public
private
Sara
👩

Asymmetric Encryption
(public & private key)
ciphertext
encryption
👩


Asymmetric Encryption
(public & private key)

John's
public
ciphertext
👩
👨



Asymmetric Encryption
(public & private key)
ciphertext
ciphertext
decryption
👩
👨




plaintext
Asymmetric Encryption
(public & private key)
John's
private

ciphertext
Signing
👩

signed message
signing


Sara's
private
Verifying a signature
signed message
verifying


Sara's
public
👨
It was
Sara!
Use
Cases
TLS
Password managers
Instant messaging apps
Email & Storage
SSH
PGP
Webauthn
Use
Cases
...

application layer
transport layer
TCP
HTTP
TLS
application layer
transport layer
TCP
HTTP
TLS
encryption layer
server
client
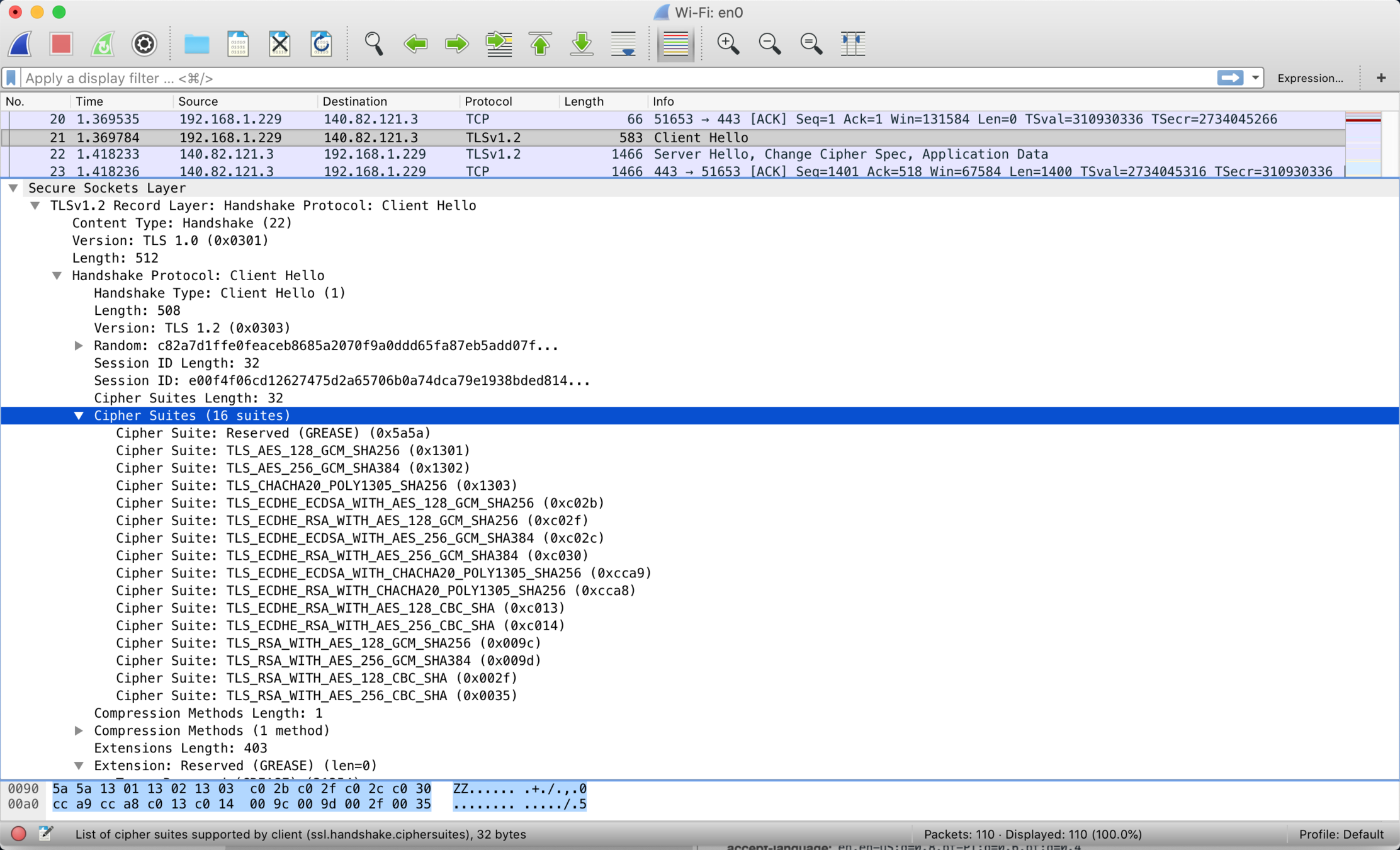
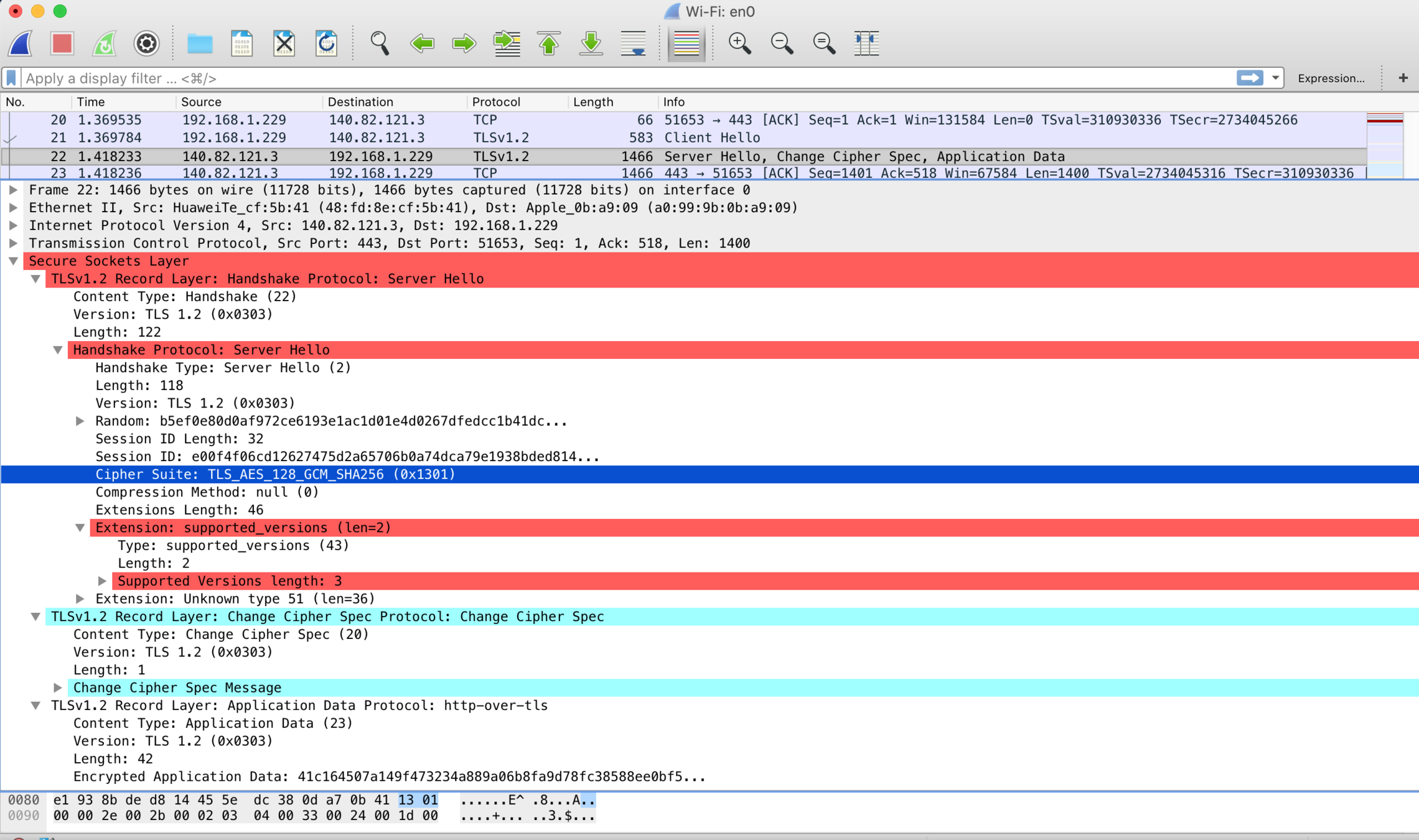
ClientHello
TLS handshake
ServerHello
server
client
ClientHello
TLS handshake
ServerHello
from asymmetric to
symmetric encryption
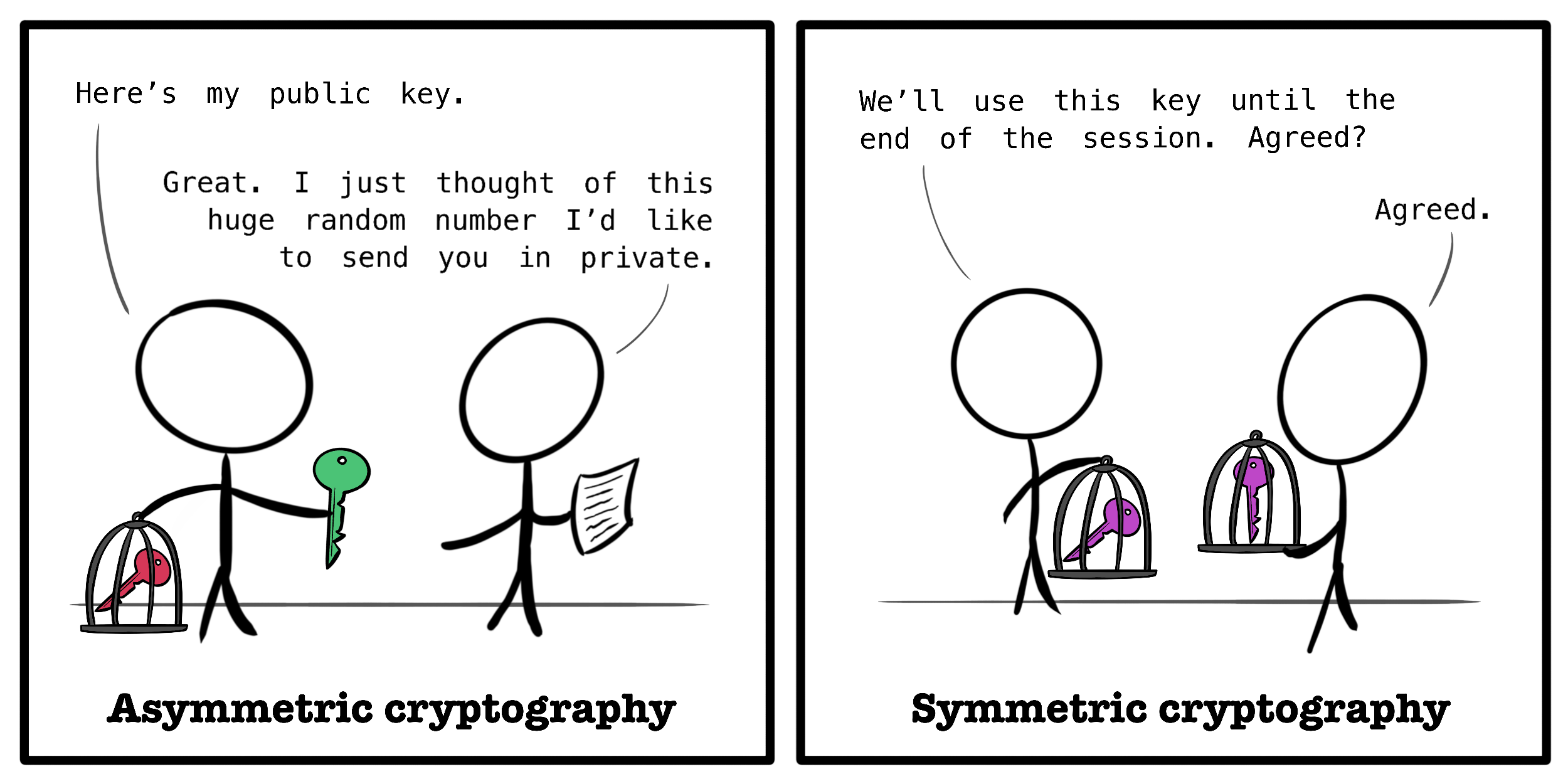
(image source https://victoria.dev/blog/what-is-tls-transport-layer-security-encryption-explained-in-plain-english/)
a note on integrity
with Message Authentication Code (MAC)
Encrypted Message
MAC
Headers
TLS
Password managers
Instant messaging apps
Email & Storage
SSH
PGP
Webauthn
Use
Cases
...
What do these use cases have in common?
(Some) "Basic" rules
What do these use cases have in common?

(gif source https://media.giphy.com/media/FVAvmLbptzZpC/giphy.gif)
Why are we not using the most recent crypto algorithms everywhere?
How to
THANKS 👋
Unboxing cryptography
Daniela Matos de Carvalho @sericaia
Jan, 14th