Never edit WordPress core files!
Seriously. Just don't.
@APredic
About me
- Twitter: @Apredic
- Company: Shindiri Studio
- PHP / WordPress developer
-
Co-founder of Nis WordPress community #WPNis, co-lead organizer of WordCamp Nis #WCNis, #WCEU organizing team.
Scenario
Who are we talking about here?
- Personal sites
- Agencies which build sites for clients
Common scenario
Favor one theme and set of plugins for building the sites for it's clients.
Why you shouldn't hack WP core?
Ask Google
If you do a Google Image search for the phrase “don’t hack wordpress core” you can find a few interesting images.

But Boromir also sad:
One does not simply walk
into Mordor!
So I guess we should just trust Boromir about not editing WordPress core files :)
What are the WordPress core files?
The simplest definition is:
WordPress core files are the one's you download via WordPress.org/download website.
You may never need to look into these WordPress core files. However, you will probably need to troubleshoot them at some point, and it will be very useful to have an understanding of what you’re looking at when you’re trying to a debug paticular problem
Two groups of WP files
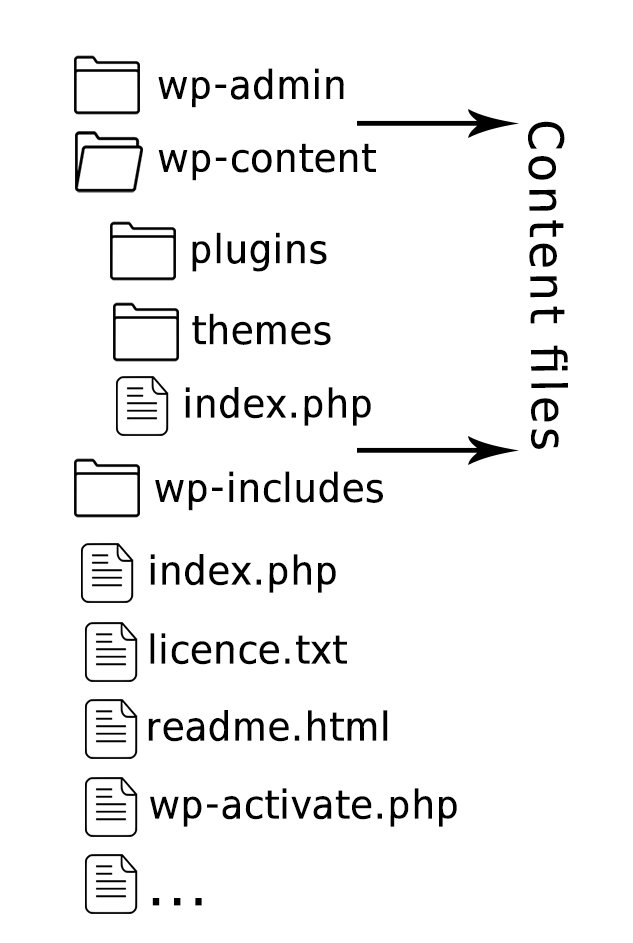
- Core files make up the appearance and functionality of the WordPress platform.
- Content files are added by the user in the form of themes and plugins.
Client
VS
WP cowboy
coding
Not so true story.
Unfortunately, very common scenario.

Client
Name: Marko
Need: Company website
Own office products manufacturing company.
Don't understand how internet works, but knows how to send an email.
He will hire a WP expert to build his website.

Developer
Name: Dragoljub AKA Dragce
Skills: Photoshop, HTML, CSS, JS, PHP basics
Role: Self-proclaimed WP expert
Experience: 20 + WordPress projects
Feels that with WordPress plugins he can make any design and functionality happen.
Dragce's workflow

- Find suitable premium / free theme
- Find plugins that do the job or will need little modifications, preferably free plugins :)
- Client accept solution without knowing how John is going to put up the site. He can be very convincing.
-
Install newest WP version (at that time 4.7.0), setup the theme, add around 30 plugins, write some CSS. Make few html and PHP changes.
-
For one task where client requested custom user dashboard on frontend and some admin customization. He had to make some changes to the WordPress core.
-
Job done.
-
Dragce is not so proficient in PHP but he often modify some core files so all client requests are meet.
-
He doesn't have time or knowledge to build a plugin and implement changes the right way.
-
He tells the client to never hit the update button in WordPress.

After few weeks, Critical zero-day vulnerability in WordPress REST API was discovered that let remote unauthorized hackers modify the content of any post or page within a WordPress site.
Millions of WP sites are in danger, but WP core team issued a patched version and immediate update is required. All the tech and not so tech news are writing about it.
- Marko sends an email to John, asking what to do.
- Dragce curse the stupid WP and tell Marko not to worry, as the threat is not referring to his site.

Dragce, as that usually happens in cowboy coding, wasn't using git to track changes made to the core and he can't remember all the changes done.
- He sends another email to his trusty developer and ask what to do?
Marko, reassured and relieved, continues with his daily routines.
After a few days he notices hacked by NG689Skw instead of his regular homepage. He doesn't understand how this could happen. He curses the WordPress as being unsecured CMS.

-
Dragce answers: Restore a backup of the site before it's been hacked. The update WordPress restriction is still active (don't click WP update button).

Dragce is worried as he can't tell the right date when the site was hacked. Data from that date will have to be entered again...

Marko is in mess not knowing what to do. Also, he will have to pay the developer additional hours for every new fix while the problem won't be solved permanently.
- Marko is Googling:
hacked by NG689Skw
Why people hack WP core
- Lack of knowledge
- Time constraints (don’t have time to hunt down the right way to do it)
- Because the client wants it
Modifying the WP Core files is a Very Bad Idea
- Zero-day vulnerabilities
- Unable to update
- Hacking up what plugins were made to do
- On update your changes will be overwritten
- Empathy toward the developer who comes after you to maintain the WP website
Zero-day vulnerabilities
1. It is a threat or attack that exploits a previously unknown vulnerability in a computer application.
The attack occurs on "day zero" when the vulnerability is discovered so developers had zero days to patch it.
2. Attacks that take advantage of a security vulnerability on the same day that the vulnerability becomes publicly known (zero-day).
Unable to update
Security issue is discovered
Update WordPress
Patched version is released
It is very difficult to update to the latest version of WordPress.
If you can’t update because you have modified the core files, then you are opening up the website to these security issues, and you have increased the chance that your website will be hacked
Hacking up what plugins were made to do
-
There’s a plugin for that.
-
You can always change how WordPress works, by using plugins.
- This can in some scenarios be very difficult, but the extra work outweighs the problems you get by modifying WP core files.
- Finding the missing hook can stop you from hacking the core. Maybe you will discover that there already is a hook to solve your problem, so you don't have to hack core!
What is a plugin?
- To prevent hacking the WordPress core
- To add new functionality
- To protect our code from WP updates
Why do we need plugins?
It is a script, mainly PHP, that extend WordPress to include new functions out of the box.
All plugins are located in wp-content/plugins directory
Submit a patch for the core!
-
The best reason not to hack core is that whatever you are doing should be reworked as a patch for core instead.
- If you need a hook that doesn't exist in WP core, add the action, document it, and submit a patch via Trac. If you're not the only one who would ever use it then you can probably get it added to core.
- You might just need a piece of code to behave differently. Pass a variable by reference, for example, or return a value rather than echo it. This is another good reason to refactor the core so it does what you need it to do and than submit a patch via Trac so someone else can benefit from your work.
Changes made to the core files will be lost on update
-
Once you upgrade wordpress to the latest version all your changes to the core files are overwritten.
- You can still manually update to keep the changes you made, but this is never-ending' job, taking up billable time, unless you can rebill your client for it.
Empathy toward the colleague developer
Most of the websites will change or update developers over the years so there is no insurance or guarantee that you will be working on a appropriate website four years from now.
It can be very hard for the developer to realize what changes previous dev made on the core files and it puts the website owner in a bad position because the most of the developers will refuse to work on a hacked version of WordPress CMS.
Why is so important to update
Automatically opting into these updates means they are applied to your site or network as soon as they’re released, which is especially important in terms of security.
The WordPress core development team does a great job of patching up security holes, but if you don’t update your site, your site isn’t protected.
Every update contains
- New features
- Bugs and Security Fixes
- Other changes
Insecure core = WP hack attacks
Most successful WordPress hack attacks are typically the result of human error, be it a configuration error or failing to maintain WordPress, such as keeping core and all plugins up to date, or installing insecure plugins etc.
Biggest source of vulnerabilities in WordPress
- Plugins
- Brute force
- WordPress core
- Themes
WordPress vulnerabilities overview
- Plugins > 55%
- Brute force > 16%
- Core < 10%
- Themes < 10%
- Other...
Keeping everything up-to-date is key. There are no serious known vulnerabilities in the current version of WordPress core.
There are however, a large number of known vulnerabilities in older WordPress versions.
Keeping WordPress core up-to-date is very important.
So if we aren’t supposed to edit the core, who is?
People who implement features and push out updates
Lead developers, core developers, and guest committers, all work together to maintain the WordPress core.
Because WordPress is fully open source, anyone is free to contribute documentation and code to the codebase. However, commit access on the core is limited, and any new contributions go through a code review process.
make.wordpress.org/core/
True fact
If your WordPress developer ever told you don't ever hit the update button in WordPress, than something isn't done WordPress friendly way.
Some tweets