The Long
Hard Road of AppSec





Kick Start
THE JOURNEy
What it takes

Mission Goals


Gitlab
support the business and ensure that all GitLab products securely manage customer data. We do this by working closely with both engineering and product teams.


SQREEN
increase the security of the services developed by their company without impacting the velocity of other software teams.


Farfetch
Incorporate modern key security standards on all phases of the Software Development Life Cycle (SDLC), in the F-Tech Portfolio.


Be enablers rather than gatekeepers


ADVISE RATHER THAN DICTATE

AUTOMATion

RISK-AWARE

REDUCE FRICTION

SECURITY IS HOLISTIC BUt KEEP RAISING THE BAR

Getting Started


CReate
the applications and Services portfolio

Dig into product development practices

Survey engineers for their appetite of security involvement

Set up relationships with Product and Engineering

Work out quick wins and define a long term strategy

enhance or Start an
InfoSec Culture
Lead by Example

Show Your Work!

DEVSECOPS
+
Secure


DevSecOps
DevSecOps refers to the integration of security practices into a DevOps software delivery model.
DevOps is an organizational paradigm that aligns development and operations practices as a shared responsibility.

DevSecOps
it’s important to drive cultural and procedural changes that help raise security awareness and considerations early in the development process.


Security Requirements
+
Secure Design
+
Secure Code
+
Testing
+
Deployment
Secure SDLC
SECURity REQUIREMENTS
A security requirement is a statement of needed security functionality that ensures one of many different security properties of software is being satisfied.

SECURE Design
Secure design is a culture and methodology that constantly evaluates threats and ensures that code/Architecture is robustly designed and tested to prevent known attack methods.

SECURE Code
Secure coding standards are rules and guidelines used to prevent security vulnerabilities. Used effectively, these security standards prevent, detect, and eliminate errors that could compromise software security.

Testing
the process of testing, analyzing, and reporting on the security level of a software application.

Software composition analysis (SCA)
STATIC APPLICATION SECURITY TESTING (SAST)
DYNAMIC APPLICATION SECURITY TESTING (DAST)
Interactive application security testing (IAST)
Deployment
mechanism through which applications, modules, updates, and patches are delivered from developers to users.


Engagement
+
Sec Architecture Team
+
SCA + SAST + Sec Libs + Sec Champions + Code Guidelines + Sec Automation
+
DAST + Run Time Validation
+
BBP + Monitor
Secure SDLC
AppSeC
Processes


Audit Process
Before starting a new assessment, we must gather technical and corporate information from the target. The latter will be used during the audit.

Before
Audit Process
During the audit, we must guarantee that all technical aspects are covered. This includes making both a static code analysis and a runtime validation, always taking into account the application inherent risk.
All the security guidelines should be checked (e.g. SAST profile or threshold is the correct one, AuthN/Z between services and dependencies, sensitive data is being well-handled, ...).

During
Audit Process
After the technical audit, we must guarantee that our communication with the stakeholders is clear and educational.
Excellence must be in everything we do, so all findings should follow the reporting guidelines and be carefully reviewed by the authors and double reviewed in the peer-review process.

After
Security Business Partner

Internal team role that will help synchronize, communicate and manage expectations with the stakeholders. It's an essential part of the vulnerabilities follow-ups.
Risk

Risk is the potential for uncontrolled loss of something of value. Values can be gained or lost when taking risk resulting from a given action or inaction, foreseen or unforeseen.
Information Security risk is defined as "potential that a given threat will exploit vulnerabilities of an asset or group of assets and thereby cause harm to the organization." (ISO 27005).
Vuln Lifecycle




Dev Security Community
The Security Champion's role is vital to enhance the overall security of the software development process. Every Security Champion is crucial in helping to improve the security posture of their team by assisting in several aspects.
Security Champions

Visibility
Revisit the team(s) backlog(s) and current initiatives to ensure that all known security issues already reported are mapped to be part of the current or near-future sprints.

Expertise
If there are issues to be resolved, no one is better than the Security Champion, having attended the assessment's results presentation, they can then act as a Subject Matter Expert (SME) during the mitigation phase.
From a preventive point of view, this member is in charge of leveraging and applying the know-how from the Farfetch internal training sessions (a.k.a Security Universities) to find possible design and implementation pitfalls early on in the SSDLC process.

Communication
The Security Champion will act as a bridge between the team(s) and the Security realm, leveraging each side expectations on sprint prioritization concerns, assessing possible fixes or mitigation designs, validating technical feature requests and any other service the AppSec or the Security Team can provide.

Training (Perks)
The AppSec Team offers several Security Universities to help all Security Champions improve their attack, defense, and prevention knowledge around the most common development pitfalls.


Events (Perks)
At least one big event will happen every year to get the community together in person (if possible). Usually, the event comprises a full day of talks, a Capture the Flag (CTF), and some surprises.




Community (Perks)
To keep a healthy community, we have monthly syncs named Security Clinics. To ease communication, we have a private Slack channel to share doubts or discuss any pertinent topic, along with a mailing list in which we can get a weekly refresher of what is happening in the InfoSec world.


Security Clinics
Security Clinics is the monthly meeting for the Security Champions. It is the space for our community to get together and share our collective knowledge. The agenda will vary, but we will address topics such as: AppSec processes, actions, and activities; F-Tech development challenges; Security issues; Did you know that... Learn something new.


TL;DR
-
Perform simple threat modelling exercises on the daily task/user stories
-
In code revision sessions, evangelize security guidelines and best practices
-
Look for the SAST integration on the SSDLC, and study possible solutions for the findings
-
Synchronize with stakeholders and triage incoming security issues reported by the AppSec Testing team
-
Look at the team(s) backlog(s) and try to raise the priority of security issues
-
Participate in the monthly Security Clinics sync

Training


"Embrace The Dark Side"
Security University
WEB/Mobile TOP 10 (IOS AND ANDROID)
SQLI/NOSQLI
INSECURE DESERIALIZATION
XML EXTERNAL ENTITY (XXE)
Cross-site Scripting (XSS)
CRYPTOGRAPHY FOR DEVELOPERS
CROSS-SITE REQUEST FORGERY (CSRF)

Security University
Agenda
What is it?
Can we kill it?
Hands-on!

All of the training sessions follow the same structure, except the crypto training, where the goal is to disambiguate crypto world jargon and, in the end, a cheat sheet for daily use is handed over.
Engineering


Reporter Tool
One job, simple, clean!
Accessible via API
Centralize all reports
Single source of truth
Ticket system agnostic
Same report template
Sync team writing styles
Overall report quality improvement

Reporter Tool



Daemon Tool
Ephemeral content
Team operations aggregator
Periodically operations syncs
Easy to integrate on the ecosystem via APIs
Extracts Transform and Load (ETL)



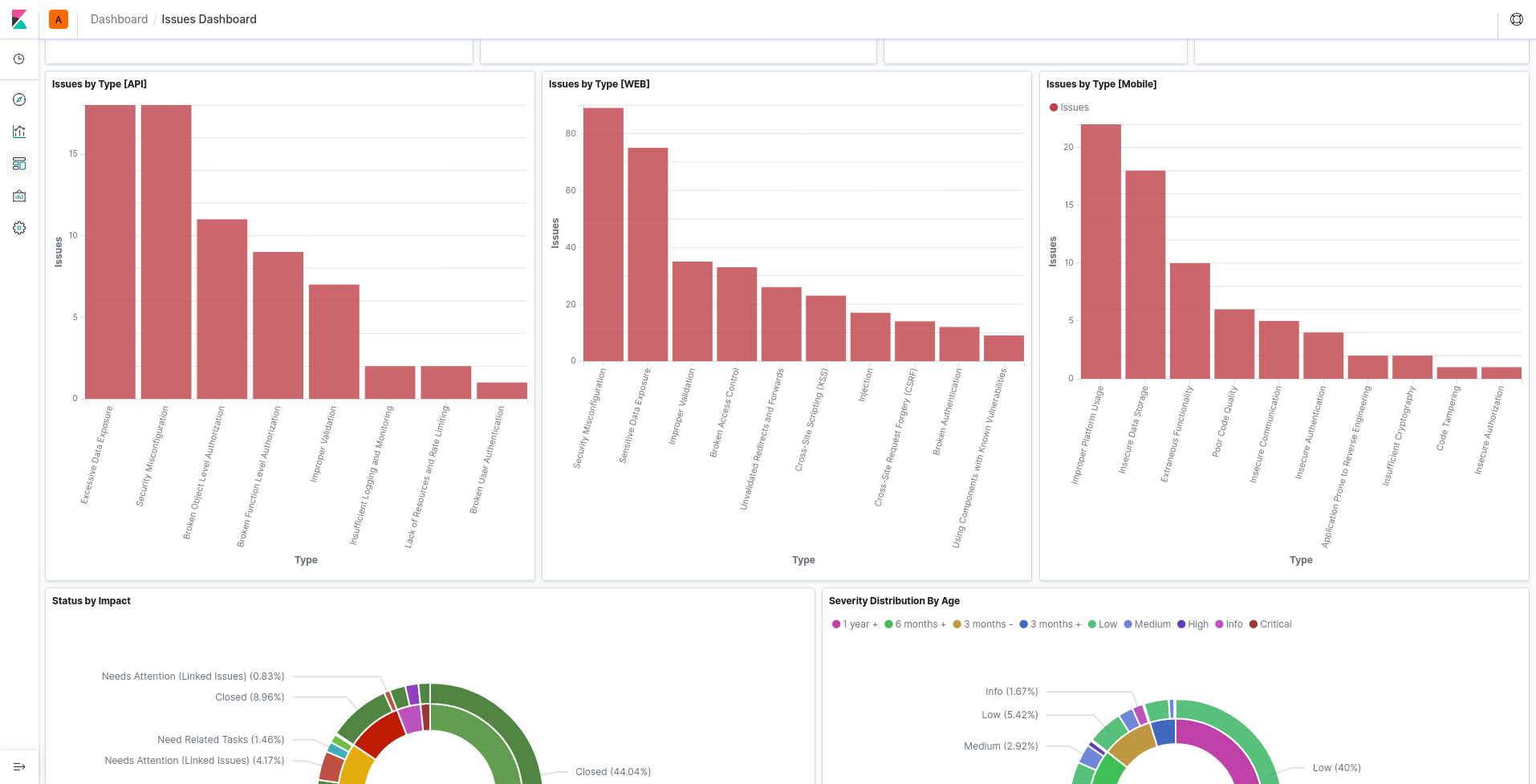
DASHBOARDS
Easy to navigate
Track ongoing work
Meaningful visualizations
Easily query available data
Internal and public boards
Company and areas overview
Designed to acquire and deliver business metrics




RISK REGISTER
Simple and clean UI
Central repository of risks
Full back-office operations
Simple AuthZ and AD integrated
Avoid document chaos



CHECKODE
Git hook
Custom rules
Catch secret leaks
Analyse all commits
Easy "enforce" company policies
Integration with linters and others parser
Alarm/Notify commiters and security team
Preventive vs Reactive



Sec Champions HQ
Achievements wall
Point of contacts finder
Training and events tracking
Easily find other community members
Central community management



SECURITY FRAMEWORKS
Simple to use
Internally built
Code standardization
Multi-language support
Ease complex operations setup
Wrappers around native libraries
Solve a particular problem



AppSEC as a Discipline
CONTINUOUs CHALLENGES
Keep
portfolios
updated

Keep relationships w/ Product and Engineering

Keep TECHNICALLY updated

Always looking for IMPROVEMENT OPPORTUNITIES
Tech stack changes, new automations, feature revamps, new products...

One Team, One Voice!

Keep the Basics Right!

AppSec Hat


We want to build a client chat!
Put on your thinking cap and dig deep into what might go wrong

function BAU() {
str = document.getElementById("xpto-field").value;
extra = "<input type='text' value='" + str + "'/>"
document.getElementById("output-div").innerHTML = extra;
}
What's Wrong with this code?
'><img src onerror=alert(1)> (Breaking HTML Attribute to HTML Tag)
' onfocus="alert(1)" (HTML Attribute)function BAU() {
str = document.getElementById("xpto-field").value;
encoded = encodeURI(str);
extra = "<input type='text' value='" + encoded + "'/>"
document.getElementById("output-div").innerHTML = extra;
}
Fix
<!-- Using Safe DOM APIs -->
function BAU() {
str = document.getElementById("xpto-field").value;
var extra = document.createElement("input");
extra.type = "text"
extra.value = str
document.body.appendChild(extra);
}Hey, we are integrating w/ this brand new marketing partner.
Put on your thinking cap and dig deep into what might go wrong

Content-Security-Policy: script-src 'self' https://cdnjs.cloudflare.com/;
object-src 'none' ; report-to /Report-parsing-url;
What's Wrong with this Policy?
"><script src="https://cdnjs.cloudflare.com/angularjs/1.1.3/angular.min.js"></script>
<div ng-app ng-csp ng-click=$event.view.alert(1337)>
APIs are the new cool kids, is CSRF still a thing?
Are we vulnerable or not...

AND SINCE IT'S AN API DO YOU HAVE ANY OTHER SUGGESTION?
Anything else?
Content-Security-Policy: sandbox; default-src 'none'; frame-ancestors 'none';
X-Frame-Options: DENY
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=63072000; includeSubDomains;
Content-Disposition: attachment; filename="api.json"
Remove Proprietary Headers (X-Powered-By, Server, X-AspNet-Version, X-AspNetMvc-Version, ...)
Need to confirm that all responses go out with the appropriate content-type
and charset (E.g. Content-Type: application/json; charset=utf-8)Special Thanks
To AppSec team and Friends!
José Moreira, Mariana Fernandes, Inês Martins, Nuno Paula, Rui Godinho, Guilherme Scombatti, Ricardo Ramos, Lotus Wang and César Silva.


The End!

